[Guide] Setup a wireguard tunnel to VPN provider (multiple VPN tunnel setup)
-
I've been running pfSense with OpenVPN tunnels to VPN providers for years. Now it was time for me to switch to Wireguard. I ran into some really annoying and frustrating situations, especially with the mixed setup of multiple OpenVPN and Wireguard tunnels
Therefore I created this step-by-step guide with my major lessons learnt at the end. Maybe it's useful for some of you.
This guide was created using pfSense 2.7.2-RELEASE and pfSense PLUS 24.11-RELEASE.
My VPN provider is Torguard, but config generators are available with most VPN providers.Preparation
- Remove unused gateways, static routes and gateway groups
- Remove unused interface assignments
- Remove unused firewall rules and unused NAT-rules (especially Outbound rules).
- Make sure that Outbound NAT Mode is set to Manual Outbound NAT rule generation. This is essential in order to ensure that the traffic is ALWAYS routed via the intended routes. If you are not familiar with settings outbound NAT in pfSense, I advice to get familiar before continuing in this guide!
Wireguard Setup
1.) Install the Wireguard package:
Head to System>Package Manager>Available Packages and search for wireguard, click Install to install the wireguard package
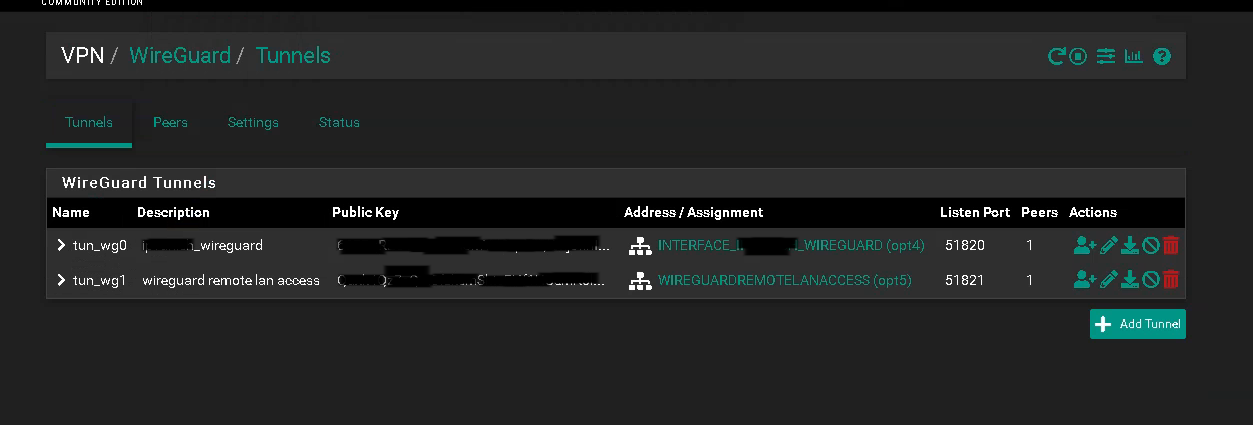
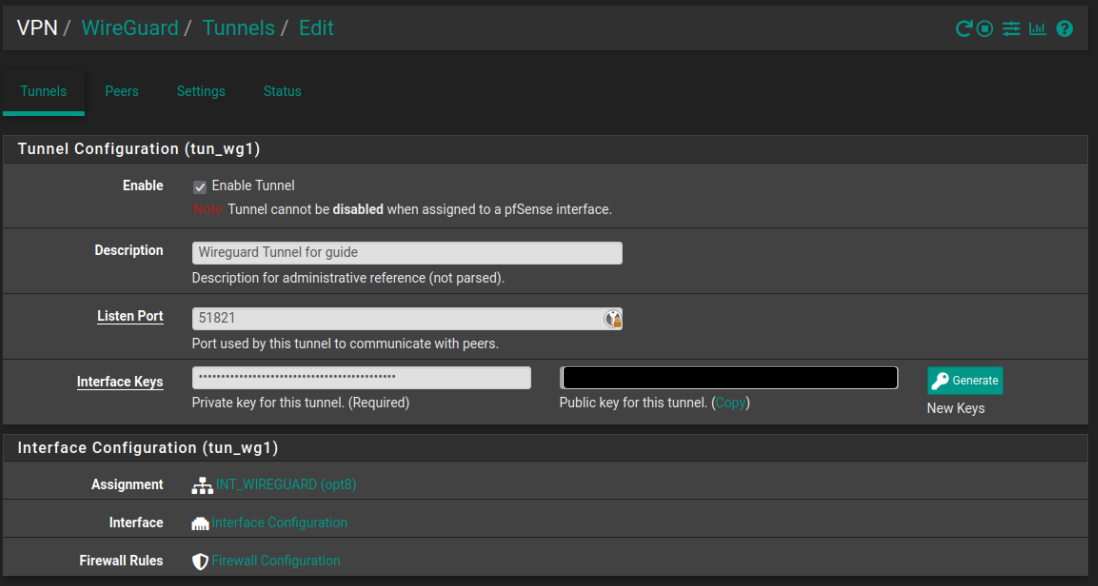
2.) Add a tunnel
- Navigate to VPN > WireGuard > Tunnels and click + Add Tunnel
- Check Enable Tunnel
- Enter a Description, like Wireguard_VPN
- Leave Listen Port empty (default)
- Click on Generate
- Click on Save Tunnel and Apply Changes
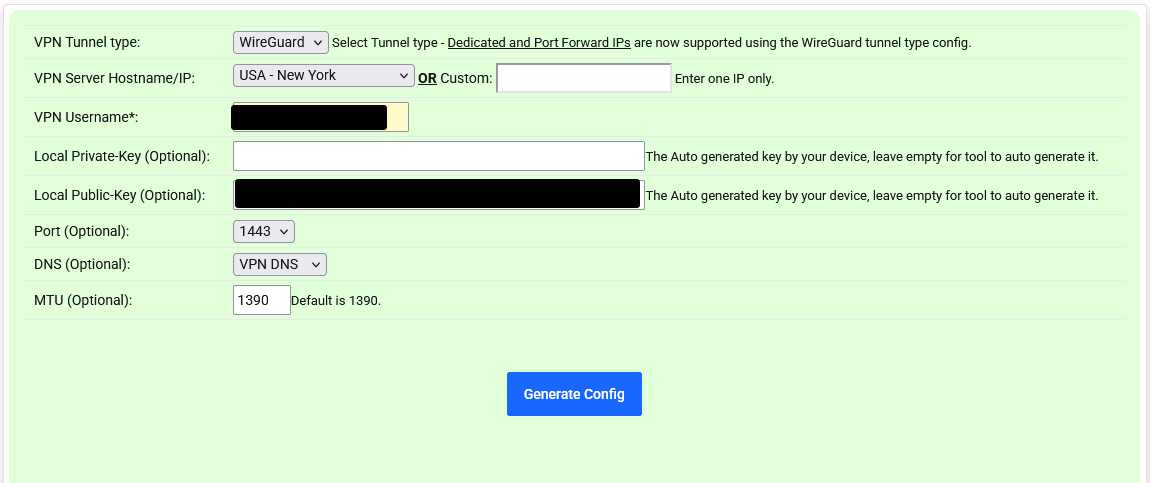
3.) Generate Wireguard Config
Go to website of the VPN Provider and follow the instructions for generating the wireguard config.
