OpenVPN External Connection
-
@LMorefield
So obviously the packet filter blocks it.
Enable the logging in of the default block rule, Block Bogon Networks, Block Private Networks and as well other block rules if any and check the firewall log after trying to connect.Do you have a multi WAN set?
Is there a router in front of pfSense? -
@viragomann
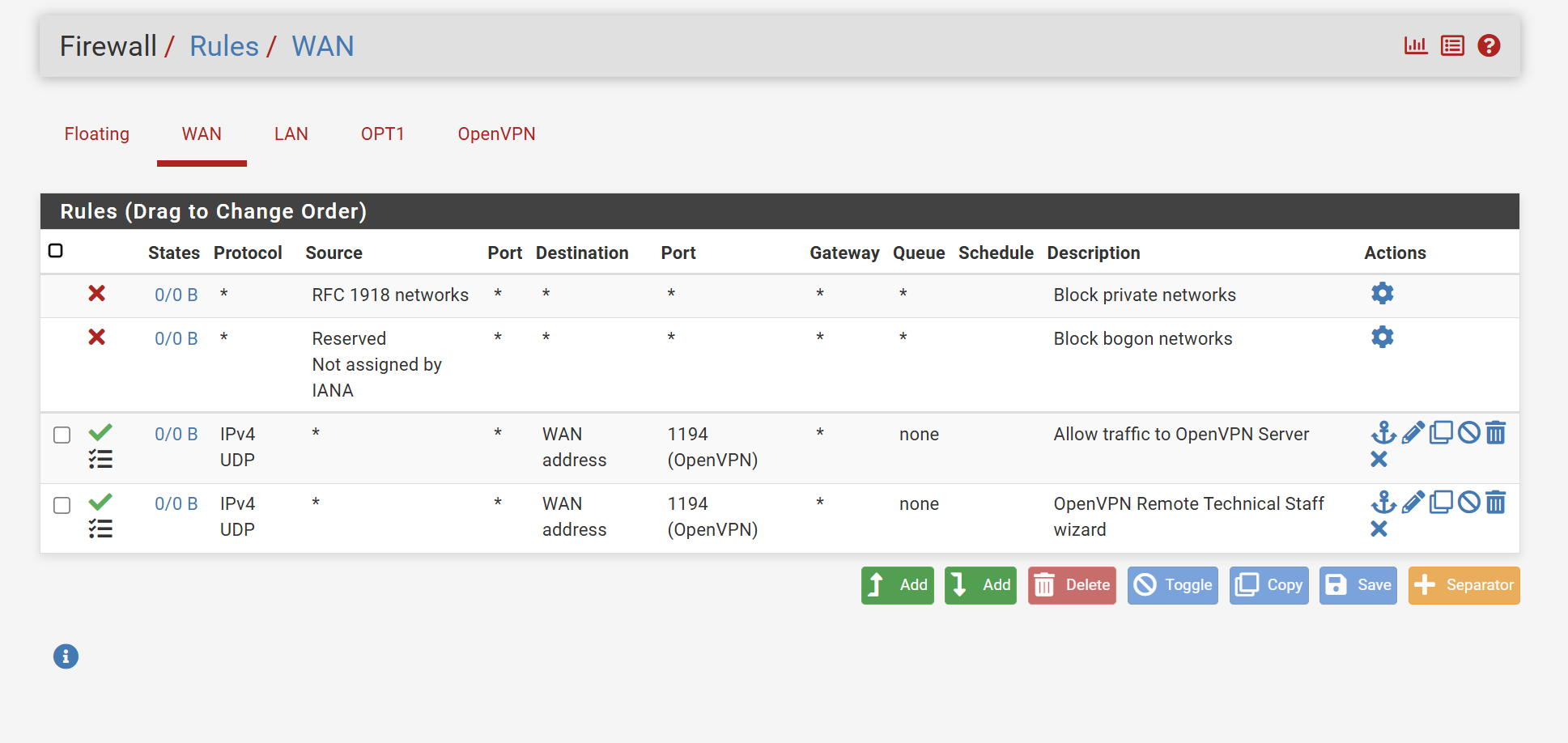
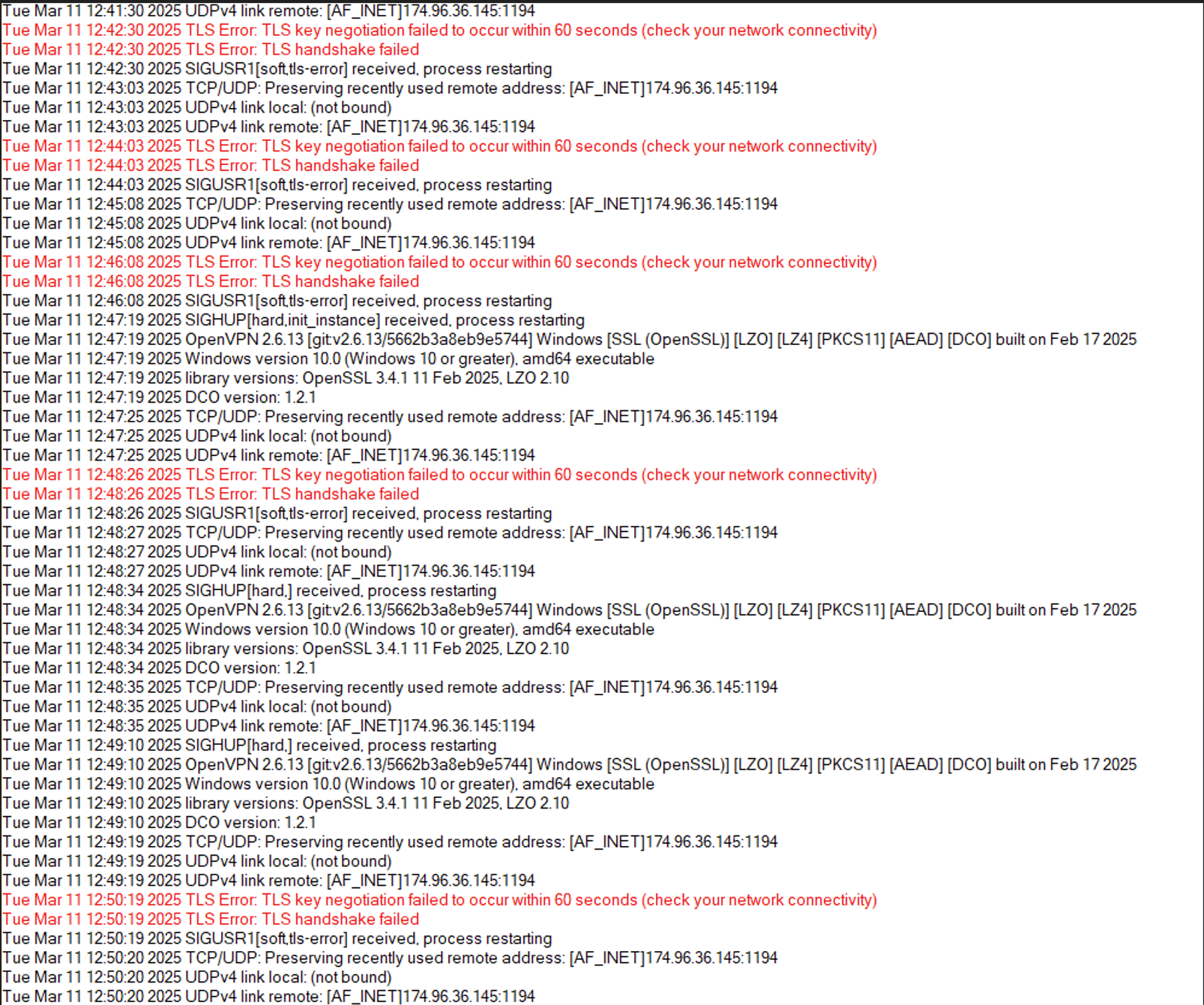
Below are logs after enabling the logging of the default block rule. I don't believe I have multi WAN set. No router in front of pfSense, only a modem from the ISP which is in bridge mode by default. ISP also isn't blocking any ports or traffic, it's wide open. Thanks for your help!
