DNS Rebind attack conditions doesn't make sense
-
I'm using pfsense for ages now... something like 10yrs at least, before had many different things between ASA/NSG and PF/IPT/other.
Like every "sane" person, i have home level micro-segmentation with multiple vlans for different purposes to isolate different types of traffic of different risk levels :)
I also have multiple domains, local and public.As i'm building a more mature build/dev environment i want local experience to be no different than the external one so i want to use my public domains internally resolved by local DNS servers to local VIP (Yes, LTM) while externally would be resolved to outside and VIA NAT.
I also don't want to use pfsense for DNS resolution or Forwarding for that matter because i have better and finer control while using my local Knot DNS and AD between users, servers and filtering or views.
I tried several workarounds to disable or whitelist on host level or domain level the affects of this DNS rebind attack policies but at no success, this is very persistent and arguably require major revamp to adapt to more advanced users which i would imagine is the majority of users of pfsense.
I need away to solve this problem, this error below seems too domineering
public domains can be resolved by internal DNS, it's usually done to avoid going outside from the inside as that wont be logical. Also the whitelisting of hosts or domains shouldn't be dependent on pfsense being in the name resolution mix - it should be a choice that would otherwise disable the unbound features and service all together.Error:
Potential DNS Rebind attack detected, see https://en.wikipedia.org/wiki/DNS_rebinding
Try accessing the router by IP address instead of by hostname. -
@bshpire where are you seeing this - you want to access pfsense via a public dns name, that resolves to rfc1918, ie your pfsense IP?
Turn of rebind protection in pfsense you are so keen on doing what is not very good idea.
If your access pfsense with a different name than what it set to like pfsense.home.arpa - you would also need to set the alias for that.
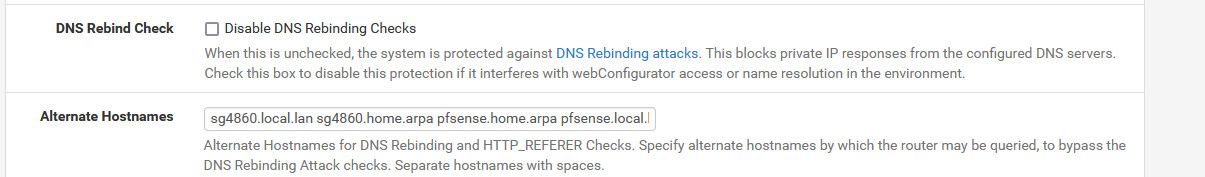
-
@johnpoz I have a DNS internal zone for a public domain, vscode.mydomain.com pointing to an RFC1918 IP which pfsense is blocking with the DNS rebind protection on https. Disabling DNS rebind protection on webgui does not solve the problem.
I've seen many people complain about this issue and the solution around using DNS resolver is not a good workaround for me.
-
@bshpire where are you seeing the error? Are you trying to access pfsense.vscode.mydomain.com that points to a rfc1918 address that is pfsense IP?
If you want to access say pfsense.vscode.mydomain.com, then you would need to add that to alternate names, unless you actually set pfsense name to be that.
So you have some other NS internal that if you do a dns query to for my example pfsense.vscode.mydomain.com returns an rfc1918 address, say 192.168.1.1 that is pfsense IP address on its lan interface?
If you have your own ns that resolves whatever you want that points to a pfsense IP.. sure that works just fine - but if pfsense thinks its name is in my example sg4860.home.arpa and I try and access it with some other name then yeah its going to balk at it..
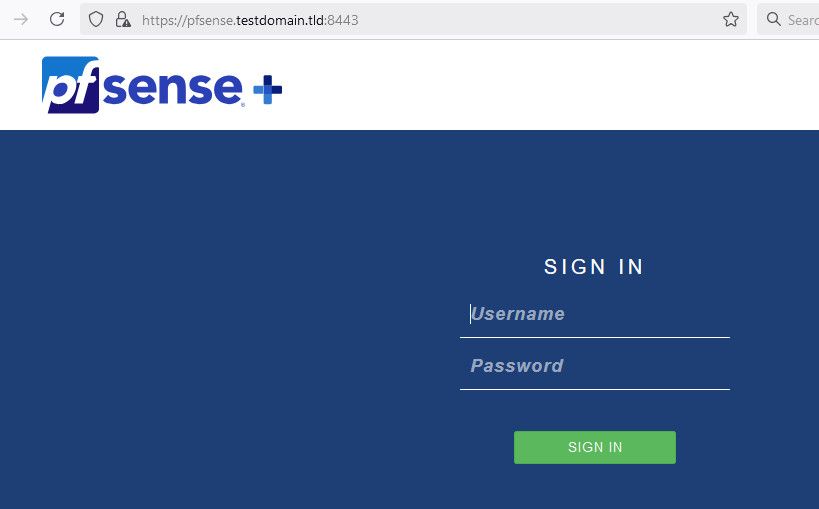
Here I created a name - pfsense.testdomain.tld that points to my lan IP 192.168.9.253
$ dig pfsense.testdomain.tld ; <<>> DiG 9.16.50 <<>> pfsense.testdomain.tld ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 251 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ;; QUESTION SECTION: ;pfsense.testdomain.tld. IN A ;; ANSWER SECTION: pfsense.testdomain.tld. 0 IN A 192.168.9.253 ;; Query time: 3 msec ;; SERVER: 192.168.3.10#53(192.168.3.10) ;; WHEN: Sat Feb 01 16:52:20 Central Standard Time 2025 ;; MSG SIZE rcvd: 67If I try and access that - I get this.
