Logging DNS queries
-
@johnpoz Ah ok, of course I enabled that, otherwise I wouldn't get anything resolved, right?
edit: It's been a long time since I set this up, and now I remember why I have it set up like that - the ISP's DNS servers are 2km away unlike something that's several countries away, so it should have much better response.
-
@Octopuss no you don't not need to set that up to resolve something like google.com or any other public domain. unbound would ask the root servers and walk down the tree.
As to response time.. Who cares if your 2ms or 100ms.. And the only time you have to talk to roots is on a cold lookup.. After a domain is looked up unbound will directly talk to the authoritative NS for that domain since it will be cached.
Your isp dns is only ever going to cache stuff queried by its customers anyway.. So you looking up something that no other customer has looked up recently will have their dns have to resolve from roots anyway, or forward it to some other NS..
If your forwarding - did you uncheck do dnssec? If you forward dnssec is only going to cause problems.. dnssec is only worthwhile when you actually resolve. All its going to do is generate extra queries for zero benefit other than your queries possibly fail.
If you want to know what is using large amount of dns, setup the logging I posted, or easier would to use dnstop to be honest.. This should give you indication right away what client behind pfsense is doing most of dns traffic..
You can very easy get a breakdown of who is asking for the most dns by IP, and what are the top things being looked for, and even what each IP is asking for the most, etc. etc..
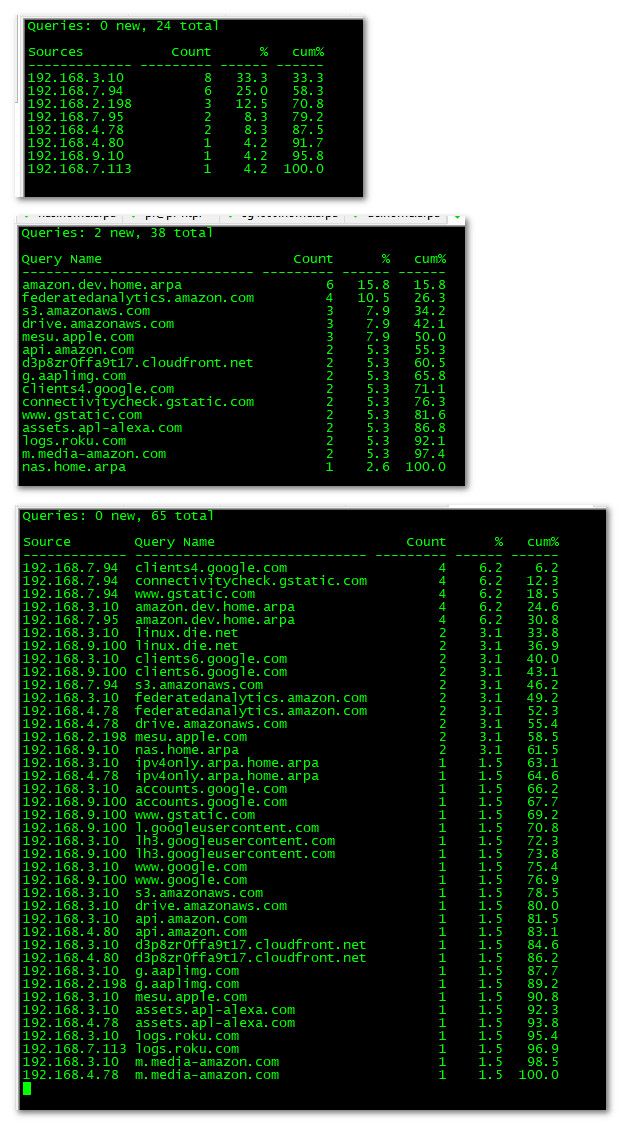
You can install dnstop on pfsense with pkg install dnstop
[24.11-RELEASE][admin@sg4860.home.arpa]/root: pkg install dnstop Updating pfSense-core repository catalogue... pfSense-core repository is up to date. Updating pfSense repository catalogue... pfSense repository is up to date. All repositories are up to date. Checking integrity... done (0 conflicting) The most recent versions of packages are already installed [24.11-RELEASE][admin@sg4860.home.arpa]/root:I already had it installed.