-
@LMorefield
Did you even add a pass rule allow OpenVPN access?
You log shows nothing but default deny. -
Mmm, were you actually trying to connect during the 4 mins covered by that log?
You can enable logging on the OpenVPN pass rule on WAN to be sure traffic is reaching you.
-
@viragomann
Yes,
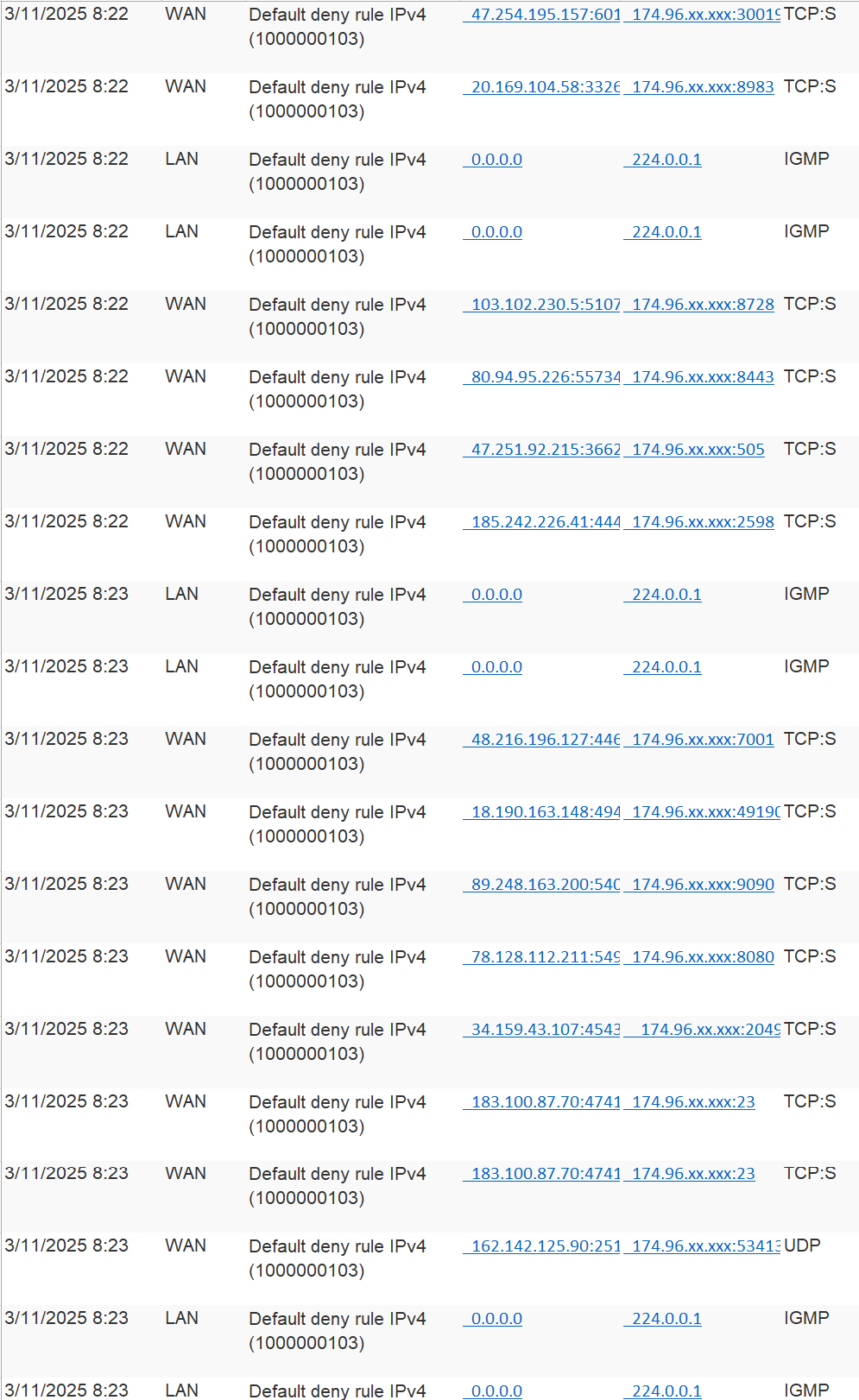
Here's a screenshot. When I test the port (1194), it shows it's closed. Also, that 174.96.xx.xxx is the dns I setup through duck dns. Is that where these attempts are being denied?
-
@stephenw10
I was indeed trying to connect. I have logging enabled, I've never seen any attempt in the log unless I disable the firewall which then the log will show the connection.