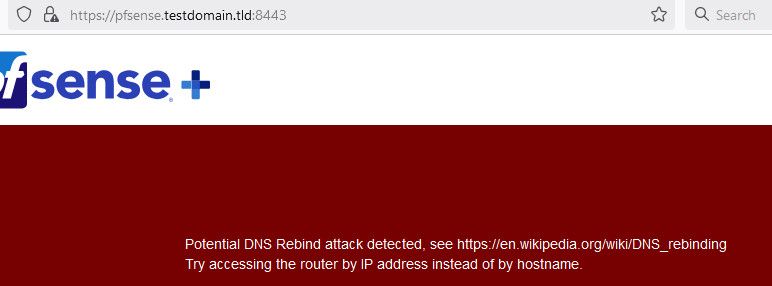
After I accept that the cert doesn't match.. If I add that name to alternate names
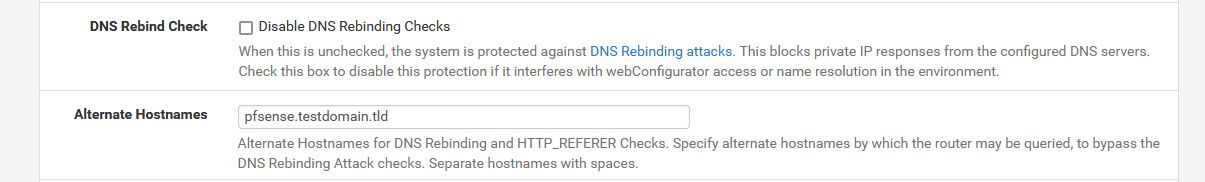
And then I can access it with no warning of a rebind
-
I'm using a windows machine on vlan A with IP 192.168.100.31 trying to reach a machine in VLAN B with IP 172.16.12.250 (pfsense is .1 for both). When trying to get to vscode.mydomain.com or any other a records pointing to local apps using same or other vlans in RFC1918 space it redirects to pfsense webgui giving me DNS rebind error.
-
172.16.12.250 = vscode.mydomain.com
Ssh to that host works just fine
I'm not even sure how this traffic is intercepted
-
@bshpire it wouldn't be, unless you set some rule on your 192.168.100 interface in pfsense.. You have a port forward that would intercept the traffic....
Pfsense wouldn't do anything with that traffic from client in vlan a to b, unless you were using a proxy that was running on pfsense or some sort of intercept rule.
Do you have any rules in floating? What are your port forwards in pfsense? The only scenario where pfsense would intercept some specific traffic to its self is with a port forward.. Like how you intercept dns and send it to pfsense.
-
@bshpire you would only see a message from pfSense if you are connecting to it, and not the desired web server.
-
Yup you are seeing that from the pfSense gui. Most common cause of that is trying to access a port forward from an internal address using an fqdn that resolves to an external IP address. But my reading of this is that you're using an IP address directly...
-
@johnpoz No rules in floating, no special intercept rule and i tried to disable my port forwarding to my LTM with no special affect, the issue still persists.
I don't disagree about this something that pfsense shouldn't be doing but it's a fact
I have about 4 different a records for that domain all behaving the same way from 4 different laptops/desktops -
@stephenw10 This happens both when the translated IP is internal or even if try to set it to the outside IP.
The only logs i see for it is the from the webgui nginx accepting the traffic. -
@johnpoz This is not pointing to pfsense itself
-
@bshpire if the IP is not pointing to pfsense then there is no way you could end up on pfsense. Unless pfsense thinks that his IP as well.
When you want to go to IP on a different network you send the traffic to the mac of your gateway but to your destination IP.. If pfsense has no portward to itself then it must think that IP is his.
