LAN cannot access internet
-
@syorke Test pinging and traceroute from pfSense using its LAN interface.
So far it sounds like your issue is the internal network can't get out? Do your rules on LAN allow that? (you might post those rules...) Can that internal network ping pfSense?
-
@syorke said in LAN cannot access internet:
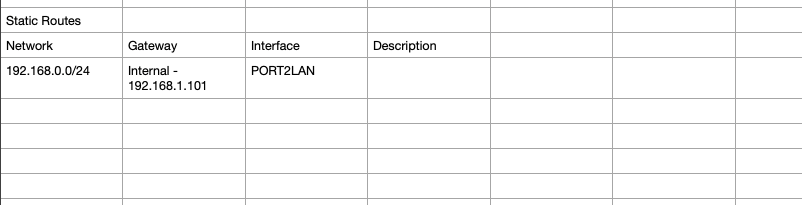
Static route added 192.168.0.0/24 using the gateway 192.168.1.101 on interface PORT2LAN
Check that pfSense has an auto outbound NAT rule for 192.168.0.0/24. I'd expect that static route to have added one but if not you'll need to add it manually if the internal router is not NATing.
-
@syorke said in LAN cannot access internet:
I tried adding a gateway to the router and then adding a static route for for the network on the inside of the router. No success.
This would be setup on pfsense, not your downstream router. Here is a diagram for how to setup a downstream router.. There should really be no hosts on the network you use for transit/connector network or you going to run into asymmetrical routing most likely.
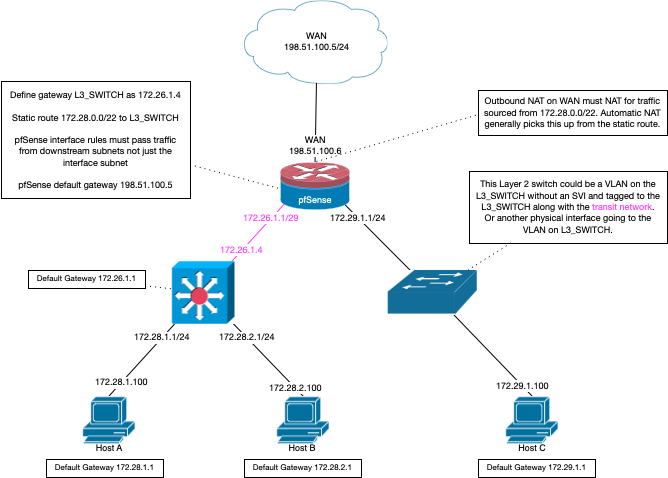
The way you worded that - sounds like your trying to setup routing on your downstream router.. Really the only route it should have is its default one.
-
I've not had any luck yet.
Current Setup
WAN - pfSense - 192.168.1.101 - internal router - 192.168.0.0pfSense has an Automatic outbound NAT rule generation set, I tried setting a manual rule to map PORT2WAN to PORT1WAN, and there was no difference
PfSense can ping the outside WAN using the DNS name or IP. So, DNS is working from the pfSense.
Internal 192.168.0.0/24 address can log into the internal address of the router and can log into pfSense by IP address (on the LAN side) as well.
-
@syorke if you can login to pfsense IP address from behind your router then lets see your outbound nat rules.
If pfsense didn't know how to get to your client on the 192.168.0 network then you would not be able to log into it. So either your router is natting to pfsense or its not, and you adjust your rules on pfsense because by default the lan rules would only allow traffic from its own lan network.
Please post up your lan rules on pfsense, and your outbound nat rules..
What is the downstream routers default gateway? If not set or wrong, then you would still be able to talk to pfsense IP since its directly connected to pfsense IP 192.168.1.x - but if there is no gateway, or its not pfsense - then no you wouldn't send traffic to pfsense to be routed and natted to the internet.
-
@johnpoz thanks for your response again
I'm thinking that the static routes might need changes or additions but I'm not sure what that should be
The default gateway on the downstream router is the pfsense PORT2LAN address.