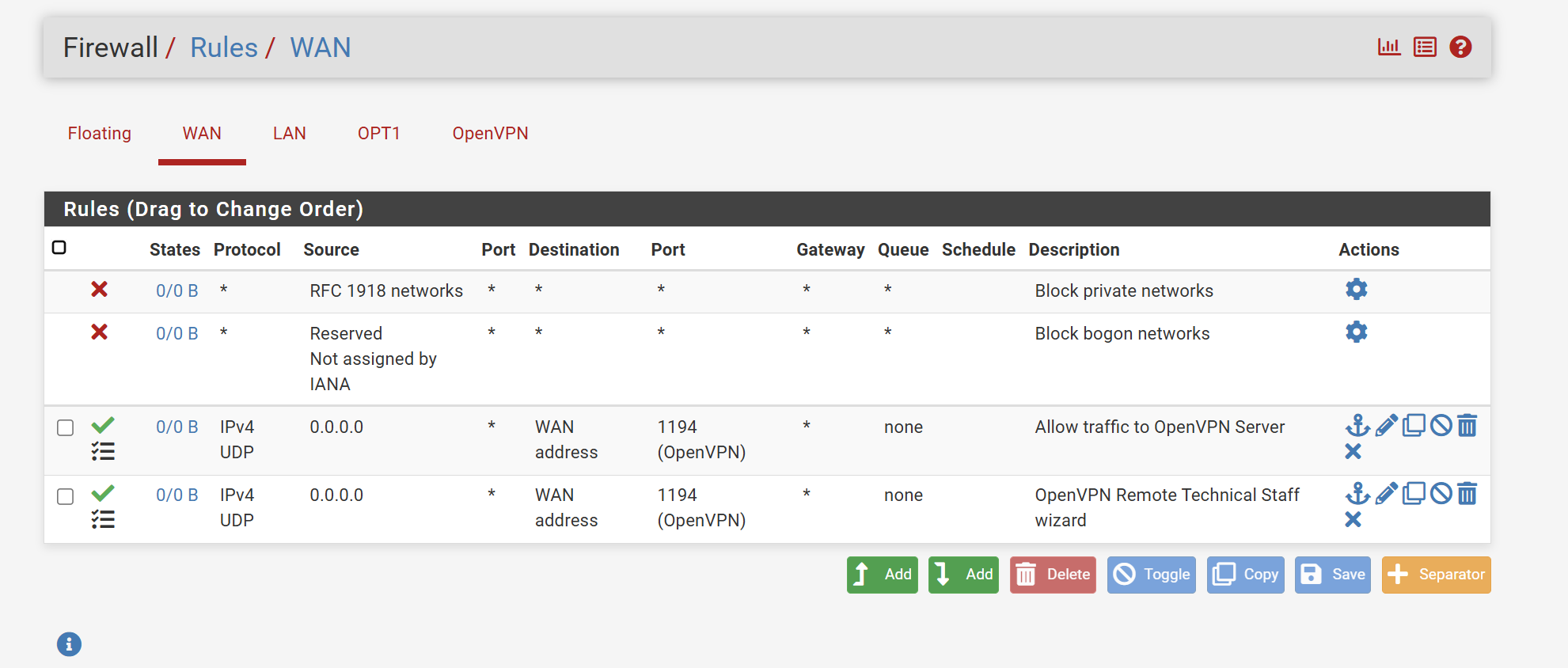
-
@LMorefield
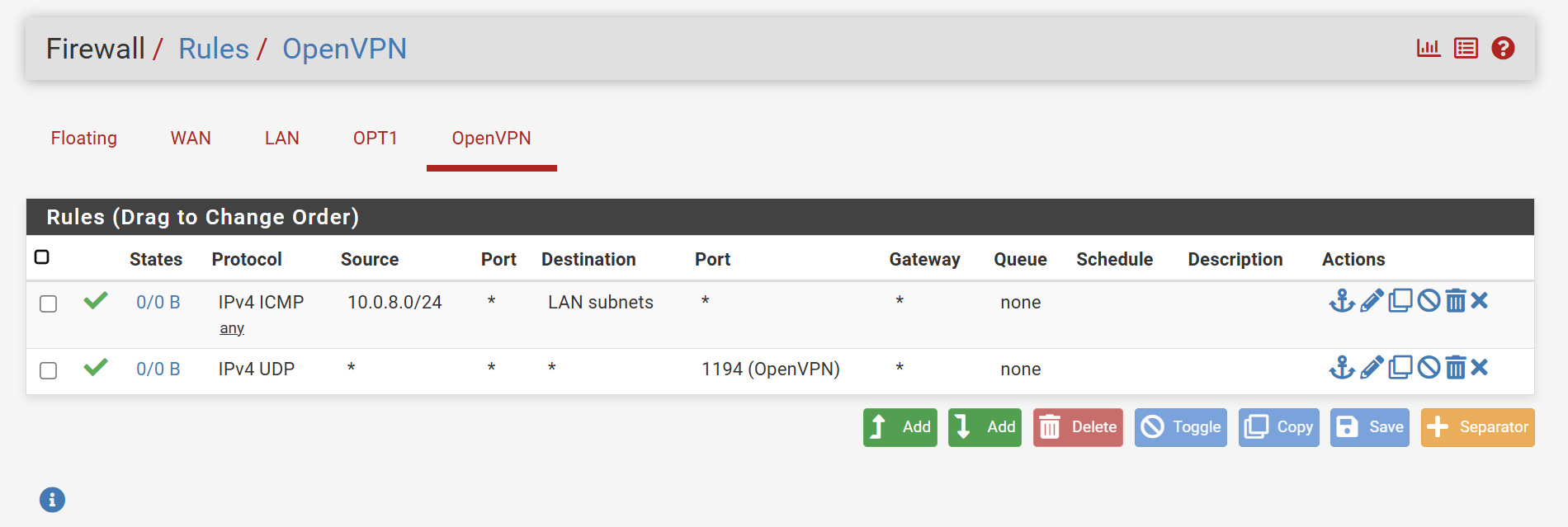
Try to set the source in the WAN rule to "any" instead of 0.0.0.0.On OpenVPN you only need a rule to allow access from the tunnel network to your LAN subnet.
