DDNS does not work
-
Hi,
I have a Natgate 4100 that has a problem that I can't solve.
I got an email a week ago that my DYNDNS had not been updated. I look in PfSense and see there is a green check mark, and then test via edit with save/update.It turns out it is not updating as it should. I set it to log traffic and get the following error.
rc.dyndns.update: Curl error occurred: SSL certificate problem: certificate has expiredWhen I send the Update URL via a browser, it works fine, the Dyndns server is updated.
It has worked perfectly for years, until about a month ago.
What can I do to get it working againIn have version 24.11-RELEASE (amd64)
built on Sat Jan 11 17:11:00 CET 2025
FreeBSD 15.0-CURRENT -
@Felix-4 said in DDNS does not work:
When I send the Update URL via a browser, it works fine, the Dyndns server is updated.
And the browser doesn't complain about the certs validity?
So display the cert and verify it.
-
That's correct, the browser doesn't complain about anything and sends a return response back.
good with my IPWhat do you mean by showing the certificate?
-
@Felix-4
Some browser have an option to display the cert by clicking at the lock symbol.
You can also verify it with OpenSSL or some web services.
-
ok I'll look into it, thanks for the quick response, I really appreciate it ;o)
-
I have investigated it, and it turns out there was an exception in the browser so the certificate was ignored.
My solution, befor the certificate on the DydDns server being renewed, is to change https in the URL string to http. This will update correctly.
When the certificate is updated I will change it back to https.
Password is hash 256 so it should be ok to send. -
Who is your DynDNS supplier ?
@Felix-4 said in DDNS does not work:
PfSense and see there is a green check mark
This means that the following check was valid :
First, pfSense uses :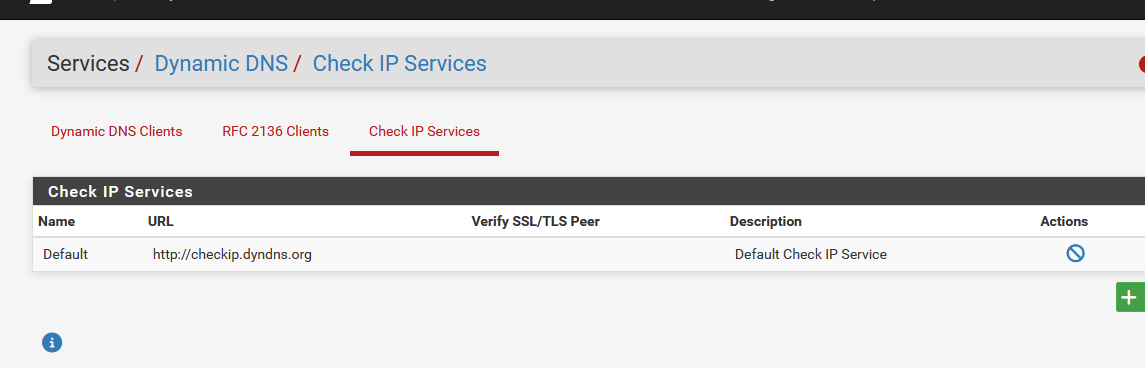
You can also use this URL : http://checkip.dyndns.org. Just click on it.
You'll be seeing your WAN IPv4.
Then, pfSense will compare this IPv4 with the one it had when the latest successful DyNDNS update happened. pfSense knows what IPv4 this was, as it kept a copy in a local cache file.
This file can be found in this folder /cf/conf/ and the file starts with 'dyndns_' and ends withc the extension 'cache'. Again, you can see it. Open the file, and check what IPv4 it contains.
If the one in the file and the one obtained by the URL are the same, the check passed = green.
This means there is no need to update your IPv4.
If the two are different, an dyndns update will happen.
If that update was successful, then the cache file will be written with this new IPv4.Look at the file/date time stamp of the cache file : that's the moment the last successful update was happening.
Your DynDNS service : if they have cert issues like this, then you should see that as a very strong indication that you need to look for dyndns services elsewhere.
-
It's dyndns.dk
Apparently it's no longer maintained, but has been easy and stable for many years.Thank you very much for your explanation, that makes sense. ;o)
However, in this case it is necessary to update at least once a month to preserve your DNS name. Therefore, in the setup I have set it to "force update" every 20 days, and due to the certificate problem it fails.
I've looked at dynu.com it looks reasonable, but I don't know it well yet -
@Felix-4 said in DDNS does not work:
However, in this case it is necessary to update at least once a month to preserve your DNS name. Therefore, in the setup I have set it to "force update" every 20 days, and due to the certificate problem it fails.
The pfSense 'dyndns' software will do a forced update after some (20 ?) days.
You saw the cache file, it contains the latest successfully updated IPv4 and something else : a time stamp value.
So pfSense knows when the last successful update happened, as it knows when to update based on the elapsed time.If you can edit the update URL that contains the https://dyndns.dk/....., change it for http://dyndns.dk/ and your issue is gone.
True, now the traffic goes over http so its not encrypted anymore, but, imho, that's not a big deal.