Clock Issue
-
Glad its working now!
-
@fireodo Thanks for your help :) this has been driving me nuts for weeks
-
I don't think you want to enable the WAN interface on the NTP server settings unless you are planning to advertise your personal NTP server on the public internet. See example
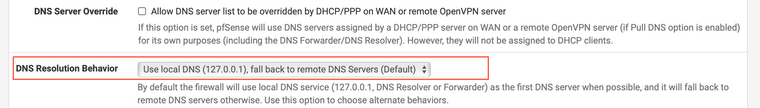
Check your System -> General setting.
-
@elvisimprsntr Well see thats what I thought, this is the general setting, I didnt have anything in the DNS servers until earlier, I added 127.0.0.1, im using the local resolver, possibly it needs something in there even if its just 127.0.0.1
-
You will want to add a valid external DNS server to the System -> General settings.
Otherwise it will not be able to resolve DNS names
-
Without the wan selected I get this:
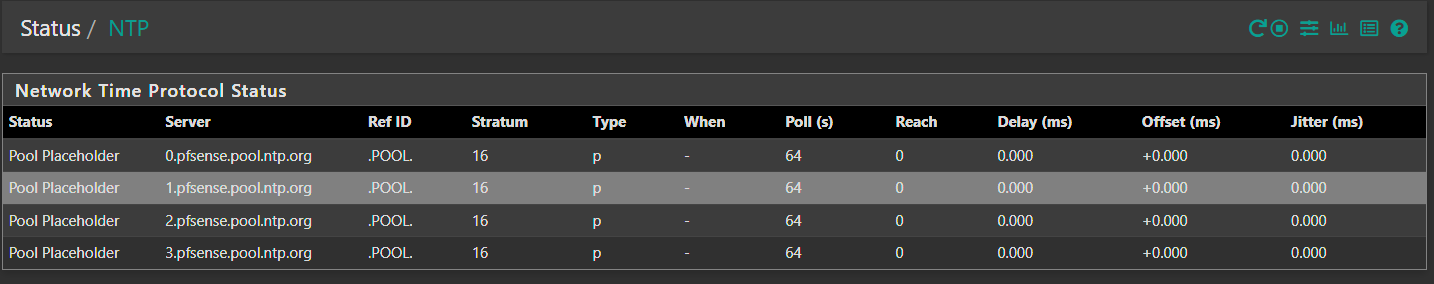
With the WAN selected I get this:
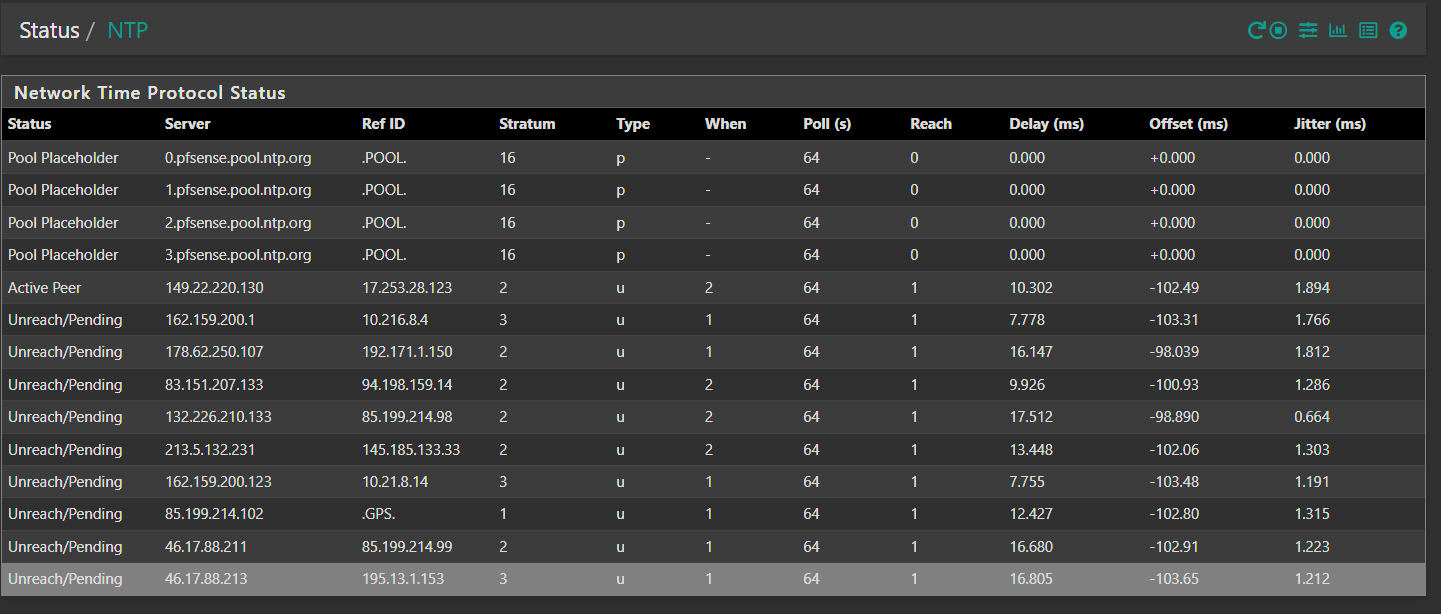
So that must need to be selected, as long as I don't have a firewall rule allowing NTP on the WAN interface it shouldn't be accessible from the outside world right?