The following steps are for TorGuard, your's might be different:
-
Select VPN tunnel type: Wireguard
-
Select VPN Server Hostname/IP/location: e.g. USA - New York
-
Enter VPN username
-
Copy ONLY the public key generated in Step 2 and leave “Local Private-Key” empty
-
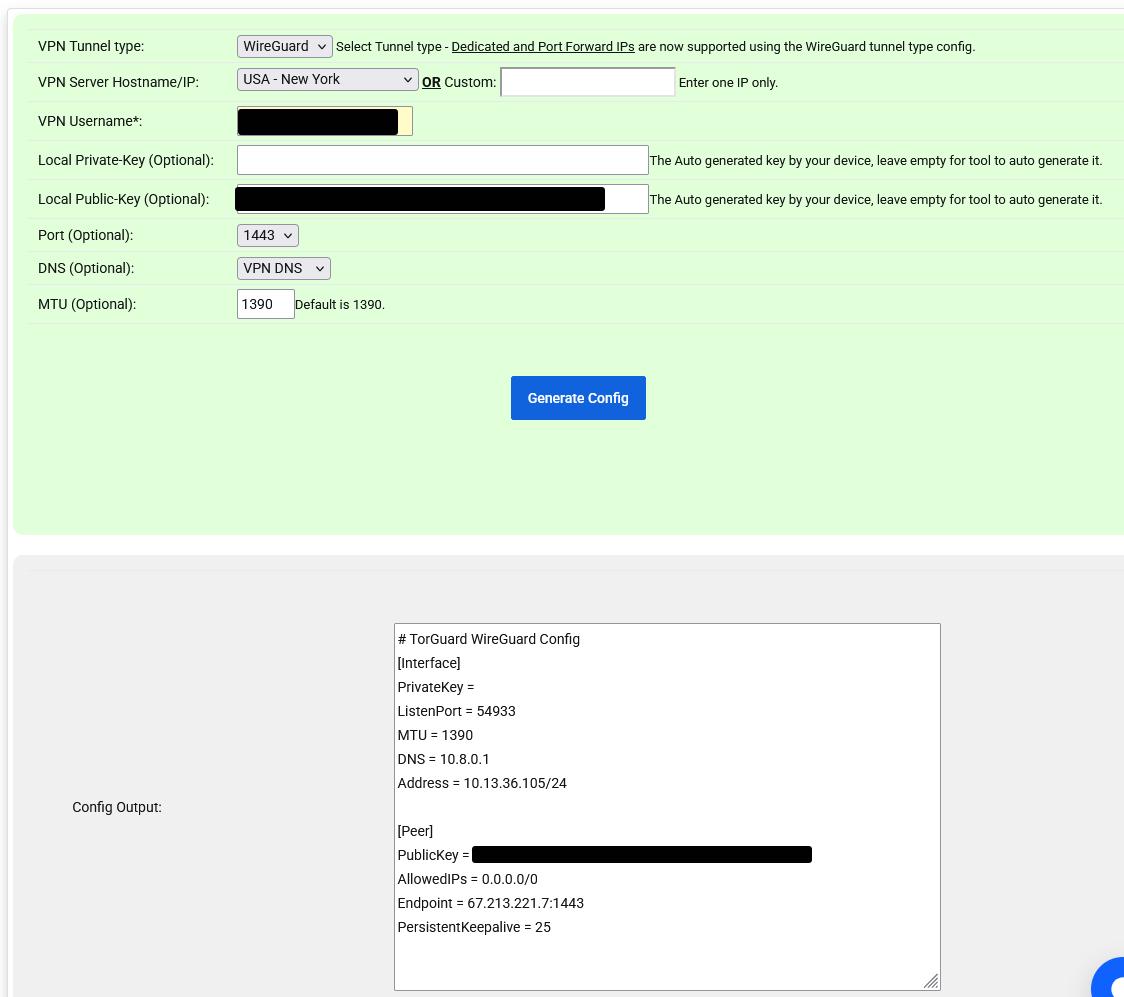
Click Generate Config to get the tunnel config and peer config
-
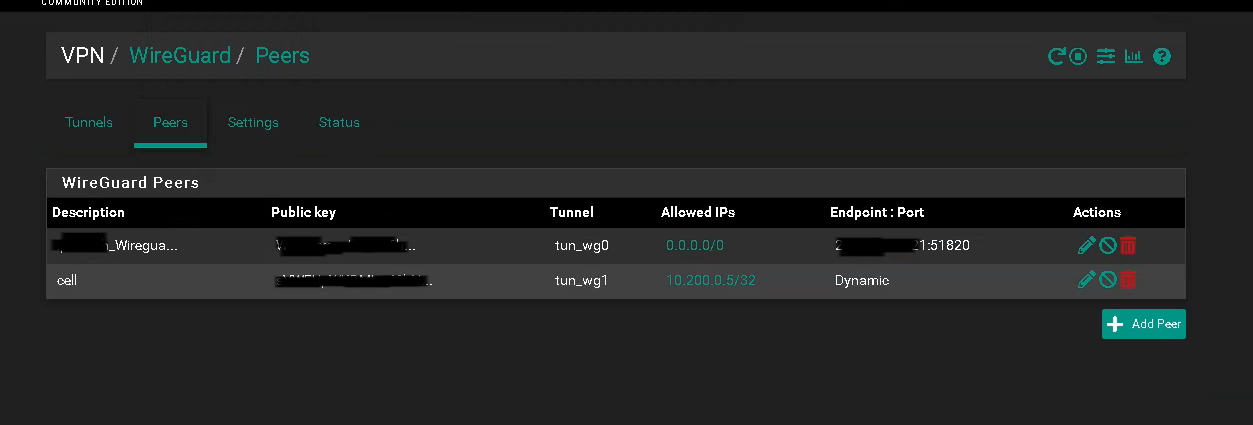
Navigate to VPN > WireGuard > Peer
-
Click Add Peer
-
For Tunnel select the name of the tunnel created in Step 2
-
Add description like Wireguard Peer #1
-
Uncheck Dynamic Endpoint
-
Enter the information of the generated peer config from Step 3
** For Endpoint enter the Endpoint IP
** Keep Alive: 25
** Public Key: from generated Config output in Step 3,
** Allowed IPs: 0.0.0.0/0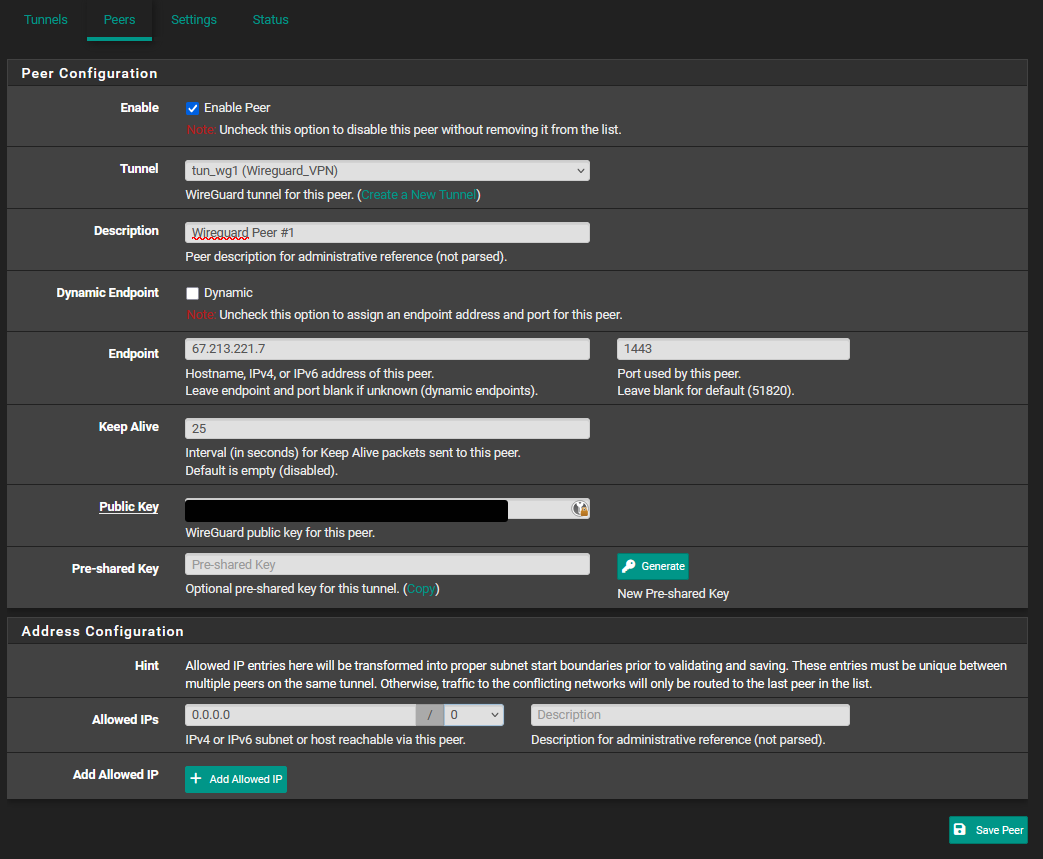
-
