Port Forward is Ignored
-
I am aware this will be something I'm doing wrong.
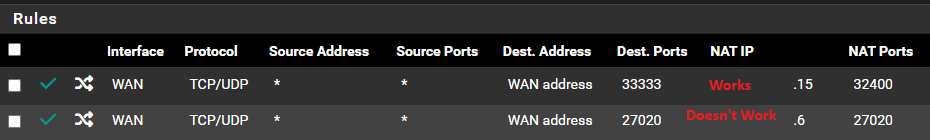
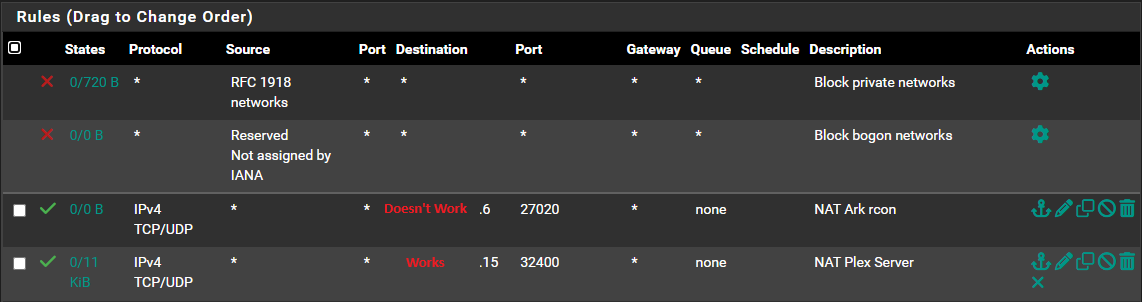
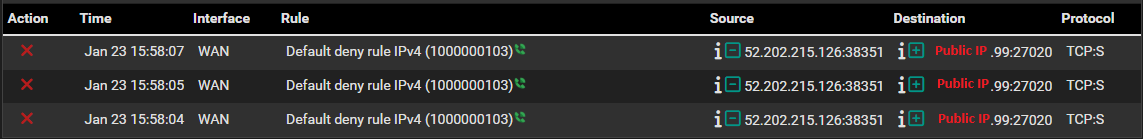
I copied a working Port Forward (33333->32400) and changed the IP and ports to be (27020->27020), but it's not working. Changing it to (27270->27020) didn't help. I'm testing from CanYouSeeMe. 33333 always succeeds and 27020 always fails. In Status -> System Logs -> Firewall the rule blocking 27020 is 'Default deny rule IPv4'. The destination listed is my public IP. I clicked the + to create an EasyRule and it's listed in Firewall -> Rules -> WAN, but the port tests still fail.
Any guidance would be appreciated.
-
@gerardshebert Copying Port Forwards is not a good idea.
Just delete the none working one and create it from scratch. -
@gerardshebert Unless those addresses on your LAN are public somehow there is no reason to obfuscate them.
Your port forward is obviously wrong somehow based on your firewall logs there..
If you can post a screenshot of the port forward setup page here that would help.. but always nice to know for me when I mess up where I did it..
-
Thank you for replying. Rebuilding the Port Forward rule from scratch did not change anything.
I tested changing the NAT IPs and ports around and discovered that successful tests follow port 33333.
I tested both rules with (33333->32400 on IP .15) and (33333->27020 on IP .6) and the port test succeeded all four times.
Both rules fail with (27020->32400) and (27020->27020). (33332->32400) and (33332->27020) also fail.So, the Port Forward rule works. The problem is I cannot add more ports to forward. I will root around and may even pay for Support on this one because I'm starting to take it personally. I'll post an update once it's fixed.
-
@gerardshebert said in Port Forward is Ignored:
Hmmm.. Looks to me like your Port forward is not taking place, if was the firewall rule would show evaluations. But it shows 0/0 and no you have no rules that allow 27020 so yeah your default deny on want would trigger. Because your wan rule is to allow to your .6 address. But if not translated with your port forward then no that rule would never trigger.
So you have to figure out why the port forward is not being applied..
Doesn't matter what port you want to send it too.. If it doesn't actually apply then yeah your default deny will block traffic to your .6 address.
Look in logs.. when you apply a port forward you should see it applied..