-
@elvisimprsntr Im using the DNS Resolver Service, never had an issue with the firewall installing packages or updates so it can resolve ok with just that and this command was working fine ntpdate -q 0.pfsense.pool.ntp.org
-
@elvisimprsntr said in Clock Issue:
You will want to add a valid external DNS server to the System -> General settings.
Only if you want to forward to this DNS Servers. Pfsense can resolve out from the box ...
-
You have likely made too many changes from the defaults that are conflicting with each other.
If you are relatively new to pfSense, you should use the defaults unless you are a spefiic reason to change them. Then only change them one at a time.
-
@elvisimprsntr Not new been using it for 15-20 years

-
-
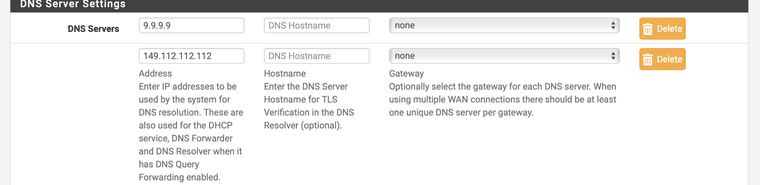
@elvisimprsntr Yeah I will set that and a google DNS server just incase there is ever an issue with the resolver.
-
You need to be able to forward DNS requests to a public DNS server, otherwise public domain names will not resolve, which is exactly what you were seeing with the NTP pools.
-