Click on Save Peer and Apply Changes
-
Navigate to VPN > WireGuard > Settings
-
Check Enable Wireguard
-
Click Save
4. Verify tunnel
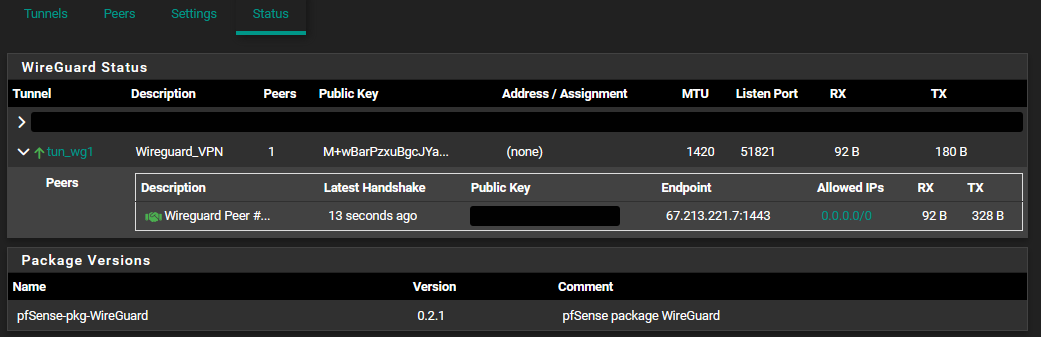
Go to VPN > WireGuard > Status
!! At this point the handshake of the tunnel must be successful. Otherwise the config is not correct !!
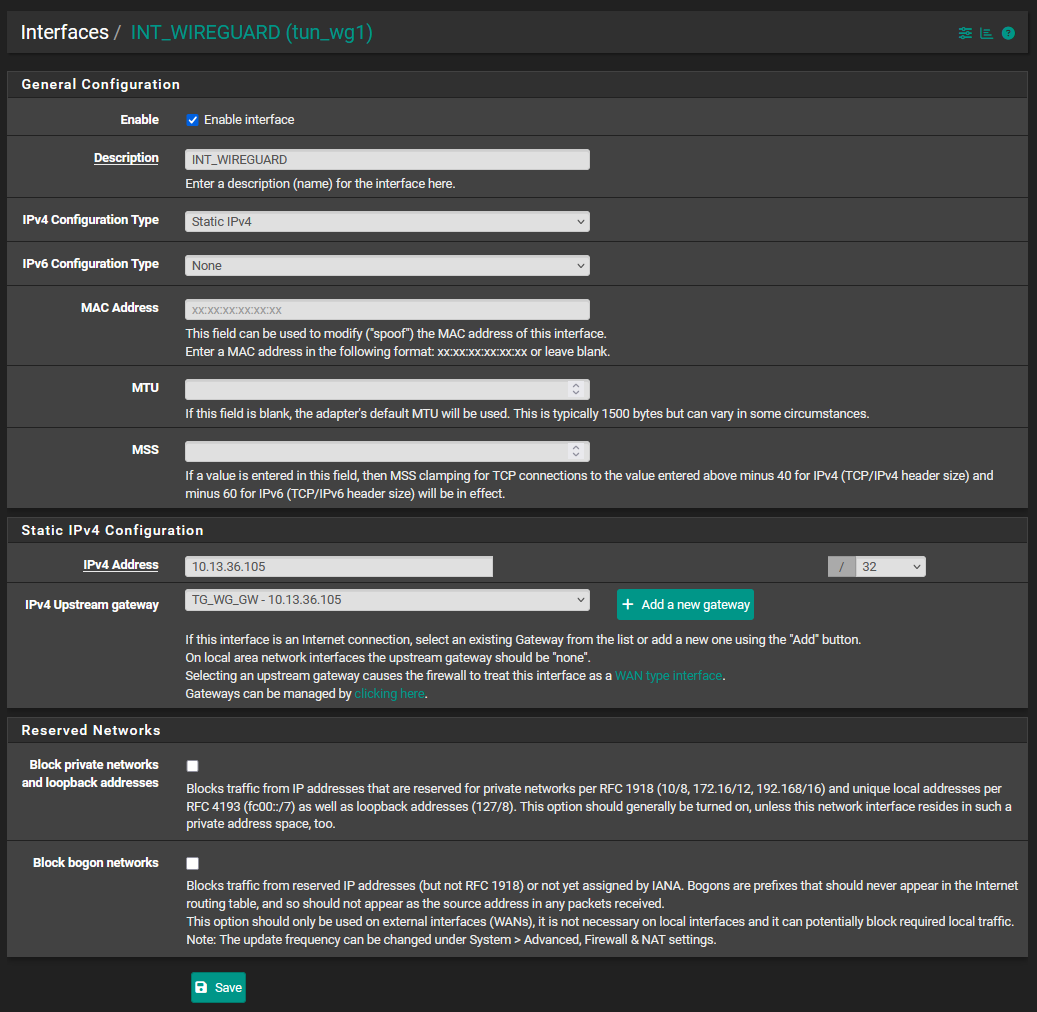
5. Interface Assignment
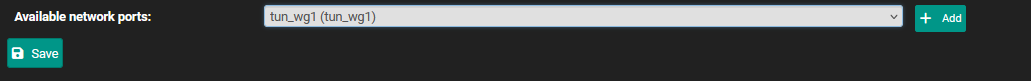
Go to Interfaces > Interface Assignments and click the + Add button beside Available networks ports: tun_wg0. The interface becomes OPT1 (if you have already other interfaces defined, the naming might be slightly different)
-
Click the Save button.
