Supressing logs blocking IPv6 mutlicast and broadcast addresses
-
Hello,
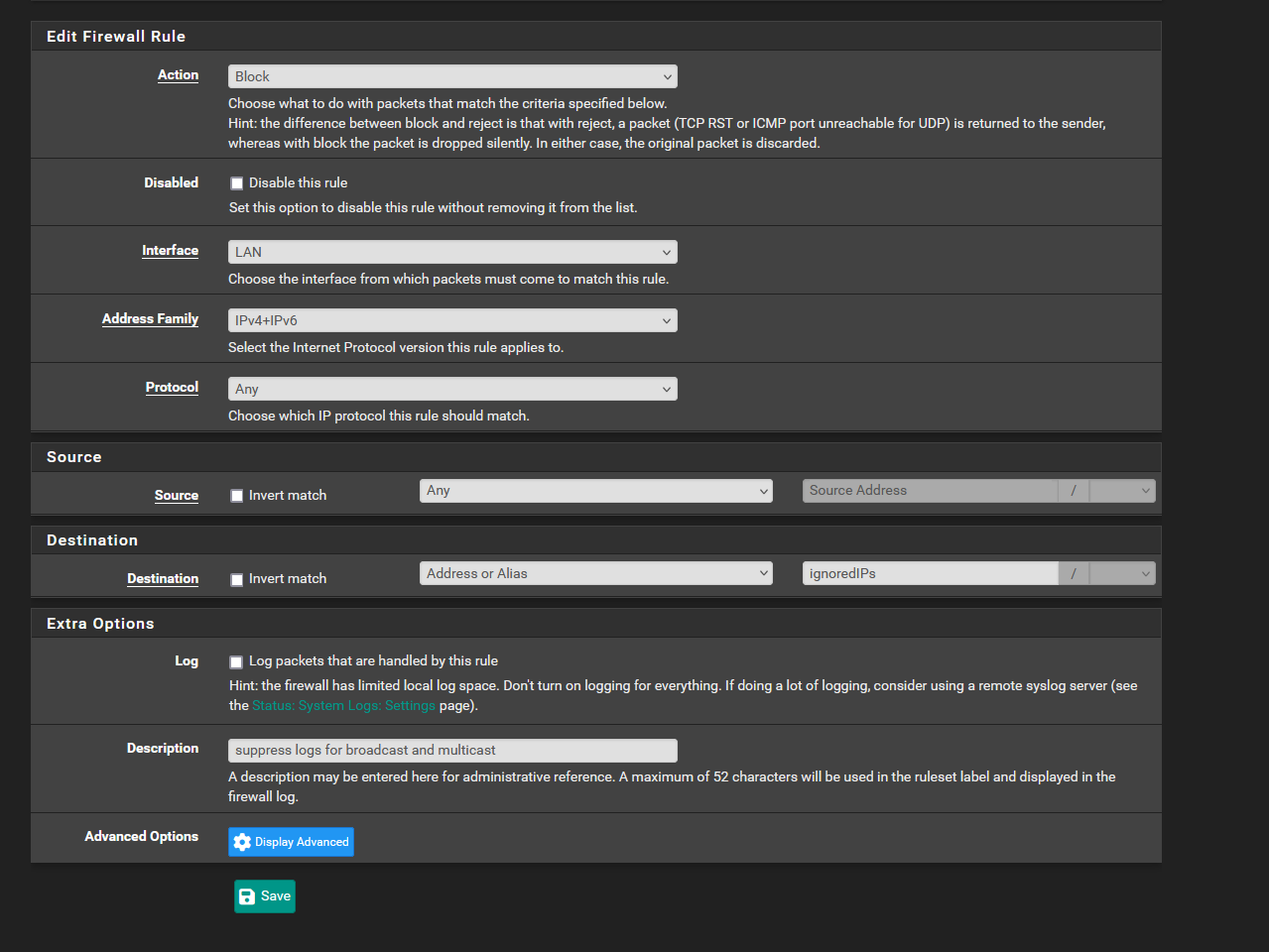
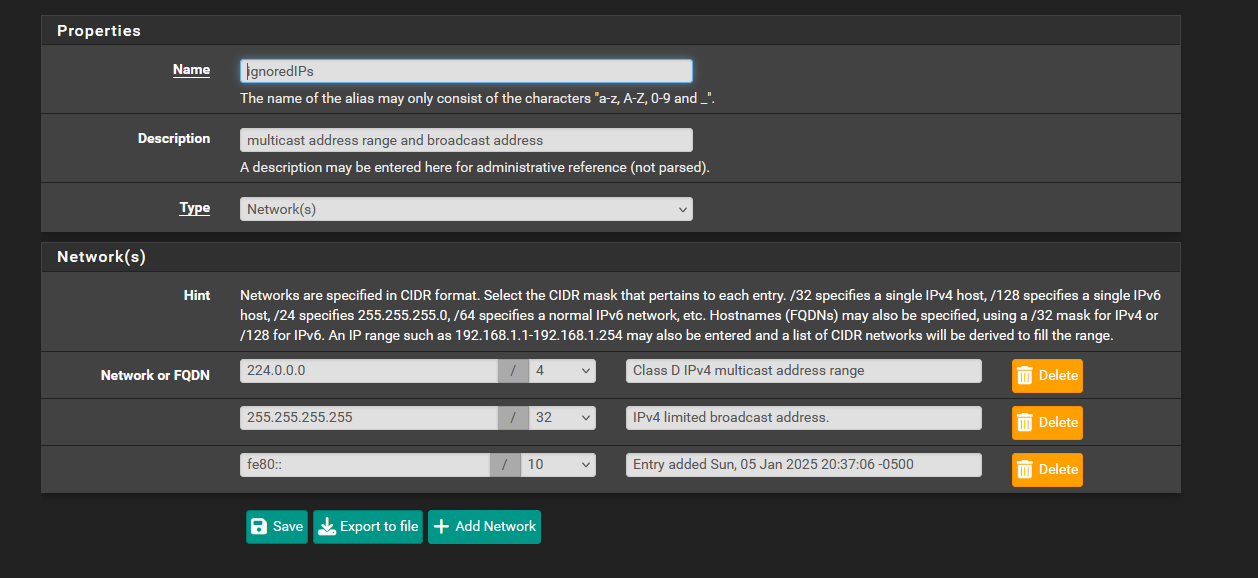
My firewall logs blocking a lot of multicast and broadcast traffic. I watched a video where someone blocked 224.0.0.0/4 and 255.255.255.255/32 to help clear the logs so this traffic wouldn't be recorded in the firewall logs.
If i wanted to do something similar for IPv6. What would I block?
FF00::/8
AND
FE80::/10
Thanks
-
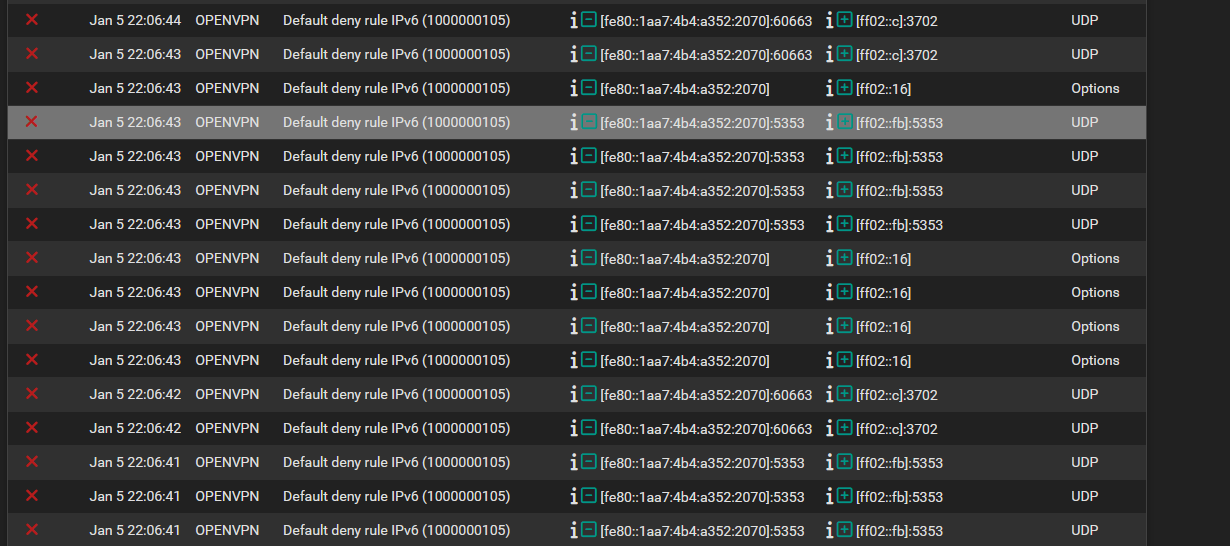
@CatSpecial202 what exactly is being logged and by what rule - can you post up some examples.
-
-
@CatSpecial202 5353 is mdns - bane to any network, noise for zero reason if you ask me.. Users should have to turn that shit on if they want to use mdns.. And sure shouldn't be going out a vpn connection.
That 3702 is WS-Discovery, why would some client think that makes sense to send out a vpn interface?
ff02::16 - joining a multicast group, again has zero use out a vpn connection.
You would wish some of these people programing these stacks would - say why should we send this noise out this interface..
-
There's no such thing as broadcasts on IPv6. The closest to it is all nodes multicast, which is an ICMP6 message. FF00::/8 is multicast. Since IPv6 relies on multicasts for a lot, you want to be careful of what in that range you filter. For example I just saw a multicast to ff02::1, which is a router advertisement to all nodes. If you block that, you'll kill your network. FE80 the link local range and those shouldn't even be passing through pfSense. However, they are also critical to the operation of IPv6, so again be very careful of what you filter.