IPSECD VPN Phase-2 configuration disappearing
-
Mmm, that does look like it in that case if the last config change was removing a P1. That doesn't seem to be the case for OP here though.
-
Same thing for me as well today , i'm running pfSense+ on Netgate 7100
24.11-RELEASE (amd64)
built on Sat Jan 11 18:11:00 EET 2025
FreeBSD 15.0-CURRENTI have 2 x phase2 entries on the configuration page , but only one is showing on the status page.
I'm not sure what's causing this, it was fine until earlier today and i didn't make any changes to the IPSec configuration. -
If both are showing in the config page that's a different issue.
What do you actually see in the status page?
Are there any errors in the logs?
-
@stephenw10 should i create a new topic ?
I don't see any errors in the logs , the bit that looks strange to me is circled with red , note that we have two connections one is ike v1 the other is ike v2 with different partners.
The part i circled , it;s because the description doesn't match the configuration page and also the id says con2 instead of con2_1 or something like that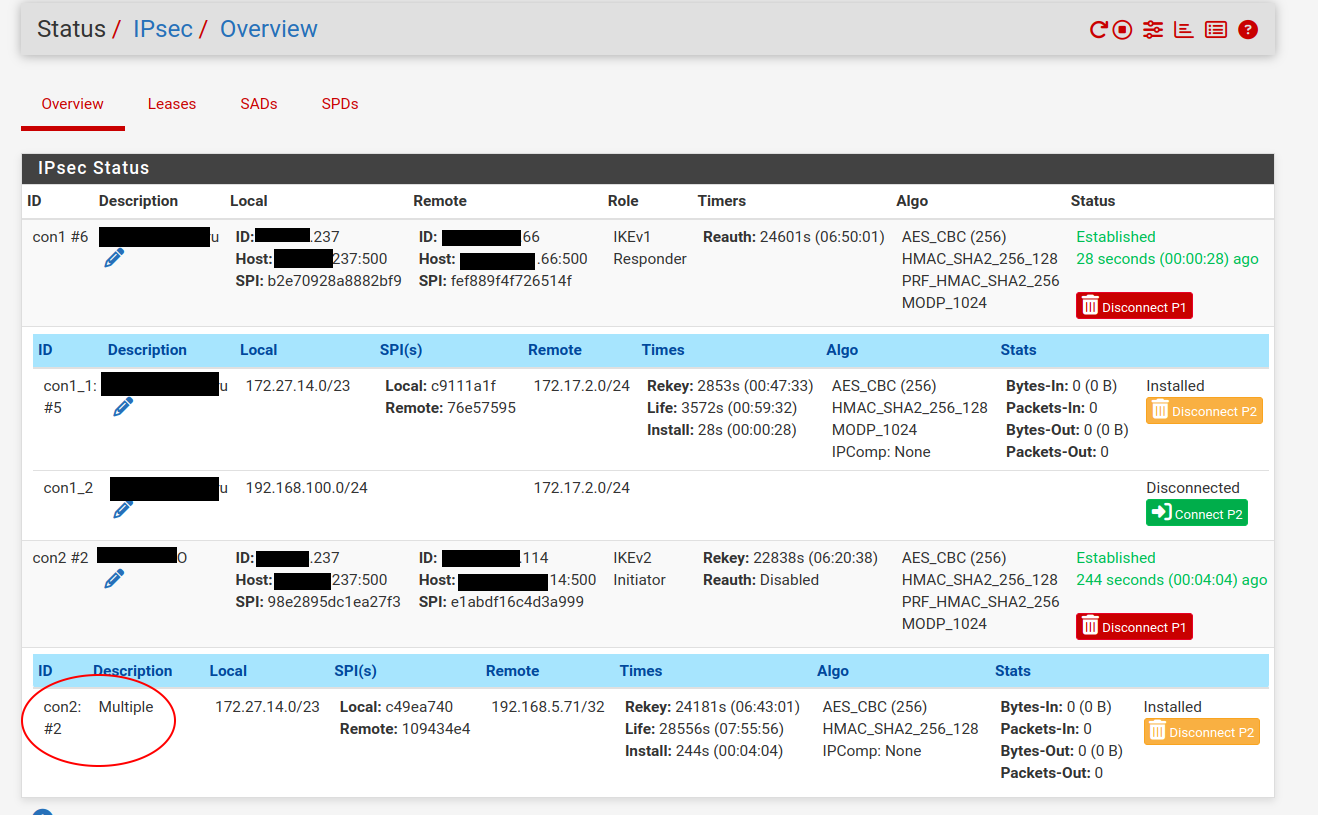
-
btw , is there any file i can edit from the command line and remedy this ? ... maybe the UI is acting out or it's confused by something ... as i said earlier i haven't changed the configuration for IPSec for a while before this happened
-
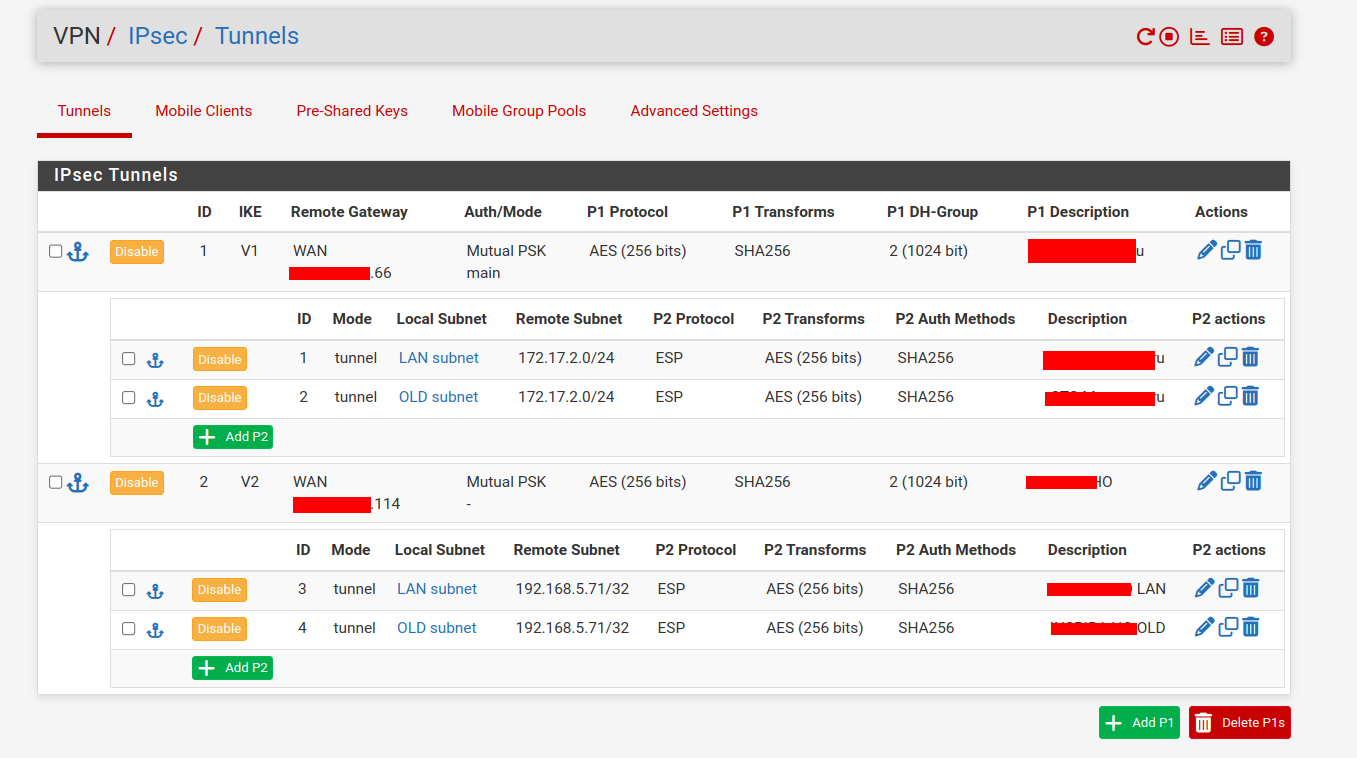
Even weirder , because i really needed to fix the connection asap , i deleted one of the p2 entries from the configuration and the status shows both as connected/installed now

I think it's safe to asume this is some kind of bug , something got stuck somewhere at some point (maybe at a software upgrade) and probably manually need to be cleaned up and recreated the configuration from scratch
i only have this single phase2 entry now for this connection
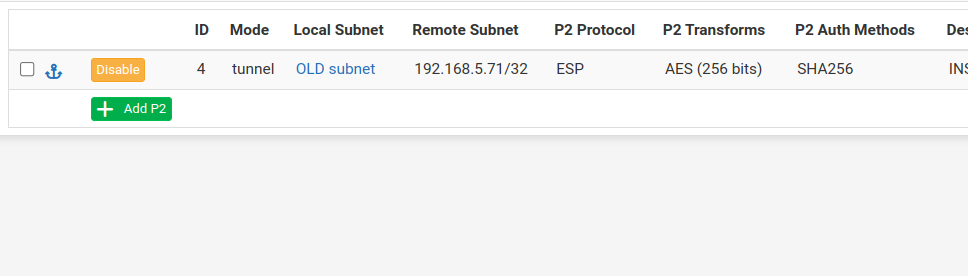