-
@johnpoz Yes I did enable DNSSEC. After some reading around it sounded like a good thing to have.
What did you mean by "dnssec is only worthwhile when you actually resolve"?
Btw how do I use dnstop? Sorry I don't know ANYTHING about Linux. The link you posted doesn't help. Supposedly one of the parameters is device, but I have no idea wha that is. I presume it wants the id of whatever network adapter it should check, but I have no idea how to figure that out.
Nevermind I got it. I guess I am supposed to keep it running and it will accumulate over time.How do I make it output like on you screenshots though?
-
@Octopuss said in Logging DNS queries:
How do I make it output like on you screenshots though?
That's what I was asking myself also.
So, google man freebd dnstop and you're in.Start with a
ifconfigand you see your interfaces. Or go to (GUI) Interfaces > Interface Assignments to see the same thing.
My LAN is igc0 ...So :
dnstop -4 -6 -Q -R -l 3 igc0When it ran, I pressed # (because "show sources + 3rd level query names")
Experiment with it.
-
@Octopuss If you have pfSense set to forward DNS queries then it doesn't look anything up itself and just asks the configured DNS server(s). In that setup DNSSEC should be off because it can create problems. The target DNS servers would use DNSSEC and you presumably trust them already.
The default in pfSense is to not forward, so it looks up DNS answers itself as noted above.
Both ways work.
One possibility is that if you are blocking anything, I've heard of IoT devices that assume "I can't connect" means "retry immediately" and generate a huge amount of lookups and connection attempts as they retry their DNS lookup several times per second.
-
@Octopuss said in Logging DNS queries:
it will accumulate over time.
yeah.. you need to leave it run for the amount of time you want to collect info.. Just running for a couple seconds isn't going to show much unless you were getting just streaming dns queries like crazy..
I would run it and then do a query from your client for something specific - and you should be able to see it, your prob going to want to use atleast -l 3 if not higher as mentioned by @Gertjan so you can see something like www.domain.com, but you won't be able to see the specific query for something like otherthing.whatever.domain.com - the query would be counted but the info it would show for the specific query would only be whatever.domain.com
I am curious what your isp considers large amount of dns requests ;) Unless you were doing what could be considered a dos, why would they care if you ask for 10,000 queries in a day or 1k.. ? Now 1k a second, ok yeah that seems high - or even worse 10k a second than yeah you doing something odd.. or wrong..
Keep in mind if your client was asking pfsense 1k times a second for www.whatever.com - your isp would only see 1 query for that for whatever the length of the ttl was.. So say the ttl was 3600 seconds for www.whatever.com.. The most your isp dns should ever see is 1 query for that an hour, even if you client locally was asking pfsense 10k times a second..
Because pfsense would have that record cached, no reason to ask the isp dns for it until the ttl expired and it was no longer in cache - then if client asks for it again it would have to forward that to your isp dns to get an answer.
If your isp is saying your doing large amount of queries you really shouldn't have to run dnstop very long to notice which client of yours is asking for large amount of queries..
