correct installation and configuration
-
@Gblenn
port forward there are no rules -
@andreanet Cool and your WAN / LAN rules are also default I suppose?
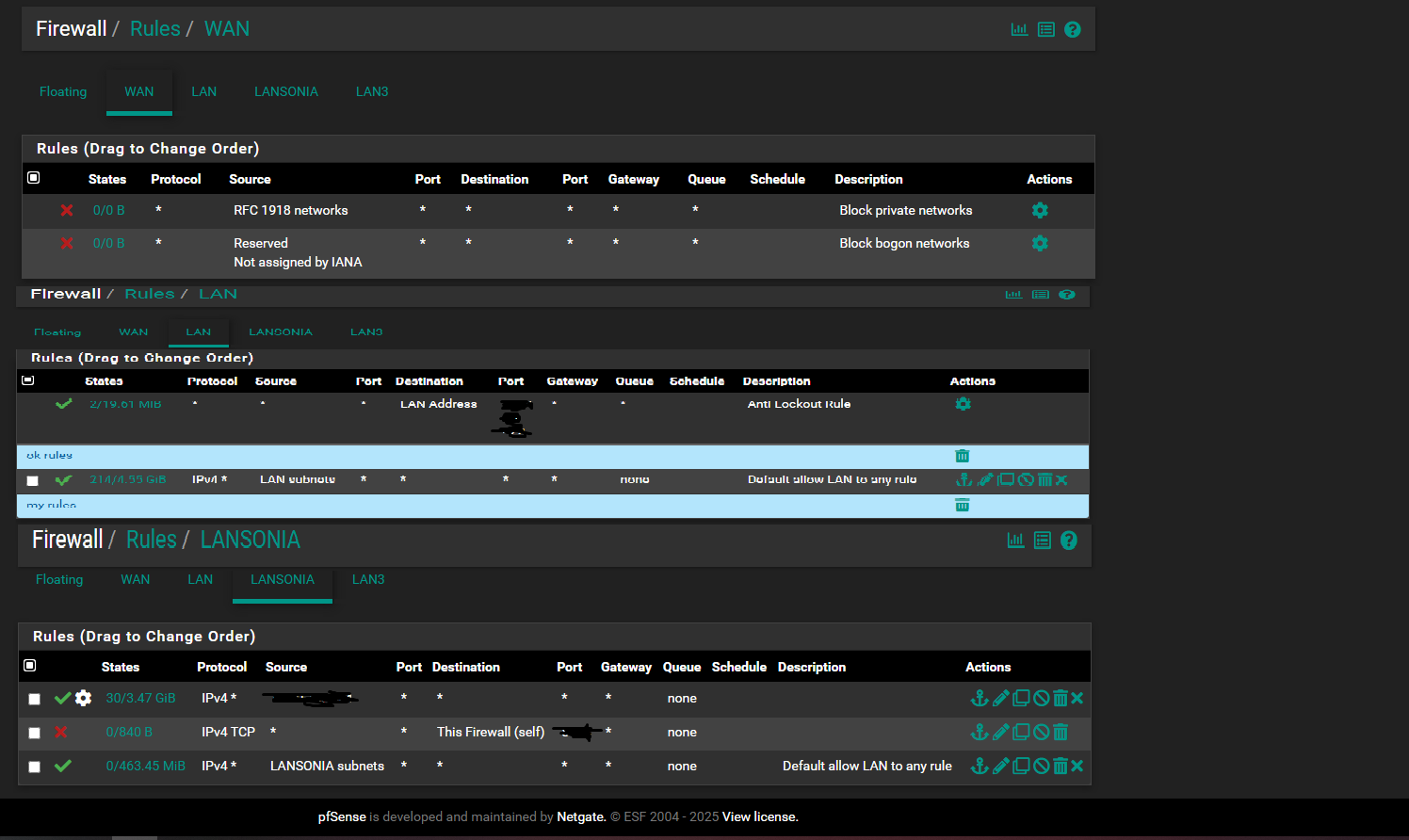
Default anti lock out rule plus one IPv4 and one IPv6 allow LAN to any rule on the LAN interface and only the block bogon and private network rules on WAN -
these are the rules I created on the LAN and WAN.
