pfsense dns lookup (netgate.com) every 30 seconds
-
Hi all,
After setting up pi-hole on my network I noticed that my pfsense appliance is doing a DNS lookup for "netgate.com" every 30 seconds and to two others less frequently (pfsense-plus-pkg00.atx.netgate.com and ews.netgate.com) though still over 4K times a day, and thus making it the highest consumer of DNS requests...
Is there a reason for this? Can this be disabled (in some form)? I find this quite excessive.
Thanks,
Bernard. -
@bdeprez well not a fan of ttl set so low.
;; ANSWER SECTION: netgate.com. 60 IN A 199.60.103.4 netgate.com. 60 IN A 199.60.103.104the ews one has a more realistic 3600, but the atx one is also really low as well
pkg00.atx.netgate.com. 300 IN A 208.123.73.207Not sure why with a ttl you would be doing a query every 30 seconds. every 60 ok sure.. But you should cache that for the ttl - so your forwarding would be my guess and your never pulling the full ttl from the actual NS for netgate.com
Do you have the page webgui page open? Not sure why it would need to talk to these sites all that often - check for updates sure, etc. but I wouldn't think it all that often unless you have the page open or something.
Like I said I am not a fan of sort ttls, I have min ttl set to 3600 in unbound for me.. Even my clients ask pihole, it forwards to unbound on pfsense, unbound then resolves.. So anything unbound looks up the min ttl would be 3600 seconds, so pihole will cache it for the 3600 seconds.
-
@johnpoz - here's a screenshot:
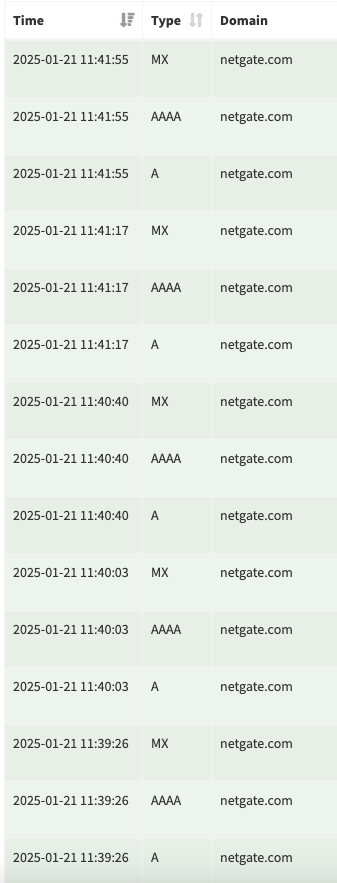
those are the most frequent ones - any way I can stop this?
I didn't have the pfsense GUI open at all...While I didn't have the pfsense GUI open at all, I disabled the "update check on dashboard" and that seems to have miraculously stopped the other DNS lookups... will keep an eye on that as well.
-
@bdeprez you sure those are being requested by pfsense itself - not sure why it would need to lookup MX? Notications would be the only reason I would think it would look up mx, or there is some package that does a mailing of reports.
You can't stop both the AAAA and A - I run into that all the time - hey stupid client why are you asking for AAAA, you do not have a IPv6 address ;).. What are the odds your going to be able to talk to netgate.com via ipv6 if you don't have a gateway or route and all you have is link-local? There should be a easy way to tell the client/application, hey don't do AAAA dns. You can turn that off in firefox for example.
The mx records have a ttl of 3600.. If I had to guess whatever is kicking those off just isn't using cache at all. Lots of iot devices do this as well - with no local cache for dns, any time they want to talk to something they have to do a dns query.
You might be able to quiet down the dns queries by changing the way your doing dns.. Where does pfsense point to for dns - directly to your pihole in general, and your not asking loopback 127.0.0.1..
I don't see any such queries in pihole, because my pfsense just asks itself, loopback 127.0.0.1.. It then resolves.. My clients all point to pihole for dns - who then forwards to unbound.
There really is little reason to have unbound point to pihole for dns.. What would pfsense be doing that you would want to filter with some block dns list?