-
Click the OPTx interface name
-
Check Enable interface
-
Change description from OPTx to INT_WIREGUARD
-
IPv4 Configuration Type: static IPv4
-
IPv6 Configuration Type: None (in my case. If you have a IPv6 config, select IPv6)
-
Static IPv4 Configuration:
-- IPv4 Address: enter the IP address from the tunnel config that was generated in Step 3: 10.13.36.105 with the subnetmask 32
-- click on + Add a new gateway
-- In the window: Check Default gateway , Change the Gateway name to TG_WG_GW, Gateway IPv4: this is the SAME ip address entered in the previous window: 10.13.36.105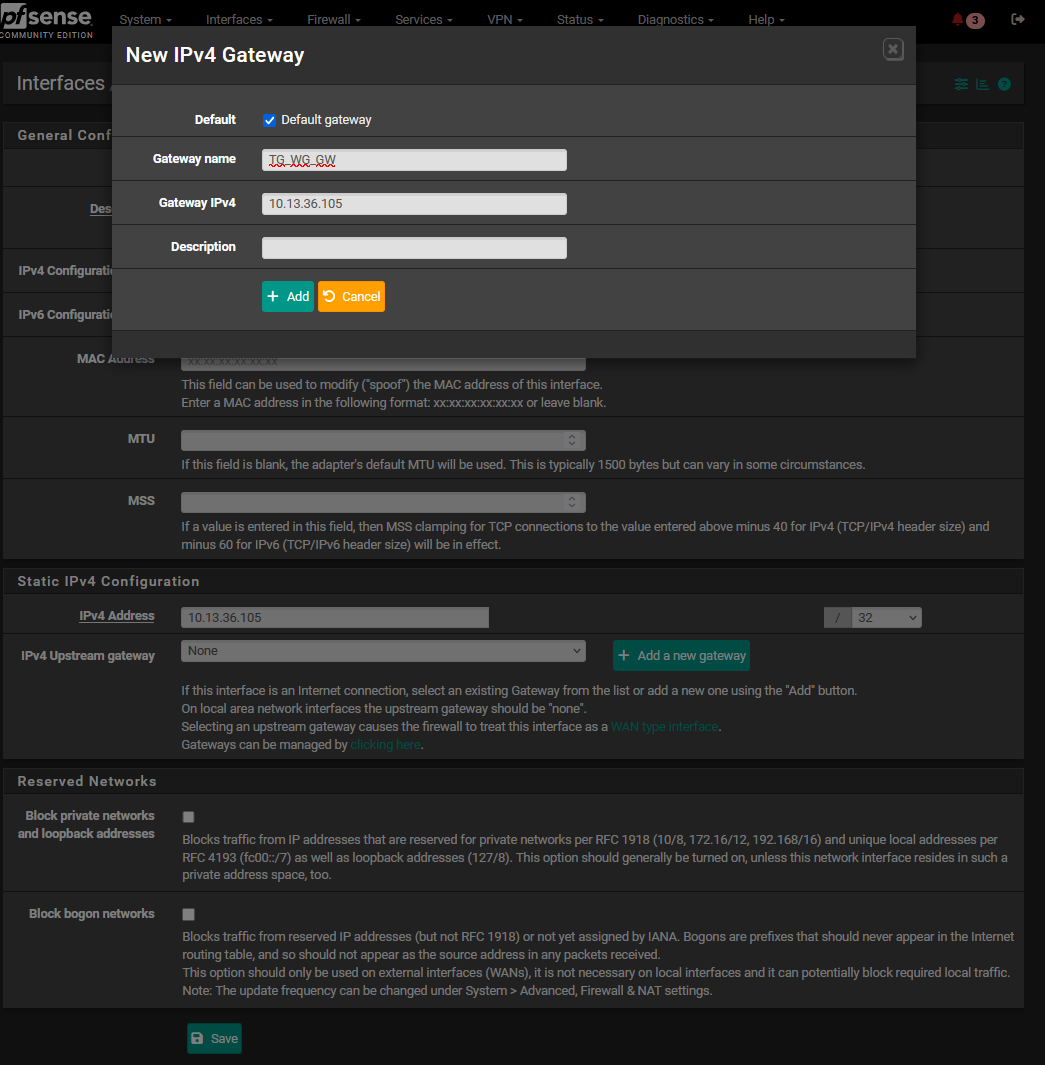
-
Click on Add
-
Set MSS to 1420
This is a point where I am not really sure about. There are many values mentioned as recommendations. Personally I left the MSS field empty and everything works fine so far. Christian McDonald, the maintainer of the wireguard package for pfSense puts 1420 in one of his videos (pfSense WireGuard Guide Series 001 - Mullvad Failover, time stamp 17:05) -
Click Save and then Apply Changes
6. NAT
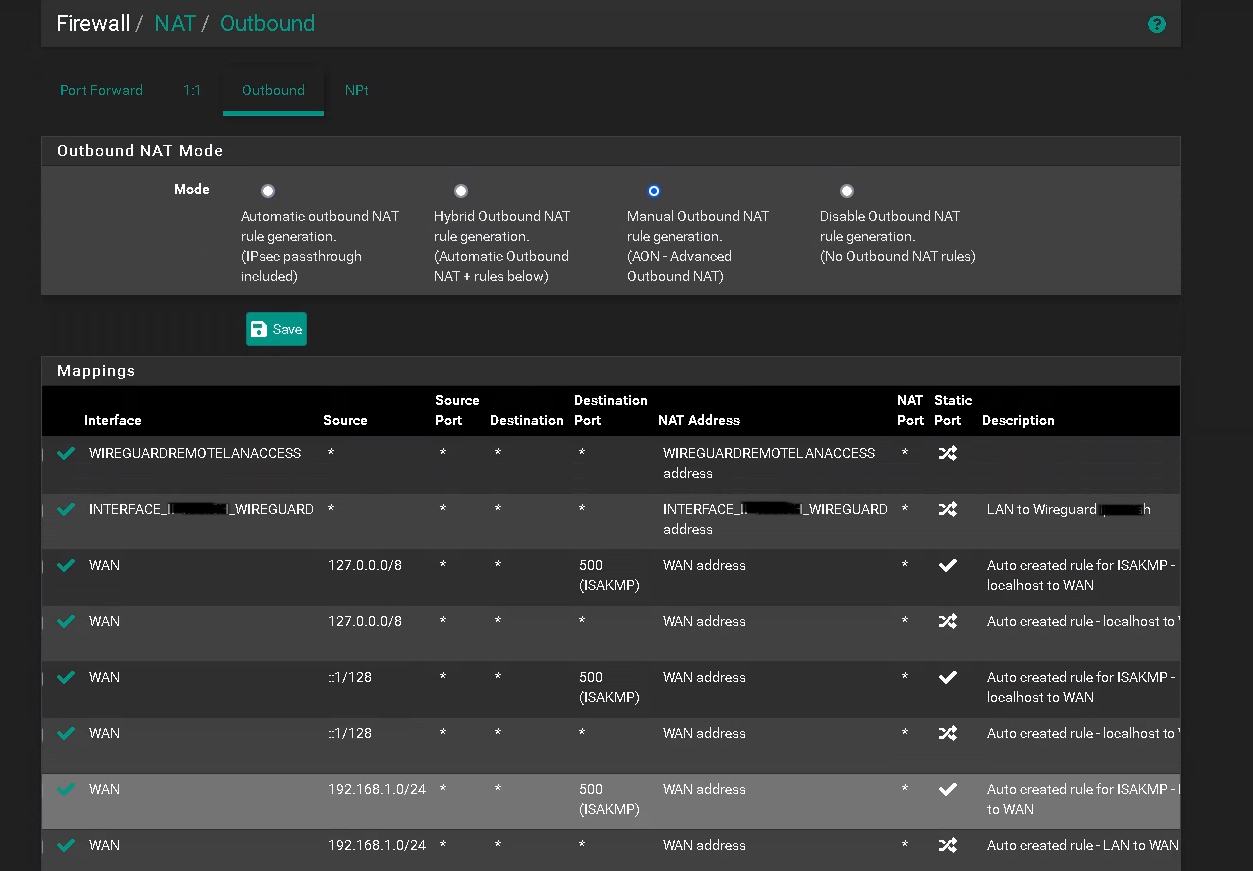
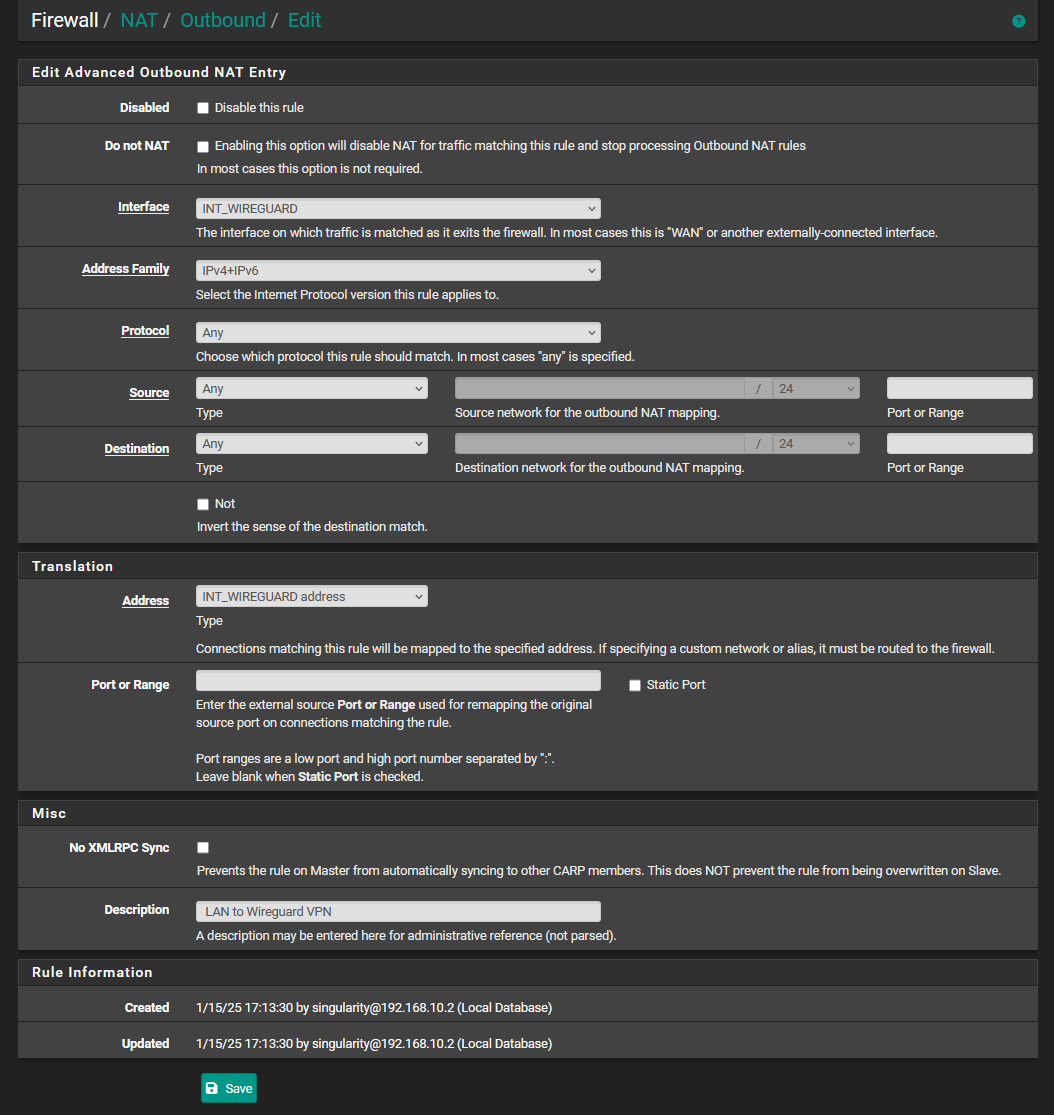
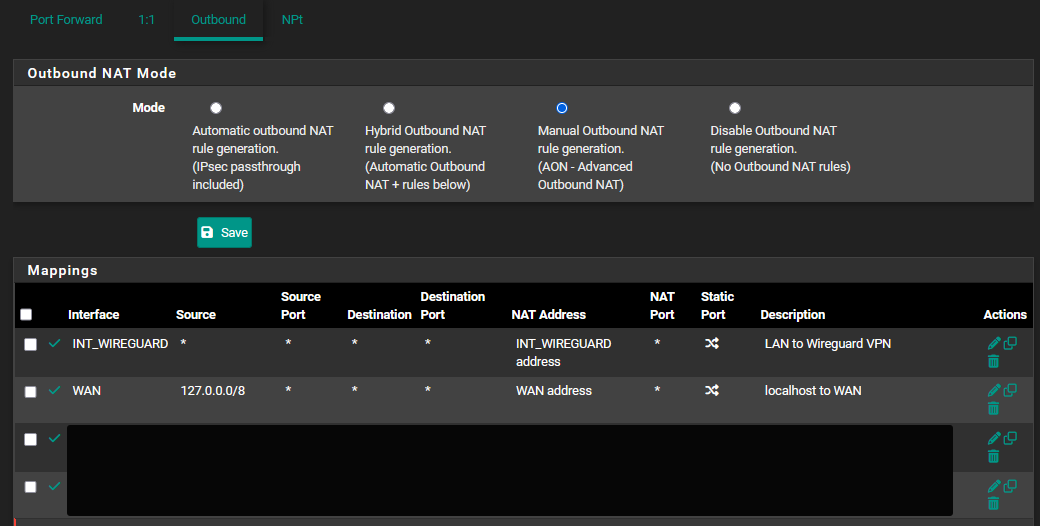
- Navigate to Firewall > NAT > Outbound and ensure that Manual Outbound NAT is selected
- Click Add (top) to add a rule for your local network subnet (Source) at the top. In case you have more subnets (sources), you can add a rule for each source or you just create a subnet that big so that all your sources are included.
- Change Interface to INT_WIREGUARD .
- Change Translation > Address to INT_WIREGUARD
- Edit description to mention the VPN, like LAN to Wireguard VPN
- Click the Save button and click the Apply Changes button.