PORT1WAN Firewall Rules

PORT2LAN Firewall Rules

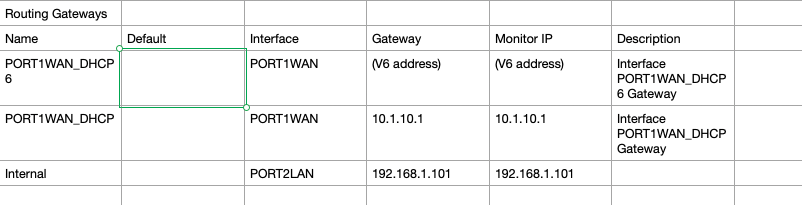
Routing Gateways
Static Routes
-
@syorke what is that from - that is not pfsense gui have seen. Did create a spreadsheet in excl or something?
Where are you outbound nats?
How would that ever work - your rules on port2lan only allow the port2lan network to go anywhere.. So you coming from anything other than 192.168.1 would never get anywhere..
Clearly you didn't even look at the diagram I put up that says how to do a downstream router.
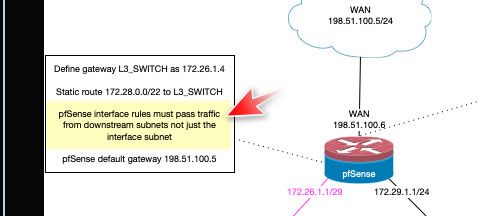
Your allowed to talk to the pfsense gui, because you have any as the source for your 80/443 ports

When you add a route to some downstream network, pfsense should auto add it to your outbound nats, unless you have changed that from auto to manual.
-
 J jimp moved this topic from Problems Installing or Upgrading pfSense Software on
J jimp moved this topic from Problems Installing or Upgrading pfSense Software on
-
This post is deleted! -
@johnpoz Sorry for missing the pointer on your original post and your frustration.
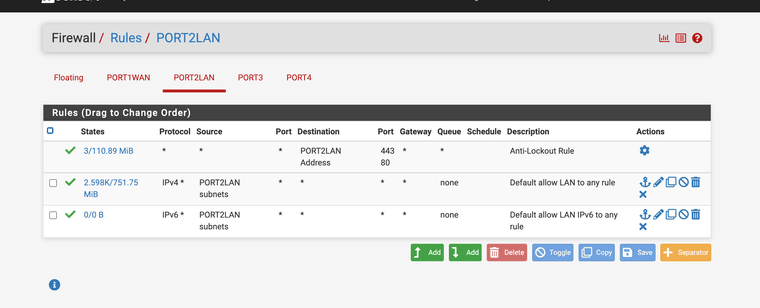
My firewall/rules/port2lan rules are as you show:
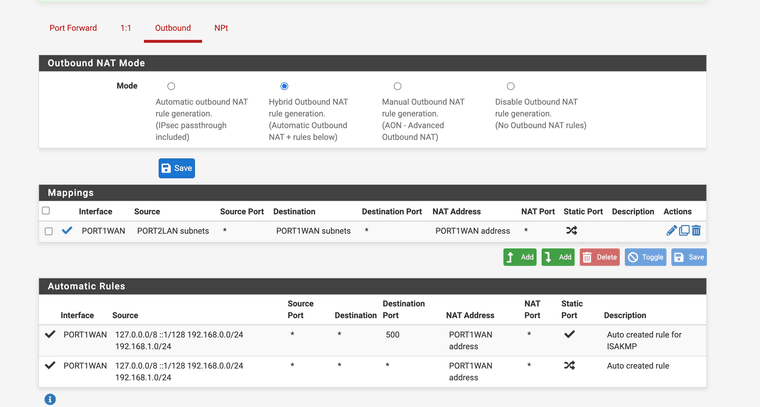
I have added a NAT/Outbound rule, It looks correct as the outbound automatic rule looks to be updated correctly, though traffic is still not passing through.
