Removal of LAGG
-
@johnpoz said in Removal of LAGG:
@stevencavanagh said in Removal of LAGG:
just following guides how to set up VPNs.
All of them are pure crap - the ones I have read at least, but yeah they have you go to manual rules for ZERO reason..
Did I say broken? I meant make no sense, if your in hybrid mode why would you have rules in mapping in your hybrid section for your normal wan interface? Maybe it was how you snipped up and posted the images?
Also hybrid are evaluated top down as well.. So then you have multiple in row with the same source network I see multiple with 192.168.20 and then 192.168.50..
How are you doing your policy routing.. Your going to have issues trying to switch between them - unless you kill all the existing states..
I snipped them up from top to bottom.
If I remember I had set them up so multiple VPN gateways were in a group (all Tier 1) and I could then use policy routing to send all traffic from certain IPs (all static) out via VPN and the rest via the default gateway. The outbound NAT for 192.168.20, 192.168.50 etc are all VLANs, hence why there are so many.
Also, floating rule exists (kill switch).
What I cannot remember is how Pfsense determines which of the Tier 1 VPNs to select as my IP address switches regularly from country to country, which is fine.
Fairly certain I'm not killing all the states, what problems will I have?
-
If they're actually set as the same tier it will just move to the next gateway in the group in the event of a failover.
-
Must be failing fairly regularly then!
-
Depends how you are using it. If they are in a group you're policy routing to (which I think they are) then pf will will load-balance between them so you will see connections change continually.
-
They are inna group and they do appear o load share but only seems to be 3 of them at any one time for some reason.
-
Are they all connected? Are they all at the same tier?
-
@stephenw10 Yes, they are all connected and all at tier 1
-
Hmm, well I would expect to see traffic on all of them then. One thing that often causes issues in this sort of setup though is when the VPN provider uses the same gateway IP for multiple servers. In that situation pf can only route to one of them.
-
Yes, that's a problem with Nordvpn, which is why I also use PIA also. Consequently, I have only one instance of Nordvpn and the rest are PIA, which have different gateways
-
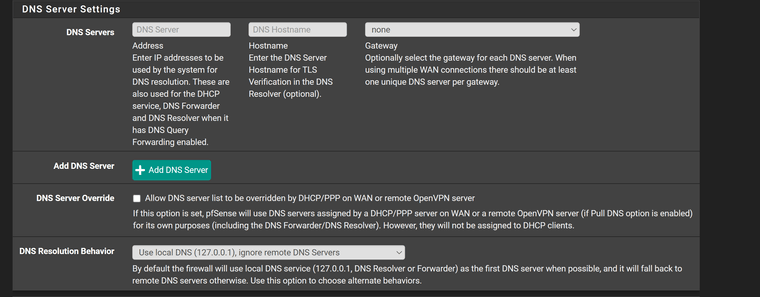
One issue I have found but may not be related to VPNs is that on running a DNS leak test, I find my ISPs external WAN ip address alongside the VPNs public ip address. The dashboard shows the only DNS server as 127.0.0.1, which I believe is correct as I am using DND resolver. Had a look around the forum at the many posts but yet to find a cause or solution!
-
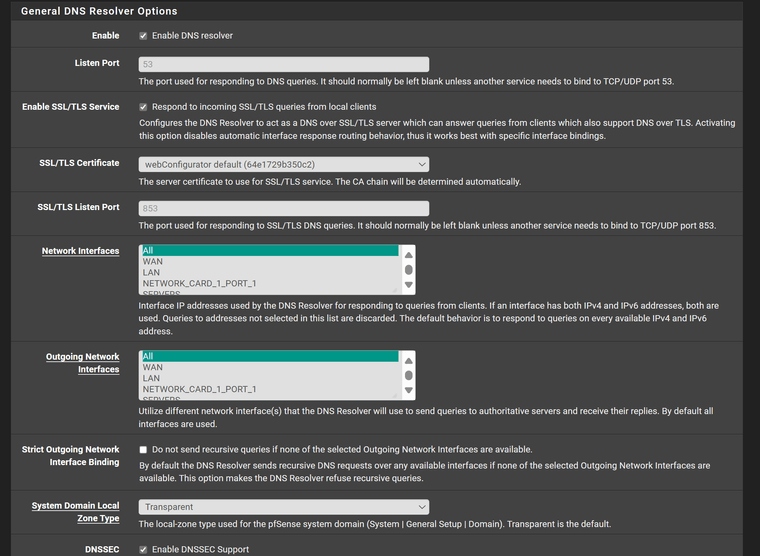
How is Unbound configured? How is DNS set in System General Setup?
-
-
OK so you have Unbound set to use any (all) interfaces for outgoing queries and that includes WAN. Since it's resolving directly anything looking for that will see the WAN IP as the source.
-
So, I assume I need to remove WAN from that then.
-
No matter what I do to the outgoing network interface i.e. leave it at WAN only, I still get the ISP ip address showing in the leak test. I thought it would just show 127.0.0.1
-
The leak test shows the IPs of the DNS resolver in use. Since you are using Unbound directly it will show your public WAN IP address for any queries sent out of the WAN.
If you set Unbound to use only the VPN connections for outbound queries the leak test will only show the VPN provider. That might cause problems for any service that uses DNS checks, like Netflix for example.