Domain Override works for Debian and Windows but not Ubuntu
-
Hello community,
I'am not sure wheather this post belongs here or into a Ubuntu forum. I'll try here first. Please advice if I am in the correct forum. Point me to a good place to ask, if not. Or even better: Give a solution or a hint to it.
We are running pfense CE 2.7.2. We have several virtuell networks.
For Network A, (companynet) the pfsense is the DNS-Server.
Network B (company.local) has its own DNS-Server.For DNS requests coming from A, we configured a domain override if a computer in company.local is asked for.
The dns resolution works perfectly for computers (in network A querying a computer in company.local) with Windows oder Debian Linux operating system.
For Ubuntu and Linux Mint (Ubuntu-based) DNS domain override fails.
DNS resolution for Network A or external domains works fine.The following lines show the problem.
Thanks a lot
Martinexternal resolution works
martin@Mint-VM:~$ host www.google.de
www.google.de has address 142.250.181.195
www.google.de has IPv6 address 2a00:1450:4005:801::2003looking for computer in network B / domain override
martin@Mint-VM:~$ host computer.company.local
Host computer.company.local not found: 2(SERVFAIL)Check which dns server is used. The result is the address of the local dns service. Strange, but on Debian with working dns override resolution the result is the same.
martin@Mint-VM:~$ nslookup
server
Default server: 127.0.0.53
Address: 127.0.0.53#53Set dns server to the pfsense ip address
server 192.168.0.x
Default server: 192.168.0.x
Address: 192.168.0.x#53Ask for computer in network B again. Result is correct
computer.company.local
Server: 192.168.0.x
Address: 192.168.0.x#53
Non-authoritative answer:
Name: computer.company.local
Address: 192.168.0.z -
@nobugswanted said in Domain Override works for Debian and Windows but not Ubuntu:
Check which dns server is used. The result is the address of the local dns service. Strange, but on Debian with working dns override resolution the result is the same.
martin@Mint-VM:~$ nslookup server Default server: 127.0.0.53 Address: 127.0.0.53#53This just shows, that the computers use a local DNS resolver. But the question is, which upstream server they use in fact.
I suspect, that the Ubuntu doesn't use your pfSense.To ensure, that DNS requests from all devices go to your pfSense, just redirect them to your server with a NAT port forwarding rule.
Best practice is to configure the server to listen on localhost and port forward DNS to 127.0.0.1 then. -
@viragomann All client computers in network "companynet" are configured via the dhcp server service of the pfsense. They all (windows, debian, ubuntu, ...) get the same dns server information. The DNS server is the pfsense itself: 192.168.0.x in my example. This is the server I manually set in my example.
I do not understand why the (debian and ubuntu) computer show 127.0.0.53 as dns server.
Do you have an idea where / why this 127.-IP address appears from?I am sure that the 127.0.0.53:53-service asks the local pfsense: I can resolve names like computer.companynet that have a static DHCP-mapping in the pfsense DHCP-server.
So your NAT suggestion is not applicable in in case.
At least I think so. Please correct me if I'm wrong.Thanks
Martin -
@nobugswanted I've found this article: https://unix.stackexchange.com/questions/612416/why-does-etc-resolv-conf-point-at-127-0-0-53#
It describes the problem and some "solutions".
/run/systemd/resolve/resolv.conf contains the correct IP-address of my pfsense . But /etc/resolve.conf is a link to /run/systemd/resolve/stub-resolv.conf
In my scenario, companynet has nearly 100% BYOD (Bring Your Own devices). I have no control over them.
Furthermore this thoughts do not explain, why standard (i.e. non domain override) dns requests are answered correctly and domain overide ones fails.
Any ideas?
Thanks
Martin -
@nobugswanted said in Domain Override works for Debian and Windows but not Ubuntu:
All client computers in network "companynet" are configured via the dhcp server service of the pfsense. They all (windows, debian, ubuntu, ...) get the same dns server information. The DNS server is the pfsense itself: 192.168.0.x in my example. This is the server I manually set in my example.
No doubt about that.
But most probably your Ubuntu use an outside DNS though.To verify, on the computer run an nslookup with stating your local DNS:
nslookup computer.company.local <DNS Server IP>Do you have an idea where / why this 127.-IP address appears from?
It's the localhost IP. As mentioned, I guess, it is running a local DNS resovler.
So your NAT suggestion is not applicable in in case.
At least I think so. Please correct me if I'm wrong.Why not?? It's easy to set up and it's bullet-prove. The NAT rule catches any DNS request and redirects it the the local server. The client doesn't get any note realize this, since pfSense responses with the origin destination IP.
I have also configured port forwarding rules for DNS and NTP. Looks like this:
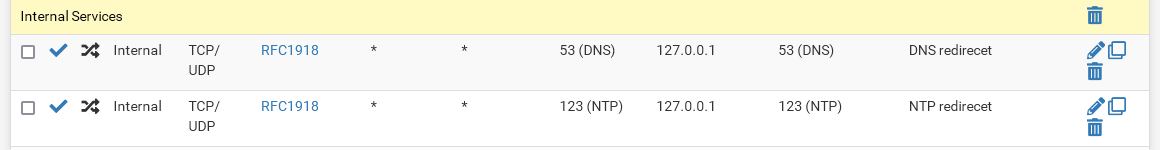
-
@viragomann I'tried to set up this rule. First defines the alias private_networks.
I wasn't succesfull....DNS requests havn't been redirected.I wasn't able to finde the menu that you have screenshot. It is not below firewall/rules or firewall/nat.
Attached is the screenshot of my two nat rules.
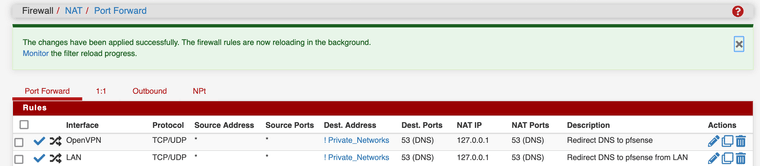
-
Yes, it's a port forwarding rule, as mentioned. "Internal" is an interface group in my configuration.
@nobugswanted said in Domain Override works for Debian and Windows but not Ubuntu:
First defines the alias private_networks.
Any reason to access to other devices than pfSense?
I wasn't succesfull....DNS requests havn't been redirected.
Did you verify if the port forwarding worked?
Or do you mean, the DNS still isn't working? -
Any reason to access to other devices than pfSense?
I followed https://docs.netgate.com/pfsense/en/latest/recipes/rfc1918-egress.html and https://docs.netgate.com/pfsense/en/latest/recipes/dns-redirect.html
I wasn't succesfull....DNS requests havn't been redirected.
Did you verify if the port forwarding worked?
How can I verify this?
Or do you mean, the DNS still isn't working?
Yes, DNS does not work better than before creating the rules. I'am offsite now. So I've tested from a VPN-computer only. Maybe the solution you proposed will not work on VPN-clients. They might send the dns request directly to their choosen dns server, not through the tunnel.
I'll check for on-site compters by the end of the week.
-
@nobugswanted said in Domain Override works for Debian and Windows but not Ubuntu:
Did you verify if the port forwarding worked?How can I verify this?
You can sniff the traffic on the localhost with Diagnostic > Packet Capture.
Select the localhost interface and enter 53 at the port filter, start the capture and run a DNS lookup on the concerned machine.So I've tested from a VPN-computer only. Maybe the solution you proposed will not work on VPN-clients.
Did you push the DNS to the VPN clients or configure the client itself to use your DNS?
Which VPN?