@elvisimprsntr Im using the Resolver service so those entries shouldn't be needed as that talks to the root DNS servers but its probably good to have that setting set as a backup
-
I have just checked the documentation and it looks like the wan does need to be selected, its just not very intuitive from the interface as its called NTP server and you would expect you are selecting the interfaces you want the server to listen and respond on, not call out on:
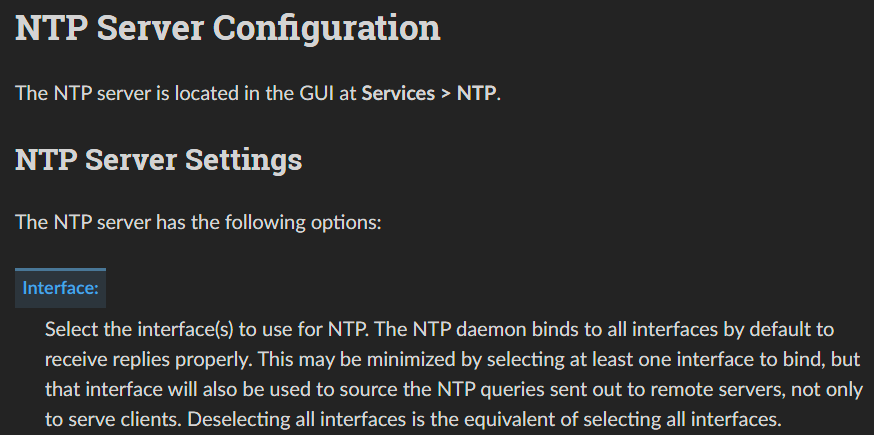
-
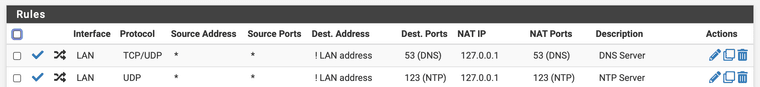
I use DNS Resolver as well. I enable transparent mode so all DHCP clients use my local DNS first, but you have to configure a public DNS server under System -> General
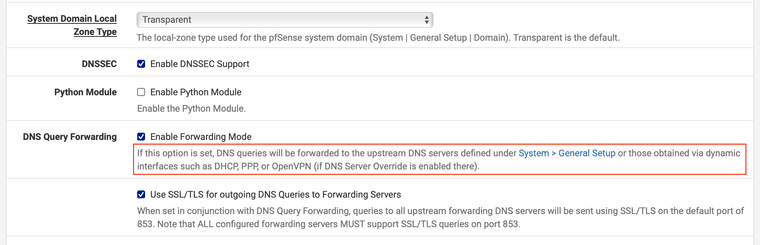
Then add a FW rule to redirect all public DNS and NTP queries to my local server,
-
@elvisimprsntr I dont use forwarding mode, ideally you want that off as for more privacy and security you want it going to the root servers not your ISP, google etc
-
I use Q9 encrypted (port 853) DNS. They seem to do a good job.
-
