OpenVPN External Connection
-
@stephenw10
Yes, was sending pings externally from an OpenVPN client to .241.There's 0/234 bytes
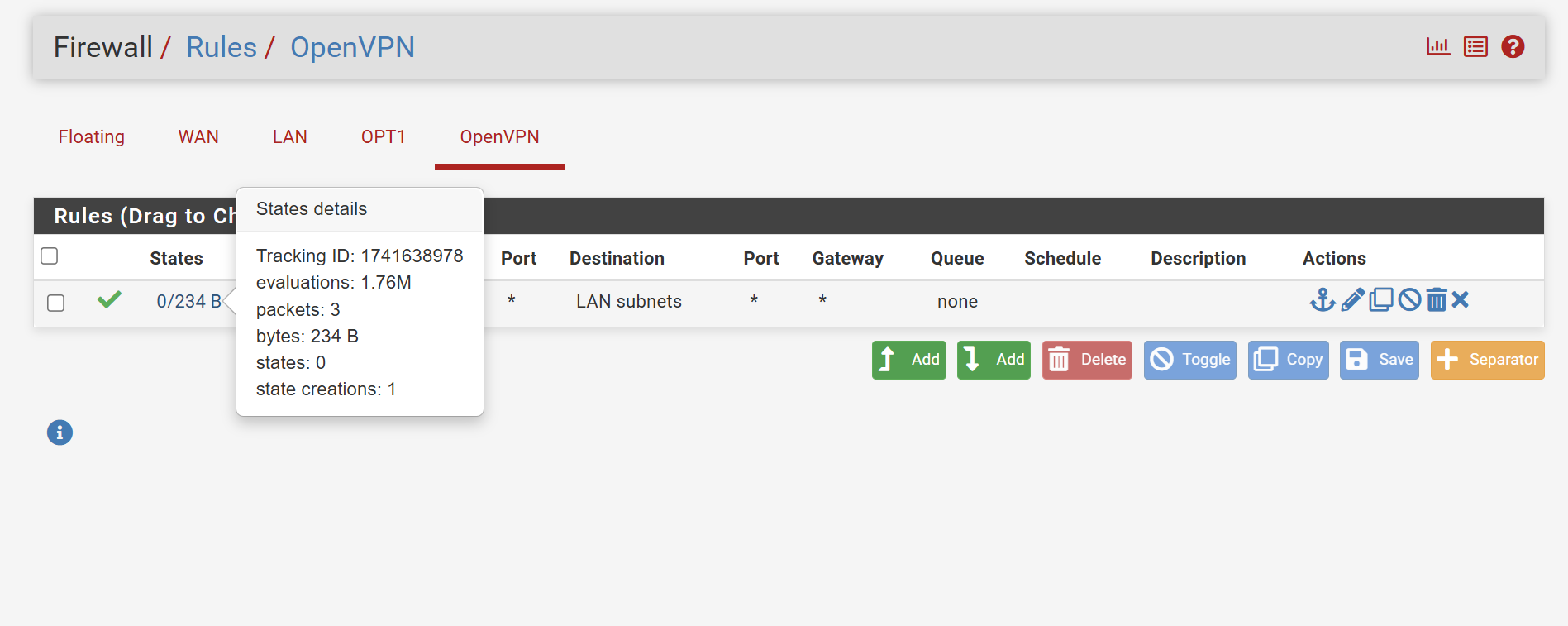
No floating rules.
-
@stephenw10 @viragomann
I just created a rule allowing port 53(DNS) which may not have had an effect, but I also created an ICMP rule in OpenVPN and I can now successfully ping the .241.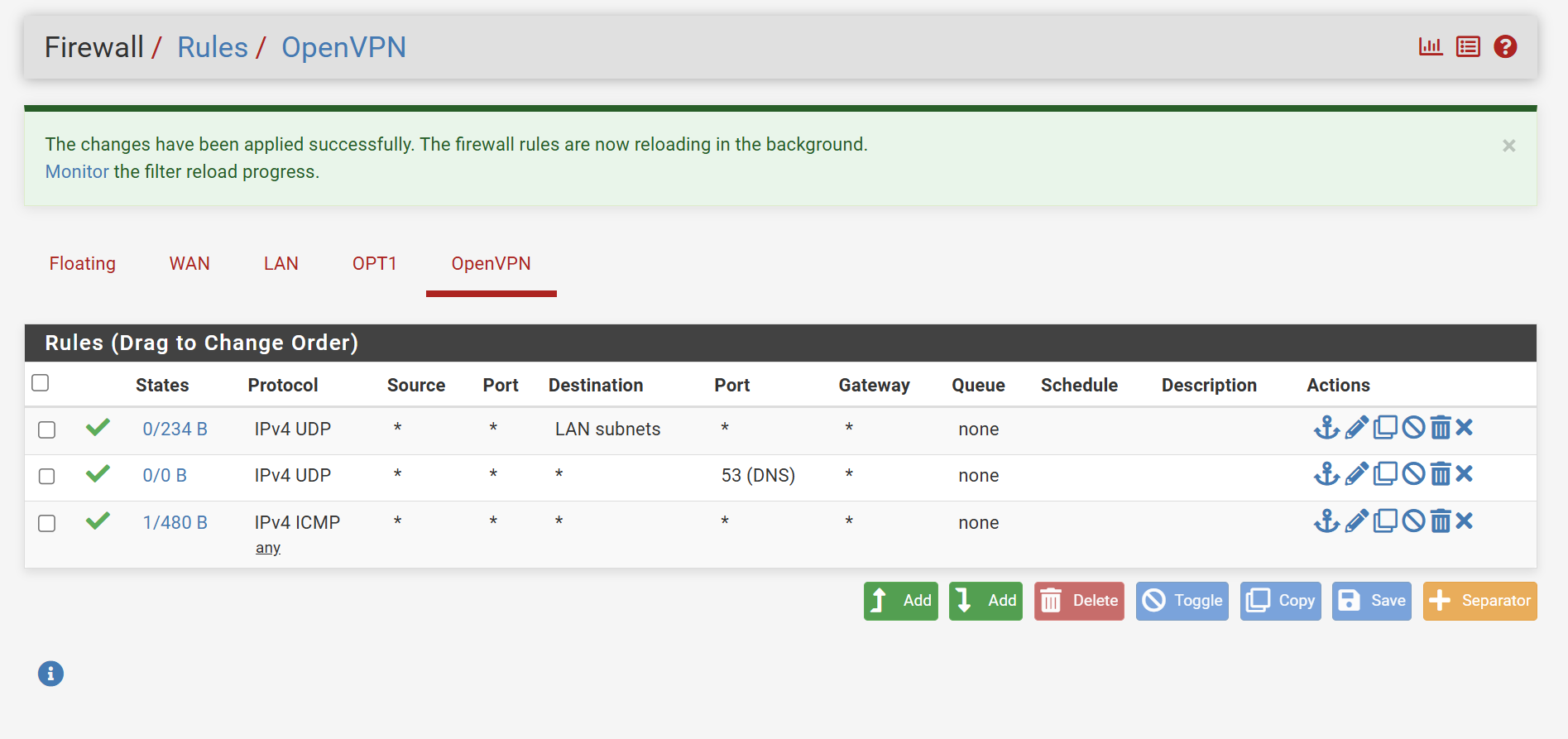
-
Your first Rule only allows UDP...
-Rico
-
@Rico
Awesome! That now allows me to access the LAN interface. Thanks! Any settings I need to change to allow me to RDP into my workstation? -
You have to pass TCP traffic for that. But I would just change that first rule to pass 'any' protocol to 'LAN subnets' and remove the other two rules.
-
@stephenw10 Done and it's working!
From the recent posts, is there anything I need to clear up to keep from getting hacked?
Thank you all again for your help, I appreciate you! I can't upvote yet or I'd be giving them!
-
I would consider putting OpenVPN on a different port. It's extremely unlikely you would be hacked that way but you will see connection attempts and possibly blocked traffic on the default port.
-
@stephenw10 Thank you again!
-
@LMorefield said in OpenVPN External Connection:
@stephenw10 Done and it's working!
From the recent posts, is there anything I need to clear up to keep from getting hacked?
Thank you all again for your help, I appreciate you! I can't upvote yet or I'd be giving them!
Depends on how aggressive you want to be on that. I secure client to site OpenVPN in a corporate environment. We are definitely targeted occasionally. The measures I'm using might be overkill for your purposes, but I can go through them broadly and you can decide.
We have actual two factor authentication (ours requires a valid username + password and a client certificate). We also do security by obscurity (we don't use the default port) and we also use the TLS static key.