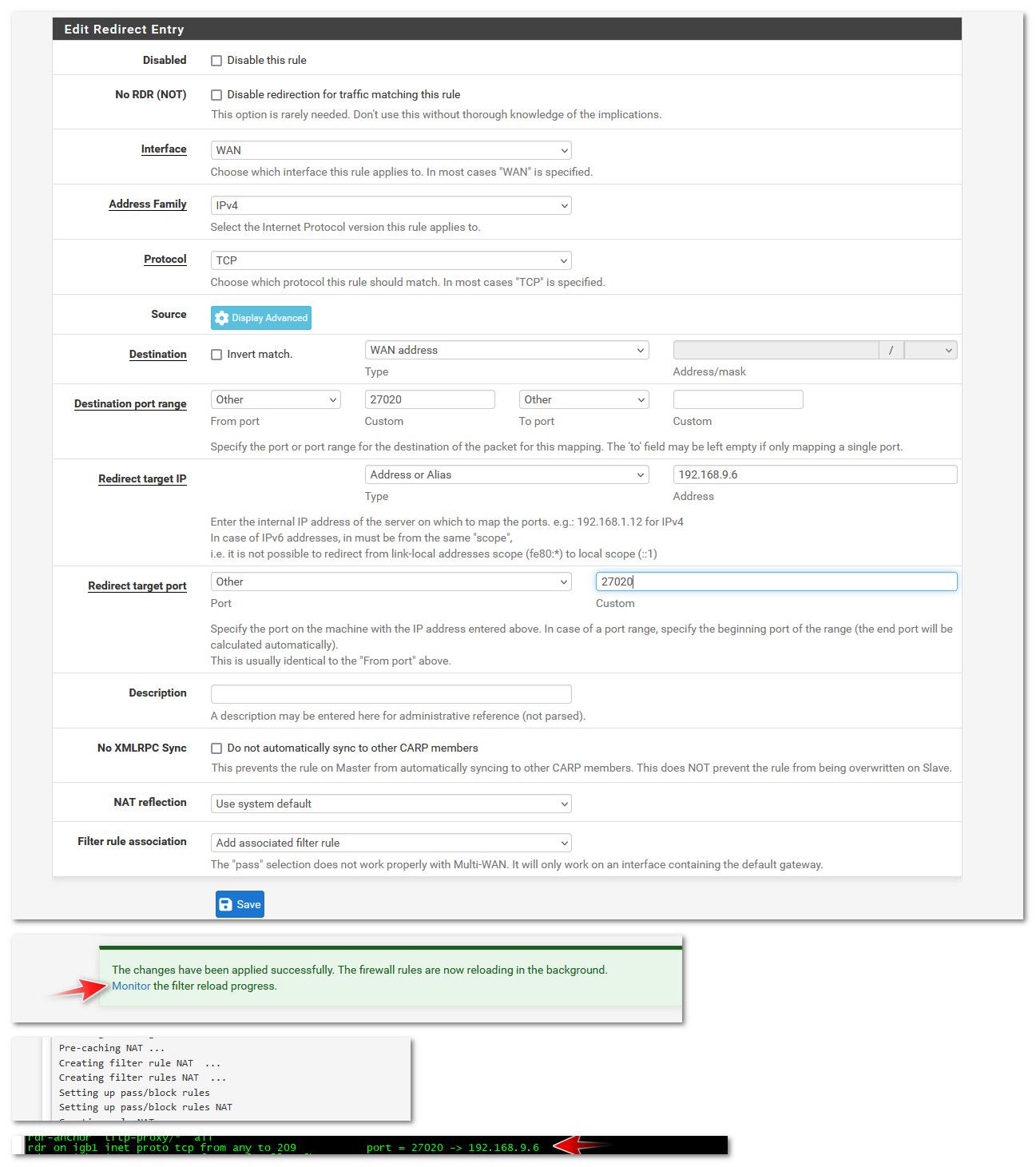
See that last image there - that is the rule being viewed with
pfctl -sn
https://docs.netgate.com/pfsense/en/latest/firewall/pf-ruleset.html
edit: I would put a description on the rule - and then make sure you do a filter reload, to see it process it
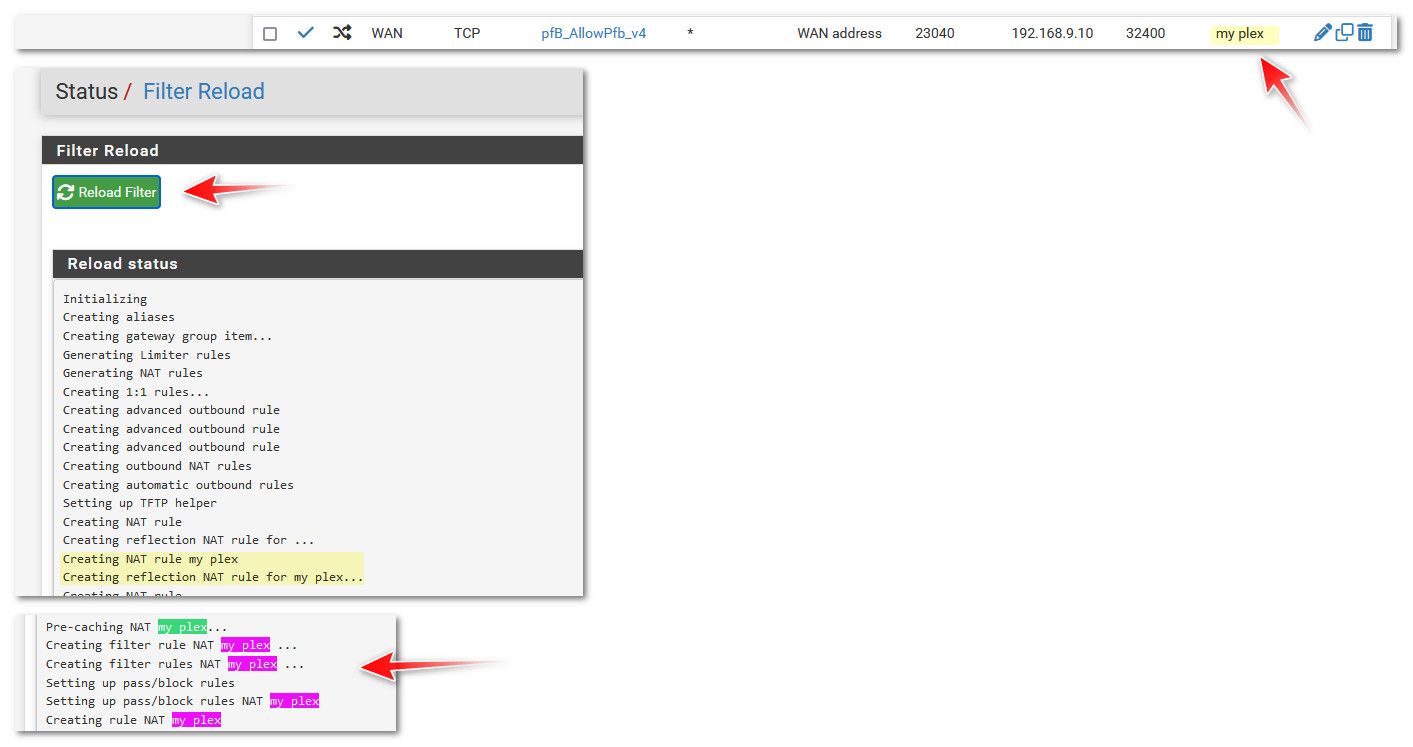
And would be good to see what is actually loaded via that pfctl -sn command
-
SOLVED!!
Thanks @johnpoz your info made me re-examine the rule reload which had always shown the new rules being created, but I finally noticed the output never stated 'Done'. Instead it was stopping at:
There were error(s) loading the rules: /tmp/rules.debug:36: cannot define table pfB_Africa_v4: Cannot allocate memory - The line in question reads [36]: table <pfB_Africa_v4> persist file "/var/db/aliastables/pfB_Africa_v4.txt"
Which led me to "/topic/176932/error-tmp-rules-debug-36-cannot-define-table-pfb_pri1_v4-cannot-allocate-memory" which made me decide to uninstall pfBlockerNG which allowed the rule reload process to get to 'Done'. I uninstalled it because Africa is the first line in the list and increasing the Firewall Maximum Table Entries in System -> Advanced -> Firewall & NAT to 700000 got it as far as Europe before erroring again. Increasing the value to 1000000 took care of it, but there's nothing I'm doing that should require increasing a value to 2.5 times the default.
The moral of the story is, if the log doesn't state 'Done', the rule reload failed and nothing changed.
That pfctl -sn was very helpful too.
Thanks, everyone for helping me out.
-
@gerardshebert FWIW long ago the advice I’d read here was, if using pfBlocker, set that max to 2 million and increase if necessary.
There is also the “don’t block the world, allow your country” discussion which takes much less memory.
-
@SteveITS said in Port Forward is Ignored:
There is also the “don’t block the world, allow your country” discussion which takes much less memory.
^Exactly - I use this method.. I only want US ips and currently Belgium (family living there using my plex) - so I just allow those in my port forwards and wan rules.. This by its very nature blocks all the other ones.. No reason to load up into the tables of bad countries IP of them, all need to load is the IPs that are US and Belgium.