and the status page shows (note that both are showing the same description now)
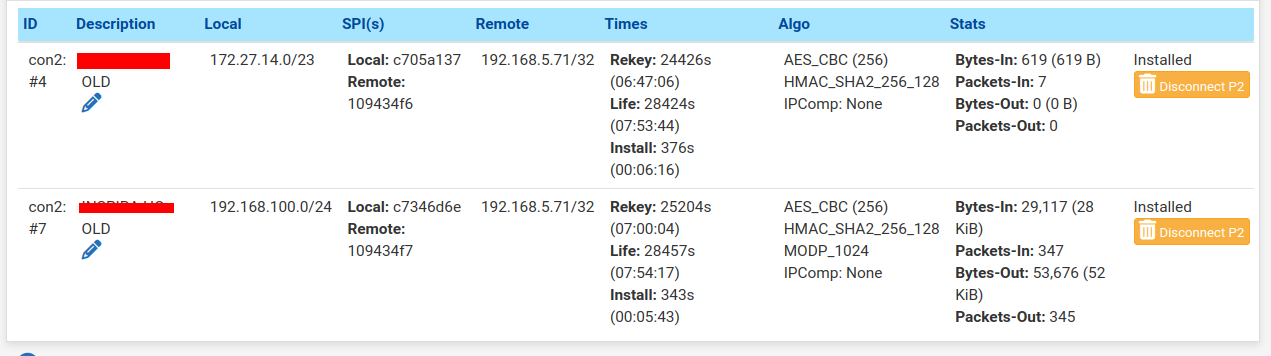
-
Hmm, that does seem odd. I would at least try re-saving those P2s and disable/re-enable the P1.
You could be seeing combined traffic selectors if whatever is at the other end was upgraded and now supports that. Setting 'split connections' on the P1 would return the previous behaviour.
-
@stephenw10 said in IPSECD VPN Phase-2 configuration disappearing:
supports
i confirmed with the partner that this is not the case on their end
also i did these disable/enable p1 and p2 entries before removing one of the p2 entry and it has not affected the status of the connection in any way , even restarting the ipsec daemon at each step
it's still working now but i would like to have a match between what's in the configuration and what's actually showing on the status page, any ideas what to look for on the command line maybe ? -
Try stopping then starting the ipsec service. Restarting it only actually reloads the config.
But ultimately check the logs. See what P2s are establishing.
Check the output of:
ipsec statusallat the CLI. -
So what is the consensus here @stephenw10, Is this bug still present in 24.11?
I thought it would be solved by this version, but since being notified of new issues in this ticket I'm holding off deleting any IPSec tunnels until I know the risk is gone.
-
@Tactis said in IPSECD VPN Phase-2 configuration disappearing:
https://redmine.pfsense.org/issues/15970
As far as I know that is fixed in 24.11. I don't think aduzsardi was/is hitting that since the config still appears only the status is different.
-
@stephenw10 , perfect, thanks!
-
