Issue with multiple P2 phases using NAT/BINAT on pfSense
-
I see the following log error:
14[CFG] <con9|130509> config: 10.45.213.42/32|/0, received: 10.45.5.163/32|/0 => no match
-
@vdjurdjevic
Are both p2 configured at the remote site as well? -
Unfortunately, I don't have control over the gateway on the remote side of the tunnel.
They sent me the following configurations for the ACL
access-list Vakel_Tunnel line 1 extended permit ip host 10.45.5.163 host 10.66.88.1
access-list Vakel_Tunnel line 2 extended permit ip host 10.45.213.42 host 10.66.88.3
The tunnel existed previously with P2_1 and it is functional.
The problems occur when I add P2_2. It is not functional.
-
@vdjurdjevic
It seems, that there is no proper ACL for the second p2, but need to check the whole handshake section of the log to get sure.I don't think, that there is a limitation on p2 numbers with BINAT. To ensure, just disable the first and check if the other come up then.
-
When I disable P2_1, which is functional, P2_2 does not come up.
-
@vdjurdjevic
So as expected, the second p2 doesn't work without an impact of another as well.
So I guess, there is something configured wrong at the remote site. -
@viragomann Tnank You
-
I tried to replicate the configuration between two pFsense instances, and I encountered the following:
- When using different NAT/BINAT addresses, only the first SA works.
- When I use the same NAT/BINAT address, everything works perfectly. I assume this is because the network being NATed is the same for both P2s.
- And finally, in the IPsec status, only a single summary connection is visible instead of two.
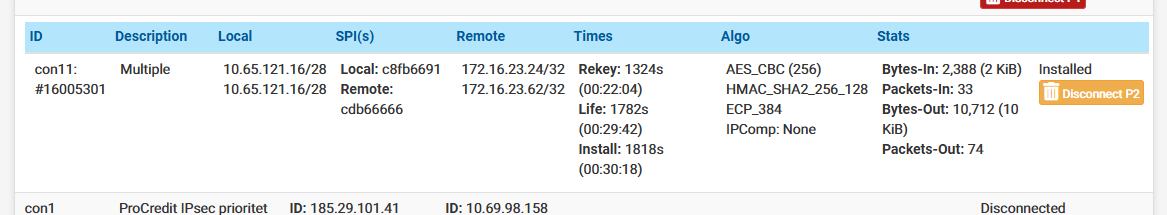
-
@vdjurdjevic said in Issue with multiple P2 phases using NAT/BINAT on pfSense:
When I use the same NAT/BINAT address, everything works perfectly. I assume this is because the network being NATed is the same for both P2s.
Ah yeah, good catch!
I can imagine, that it would be possible if you use different local addresses (single IPs instead of DMZ).
-
@viragomann Yes, I think so too.