192.168.100.31 ---> 192.168.100.1 pfsense 172.16.12.1 ---> 172.16.12.250
So .31 says oh that 172.16 address is not on my network, send it to the mac of my gateway 100.1 (pfsense) with destination IP 12.250
So either you have a port forward that intercepts that, or pfsense thinks 12.250 is his address.. Do you have VIP setup on pfsense?
You sure that fqdn resolve to 12.250 address and not 12.1 ?
Is pfsense a VM? Is this all on VM host?
-
Yup that^. Somehow it's hitting the pfSense webgui so it must be hitting an IP address on pfSense.
-
@stephenw10 Happy to screen share ;)
pfsense running on specialized HW but everything else is either RPi or VMs (vSphere).
Not happening when using mydomain.localAgain, not pfsense, it's gitlab, Jenkins, vscode hosts
I'm very curious myself to how this is happening
Happy to pay netgate for a single ticket or TAC lite to get this resolved and understand the "how" -
Check the states when this is happening. If there is some translations being applied you would see it there.
-
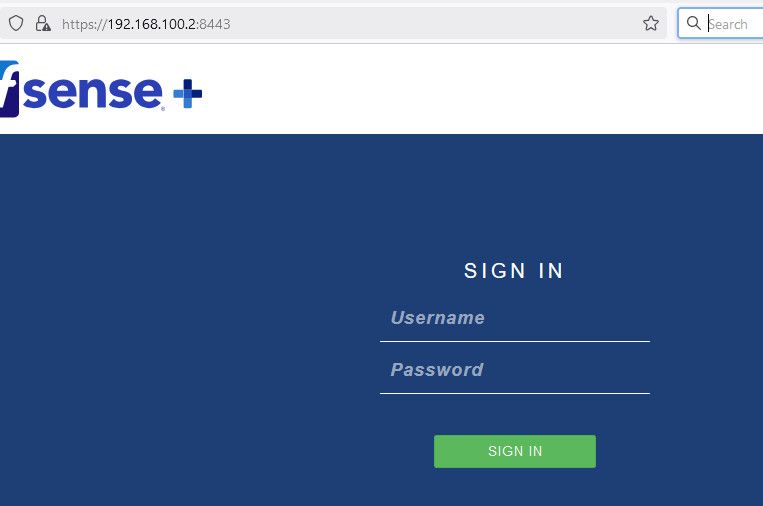
@bshpire well first thing I would do is do a quick look if you have a vip setup.. just look at the output of ifconfig on pfsense
example - here my wan has a vip
igb1: flags=1008843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST,LOWER_UP> metric 0 mtu 1500 description: WAN options=4e100bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,VLAN_HWFILTER,RXCSUM_IPV6,TXCSUM_IPV6,HWSTATS,MEXTPG> ether 00:08:a2:0c:e6:25 inet 209.snipped netmask 0xfffff000 broadcast 255.255.255.255 inet 192.168.100.2 netmask 0xffffff00 broadcast 192.168.100.255 inet6 fe80::208:a2ff:fe0c:e625%igb1 prefixlen 64 scopeid 0x2 media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>unless you intercept traffic - nothing on pfsense could even answer unless it thinks the IP your going to is one of its IPs.. See the 192.168.100.2 IP that is a vip I have on my wan interface to use to talk to my modems 192.168.100.1 IP..
See if I go to that I can see my pfsense gui
But going back to where you say ssh works to the correct host.. That screams interception then for the port your hitting vs ssh.. Or proxy.. So you have no port forwards? You are not running a proxy on pfsense?
You say it works when you use a different domain >Not happening when using mydomain.local
So when you ssh to the host, are you using a fqdn or a IP.. Maybe your dns is just pointing to a pfsense IP? vs the actual IP of what your wanting to talk to.
Are you using .local really? That is a mdns domain, not something that would normally resolve across subnets with out avahi or something responding.. Unless you were on the same L2 and the device answered itself.
I would double check you have no interceptions setup on pfsense, that your fqdn your using actually resolves to the correct IP your talking to.. And that pfsense does not have this IP as one of its own. So you can't access vscode.mydomain.com when you use fqdn, what about via IP..
-
@stephenw10 I disabled all port forward rules, only nat to outside is there per VLAN.
-
Ssh host1.mydomain.local works
Browse host1.mydomain.local (http/https) works
Ssh host1.mydomain.com works
Browse host1.mydomain.com - weird redirection and DNS binding errorDNS is bind9 running on RPi running general cache DNS and local zones transfered from AD (my domain.local/com)
I will get screenshots to show resolution and scenarios above once back home
-
@bshpire said in DNS Rebind attack conditions doesn't make sense:
Ssh host1.mydomain.com works
Browse host1.mydomain.com - weird redirection and DNS binding errorCheck the states created by these connections.