I also experienced a disappearing P2. Unfortunately, it is hard to say what triggered it because the other side has been down for 5 months and just became available again. They just brought it back up and I expected everything to connect automatically but it didn't. So I looked into what could cause it and found the P2 missing. In that 5 months where the other side was down, my side had a hard drive failure and restore from autoconfig backup. Also, in the config history, wireguard has been automatically spamming the config history so I only have one day worth of true backups (but 30 copies of virtually the same thing thanks to wireguard).
I was able to find and decrypt a much older config manually, view the P2 XML, and recreate the P2 manually.
-
We are having this same issue on 2.7.2 on a Hyper V VM. Seems this is a new issue after upgrading from 2.7, but can't be 100% sure of that. However I can report that as we've been moving some policy based VPNs to VTIs (and in that process deleting certain P2s under a given P1, or deleting all the P2s and P1s related to the site we're moving to VTIs), other P2s, for separate P1s that we've left untouched as policy based VPNs, will disappear. This has happened repeatably, each time we delete another set of P2s. So late night I moved five VPNs from policy based to VTI, and I had to rebuild 16 P2s (most of our policy based tunnels have four P2s each).
Anyway, just adding to the discussion.
-
Adding to discussion.
Same for me as scurriers post from March 9.
P1 + P2 running for years, now all P2 disappeard from a specific P1 config.There are still 9 of 12 P2 established though of that P1.
Will restore it from documentation. -
That was also after making some other config change?
In which pfSense version?
-
Hello. We had the same issue yesterday night 14th of July 2025 to today 15th July 2025.
We have 5 IPSEC VPN tunnels entered in our v2.7.2 pfSense (all with P2 entries), of which 3 IPSECs (P1s) were productive. The pfSense itself is hosted on a VM in Microsoft Azure and it has an uninterrupted runtime of 375 days now.