-
@bp81 The more secure, the better! It would be great to enable two-factor authentication. It's actually a requirement. Unfortunately I'm tasked with figuring this all out via pfSense when it's not my wheelhouse, hence the lack of knowledge coupled with the many questions.
-
@LMorefield said in OpenVPN External Connection:
@bp81 The more secure, the better! It would be great to enable two-factor authentication. It's actually a requirement. Unfortunately I'm tasked with figuring this all out via pfSense when it's not my wheelhouse, hence the lack of knowledge coupled with the many questions.
I can give you some step by step to get this setup. It makes some assumptions, chiefly that 1) you will be using the pfSense user database for user authentication and 2) you will use a self signed certificate authority instead of a third party CA or internal certificate infrastructure (like ADCS). Obviously your steps related to user auth and certificate creation will differ if you have any of these elements.
Create certificates
- Go to System -> Certificates -> Authorities.
- Add a new authority.
- Choose a descriptive name. Doesn't affect function, but best to clearly label it.
- Method: create an internal certificate authority
- For the key, the default settings of RSA, 2048 bit key, sha256 digest algorthm are fine. Feel free to use something more stringent for extra paranoia.
- Choose a common name. I often use the hostname of the router for this, but that's certainly not required. Choose a reasonable common name.
- Fill in the locality information if you'd like.
- Save.
- Go to certificates tab.
- You will need to create two types of certificates. A server certificate and multiple user certificates. Start with the server certificate by clicking Add/Sign.
- Method: create an internal certificate.