The rule for port 1194 is not needed there. -
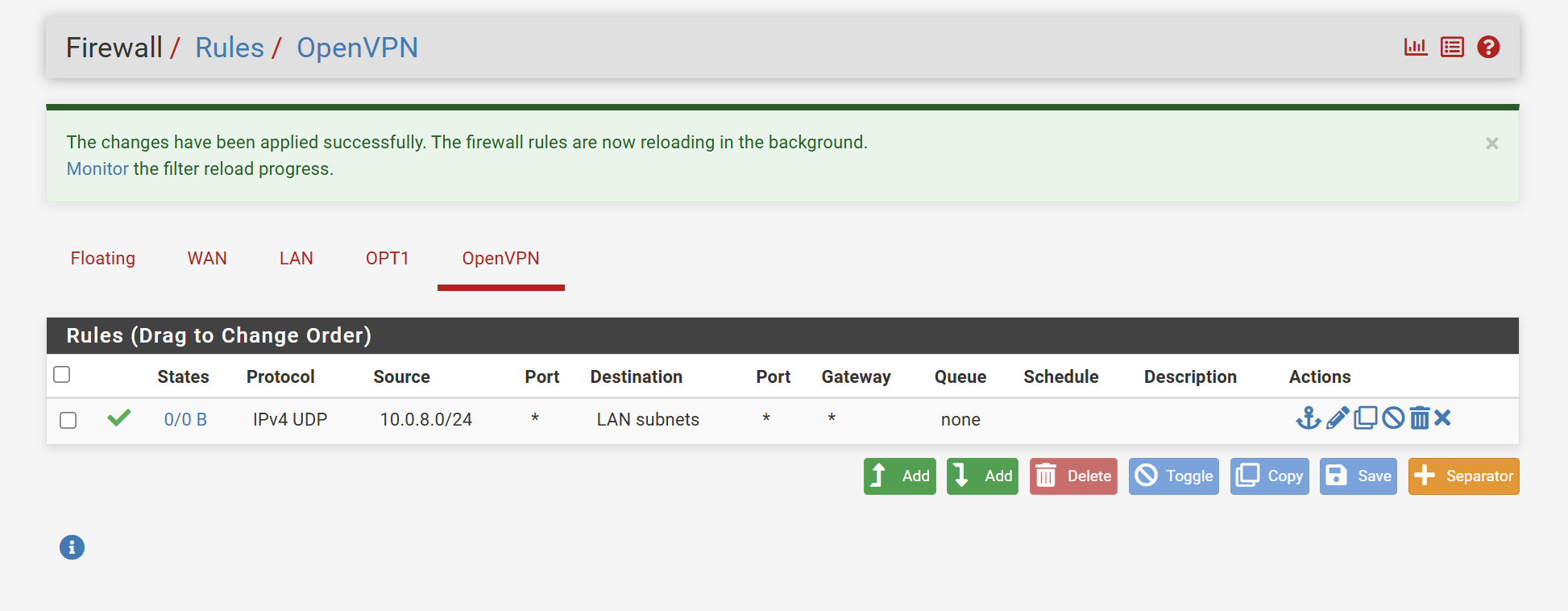
I'm currently trying to connect, however, nothing is registering in the logs for OpenVPN.
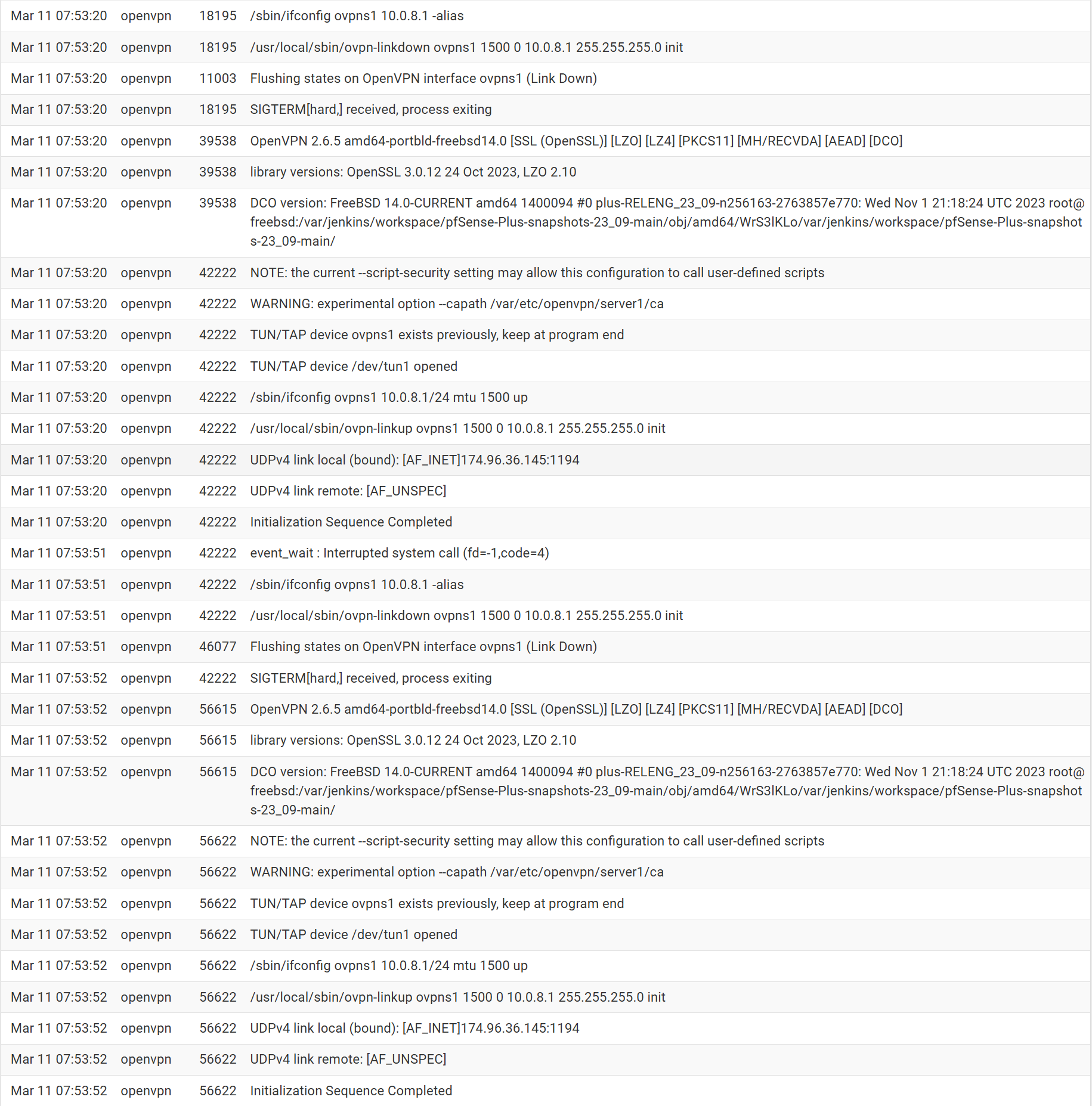
-
@LMorefield
What shows the client log? -
-
You only need one of those rules on WAN, they are the same.