edit: see I ran it with -l 3 and I can see query for something.otherthing.com, but what I really asked for was www.something.otherthing.com, but that is 4 levels in the query, and I told dnstop to only keep track of 3
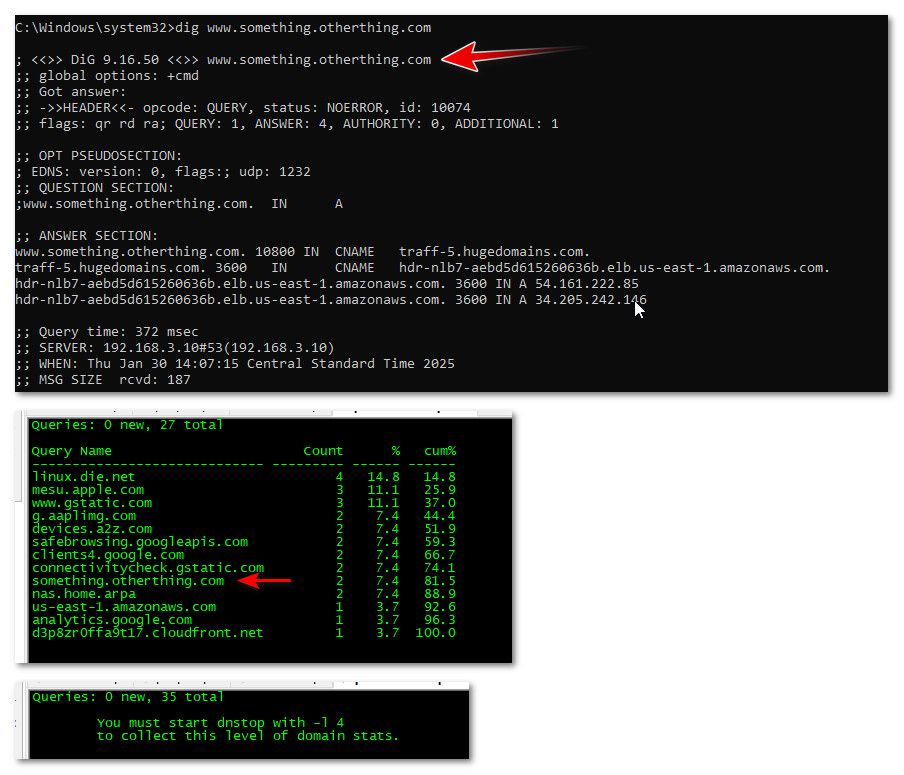
-
@johnpoz said in Logging DNS queries:
I am curious what your isp considers large amount of dns requests ;)
Me too!
I asked them to call me tomorrow to explain what the heck they see that worried them enough to justify contacting me.
I let it run for two hours or so, and this doesn't look anything out of ordinary.
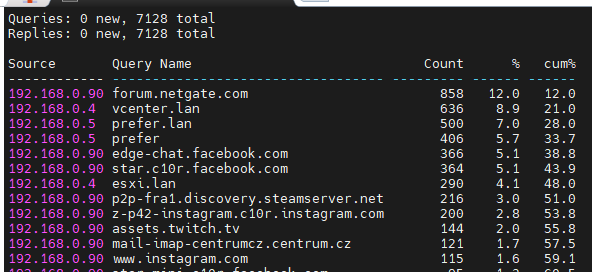
-
@Octopuss no that is not crazy by any means.. And to be honest those vcenter.lan and prefer.lan shouldn't even be sent to your isp dns. or that esxi.lan either. I mean there is no way your isp would be able to answer that query.. And I take they actually resolve locally right.
so forum.netgate.com.. the ttl on that record is 60 seconds, which I personally think is crazy low.. But with a ttl of 60 seconds.
;; ANSWER SECTION: forum.netgate.com. 60 IN A 208.123.73.77And you ran for 2 hours.. so 120 minutes.. While your client asked unbound 858 times.. The most your isp should of seen is 120, once a minute every hour.. same could be said for those other counts.. Your isp dns should only see a fraction of those numbers, depending on what the ttl of the specific record is.
7k queries in 2 hours, doesn't seem crazy to me.. Especially since a lot of those shouldn't even be going to your isp, and other would only be a portion of those numbers because unbound should answer those from cache.
-
@johnpoz said in Logging DNS queries:
And to be honest those vcenter.lan and prefer.lan shouldn't even be sent to your isp dns
vcenter.lan is just a virtualized server running FreeNAS that sits in the living room, and considering I was watching DNS queries on LAN interface, I guess this was strictly local.
