issue with certificates
-
Hello,
Running pfSense+ 24.11 on Netgate 8200.
System/Certificates tells me I have a valid self-signed certificate (valid until 5/24/25).
Whenever I use a browser (Firefox or Chrome) access the pfSense GUI I get errors:
Chrome reports ERR_CERT_AUTHORITY_INVALID
Firefox reports some other error.What am I missing to fix this?
-
@hspindel said in issue with certificates:
Chrome reports ERR_CERT_AUTHORITY_INVALID
Firefox reports some other error.Certificates are signed by some kind of authority.
Your browser (all browsers) have a list with the known ones, they are from Microsoft, Apple, Google, Verisign etc. Here is a list.
So when you visit a web site on the net, and the root CA belong top one of them, the certificate of the web site is trusted by default.
You could do this test : your browser (any browser) has a folder somewhere where it stores a copy of all the CA's. It could be local to the browser, or the OS's system wide list.
Delete (no, move them to a safe place, elsewhere) all those that come from Microsoft and restart your browser. Then visit a Microsoft web site. It will now fail to show the site .... it doesn't trust microsoft anymore.Now you now what to do so the browser accepts the pfSense web server as 'valid' (no errors) : export the CA created on pfSense, the one used to create the pfSense webserver's certificate, and import it into your device (browser or cert storage).
From now on your browser will trust the certificate from pfSense as it was created by a CA that you've created. And, normally, you trust yourself. This CA is know as an auto signed CA certificate.How and what to do : look for the posts of the forum user johnpoz, or dig a bit in the pfSense documentation , you'll find how to export the CA and what to do with on your own device, the one you use to access pfSense.
Be ware : this isn't how pfSense handles certificate stuff, is common to everything related to certificates. It's part of the what https or actually any TLS communication is all about.
-
@hspindel Here is one of the posts @Gertjan is talking about - where I go over how to create a CA and have your browser trust certs signed by it
https://forum.netgate.com/post/831783
You can make it good for like 10 years if you want - browsers still ok with long valid certs with your own CA.
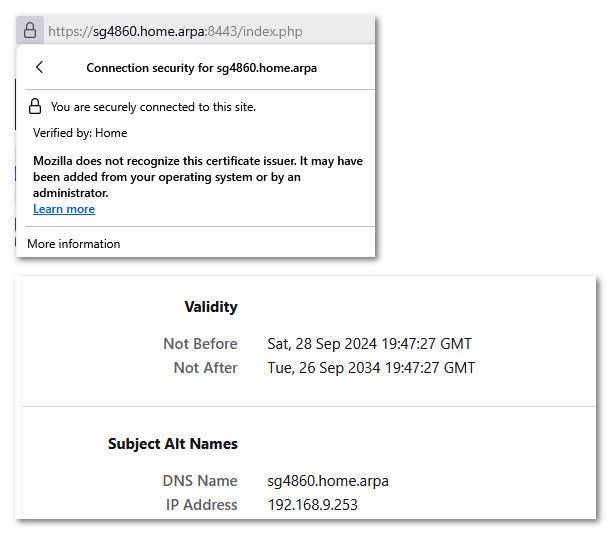
-
Yeah you can just add an exception in the browser to allow the self signed cert. You don't actually need to add the CA cert.
-
@stephenw10 firefox makes it easy to do that - but I think like chrome you have to type something there is no button to click to trust it.. Until you type the magic word ;)
-
Thank you all for your comments.
Not sure what I did, but Firefox stopped complaining.