You can see there are 0 states and 0 bytes shown on those rules implying no traffic has hit them.
You can't test the a UDP port like that since nothing is expected to rely there.
I would run a packet capture on the WAN filtered by port 1194 and see if any traffic is arriving from the client at all. It might be blocked somewhere upstream.
-
I got rid of one of the rules on WAN. Ran a packet capture, below are the results.
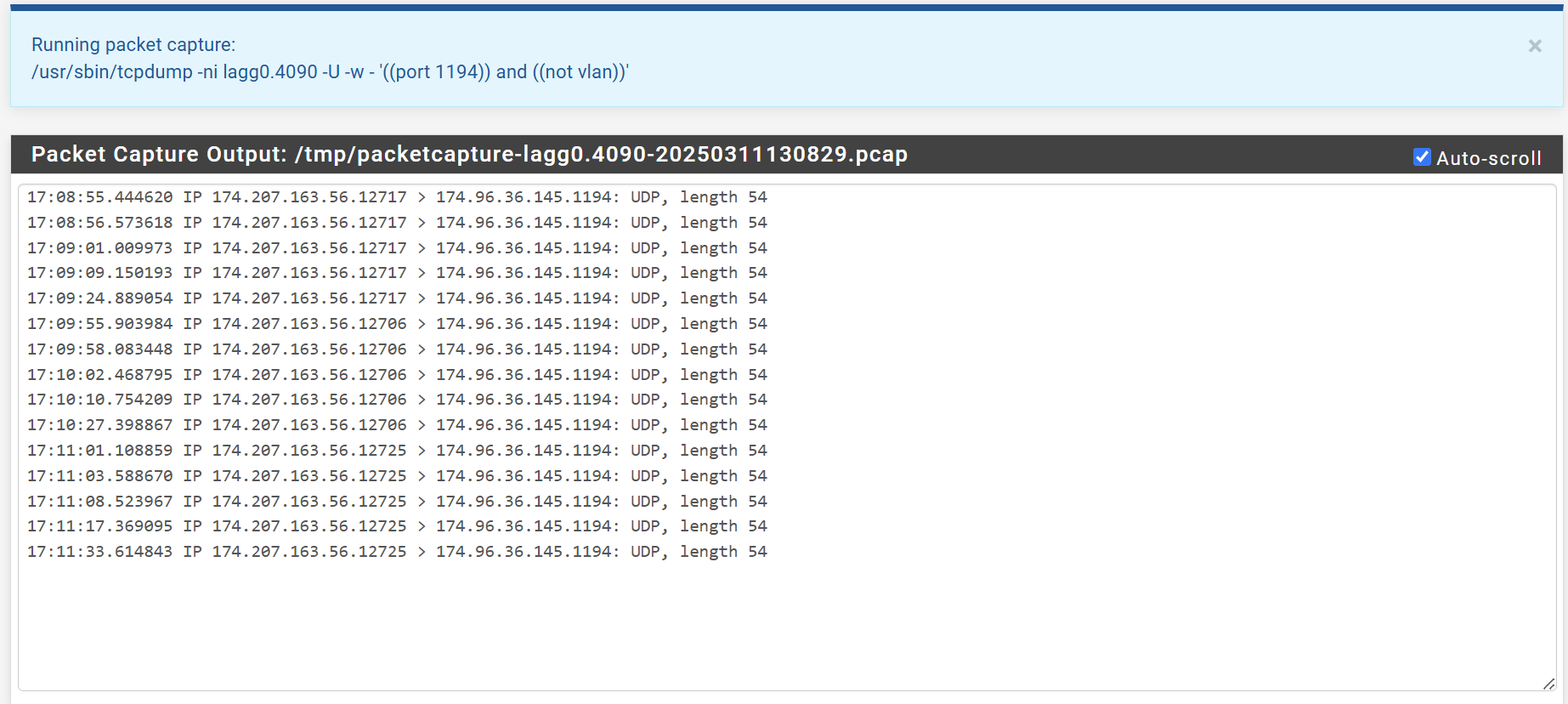
It looks like OpenVPN is listening on 1194
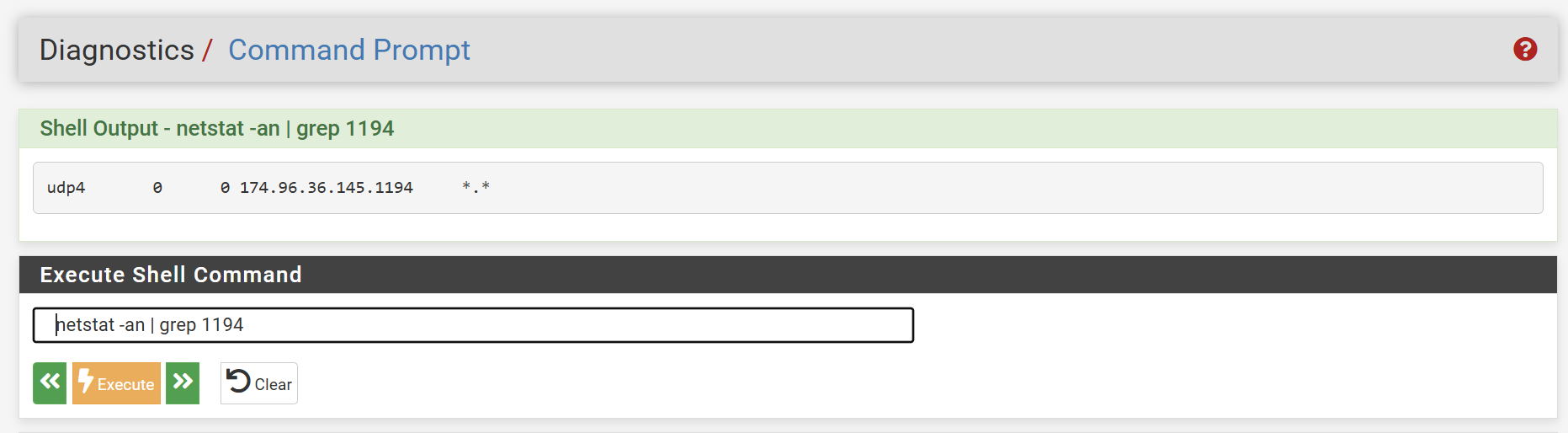
-
@LMorefield
So the packets from the client are arriving, but your OpenVPN server doesn't respond. If there is nothing to see in the logs of the clients access the server obviously doesn't get the packet or is dead meanwhile.Did you forward the packets to anywhere else by any chance?
