Hardware Crypto Support Missing AES-GCM?
-
@mcury - thanks for the suggestion, but unfortunately running that command didn't show too much beyond that the /dev/crypto and Intel RDRAND engines are available.
I also ran
kldstatand see that theaesni.ko,iimb.ko, andcryptodev.komodules are loaded.Could this be UI bug? Is there any other way to check? Thanks again.
-
@tman222 said in Hardware Crypto Support Missing AES-GCM?:
Could this be UI bug? Is there any other way to check? Thanks again.
I think so.
I've also upgraded from 23.01 to 23.05 and the IPsec MB wasn't showing.After that upgrade, I decided to use a SSD and not the eMMC, I had to reinstall my system, so did a 23.05 clean install.
After that, IPsec MB became available in the GUI.
So, not sure if this is a bug but after a clean 23.05 install, GUI started to show the other options.
Here is what jimp said about this:
https://forum.netgate.com/topic/180341/surprise-swap-and-ipsec-mb-crypto?_=1685031490197 -
Thanks @mcury - I'll wait for others to hopefully chime in on this as well, otherwise I'll go ahead and raise a ticket on Redmine.
@jimp @stephenw10 - any ideas on this?
Thanks again for your help.
-
@tman222 I think I found the problem.
In /usr/local/www/includes/functions.inc.php, function crypto_accel_get_algs() the code to handle duplicates in the arrays seems to be broken, which leads to exclusion of algorithms that are included in both CPU and IIMB. That the algorithms comes out unsorted is also an indication the logic is broken.
I changed the function to look like this, which works as expected. Unfortunately I can't provide a diff as I forgot to take a backup...
function crypto_accel_get_algs($crypto) { $algs = []; foreach ($crypto['accel'] as $accel) { /* skip these... */ if (!$accel['present'] || !$accel['enabled']) continue; $algs = array_merge($algs, $accel['algs']); } /* return early */ if (empty($algs)) return (gettext('Inactive')); /* sort alphabetically */ ksort($algs); /* now flip back so keys become values, done twice to remove duplicates */ $algs = array_flip($algs); $algs = array_flip($algs); /* format and return the algs string */ return (implode(',', $algs)); }GUI now shows:
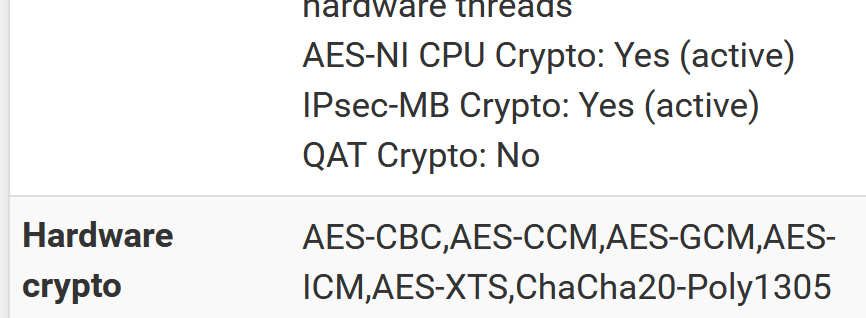
-
Thanks @pst - this look like it could be fixed via simple patch to that PHP function. Do you want to go ahead and raise a Redmine bug report on this (since you already figured out the fix) so that the Netgate developers can see it? Thanks again.
-
@tman222 Yes, I can create a bug report
-
@pst said in Hardware Crypto Support Missing AES-GCM?:
@tman222 Yes, I can create a bug report
Thanks @pst - can you post the link here to the Redmine ticket once done? Thanks again for all your help with figuring this out.
-
@tman222 https://redmine.pfsense.org/issues/14417
-
Thanks for this! I've created a patch file here in case it helps anyone!
https://gist.githubusercontent.com/jackyaz/1fc79ab30dba254af73a85e48551a1e4/raw/e3f241e8109904196d6563bb000042d521bccbc6/crypto_algs_dashboard.patch
-
@jackyaz Thank you was wondering about this with my 23.05.01 and found this post. Fixed my issues. On the 2100 if you enabled both
IPsec-MB Crypto: Yes (active) SafeXcel Crypto: Yes (active)Chacha20-Poly1305 would vanish off the system when IPsec-MB was marked inactive.
However with both enabledBefore Patch
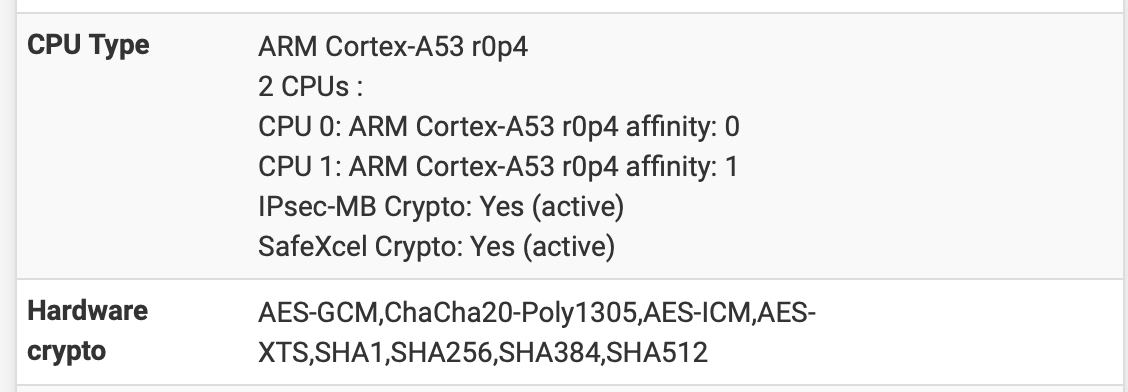
AES-GCM,ChaCha20-Poly1305,AES-ICM,AES-XTS,SHA1,SHA256,SHA384,SHA512After Patch...
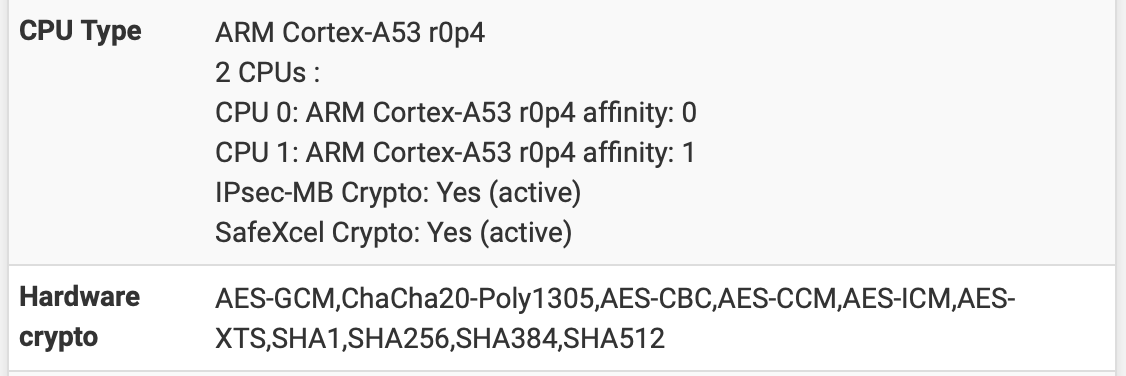
AES-CCM and AES-CBC is backAgain cbc is an older cipher
-
Is this of concern /* duplicates are ignored because keys must be unique */