wan by default created the rules.lan
internet accesslansonia
internet access
can't enter pfsense gui interface,
upload/download limitation 30gb/s -
@andreanet Yeah they look ok and you don't have to obfuscate the ports, on the LAN side (that is a default rule anyway with ports 443, 80 and 22). That rule applies only to traffic coming from any source on your LAN.
And even showing or discussing ports on your WAN is ok and the only thing to obfuscate is your WAN IP.
The LAN source IP that you have obfuscated is an internal IP and accessible and known only inside your network.So you have intentionally blocked access to the firewall for anyone on the LANSONIA subnet?
What do you mean with this?
upload/download limitation 30gb/s
Have you put limiters on LANSONIA network?
-
@andreanet said in correct installation and configuration:
I created a lan on eth1 with ip 19.x.x.x.
JFYI: If you really set lan to 19.x.x.x you would be advised to change that to an private network range.
-
@Gblenn
I limited the connection speed both on the upload and download sideok, I thought it was better to blur everything.
that's right, anyone who is in the lansonia subnet, has no chance to enter the Pfsense GUI
-
hi.
no, the internal lan is 192.168.10.10 -
This post is deleted! -
@andreanet Well, back to your question...
How can I understand if, as I configured Pfsense, I was able to block the entrances to my network?
As mentioned initially, pfsense blocks everything from the outside right out of the "box". Which is pretty much true for any firewall out there, including consumer routers. And none of the things you have made, changes that.
Perhaps one thing to think about with firewall rules, is that they work from top to bottom. And as soon traffic is affected by a rule in the list, none of the lower rules apply.
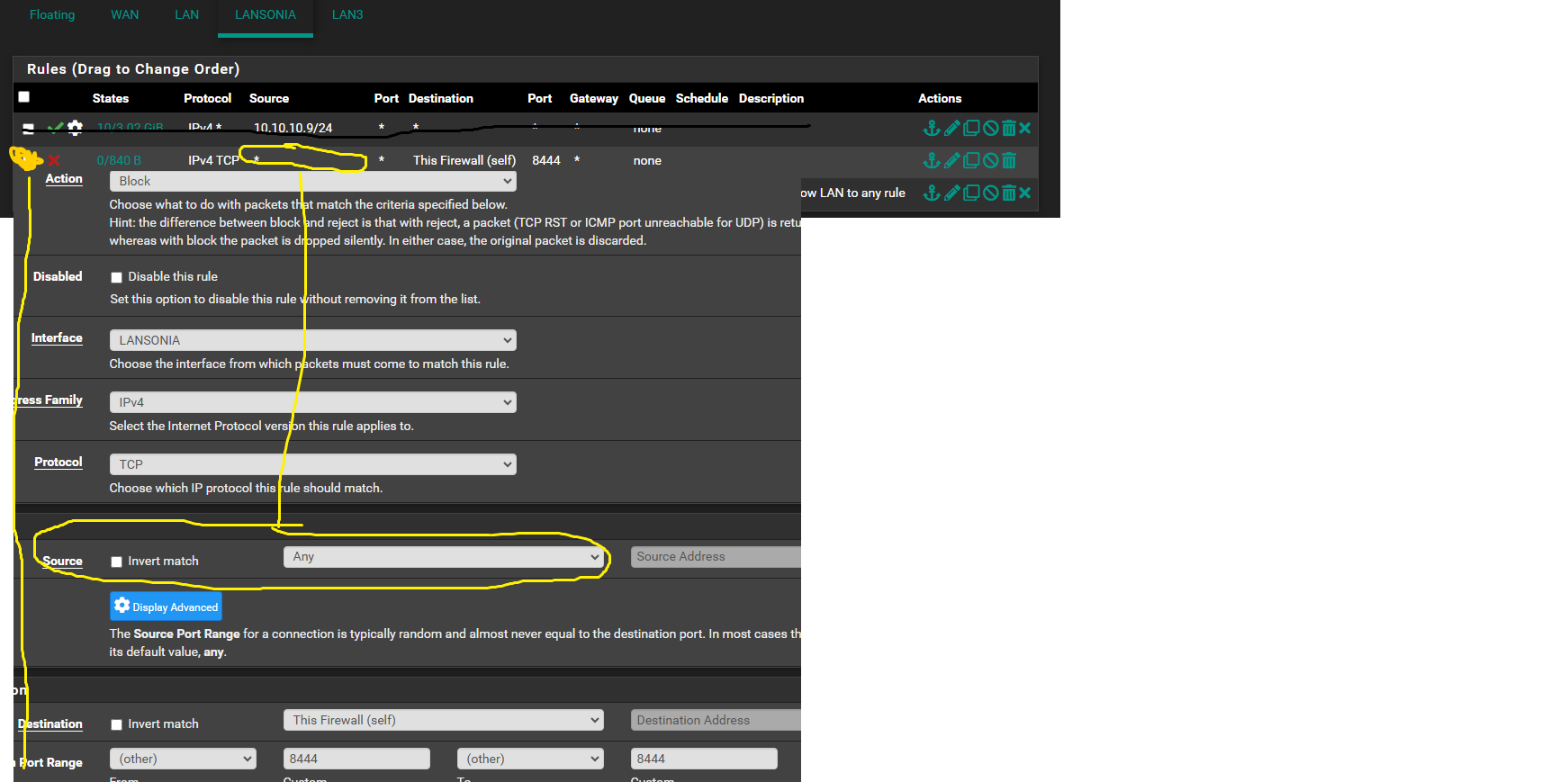
So based on that, you might want to think about this ruleset, and whether that first rule is according to your intentions? It's unclear what that source is since you hid it, but any traffic related to that source is allowed to connect with any destination, including "This Firewall (self)" = pfsense GUI. And on the left there, you can see the amount of traffic that has hit that rule so far.
Only traffic NOT from that source, will be affected by your block rule... If the intention is in fact to allow that source access to the GUI, it might be better to be specific and put "This Firewall (self)" as the destination.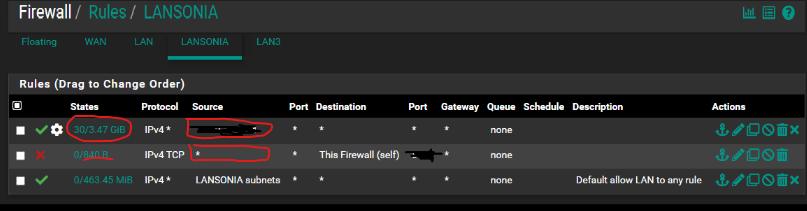
-
Good morning
I'll post some photos to show you how I created the rules.