Do you have any port forwarding rules? -
I didn't forward the packets elsewhere when doing the packet capture.
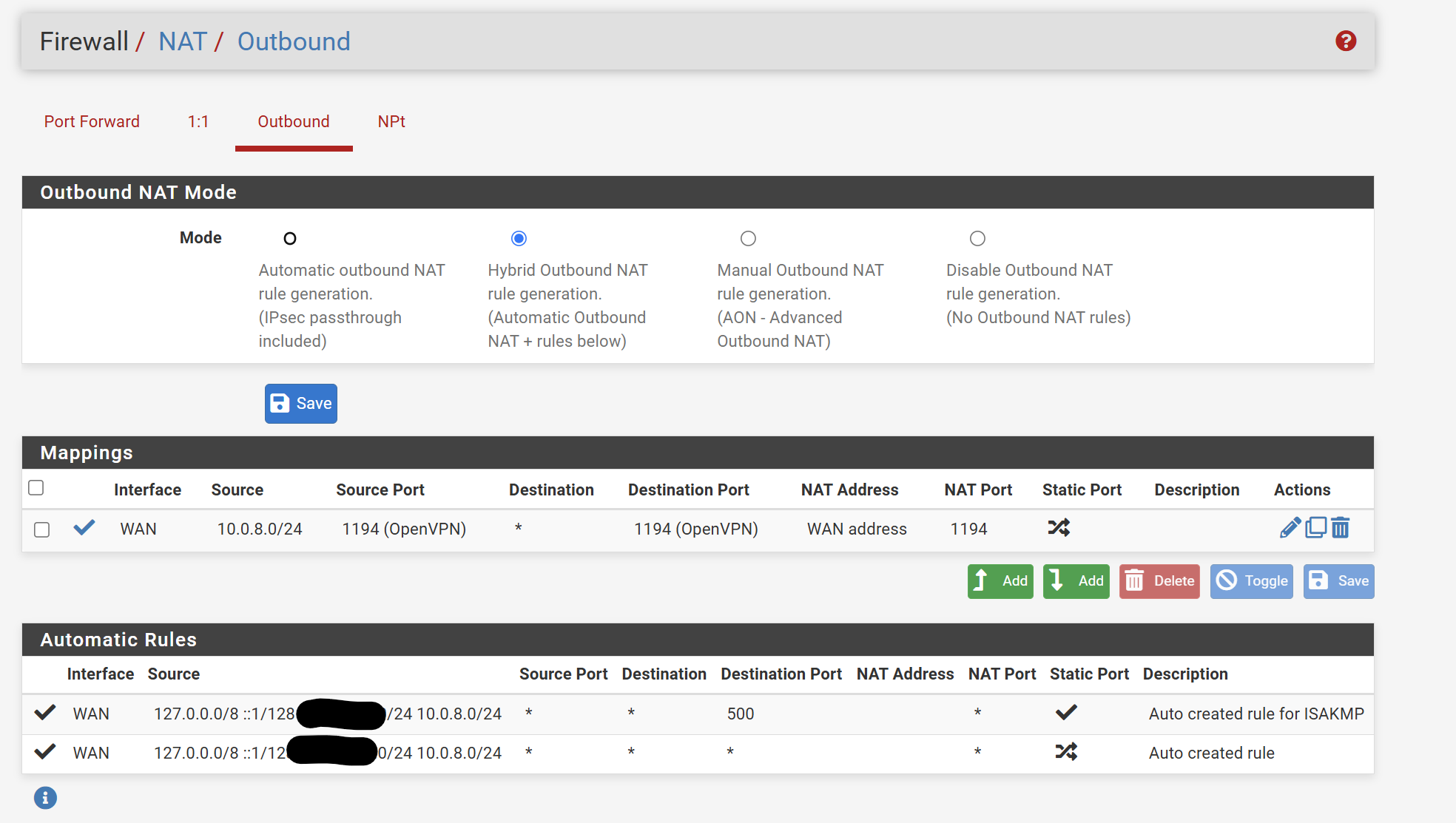
These are the port forwarding rules I have setup.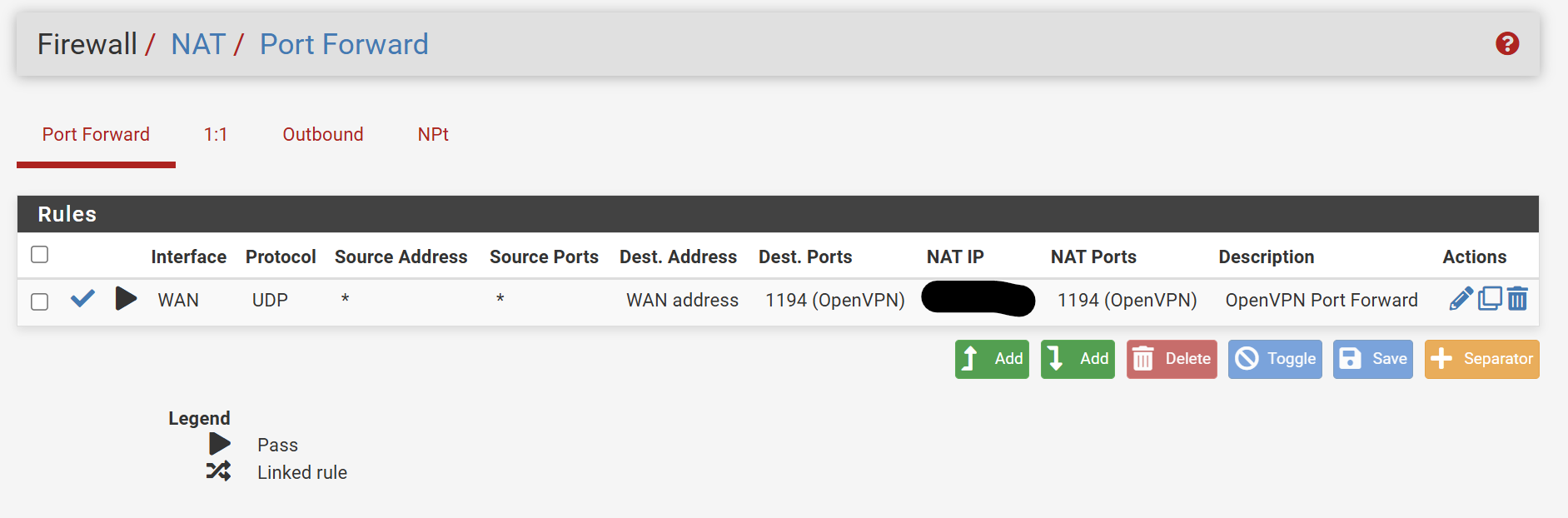
-
@LMorefield
But your screenshot shows port forwarding of UDP 1194 on WAN. So remove or disable this rule.
