NAT Logs
-
Not VPNs generally, just Tailscale I think. The ACLs applied by Tailscale are not pf so flows are not logged from it.
-
@stephenw10 said in NAT Logs:
Not VPNs generally, just Tailscale I think. The ACLs applied by Tailscale are not pf so flows are not logged from it.
perhaps creating an OUT firewall rule on the destination LAN and tracking that ?
-
hmm. The documentation says something a bit different. Its based on state creation which dictates the flow record creation. At least that's how I'm interpreting it.
-
Right, states are created by pf. Anything that creates a state should be logged. I would expect!
-
Traffic coming from the tailscale network into the tailscale interface in pfSense is not filtered by pf unless it is coming the tailscale interface itself.
Yes you would only see an outbound state on the destination interface.
-
I believe pflow does not capture any VPN traffic.
I also have Wireguard peers and there is no data from IPFix.
I can try and test with OpenVPN but i have a feeling its going to be the same result.So far my guess is that physical interfaces are tracked but logical ones are not.
-
I would be very surprised if that was the case. pflow collects data directly from pf. And pf doesn't care about physical NICs, it filters and opens states on all interface types, physical or otherwise.
Of course I've been surprised before but....

-
hmm you may be right.
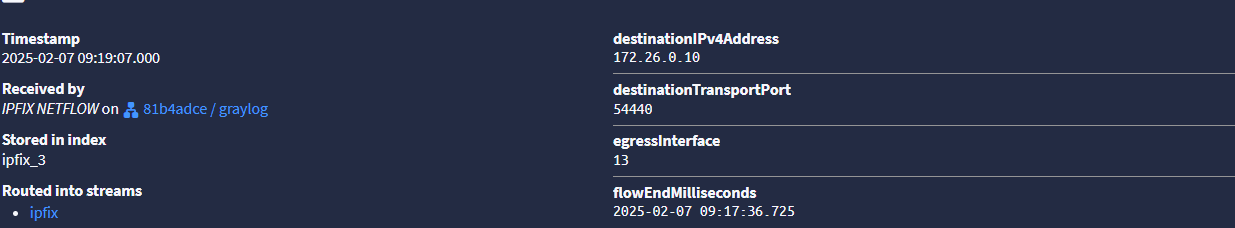
172.26.0.10 is a wireguard peer and here is the IPfix record. So now I'm not sure why its not coming up in my dashboard...hmmmm.....ok figured it out...@stephenw10 you are correct again sir.
-
@stephenw10 One more thing.
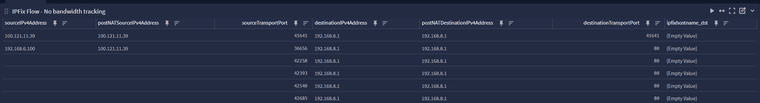
Tailscale flows are indeed captured by IPFix.
The source is the pfsense and the destination is the LAN behind another subnet router.
-
Yup there we go. Tailscale acts more like a proxy in firewall terms. You can only see the traffic to/from it and not the source/destination inside the tailscale network.