-
@Octopuss yeah any local resources should never go to your isp.. because unbound should resolve that locally.
example
$ dig nas.home.arpa ; <<>> DiG 9.16.50 <<>> nas.home.arpa ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 61959 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ;; QUESTION SECTION: ;nas.home.arpa. IN A ;; ANSWER SECTION: nas.home.arpa. 2364 IN A 192.168.9.10 ;; Query time: 2 msec ;; SERVER: 192.168.3.10#53(192.168.3.10) ;; WHEN: Thu Jan 30 14:39:44 Central Standard Time 2025 ;; MSG SIZE rcvd: 58no public dns would ever be able to resolve that, so why should it be sent upstream either forwarding or resolving. if its not resolving locally then you wouldn't be able to use it locally. because you wouldn't be able to get an answer.
If you ping vcenter.lan from your pc - you get back an IP right..
$ ping nas.home.arpa Pinging nas.home.arpa [192.168.9.10] with 32 bytes of data: $ ping ntp.home.arpa Pinging ntp.home.arpa [192.168.3.32] with 32 bytes of data:edit: now that you mention locally listening - you might want to make sure your dns isn't open to the public internet.. Its possible if your dns is open to the public, all kinds of ips could be asking your dns from the public internet and unbound is forwarding that to your isp.. This can be used as a dns amplification attack.
You should make sure your firewall rules on your wan are not open to dns traffic tcp/udp 53.. You might want to run dnstop on yoru pfsense wan and see if your seeing queries from IPs out on the internet.
-
@johnpoz Ah the firewall, that's a problem. I do not understand networking at all, it's just something I could never learn despite being an IT support guy by trade (well, used to up until ~ten years ago).
This is what I have for WAN.
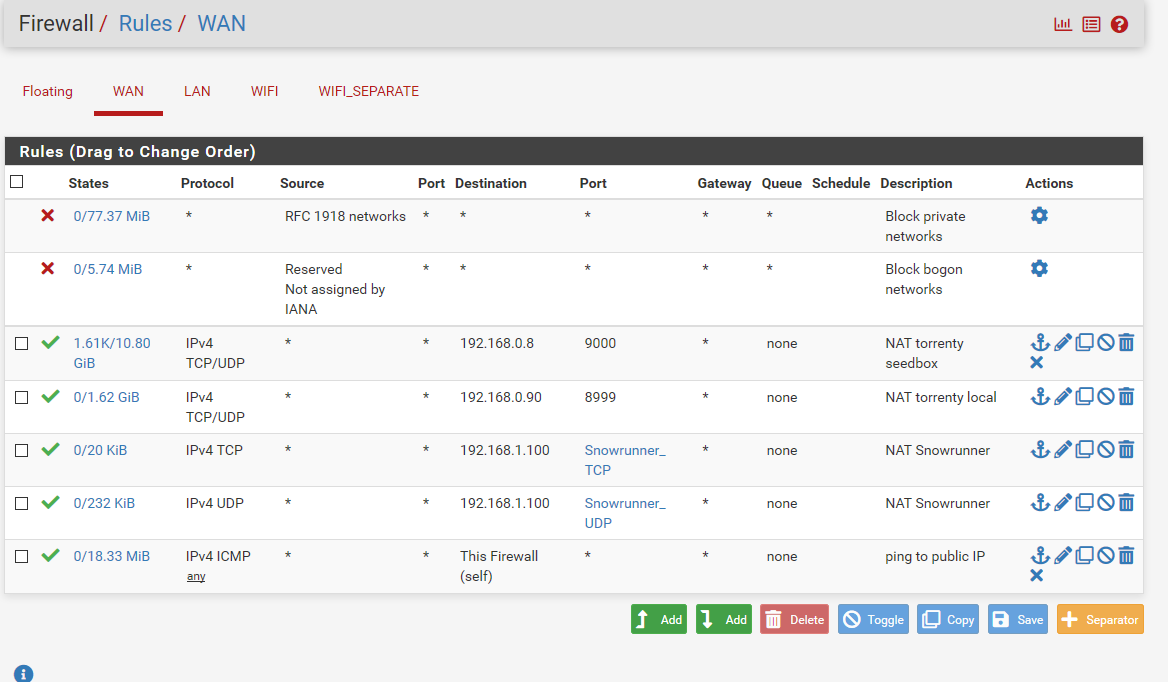
-
@Octopuss nope nothing there that would allow access to your dns from outside.