You server is listening on the WAN IP. If you want to use any other change the server settings.The outbound NAT rule affects outbound connections only. It has no impact on the VPN server.
-
@viragomann Done!
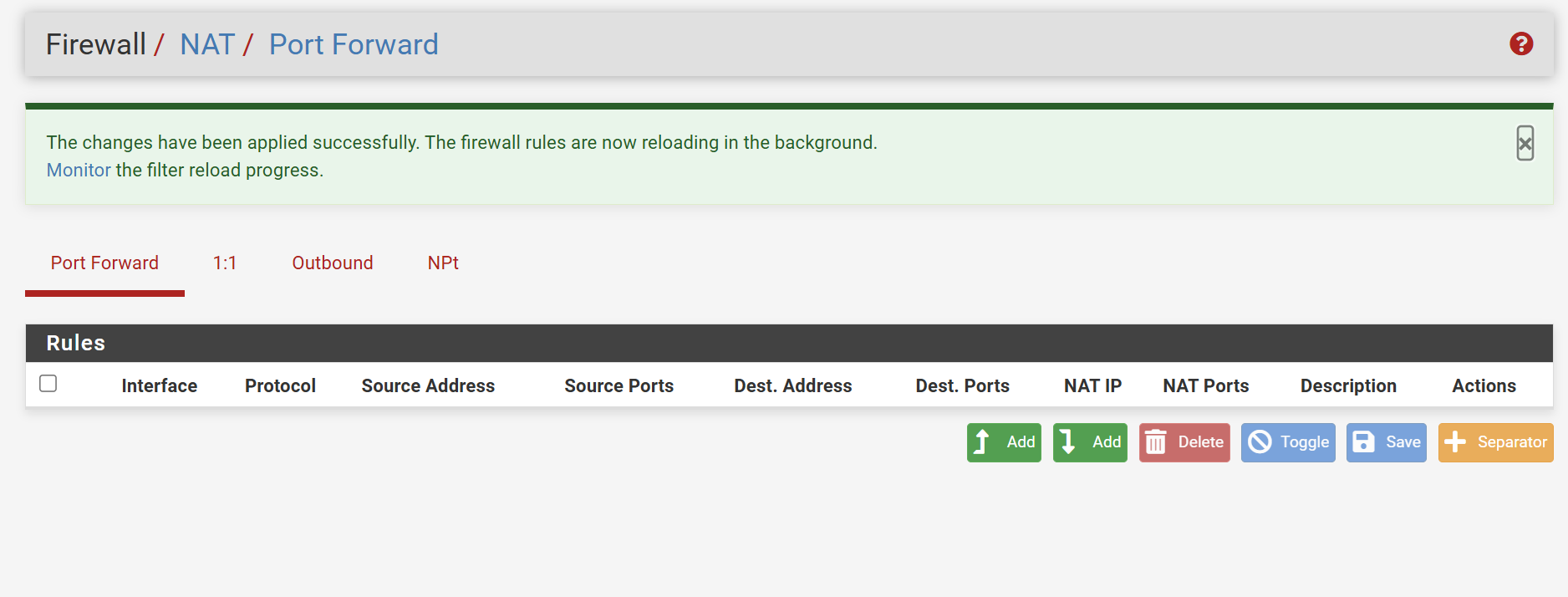
I went back to start capturing packets and the VPN actually connected. It says no internet access and isn't allowing me to access anything, but it's finally connected!
I disconnected an reconnected multiple times to ensure it's connecting.
Thanks again for your help!
Any suggestions on how to continue configuring so I can access my network and workstation and utilize rdp?
-
@LMorefield
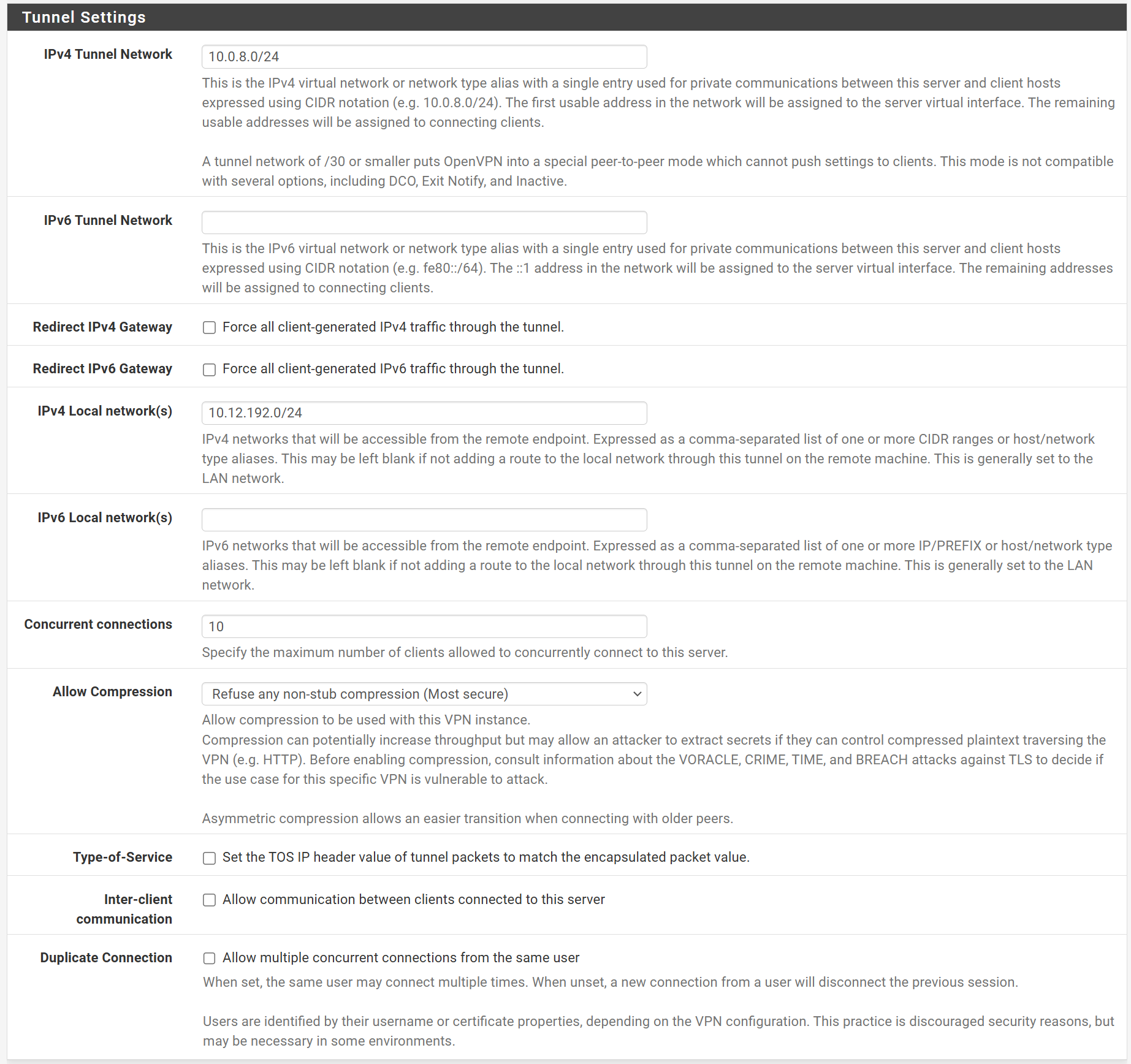
You OpenVPN rules allow access to the WAN subnet only. So I assume, this is what you want. And you don't want to redirect the whole upstream traffic from the client over the VPN.So did you have checked "redirect gateway" in the server settings?