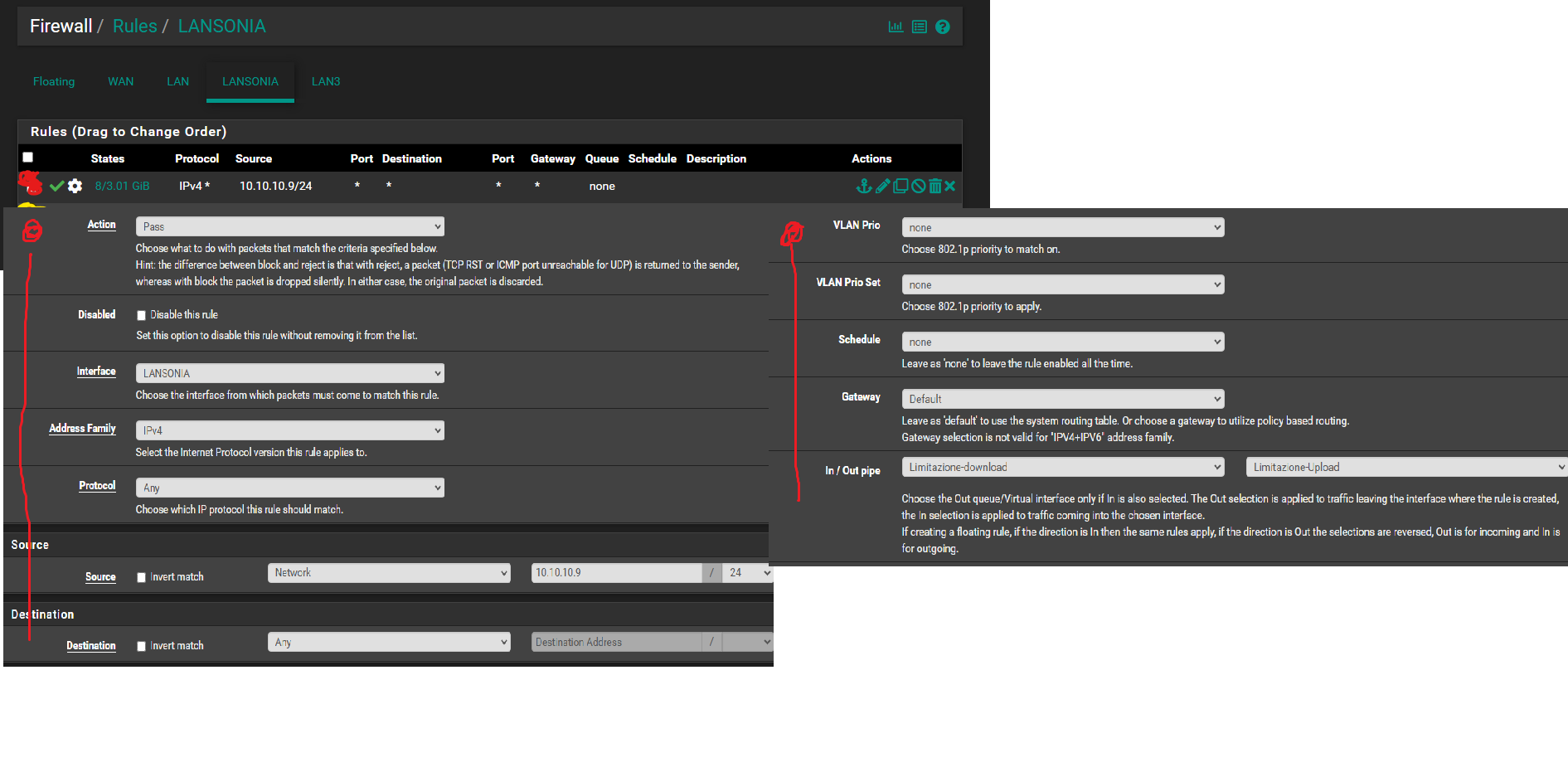
The Red:
the source 10.10.10.9 is the IP address of the Lansonia router
I'm blocking the connection speed at 30mb/s on the Lansonia network for both download and upload.