Do you have anything in the floating tab?
So when you running dnstop for 2 hours.. Did you have active p2p running (torrents).. Maybe when you have active p2p running is when your dns queries spike like crazy? Maybe you might want to leave dnstop running for a day or 2 to see what your typical sort of queries are day to day..
So also when you were running it you were only listening for dns that comes in on your lan interface, but see you also have a wifi and wifi-separate.. Its possible lots of queries are coming in there?
You could also run it on your wan interface and it should show you the queries your pfsense is sending and to what IPs
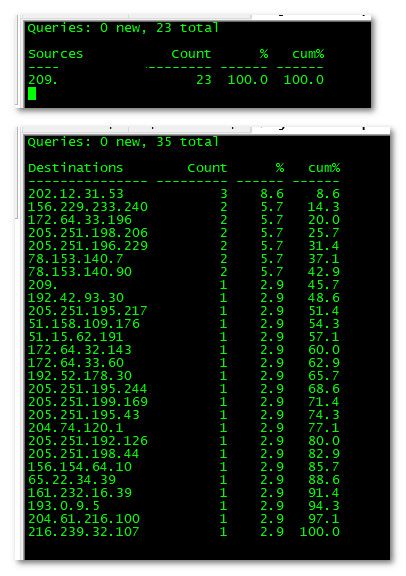
You will see lot of destination in mine because I resolve, and do not forward.. For your destinations you should only see your isp dns since your forwarding.. But its more about the amount of them, and sure you could log with like -l 3 again to see what is being asked for..
-
@johnpoz said in Logging DNS queries:
Maybe when you have active p2p running is when your dns queries spike like crazy? Maybe you might want to leave dnstop running for a day or 2 to see what your typical sort of queries are day to day..
I would have to catch a moment when a torrent starts seeding.
And sure, I could keep it running for a day, but the program could crash or I would forget and reboot the PC and all the results would be gone.
-
@Octopuss you can store the info to a file. You reboot your pfsense? The only time a reboot is if upgrading its version.
See the manual for dnstop on how to use the savefile - it really should just be the /path/filename at the end of your command.
I would run it first just on your wan interface for say an hour or so - are you seeing something crazy like 10k queries a minute or something to your isp dns?
-
@johnpoz said in Logging DNS queries:
You reboot your pfsense? The only time a reboot is if upgrading its version.
Oh, no, I use Mobaxterm to SSH to the various devices on the network that can do so. Obviously if my PC somehow restarts or goes to sleep or locks up or whatever, all the data would be lost.
edit: dnstop -Q -l 4 igc0 /tmp/dnstop doesn't save anything. This folder looked like something that can be written into but somehow nothing happened.
-
@Octopuss oh my bad - savefile is for reading in info from a pcap.. You would have to run a pcap capturing your dns and then load that in..
Ah your talking about loosing your ssh connection.. Ah you can run it in a screen then.. you can install that on pfsense with pkg install screen.
This allows you to run it in a screen, detach it and then reattach it later.. that way you can disconnect your ssh session.
see here is one running
[24.11-RELEASE][admin@sg4860.home.arpa]/root: screen -ls There is a screen on: 8926.pts-0.sg4860 (01/30/25 17:50:51) (Detached) 1 Socket in /tmp/screens/S-admin. [24.11-RELEASE][admin@sg4860.home.arpa]/root:I can then reattach to that .. there are plenty of examples on the net on how to use screen
edit:
quick and dirty howtorun screen, start your command. do a cntrl+a and then d to detach it.. then you can even close your ssh session. Come back in a couple of days and reattach to that screen.. do a screen -ls to see your sessions, then attach to one you want with screen -r number
-
I have finally lost patience and call the ISP, spoke to the owner, and am not any smarter than before, lol.