- Disable all other rules containing with WAN in the Interface column. Only keep the rule with source 127.0.0.1. This will ensure that traffic does not leak if the VPN tunnel accidentally goes down.
- In many cases the auto-generated NAT rules (for example, the ones containing port “500 ISAKMP”) can be disabled. Try cleaning up those rules BEFORE you start with this guide
- Click the Apply Changes button.
7. RULES
The goal is now to ensure that the traffic only uses the VPN tunnel and does not leak via the any other interface. Here you have 2 options:
- Option 1: Use the Default Gateway (for example, System > Routing > Default gateway IPv4).
I chose this option as I have multiple interfaces and don’t want to create a rule for each and every one. By setting the default gateway and not working with gateway groups, it is ensured that the traffic only goes through the VPN tunnel (= default gateway). This step is implemented in Step 10 - Option 2: Define rules for every interface (for example, Firewall > Rules > LAN)
** Navigate to Firewall > Rules > LAN, click the Add (top) button and set the following:
** Action: Pass
** Interface: LAN
** Address Family: IPv4
** Protocol: Any
** Source: LAN subnets
** Click Advanced Options > Display Advanced and scroll down to Gateway and set it to the VPN gateway TG_WG_GW
** Click the Save button and click the Apply Changes button.
8. Kill Switch (optional)
The kill switch ensures that no traffic is allowed through any other gateway then the Wireguard tunnel. It is essential that the ‘Block’ rule is below the ‘Allow' rule.
In my case, I did not configure this, as I need certain traffic not going through the Wireguard tunnel.