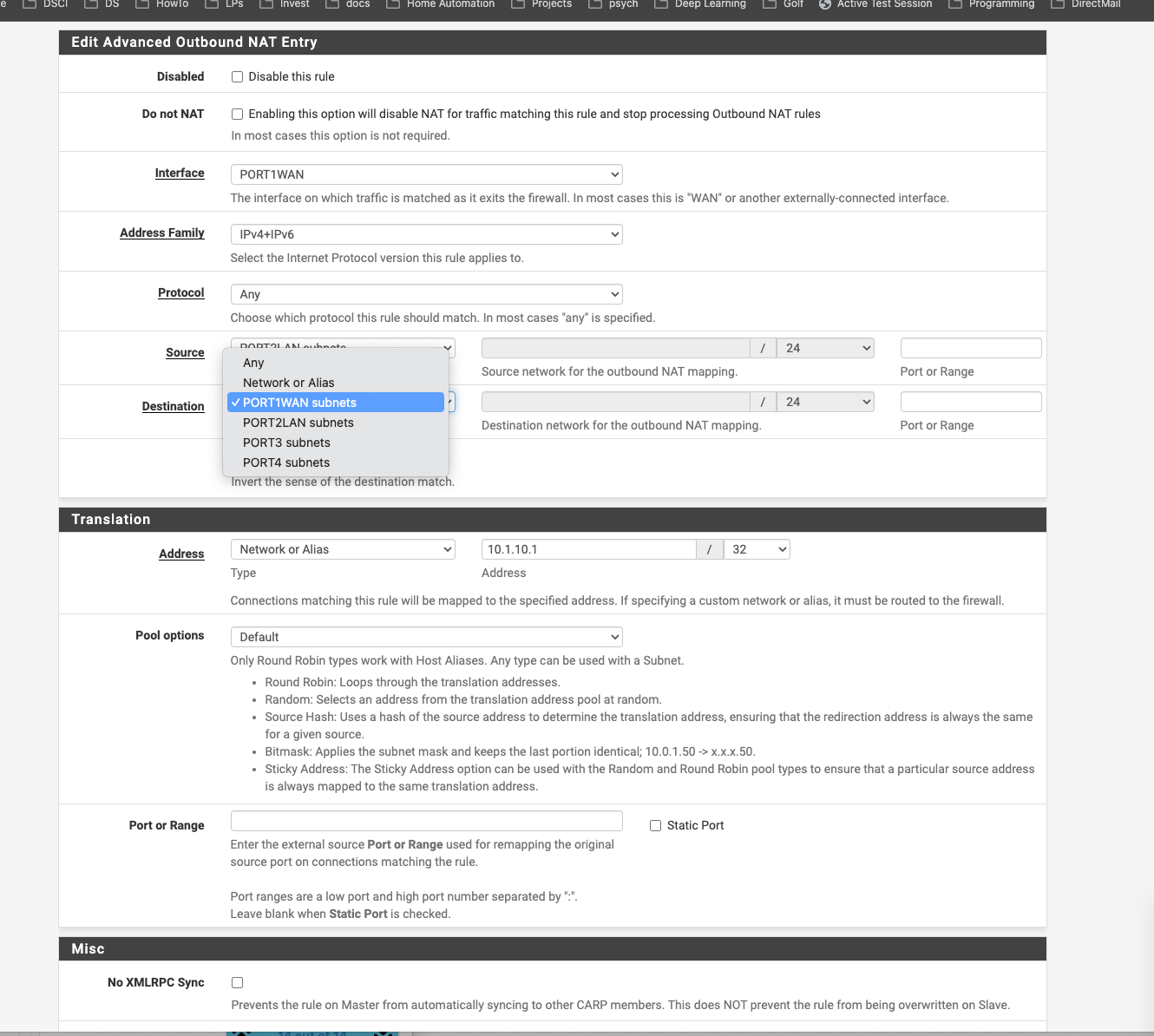
For the NAT should I have switched the destination to the network or alias instead of the Port1Subnets, also, should I have done the same and specified the Modem address for the NAT address?