Yup ntp will bind to those interface addresses for outbound queries. That usually still works because most configurations have outbound NAT rules for those subnets and default routes via the WAN. But if you don't have one of those things it will fail.
-
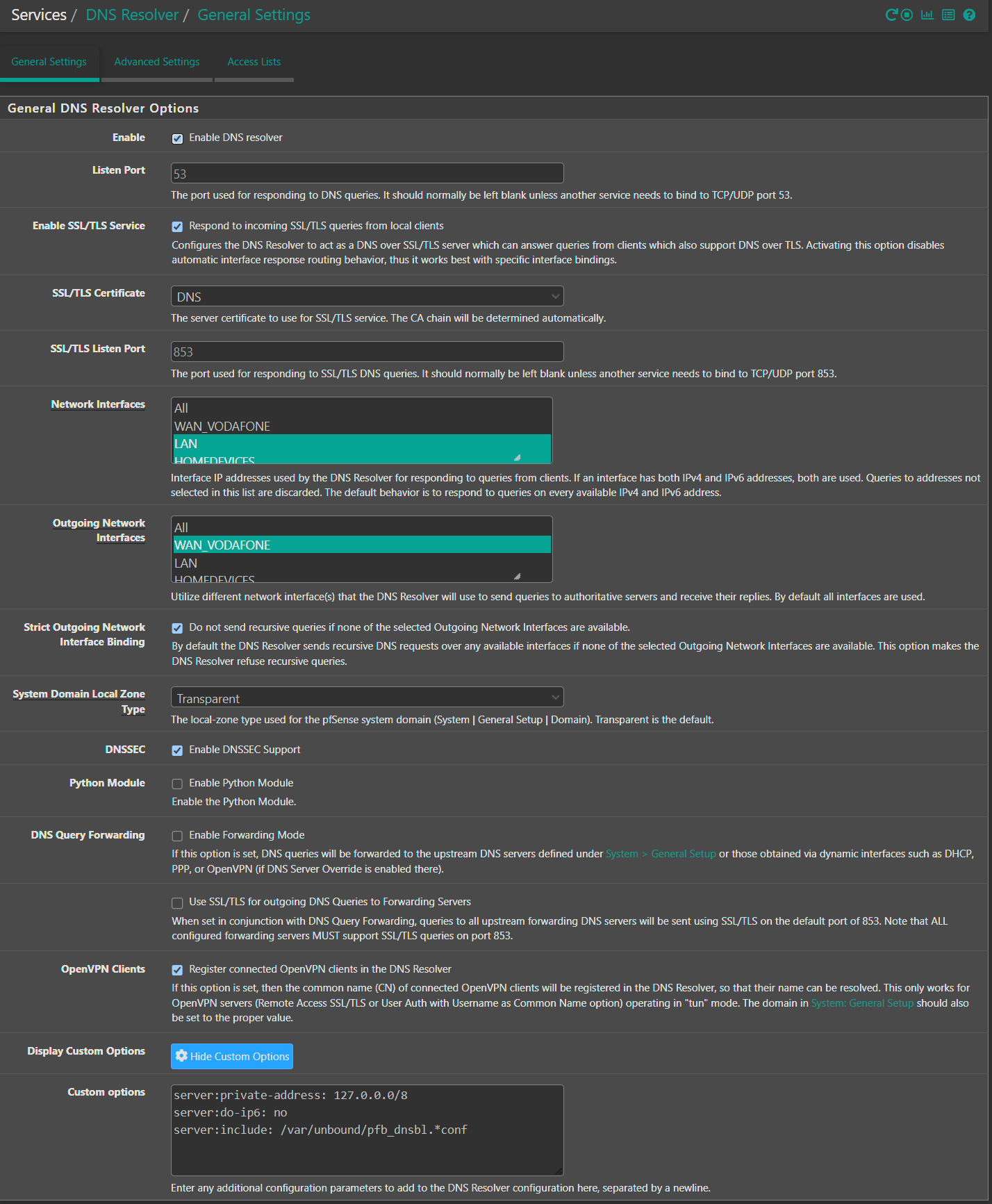
I believe you have come to the wrong conclusion about having to have WAN selected for the NTP server configuration interfaces. It’s true for how you have your PFS set up. Possibly because of interfaces you have selected in the DNS resolver network settings. This is just a guess on my part.
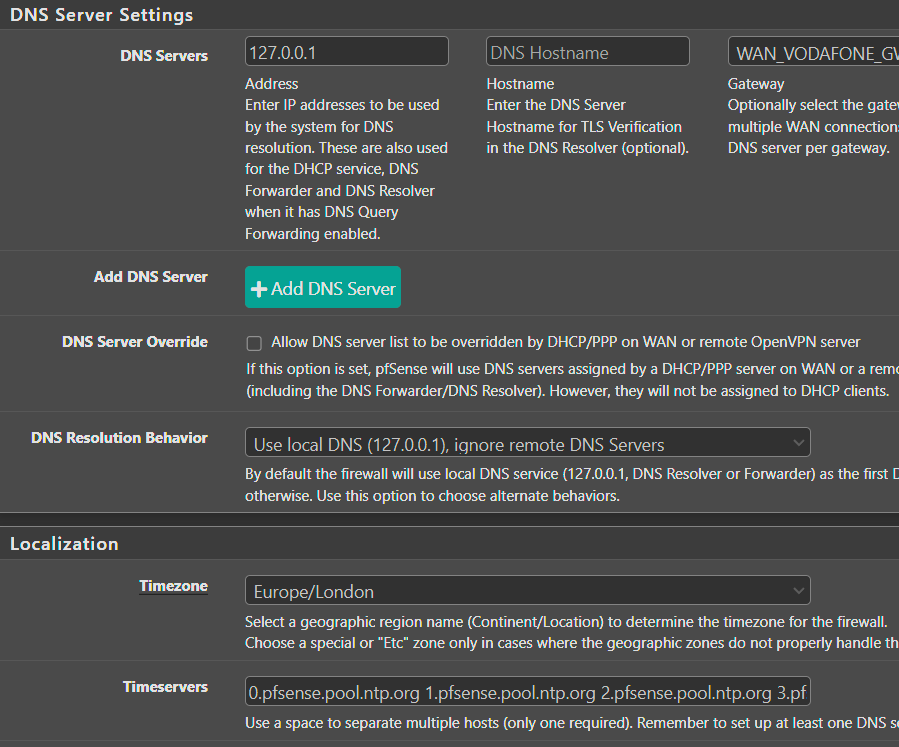
For comparison, I use resolver.
DNS server settings are empty, resolver behavior is set to use local DNS, ignore remote DNS servers.
Resolver is set up in a transparent zone with DNSSEC support enabled.
Resolver is set to listen to all network interfaces and is listening on all outgoing network interfaces. This is a stock out of the box setting.
The NTP server is enabled and set to listen on all interfaces except WAN.
The only difference is I have set up time server pools that are closest to me rather than use the PFSense pools.