NAT AT&T Fiber
-
I put ATT GW in passthrough mode and disabled the onboard WiFi, and added my own enterprise class access points behind pfSense.
You are better off hosting a VPN you can securely remote into your home network.
Personally, I host Tailscale on pfSense and advertise sub-net routes so I can remotely access any device behind pfSense using the local LAN IP address. They have a free tier with up to 3 users and 100 nodes. With advertising sub-net routes enabled, you only need one instance of Tailscale running.
Your scenario is exacly why I run pfSense bare metal on a dedicated appliance. Makes it a "set it, and forget it" Ron Popeil device, except for infrequent updates.
-
As @elvisimprsntr said, better to turn off wifi (which I thought was the default behavior when you put an ATT router into passthru mode).
Are sure you can actually access internet on a device other than the one that the public IP is being passed through to?? Sounds like the ATT device isn't actually in passthrough mode to me?
@sae said in NAT AT&T Fiber:
The problem is if I'm in my office, I can't connect to the iLO on it's local ip.
Where is your office in this setup? Is that a remote site or is it on the 192.168.0.1/24 network?
I can get to 192.168.9.1 but not 192.168.9.11 (iLO ip)
is there something I could do to route this or does this need a static route on the ATT device? (I don't see a static route option)I guess you are blocking RFC 1918 traffic on WAN aren't you?
-
@Gblenn said in NAT AT&T Fiber:
Are sure you can actually access internet on a device other than the one that the public IP is being passed through to?? Sounds like the ATT device isn't actually in passthrough mode to me?
No issues for me
On my ATT GW (NVG599) you have to log in to the interface (192.168.1.254) and in addition to setting passthrough mode, you have to set mode to fixed and specify the WAN MAC address of the pfSense firewall.
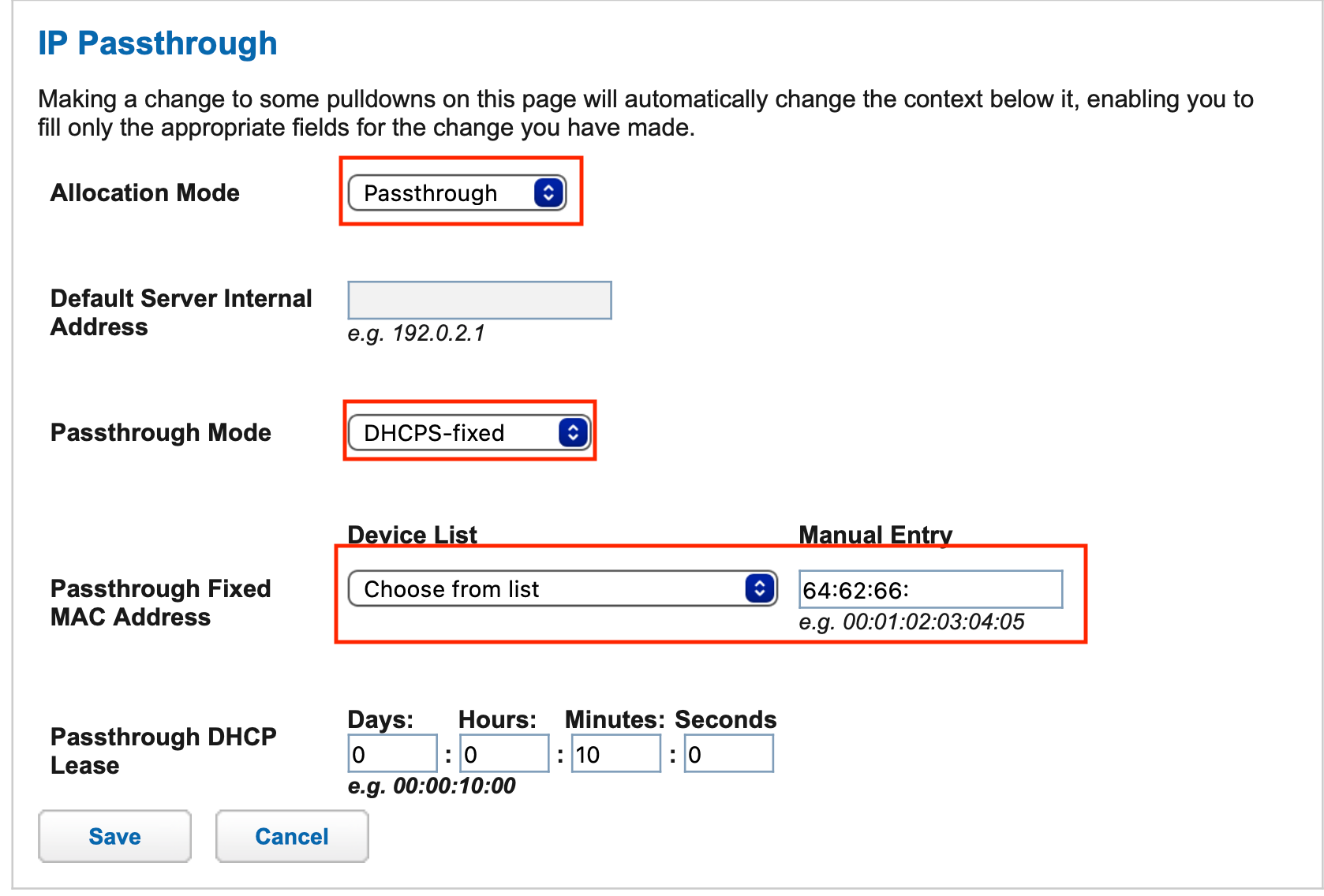
-
@elvisimprsntr Quoting myself again...