I ran a speed test on Lansonia and it's limited to 30mb/s
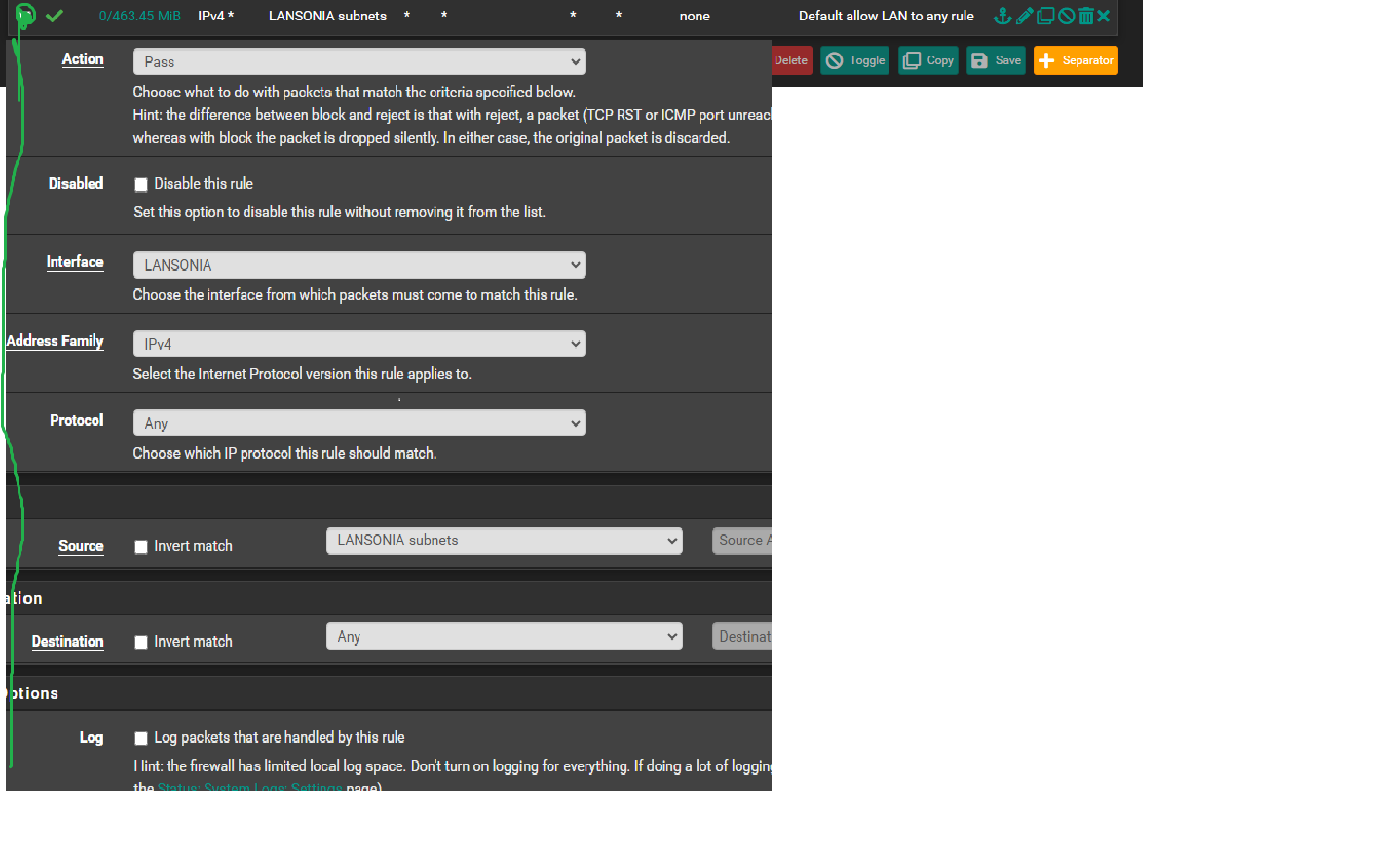
The Green:
I am authorizing the connection of devices in the anxiety of going out to the internet.
all devices can connect to the internet
 ...
...The Yellow:
I'm blocking all devices connected to the lansonia network from accessing the Pfsense WebGui.
I tried with my cell phone and I can't connect to the Pfsense WebGui page
-
@andreanet said in correct installation and configuration:
the source 10.10.10.9 is the IP address of the Lansonia router
Do you have another "router" connected or perhaps you mean wifi Access Point?
If it's an AP, and 10.10.10.9 is just the management interface for that AP, try disabling that rule. Then you will still see that all wifi clients will be able to access internet. Any traffic not targeting rule number two (destination 10.10.10.1 I suppose) will simply hit the last rule allowing internet access.