Navigate to Firewall > Rules > Floating, click on the Add (bottom) button and create the rule to reject all traffic on WAN interface:
- Action: Reject
- Quick: Checked
- Interface: WAN
- Direction: Any
- Address Family: IPv4
- Protocol: Any
- Description: [FL] Reject all WAN traffic
- (I use the [FL] prefix as this indicates a ‘floating rule’ which makes troubleshooting easier)
- Save
- Click on the Add (top) button again and create another rule to allow the traffic from WAN interface to VPN server:
- Action: Pass
- Quick: Checked
- Interface: WAN
- Direction: Any
- Address Family: IPv4
- Protocol: Any
- Destination > Single host or alias > <IP of Wireguard server> (Step 3)
- Description: Allow traffic to VPN server
- Save
- Ensure that ‘Reject’ rule resides below the ‘Allow’ one, otherwise drag it down manually
- Click Save and Apply Changes
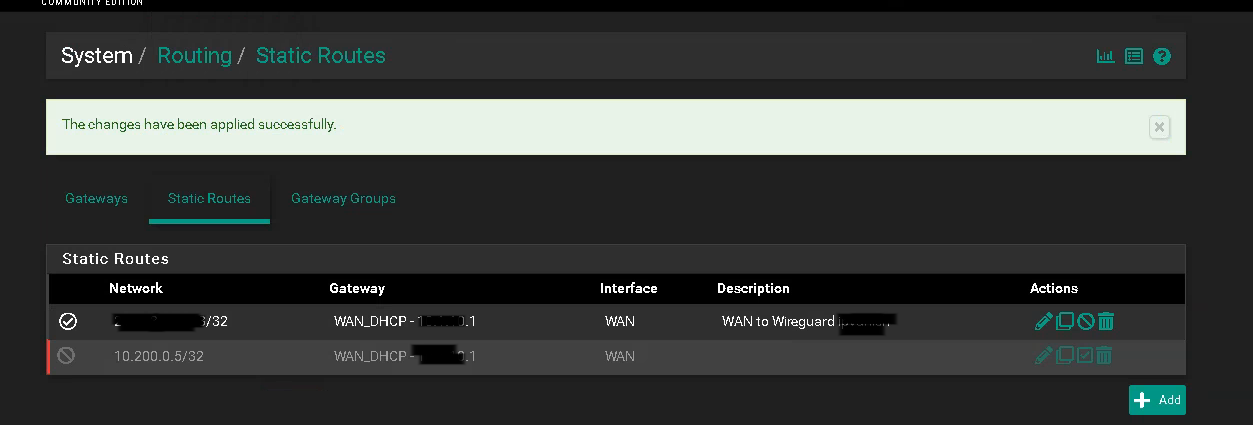
9. Static Routing
Navigate to System > Routing > Static Routes
Click the Add button and configure the routes as follows:
Destination network: The IP address of the Wireguard server <IP of VPN server> (Step 3)
Gateway: WAN Gateway
Description: WAN to Wireguard VPN
Click Save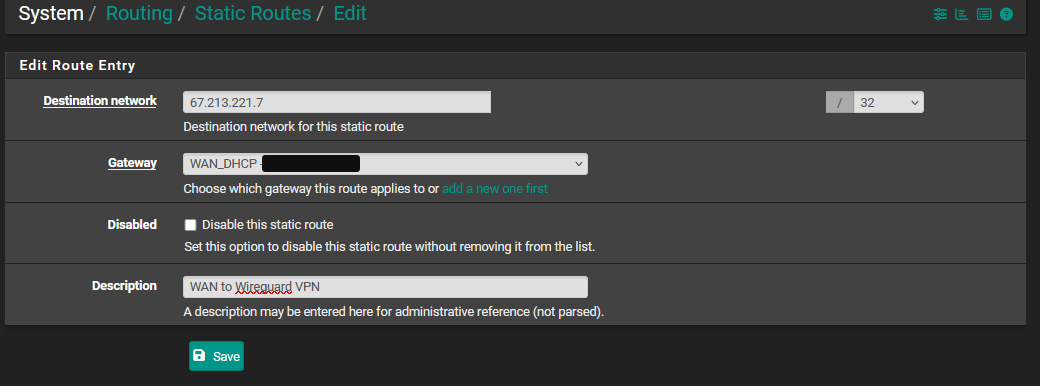
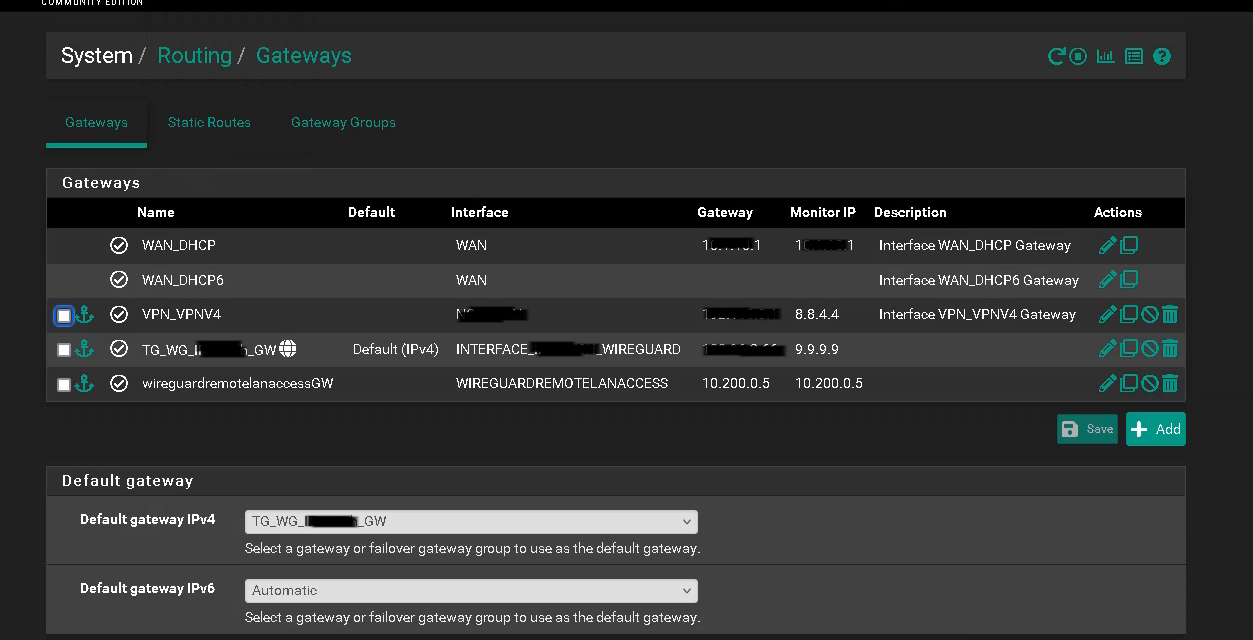
10. Default Gateway
Navigate to System > Routing > Gateways tab and set Default gateway IPv4 to TG_WG_GW
Click Save and Apply changes.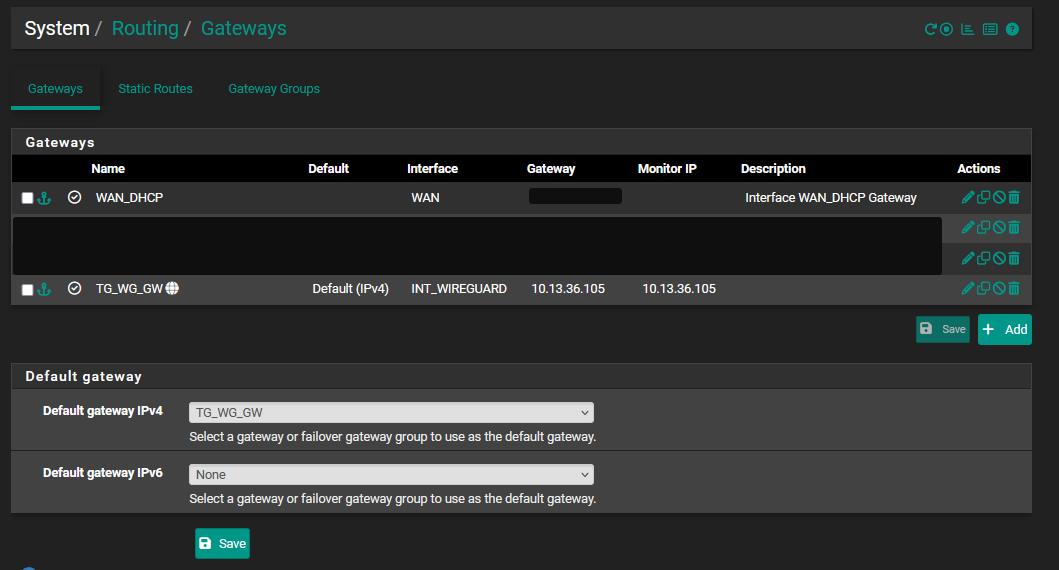
If you intend to setup multiple VPN tunnels (for example to different VPN locations), static routing needs to be defined for EVERY VPN tunnel!