-
@syorke what part are you not getting that if your rule says only 192.168.1/24 can use this interface with the lan2port subnets, how would 192.168.0.x be able to use it?
You need to allow both 192.168.1 and 192.168.0 - you can do that with a 2nd rule, you could do that with using a cidr of 192.168.0/23 you could create an alias that has both networks in it.. Or you could just make it an any with the "*" like your antilock out rule.
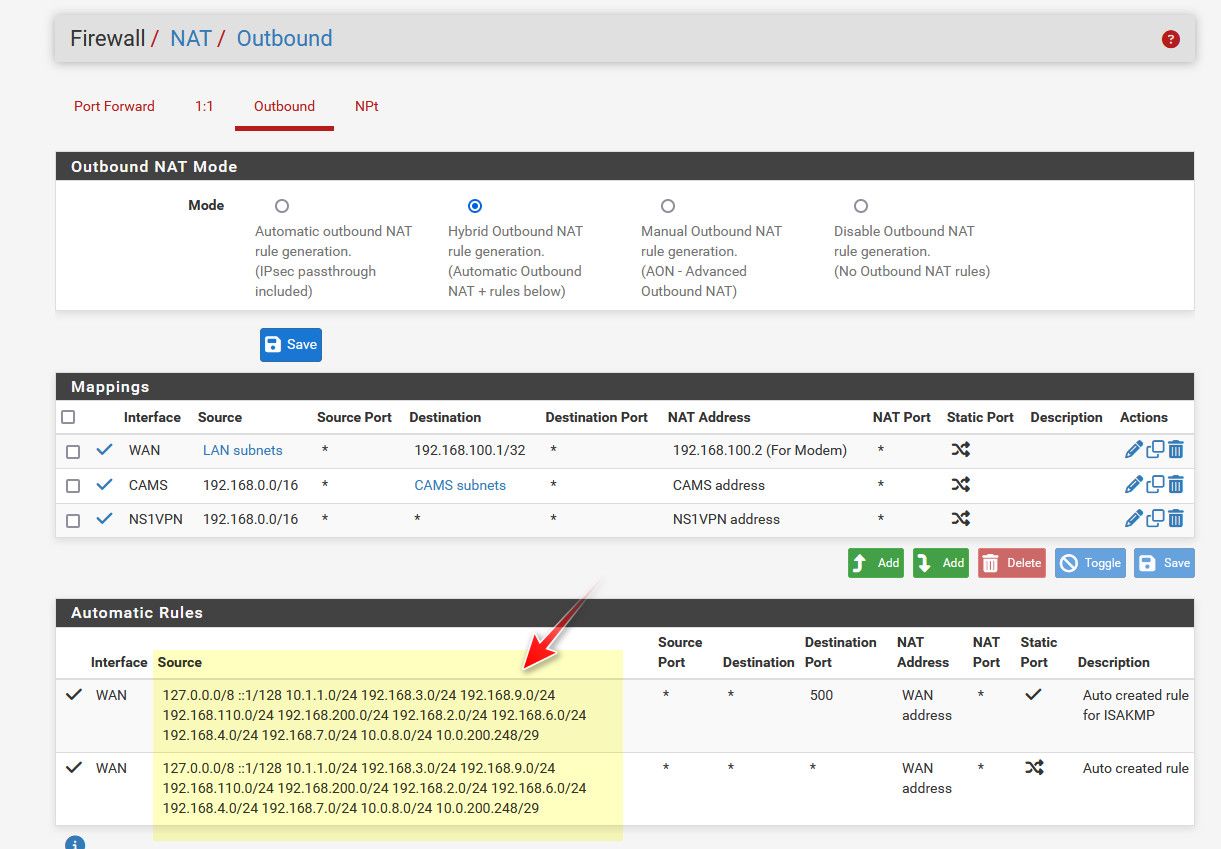
No you shouldn't use a modem vip I created for use on my network.. I posted up a screen shot of my outbound nats - I highlighted the part you should be looking for that downstream network to be in.