Block by MAC address to LAN
-
I have two LAN's - LAN1 & LAN2
I do not want certain MAC address to access LAN1. Is it possible to ALLOW or BLOCK by MAC address?
If so, how.
-
@netboy huh? Why would you think a device connected to lan1 would even be able to talk to a lan2 - those should be in different networks at layer 2 and isolated. You mean your pfsense has a built in switch and you have 2 interfaces of the switch in the same lan network?
-
@johnpoz I have two LANS - LAN1 & LAN2
i would prefer all IoT to connect to say LAN2. But sometimes my family members will connect to any LAN1 and I want to prevent it
-
@netboy if LAN1 is WiFi…change the WiFi password??
-
@michmoor
Nice Try! Don't you think I have not thought about it?They need to know both passwords as they home that connect to LAN1 and some to LAN2
-
@netboy still makes no sense.. As @michmoor mentions - are these wifi networks? What provides the wifi.. You have different APs connected to different lan ports.
You're going to have to give us more details of how you are setup - because I have no idea what your asking because it doesn't make any sense.. Are they plugging into different switches, are they connecting to different ssids..
Is pfsense providing the wifi? Or do you have APs?
-
@johnpoz said in Block by MAC address to LAN:
You're going to have to give us more details
I have two VLAN's (Kind off) say LAN1 and LAN2. It doe s not matter if the wifi is going thru an extender thru LAN1 or LAN2.
How do you BLOCK a mac address from accessing say LAN1? Why do you think this makes no sense? It makes lots of sense to me
-
@netboy said in Block by MAC address to LAN:
I have two VLAN's (Kind off) say LAN1 and LAN2.
You either have a VLAN or you don't. There is no "Kind off".
Are these LAN ports in separate vlans? Do they have different networks? For example is LAN1 192.168.1.0/24 and LAN2 is 192.168.2.0/24
These seem like bridged interfaces but again you gave no details how your set up and yes, nothing you are saying makes any sense and if it only makes sense to you then why cant you figure it out? -
Forget about VLAN's .Let me make this simple.
Is there a way to block a MAC address from a LAN (taliking wifi here) assuming the everybody knows the password?
-
@michmoor said in Block by MAC address to LAN:
ou either have a VLAN or you don't. There is no "Kind off".
Please read my thorough article how my network is setup
-
Do you mean connecting to that subnet directly, like pulling an IP address in that subnet.
Or do you mean prevent a device/MAC address connected to LAN2 from accessing a resource on LAN1.
If it is wifi you probably have MAC address filtering there.
If you're running plus you can enable and add layer 2 firewall rules to filter by MAC.
-
@stephenw10 said in Block by MAC address to LAN:
If you're running plus you can enable and add layer 2 firewall rules to filter by MAC.
Yes this is what looks like is the solution. How is this done? You got it! (I do have pfsense+)
-
@netboy you want us to try and figure out what you have setup in a thread from 2022 with 67 posts that is all over the board? From a diagram that doesn't even mention wifi, and according to that drawing your lan 1 and 2 are in the same 192.168.0 network.
Why are you calling them lan1 and lan2 if they are the same network?
Where on that drawing would it matter which actual physical interface would it matter someone on that network connects to either 1 or 2?
You don't show which port the nas nic is connected to or your unmanaged switch you are pointing too.. Where is your unmanaged switch connected too - it sure can not be both or you would create a loop, or your switch would shutdown one of the ports to prevent the loop.
So how exactly are we suppose to figure out what you want or what your trying to do.
even if you do ethernet filtering, you can't block a mac from talking to either port 1 or 2 that are in the same network.. They would be talking to the mac of your pfsense interface that has the 192.168.0.x IP - its not going to block them from using one of the physical interfaces in the switchport of your 2100..
Your not going to show lan1 and lan2 as different interfaces if they are in the same network - unless you created a bridge.. Why would you bridge 2 switch ports? That is nonsense..
-
@netboy Is this the solution
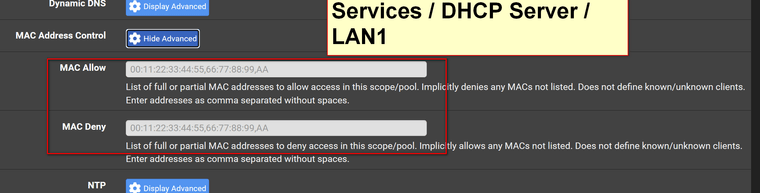
-
@johnpoz Thanks for your help @stephenw10 got it what I was looking for.
-
Doing that prevents MAC addresses pulling a DHCP lease but devices could still connect and use a static IP.
This is what I was referring to:
https://docs.netgate.com/pfsense/en/latest/firewall/ethernet-rules.html -
@stephenw10 Ok thx - let me read try to understand how this is done.
-
@netboy that is not anywhere close to what you asked..
Nowhere have you mentioned anything about dhcp until just this post. When you post up a screenshot of dhcp server settings.
Hope you figure out what your trying to do... But how is blocking dhcp from the same lan - per your drawing going to stop them from using lan1 but still allow them access to lan 2.. Per your drawing - this is the same network..
-
@stephenw10 said in Block by MAC address to LAN:
https://docs.netgate.com/pfsense/en/latest/firewall/ethernet-rules.html
@netboy said in Block by MAC address to LAN:
Ok thx - let me read try to understand how this is done.
You are are aware that most phone (devices) have the "randomize MAC" activated by default ?
You should as your phone does this ... and the bad news it : the device of the people that you want to block have it too.
So, ok, you start blocking MAC's. People disconnect, "forget the network", reconnect, and they will use a new MAC ....
What could work : block all, and only use PASS rules so known devices can get through.Anther solution : observe the LAN network that you want to limit in usage. See where the connected (authorized) devices go to. Enable their destinations with firewall rules. Then : block the rest. From no won, nobody want to use your (that LAN) connection anymore, as they can't go no where.
-
@Gertjan said in Block by MAC address to LAN:
You are are aware that most phone (devices) have the "randomize MAC" activated by default ?
I did not know this. Thanks for bringing this up
What could work : block all, and only use PASS rules so known devices can get through.
I will have to try this probably