!! At this point your Wireguard connection should be working !!
DNS (optional)
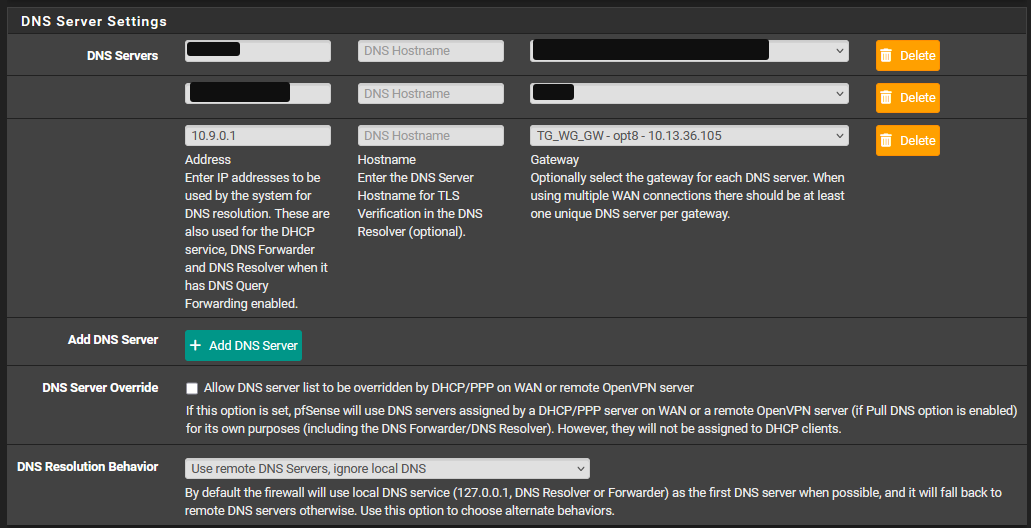
11. DNS Server
I recommend to adjust the DNS settings as well. Most VPN provider also provide different DNS server options (no blocking, family filter, etc.)
- Navigate to System > General Setup > DNS and set the DNS Servers > Address to one of the DNS server options provided by your VPN provider
- Set the Gateway to the Wireguard gateway TG_WG_GW
- Uncheck DNS Server Override
- Select Use remote DNS server, ignore local DNS
- Click the Save button.
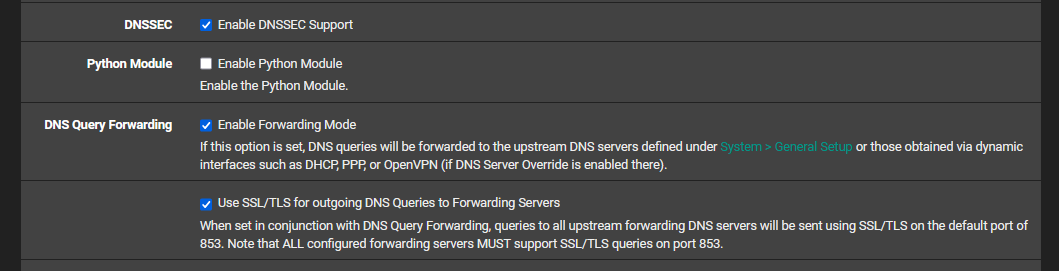
12. DNS Resolver
- Navigate to Services > DNS Resolver and check Enable
- Have Enable DNSSEC checked.
- Check Enable Forwarding Mode
- Click the Save and Apply Changes
Verification
_
The next step is the most important one! You need to verify that everything is working as expected.13. Check you public IP address:
This can be done in command-line or via a website, for exmaple: IP Chicken
Expected result: <IP of VPN server>from Step 3user@pfsense:~$ curl -4 ifconfig.co 67.213.221.7 user@pfsense:~$14. Verify correct routing via default gateway
- Open a command-line and start a constant ping and let it run (for example, Google DNS): ping -t 9.9.9.9
- While the ping continues, go to System > Routing and change the Default gateway IPv4 from TG_WG_GW to the WAN interface
- Expected result: the ping has to run into a time-out because all the traffic is only allowed through the Wireguard gateway. If your ping continues, check your firewall rules and NAT Outbound rules
- Switch back from WAN interface to TG_WG_GW
- Expected result: the ping should be resumed
15. Reboot
- Save your pfSense config via Diagnostics > Backup & Restore
- Reboot pfSense to ensure that the config is REALLY working. I had many situations in the past where only a reboot revealed that something was not correctly configured/working.
For example, the wireguard interface did not come up correctly after a reboot (see ‘Troubleshooting’ below)
Troubleshooting / Lessons learnt
As stated in the introduction, I am using a setup with multiple VPN tunnels in a mixed-mode of OpenVPN and Wireguard.
Here I encountered some issues which I'd like to mention here.A. MSS value
The MSS value is still a mystery to me. If your Wireguard tunnel was successfully verified (Step 4), but you cannot ping or DNS is not working, it might be a try to change the MSS value (1380, 1412, 1420 are common values).
B. OpenVPN tunnels:
- Check Don't pull routes and Don't add/remove routes for EVERY OpenVPN tunnel in VPN > OpenVPN > Clients
- Otherwise switching the default gateway is inconsistent and packets are send via other OpenVPN tunnels even if a different default gateway is selected in System > Routing > Gateways. This is especially relevant for Step 14
C. Multiple VPN Gateways
In case you want to setup multiple VPN tunnels, keep in mind:
- For every tunnel a static route (Step 9) is required !
- For every tunnel a NAT Outbound rule (Step 6) is required !
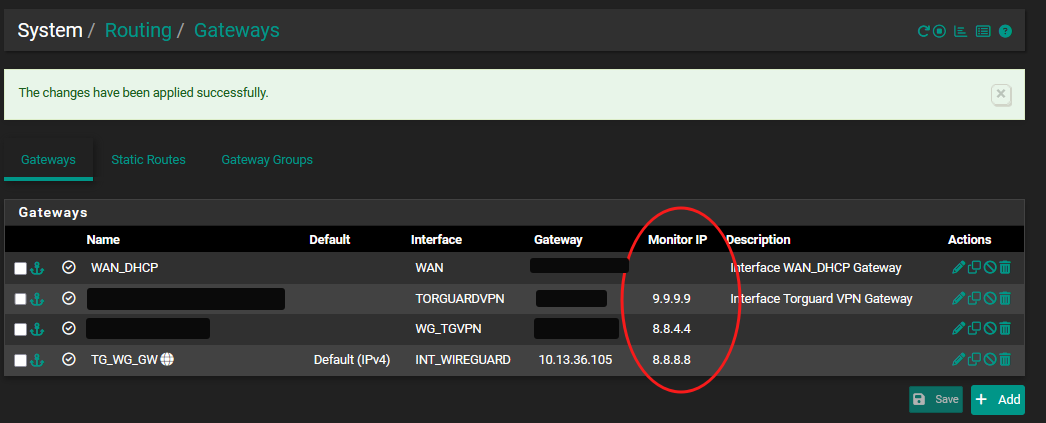
D. Monitoring of Gateways
For monitoring the VPN gateways, I use IPs of public available DNS servers. Of course, I just could use the IP of the VPN endpoint/GW, but by using DNS servers I can ensure that traffic is going beyond the VPN gateway.
Usuals suspects of DNS servers are: 8.8.8.8, 8.8.4.4, 9.9.9.9, 1.1.1.1 (Google, Quad9, Cloudfare).
