OpenSSL not loading full SafeXcel capabilities.
-
@stephenw10 23.05.01
-
@stephenw10 does 25.03 reflect increments on use of the chip in your system?
-
You mean in the interrupts shown by vmstat? They do, but not for aes-gcm. Which is what I'm digging into.
-
@stephenw10 thank you. Yes on the vmstat.I was thinking about adapting the OpenSSL.conf file to add the SafeXcel but I don’t know how, I am sure it is just adding the chip. I seem to remember I could change openvpn to bsd/safexcel on the hardware offload a couple months ago.
Side Note: There is also a way to use offloading with the directive ssl_engine on my favorite Squid package I have learned, that is amazing.
Per Squid support..
- If your Squid is built for libssl 3.0 or later, you may be able to configure /etc/ssl/openssl.cnf default provider to be the one you want. Such that Squid does not have to do anything for it to work.
I expect all the details relating to how devcrypto does its thing to be configured in /etc/ssl/openssl.cnf.
You may find this discussion from the OpenSSL community helpful:
https://github.com/openssl/openssl/issues/10701(FTR; the
HTH
Amos
____________________*ssl_engine devcryptoAgain same thing it accepts the directive but the vmstat counters do not increase.
Another note:
I also use .eli in fstab
# Device Mountpoint FStype Options Dump Pass# /dev/msdosfs/EFISYS /boot/efi msdosfs rw,noatime,noauto 0 0 /dev/msdosfs/DTBFAT0 /boot/msdos msdosfs rw,noatime,noauto 0 0 /dev/gpt/swapUSB.eli none swap sw 0 0This .eli use with FreeBSD encrypts the swap and it does work when looking at logs.
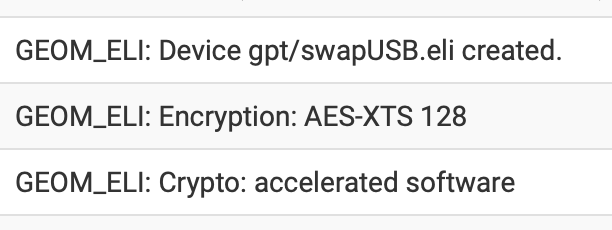
Weird right this does increase vmstat when it is used. Again that would not block out everything because I also disabled it to test and it still did not normalize the system.
Mar 5 20:23:52 kernel safexcel0: <SafeXcel EIP-97 crypto accelerator> mem 0x90000-0xaffff irq 18,19,20,21,22,23 on simplebus1 Mar 5 20:23:52 kernel warning: increase kern.maxswzone or reduce amount of swap. Mar 5 20:23:52 kernel warning: total configured swap (3831807 pages) exceeds maximum recommended amount (3383256 pages). Mar 5 20:23:52 kernel GEOM_ELI: Crypto: accelerated software Mar 5 20:23:52 kernel GEOM_ELI: Encryption: AES-XTS 128 Mar 5 20:23:52 kernel GEOM_ELI: Device gpt/swapUSB.eli created. Mar 5 20:23:52 kernel nda0: 244198MB (500118192 512 byte sectors) Mar 5 20:23:52 kernel nda0: nvme version 1.3 x1 (max x2) lanes PCIe Gen2 (max Gen3) link Mar 5 20:23:52 kernel nda0: Serial Number BTTE9510086T256D-1 Mar 5 20:23:52 kernel nda0: <INTEL HBRPEKNX0101AH HPS1 BTTE9510086T256D-1> Mar 5 20:23:52 kernel nda0 at nvme0 bus 0 scbus1 target 0 lun 1 Mar 5 20:23:52 kernel ada0: 122104MB (250069680 512 byte sectors) Mar 5 20:23:52 kernel ada0: Command Queueing enabled Mar 5 20:23:52 kernel ada0: 600.000MB/s transfers (SATA 3.x, UDMA6, PIO 512bytes) Mar 5 20:23:52 kernel ada0: Serial Number 0014307000651 Mar 5 20:23:52 kernel ada0: <NT-128 2242 SN14941> ACS-4 ATA SATA 3.x device -
@stephenw10 any update on this? Maybe a change in openssl.conf ? I don’t know I am wondering where to add that cipher, as it is supported.
-
It's unlikely to work with the userspace devcrypto device. And even if it did you should not use it because it's so slow as to be worthless. Especially since armv8crypto was added.
But it should work for in-kernel crypto functions and appears not to be. Still digging...
-
@stephenw10 thanks for checking.
-
@stephenw10 Does use of .eli in the fstab file cause this? It should be able to do both right?
-
I would expect that to be kernel level crypto, yes. But I've never checked specifically.
-
@stephenw10 how you doing today?
Any updates on that kernel crypto functions?
-
Not yet. I was away this weekend.
-
@stephenw10 I think it has to do with fstab use or .eli for swap, but even if I turned off .eli it still does not work.
-
@stephenw10 Any word, if you need a copy of my config that is no problem.
-
@stephenw10 I just wanted to follow up on this. I was able to get SafeXcel to increment with use of setting Squid proxy to use the sslengine as devcrypto. Don’t know if that helps
-
Hmm, interesting so you see interrupts there but not when calling it via openssl-speed?
-
@stephenw10 yes, I can see interrupts when using squid’s ssl engine directive when doing ssl intercept, but when the OpenVPN use it will not increment. I keep thinking it is because I use .Eli in the fstab file for the swap encryption, but if that was the case why does it increment when I use .Eli and squid’s ssl engine directive? Weird right ? And it does improve performance with the certificate stuff.
Squid custom option.
ssl_engine devcrypto -
@JonathanLee said in OpenSSL not loading full SafeXcel capabilities.:
I can see interrupts when using squid’s ssl engine directive when doing ssl intercept, but when the OpenVPN use it will not increment.
Seems normal and understandable to me.
The OpenVPN app connects only to the OpenVPN server, and the connection is created if authentication worked out fine.
I don't see the MITM (pfSense) doing that : emulating and OpenVPN server authentication so it can intercept.And its a waste of time trying to decrypt a OpenVPN stream, OpenVPN can't be 'MITMed', not with the hardware that exist in 2025.
Maybe the quantum pfSense version in the future ?
-
No it's when using pfSense as an OpenVPN server or client with an encryption algorithm that safeXcel supports. Or at least should support.
-
Ah, overlooked that.
I thought, while reading : an OpenVPN connection flowing through pfSense that does Squid stuff ... -
@Gertjan I am attempting to offload the encryption to the SafeXcel chip, I have had it running in the past with OpenVPN again I am also testing use of it with squid and my swap partition, but of those cause the interrupts to be incremented, but all the sudden OpenVPN will not use the SafeXcel chip anymore and it did with this version a couple months ago. Something is different as it should utilize it like it did in the past. I originally thought it could only be used by one component, that could be fstab file and use of .eli to encrypt the swap and or using it with squid for acceleration of ssl certificates, but they both work, all the sudden OpenVPN won’t increment the counters anymore. It’s weird because from what I am told OpenVPN should do this automatically, the new versions of software remove use of hardware crypto and OpenVPN but I can’t even run tests it acts like the chip does not load. That’s where it has confusion it should still see the counters increment in the system but it does not. It does drastically improve performance with the “ssl engine” directive in squid. Again not many people use .eli at the end of the swap config in fstab. So it’s kind of a trial and error thing. Goal faster vpn access to my private NAS.