If so remove this check and state you LAN subnet at "local networks".Also if you provide a DNS server in the VPN settings, ensure that you allow access to it.
-
@viragomann I'm looking to utilize the network once I remote into it, and mainly to access my workstation remotely using RDP. If the traffic going through the VPN is adverse, I can do without routing the traffic through the VPN.
I could not find the "redirect gateway" setting in the server settings.
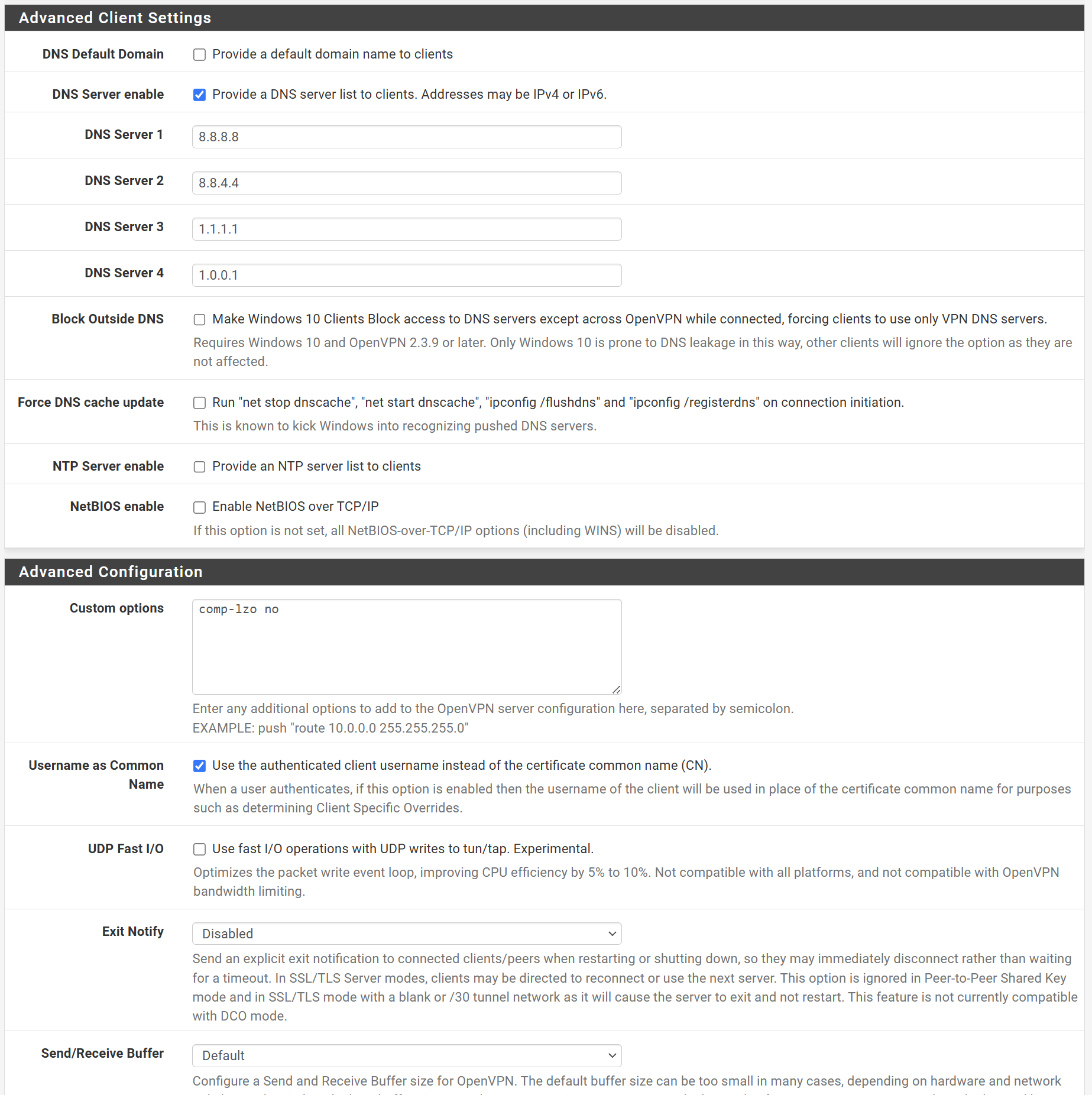
I added DNS servers in the VPN settings and opened it up I believe.
-
@LMorefield said in OpenVPN External Connection:
If the traffic going through the VPN is adverse, I can do without routing the traffic through the VPN.
This depends on your needs. Some want to redirect all traffic over the VPN to use the servers WAN IP to go out to the internet.
If you only intend to access the local networks stay with split tunneling.I could not find the "redirect gateway" setting in the server settings.
It "Redirect IPv4 gateway" and "Reirect IPv6 gateway". It's not checked.
I added DNS servers in the VPN settings and opened it up I believe.
Stating public DNS server requires, that the client has access to them. But I guess, this might be given.
So I'd expect, that the client has no issues with internet access with these settings.
BTW: there is no need to state "comp-lzo" in the custom options. This can be set at "allow compression".
-
Do you see states and/or bytes on the pass rule on WAN?
Anything logged now?
Edit: Ooops missed some posts.