- Descriptive Name: this certificate will be used by the OpenVPN server on the pfsense router to authenticate itself to clients connecting to it. I would choose a descriptive name that makes that clear (ie, OpenVPN Server Certificate or similar).
- Certificate authority: choose the CA you just created.
- The default key information (RSA, 2048 bit key, sha256 digest algorithm) is perfectly fine. However, as before, feel free to use more stringent settings for extra paranoia. Not all settings here are compatible with OpenVPN, but the ones that are will be marked as such.
- Set a common name. It's best to use the FQDN of the router here, makes setup smoother.
- Fill in the locality info if you want.
- Set certificate type to server certificate.
- Save.
- Add/Sign another certificate.
- Method: create an internal certificate.
- Descriptive name: this will be a user certificate. Make that clear in the descriptive name (ie, user1 C2S VPN Certificate).
- Certificate authority: the CA you created earlier.
- The key's default settings (RSA 2048 bit, sha256 digest) should be fine.
24, Common name: it is very important that the common name exactly match what the end user will key in for his/her username. We will call our example user user1. This will often be an email address if you are using AD auth instead of pfsense local user database. Key in user1 for the common name. - Fill in the locality information if you want.
- Save
- Repeat 19 through 26 for every user that needs VPN access.
Create user accounts
- Go to System -> User Manager -> Users tab
- Set the username to user1, set a password, and save.
- Repeat steps 1 and 2 for each user needing VPN access.
Create VPN Server
You may already have a working vpn server. You can make adjustments to the existing server to match.
- Go to VPN -> OpenVPN -> Servers tab.
- Add new server.
- Enter a description that suits you.
- Server Mode: Remote Access (SSL/TLS + User Auth).
4a. If you have pfSense+, you may see an option to enable DCO. This is recommended if you have it. It greatly improves OpenVPN's performance for bulk downloads/uploads. - Backend for authentication: local database
- Device mode: tun / Layer 3
- Protocol: UDP on IPv4 only
- Interface: WAN
- Local port: I would recommend choosing a port other than the default 1194. Any port not used by something else will work.
- TLS Configuration: Check the box to use a TLS key,
- Check the box to automatically generate the TLS key.
- Peer Certificate Authority: choose the CA you created earlier.
- Server certificate: choose the SERVER certificate you created earlier. NOT the user certificate.
- DH Parameter length: the default 2048 is fine. If you want extra paranoiam ECDH only, then set the ECDH curve to secp521r1. Not really necessary, but it's available if you want to do it. Otherwise 2048 for DH Parameter Length and default for curve is fine.
- Next you choose data encryption algorithms your server will support. The default is AES-256-GCM, AES-128-GCM, and ChaCha20-Poly1305. I tend to pull AES-128-GCM from this list but leave the other two. Up to you.
- Fallback Algorithm: data encryption algorithm to use if a connecting client doesn't support any of the algorithms from step 15. AES-256-CBC is the default and a good choice here.
- Auto digest: SH256.
- Hardware Crypto: this depends on your hardware. If you have ANY options here, make sure you choose one.
- Certificate depth: default is one, and will work with the setup I've listed here. If you're using a certificate infrastructure or a third party CA that has intermediate certificates, you may need to increase this value.
- IPv4 Tunnel Network: this defines a network / subnet on the router that the OpenVPN clients will have IP addresses in. This should NOT overlap with any existing lan or vlan subnets already on the router. This should be keyed in using CIDR format (ie, 10.100.100.0/24)
- IPv4 Local Networks: these are networks you want to be reachable through the VPN tunnel. Typically this will be your LAN subnet.
- The remaining settings can be left at default typically.
Export OpenVPN user profiles and install on user workstations
- Go to VPN -> OpenVPN -> Client Export tab. If you don't see Client Export tab, then go to the package manager and install the package openvpn-client-export.
- In Remote Access Server, select the server you just created.
- Host name resolution: Other
- Host name: FQDN of the router.
- Verify server cn: Automatic is recommended
- The rest of the default options are probably fine. One thing here that I wish worked ncier was the option to use Microsoft Certificate Storage for Windows machines. I've had issues getting this to work and so am not using it. I would prefer to though.
- Click Save As Default so it will keep these settings for later.
- For each user, click the button "Most Clients" to generate an OpenVPN config file. This config should work with OpenVPN community edition or the paid version.
- With OpenVPN community edition, copy the profile to the user's Windows PC to c:\users<user's folder>\OpenVPN\Config
Create firewall rules
- Go to Firewall -> Rules -> WAN interface
- Add a new rule.
- Action: Pass
- Interface: WAN
- Address Family: IPv4
- Protocol: UDP
- Source: Any
- Desintation: WAN address
- Destination port range: In the leftmost "Custom" box, enter the port you chose earlier when setting up the OpenVPN server
- Enter a description of your choice.
- Save and apply changes.
- Go to OpenVPN tab.
- Add a rule that allows all traffic on the OpenVPN interface, that is from the OpenVPN tunnel network subnet for now. Once you establish traffic is working across the tunnel, feel free to come back and lock this down a little.
- Done. Your user should now be able to connect with OpenVPN from his/her workstation.
If this doesn't work, post back with error messaging so it can be diagnosed.