He basically told me our address was number 2 in DNS queries - presumably in our network segment, but possibly in the entire network (I forgot). I think he said the total number of queries for yesterday was... 16k? Something like that.
I can't tell if that's a lot or not for a power user kind of person. My PC basically stays on 10+ hours a day with lots of tabs open, plus there is torrent seedbox, a few phones and 2-3 notebooks (which aren't used much so that's probably irrelevant).I let dnshot running overnight, and since I last posted here until now, there have been 25283 total requests. 5900 of those is this forum alone which I let running. It was checking the WAN interface, and I am confused why it still displays local queries, but whatever.
edit: One more thing I don't understand is why whenever I refresh any page in the browser on my PC, extra DNS request is made, but when I do the same on my phone, nothing happens. I tried various things but the only time I see any DNS requests being logged from my phone is when I actually connect to the wifi.
-
@Octopuss said in Logging DNS queries:
I think he said the total number of queries for yesterday was... 16k? Something like that.
Euh, lol. That's nothing. That's what we consume here per hours .... and its Friday, they all left for the weekend already.
You spoke to the owner .... wow, how big is your ISP ? 3 or 4 clients ?
@Octopuss said in Logging DNS queries:
I see any DNS requests being logged from my phone is when I actually connect to the wifi.
If your not connected to your wifi .... then where does the traffic come from ?
I give you a hint : not through pfSense.@Octopuss said in Logging DNS queries:
I don't understand is why whenever I refresh any page in the browser on my PC
What host name ?
For example : this one : forum.netgate.com ? You already know why, but didn't connect all the dots yet ^^[24.11-RELEASE][root@pfSense.bhf.tld]/root: dig forum.netgate.com AAAA Bla bla bla ;; ANSWER SECTION: forum.netgate.com. 30 IN AAAA 2610:160:11:11::6So, the IP that was resolved from [24.11-RELEASE][root@pfSense.brit-hotel-fumel.net]/root: dig forum.netgate.com AAAA is 2610:160:11:11::6 and its valid for (TTL) 30 seconds.
The browser will send out a DNS request to update the info as soon as the TTL is expired.
As you found out yourself : that happens every 60 seconds. Why 60 seconds ? Not sure, the question was already asked, but no one from Netgate could come public with a reason.TTL = Time To Live.
You saw 5900 requests for the "forum.net.com" so you had a forum web page open for 5900/60 = 100 minutes or so.
@Octopuss said in Logging DNS queries:
It was checking the WAN interface
In that case you'll see the DNS requests that are coming from the resolver, and, if you have devices that don't use the pfSense resolver but do their own resolver or tap into 8.8.8.8 or 1.1.1.1,
If you 'dnstop' on a LAN, you would see even more DNS traffic. The traffic that was already in the resolver cache with a not expired TTL would get answered directly without the need of a more time consuming resolve process. -
@Gertjan said in Logging DNS queries:
You spoke to the owner .... wow, how big is your ISP ? 3 or 4 clients ?

I'm not sure, it's a local one for this town and the surrounding areas. They have their own fibre cables laid all around. I would guess the number of clients could be very low thousands.
@Gertjan said in Logging DNS queries:
f your not connected to your wifi .... then where does the traffic come from ?
You misunderstood.
Every time I refresh any page in the browser on my PC, a hit number for that address/IP in dnstop window increases.
When I do the same on the phone (which is on the wifi), nothing happens. Actually the phone's IP doesn't even show up in the list when I go watch the virtual interface for the wifi. The only time the phone's IP and some requests show up in the list is the moment the phone actually connects to the wifi.@Gertjan said in Logging DNS queries:
The traffic that was already in the resolver cache with a not expired TTL would get answered directly without the need of a more time consuming resolve process.
By that logic there should not be any additional requests logged when I refresh a page on my PC, right?
-
@Octopuss Many phones and even desktop browsers now will use DOH/DOT and bypass local DNS servers.