Somewhen in the night, nobody was working at the company, the pfSense lost all underlying P2 entries on two IPSEC P1 entries (one of these tunnels was deactivated/non-productive, but the other one was productive).The business critical outage was reported to me in the early morning and I nearly needed two hours to find the root course of the outage, because I could not imagine the tunnel config could have changed itself. So at first I investigated the internet connections, also with our ISP, and restarted local hardware, but that did not help.
I checked the logs to make sure the pfSense environment didn´t get compromised, but there are no logins on the webgui or via ssh recognizable for us.
Though I was able to observe an anomaly in the logs. I attached the screenshot so there is some basis to investigate the issue.Had to insert as a picture instead of reading and copy friendly raw code because the forum anti-spam flags it and prevents us posting...
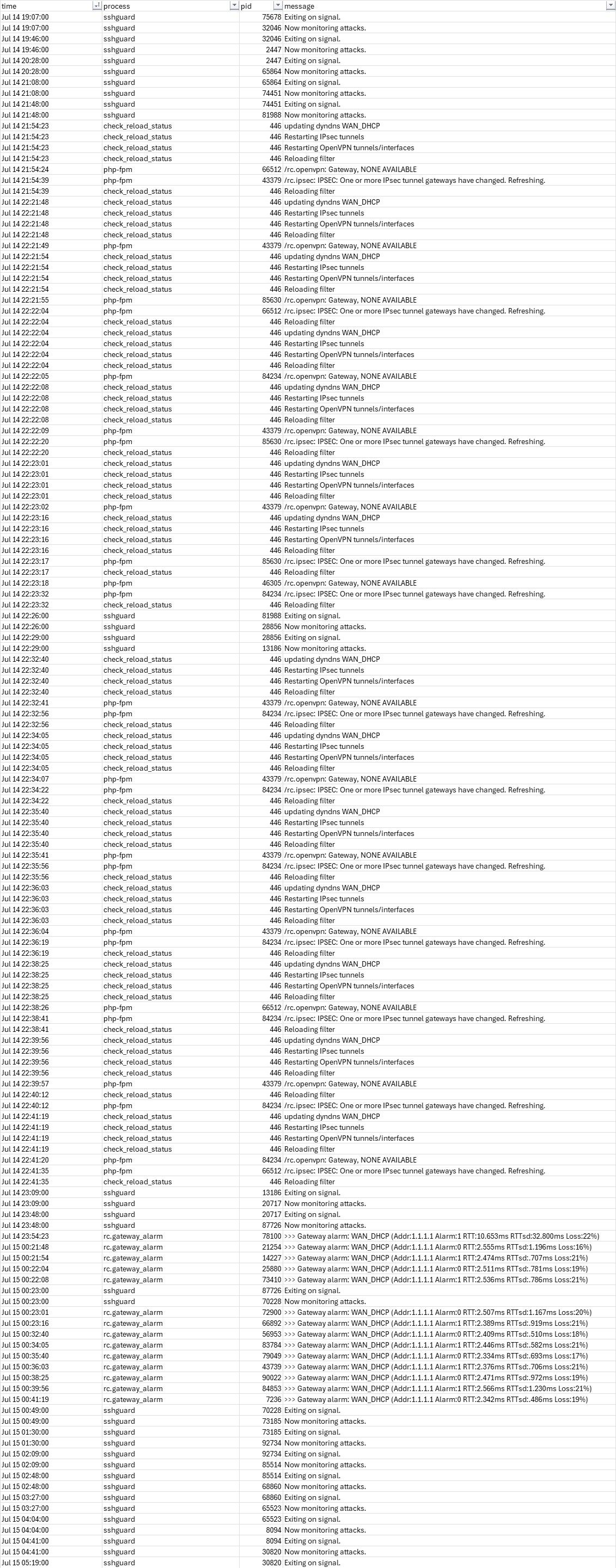
As from the current point of view, we assume there is a critical software bug leading to these deletions, because we can´t find a reasonable explanation on our behalf rn. Imo this should be further investigated by netgate with a high priority, please, because we don´t really understand what caused this self-destructive behavior of the pfSense application.
(For ourselves, we restored the P2 entries manually, so this is short-term solved for us now, but what if this issue strikes again? We have no feel of security on the reliablity of the application right now). Thanks in advance for your feedback and kind regards from Germany. -
Had they actually been removed from the config or just the running tunnels?
I don't see any logs showing a config change there. Nothing of note really except packet loss on the WAN
-
@baustoffewolf If I remember correctly from my experience, my P2s also disappeared spontaneously.
When I went combing through the config history, it looks like a change to an (unrelated) tunnel made months earlier when the bug had wiped out the affected P2 at that time in the config. I'm not sure what event causes the tunnel config to actually reload but it can be very far down the line.
-
It's possible the config was changed and not reloaded at the time if the usual process was not used. Somehow. Then later some other event caused IPSec to reload and pulled in the new config values.
There should still be something logged somewhere though.