If your pihole is doing your local dns and you want to be able to look those up from pfsense for say resolving IPs in your firewall log or via aliases, etc. you could setup a conditional forward for the domain, and or reverse zone your using to ask pihole for those. But pfsense looking up something external would never need to ask your pihole.
-
@johnpoz You're right, the pfsense box isn't the one I'm worried about so that's exactly what I just did - I pointed the pfsense to 1.1.1.1 for it's own DNS and I'm done

Now to conquer the other 80someting thousand...
Thanks for your help, John. -
@bdeprez so your not running unbound or dnsmasq on unbound at all?
One thing bad about just pointing pfsense to some outside dns is you can't resolve any local resources.. you can't put a fqdn of a local resource in your aliases, you can't resolve ptr of local IPs in your firewall by just clicking the little i

-
@bdeprez said in pfsense dns lookup (netgate.com) every 30 seconds:
Is there a reason for this?
As said above : a TTL for a domain zone (whatever zone), I still don't know why that would be needed (exception : mega zones like Microsoft.com google.com facebook.com etc - and, afaik, netgate.com isn't that big as a company - or, for example, load scheduling over en entire server park)
But as we all learn on this forum, people do things with DNS that can't be explained by reasoning.It gets even better : while posting here on the forum, I used - that is, my browser is, polling forum.netgate.com constantly. Exactly what you found. Guess what, "forum.netgate.com" also has a 60 sec TTL : so
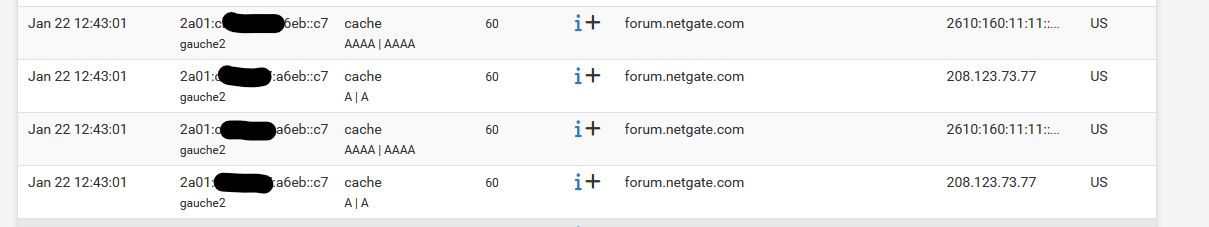
All request are received, and answered out of the (local !) unbound cache.
Not sure why it asks for a IPv4. I used IPv6, and IPv4 exists as a fallback
But ... I have this option checked :
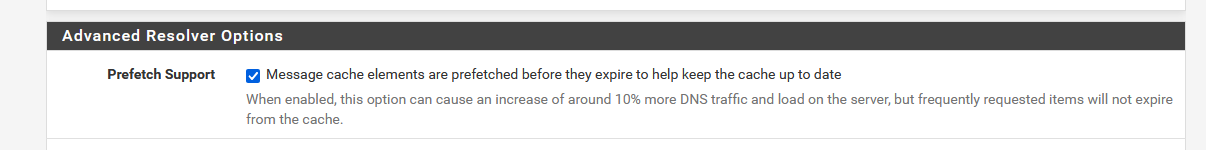
which does what it says that it does (or, probably better : what I make of it ^^ )
If an already resolved domain name, now in the resolver cache, starts to reach a zero TTL unbound will re-resolve automatically so it can answer a requesting client always right away, without going out and do the entire resolve process 'while I'm waiting (the give to take 100 ( ? ? msec this will take).So, I, the admin, was asking for it.
As always, to see stupid things you need to be two : the one who creates them, and the other, who sees them.So, ones a "forum.netgate.com" resolved host name exists in my local unbound resolver cache, it will stay there, and get refreshed every TTL-10% = 54 seconds.
Let's contact "netgate.com", and ask if they can lower that 60 to 1 seconds, because "why not ?!".
Their domain name servers will get smacked with requests ...Btw : No, pfSEnse isn't polling netgate.com for "telemetry" reasons.
pfSenses wants to resolves "netgate.com" a couple of time per day ( ? ) while checking for possible updates and some more reasons.