In order to have a consistent gateway monitoring:- Check Do not add static routes for gateway monitor IP addresses in System > Advanced > Miscellaneous
- Otherwise monitoring VPN Gateways gets very fuzzy und not deterministic, i.e. the gateway selection becomes very vague and inconsistent.
- Gateway monitoring in general can be tricky with the service dpinger
Sometimes dpinger needs to be restarted in order to provide the correct gateway status - especially after rebooting pfSense
Solution:
** Install cron and watchdog
** Add the service wireguard to watchdog
** Add to cron @reboot with the command sleep 45 && /usr/local/sbin/pfSsh.php playback svc restart dpinger
References:
IVPN - pfSense WireGuard Setup Guide/
OpenVPN + WireGuard breaking DNS resolver. [SOLVED]
Is it possible to resolve DNS via WireGuard interfaces?
How to Setup the Latest pfSense Wireguard Client -
L LaUs3r referenced this topic on
-
firts off, Great tutorial!
Now for the issue I have. When the default gateway is set to wireguard tunnel interface, I can't access my LAN. I cam't seem to figure out the firewall rules (assuming it blocks the connection). Not much on the logs either.
Do you have any idea of whats is going on?
-
@philjoyal this is the tutorial I have follow for my lan access.
https://www.wundertech.net/how-to-set-up-wireguard-on-pfsense/ -
Hi @philjoyal,
fist of all, your scenario is a different one as described here in this tutorial!
this tutorial: pfSense acts as Wireguard CLIENT that connects to the Wireguard SERVER of the VPN provider
your scenarion: pfSense acts as Wireguard SERVER to which you can connect with Wireguard clients (for example, on your smartphone).
In order for your Wireguard clients to be able to access the LAN, you need to define firewall rules to allow traffic from the incoming Wireguard peers (10.200.0.5/24) to your LAN.
In the tutorial you used, the Wireguard interface is called "WG_VPN". You will find in Firewall > Rules the same name. Here you need to allow "WG_VPN subnets" (source) to your LAN (destination). -
@LaUs3r thank you for your reply. In fact my pfsense should be a client and a server. Client for vpn provider and server for my client to access my lan. My pfsense have 2 wireguard tunnels (on different port and different vinterface): client and server. My clients can connect to my lan (if wan is set as default gateway-->routing) and pfsense can connect as client for my vpn provider (default gateway set to vpn_provider) but not at the same time. my clients cant connect to lan tunnel if pfsense is connected as a client for vpn_provider.
-
@philjoyal, do you allow NAT Outbound traffic for your Wireguard Client addresses via the Wireguard Gateway?
In Firewall > NAT > outbound you should have something like:
Interface................Source..................NAT Address
WG_VPN............10.200.0.5/24...............WG_VPNCan you maybe post a picture of your NAT Outbound rules?
-
-
This post is deleted! -
You probably need to add a static route for your WireGuard Remote Clients VPN subnet (10.200.0.5) to use the WireGuard ISP VPN (WG_VPN)
-
-
@LaUs3r Doesn't seems to work either
-
@philjoyal but that's not showing a static route. You need to add one in the routing tab.
Check out this guide: https://jarrodstech.net/fix-pfsense-remote-wireguard-vpn-clients-access-to-wireguard-site-to-site-vpn/ -
@LaUs3r the static route is shown in the 3rd screenshot
-
P philjoyal referenced this topic on
-
I found this guide years ago. This was back before there were any pfsense VPN guides on the internet. The site has since gone down, but is still on the WayBackMachine. There is a brief explanation of the Wireguard MTU and MSS and how they relate to each other.
DevinMadeThat - Guide: Adding Proton VPN with WireGuard to pfSense
Excerpt:
- MTU: 1420
Maximum Transmission Unit: Because of WireGuard's overhead, you want to set it for 1420 - MSS: 1420
Maximum Segment Size: You want this clamped to 1380, but it's calculated minus 40 (for 40 bytes of v4 header) from whatever you type here. So you want to enter 1420 (1420-40=1380)
- MTU: 1420
-
This was a great post to get me started with a dual VPN solution - thanks so much for the write up @LaUs3r . For my use case I desire a wireguard primary interface and a failover wireguard connection if primary goes down or has high latency. I finally got both set up, handshaking and passing traffic.
I'm probably a bit over my head here and did a lot of trial and error to get things going so sorry if stupid question but once thing still isn't working for me correctly. wg0 and wg1 are both passing traffic like a round robin load balance situation - each successive connection alternates which one is being used - but that isn't the behavior I want.
I want to only send traffic to wg1 if wg0 fails (or gets high letency and packet loss). I created a gateway for each and a gateway group. In the gw group I have wg0 as Tier 1 and wg1 as Tier 2 but they seem to be treated equal. I also created an interface group for my NAT rules that contains VPN1(wg0) and VPN2(wg1)
I think I am missing what rules/process steers the traffic to the gateway group and how the NAT works and maybe somehow I'm sending traffic to both gateways ignoring the group tier and priority.
Any ideas where I should look in more detail to figure this out?
TIA
-
I tried following your guide to set up the Surfshark WireGuard server configuration in pfSense as default gateway, but I got stuck at the static routes step.
In my case, the endpoint isn’t a numeric IP — it’s listed as us-bna.prod.surfshark.com. How should I add this to the static routes?
In my configuration:
Endpoint: us-bna.prod.surfshark.com
Address: 10.14.0.2/16
So what exactly should I enter in the static routes? after switching the default gateway from WAN_DHCP to the WireGuard VPN my Interent doesn't work so adding static routes is mandotary
(Im using inside vmware)
-
@subhan2k said in [Guide] Setup a wireguard tunnel to VPN provider (multiple VPN tunnel setup):
I tried following your guide to set up the Surfshark WireGuard server configuration in pfSense as default gateway, but I got stuck at the static routes step.
In my case, the endpoint isn’t a numeric IP — it’s listed as us-bna.prod.surfshark.com. How should I add this to the static routes?
In my configuration:
Endpoint: us-bna.prod.surfshark.com
Address: 10.14.0.2/16
So what exactly should I enter in the static routes? after switching the default gateway from WAN_DHCP to the WireGuard VPN my Interent doesn't work so adding static routes is mandotary
(Im using inside vmware)
nslookup us-bna.prod.surfshark.com Server: 127.0.0.53 Address: 127.0.0.53#53 Non-authoritative answer: Name: us-bna.prod.surfshark.com Address: 82.26.162.48 Name: us-bna.prod.surfshark.com Address: 82.26.162.53That should do it

Just take 1 of the 2.And in general, don't use domain names but only IP. Before you start, choose 1 of the 2 IPs and use it for the whole process
-
@LaUs3r ok I use this 1 IP It works initially, but after every restart the handshake fails. I believe Surfshark assigns a new dynamic IP each time, and even when I update that IP in the peer, static route, and firewall rule, the handshake still doesn’t work because it needs a temporary connection (like WAN) to establish first.
-
do you have a guide for setting up a Multi-Hop VPN inside pfSense (running on VMware)? Right now, I have an extra server running OpenVPN, and I want to route it through a Multi-Hop setup. Do you know how to do it? I’ve also heard that Multi-Hop setups are prone to more leaks, so it needs to be configured properly.
-
@subhan2k , SurfShark offers some tutorials how to set up wireguard on openwrt, etc.
https://support.surfshark.com/hc/en-us/articles/7161303618834-How-to-set-up-WireGuard-on-a-DD-WRT-router#01HJ8AJJW5SRFKFRBQF9P550Q7
How does the config look like with regards to the server location? I mean there must be some specific IP for the server be included. Maybe it makes more sense to use this.
For example, I use TorGuard: when I have a config file created for us.torguard.com, I get an IP in the config and not the domain name