Are sure you can actually access internet on a device other than the one that the public IP is being passed through to??
So with the ATT modem in DHCP-fixed, the only device that can get a public ip is the one you enter into the MAC field (pfsense).
So how can you then at the same time have internet access on another device also connected to the ATT (now modem)? Or am I misunderstanding the whole idea of placing the server on the ATT device LAN?
-
You are confusing me with the OP. I am not the one trying to place a server on the ATT GW LAN
The OP is running pfSense as a VM on his server. pfSense VM locks up, so he wants remote access to server so he can reboot and get pfSense working again. Just seems like more headaches than it's worth running pfSense virtualized. Every time you update your server and have to reboot, you loose your entire network including internet access.
I run pfSense bare metal on a dedicated low power appliance and never have to touch it, except for very infrequent updates. When I want remote access to my LAN, I use Tailscale. Not sure why there seems to be so many who insist on running pfSense virtualized, other than someone thinks they are saving $ on power. It costs me <$13/year to run my dedicated pfSense appliance. You can pick up a used Qotom Mini PC for ~$50 off evilBay. They will eventually figure out it creates more problems than it solves. What is the price of one's sanity?
-
@elvisimprsntr Haha, indeed I am, so sorry about that!
-
@Gertjan said in NAT AT&T Fiber:
the server is 'behind' pfSense, on the pfSense LAN ?
If it's on the ATT LAN (like the pfSEnse WAN) then the traffic neverSorry got caught up on some work....
pfSense ip is the public:
192.168.9.x is not public, its rfc1918.
192.168.9.1 is the ATT router LAN ip. Not the public IP passed through to the pfsense
Why 192.168.9.11 ? I thought the server is 'behind' pfSense, on the pfSense LAN ?
If it's on the ATT LAN (like the pfSEnse WAN) then the traffic never uses pfSense.I put the iLO port in front of pfsense in the ATT router. I want to be able to reboot the server if for some reason pfsense goes down. The rest of my internal network is on the 192.168.0.1 subnet
-
@elvisimprsntr I do host my own vpn to access the network remotely. I do have ATT in passthrough but noticed that the wifi still worked and was giving ip's based on it's subnet. I left that up for guest access as it's in front of the firewall.
The entire reason I want to do this is if pfsense goes down or if I'm traveling pfblocker or something is blocking me from getting vpn access. Don't know much about tailscale, just looked into it a bit when I switched my house internet and they were using CGNAT...made me switch back.
Your scenario is exacly why I run pfSense bare metal on a dedicated appliance. Makes it a "set it, and forget it" Ron Popeil device, except for infrequent updates.
Bare metal or not, this would be the same scenario.
@Gblenn 100% sure it's passthrough and sending the public ip to pfsense. and 100% sure I'm getting internet on devices connected to the ATT subnet
So with the ATT modem in DHCP-fixed, the only device that can get a public ip is the one you enter into the MAC field (pfsense).
So how can you then at the same time have internet access on another device also connected to the ATT (now modem)? Or am I misunderstanding the whole idea of placing the server on the ATT device LAN?
I don't think you are misunderstanding the setup and I have no idea how both devices have internet at the same time. I was surprised when I saw it working as well.
-
@sae It works because the IP Passthrough mode on ATT residential gateways is not a bridge mode. It's closer to a NAT mode for the passthrough host. On an ATT BGW320, for example, the passthrough sessions can be seen in the BGW's NAT table: Diagnostics>NATTable. Overall, the gateway is still functioning as a router, which is why you can attach additional, non-passthrough, hosts to its LAN.
Here's an older doc from ATT that attempts to explain Passthrough.
-
@marcg Good info. That makes sense then. It's essentially a DMZ passing through the external IP. Still not sure how both the att router and my pfSense passthrough can have the same IP but I'll chalk it up to magic.
In any case, I have it working great now. I can reach my iLO gui if for whatever reason the pfsense goes down, I can reboot or reconfigure it to get everything back up remotely.