Difficulty setting up a split wireguard tunnel with one of the destination networks on the other side of the remote WAN interface
-
I posted this question over on Lawrence System Forums however wasn't getting much traction. I'm basically setting up a site to site VPN using Wireguard using two pfsense boxes as the wireguard peers. I've setup the pfsense wireguard peers and with each peer I can reach networks (untagged and tagged VLANs) located on the remote peer "LAN" side of the router. What I'm having difficulty with is creating a split tunnel VPN, where one of the remote networks is actually located on the "WAN" side of the remote peer. I can't get pfsense wireguard to forward packets outside the "WAN" interface to the remote network.
Here is a drawing of my network:
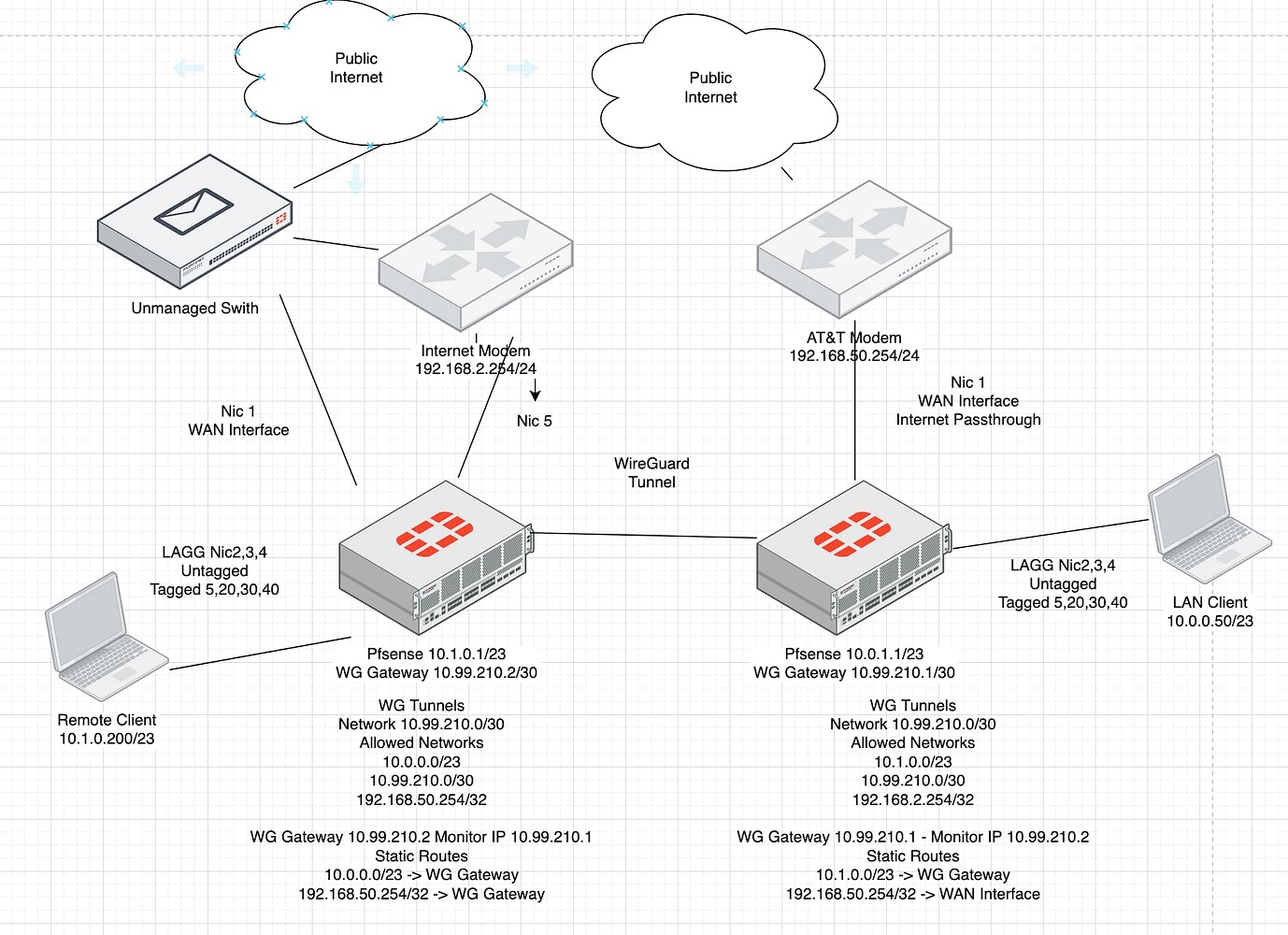
Using the drawing for reference, Ive tried to have either the remote client @ 10.1.0.200/23 or the actual pfsense router @ 10.1.0.1/23 ping the AT&T modem @ 192.168.50.254/24. The AT&T modem is configured for network passthrough and is connected to the pfsense WAN port @ 10.0.1.1/23. LAN client @ 10.0.0.50/23 and the pfsense box @ 10.0.1.1/23 can both ping the 192.168.50.254 ATT modeml
To show I've have a working Wireguard Tunnel, I using mtr which does a ping and traceroute simultaneously. A remote client @ 10.1.0.200 can reach the LAN client at 10.0.1.161/23.
(10.1.0.200) -> 10.0.1.161 (10.0.2025-03-09T14:09:19-0500 Keys: Help Display mode Restart statistics Order of fields quit Packets Pings Host Loss% Snt Last Avg Best Wrst StDev 1. 10.1.0.1 0.0% 85 0.2 0.2 0.1 0.3 0.0 2. 10.99.210.1 1.2% 85 37.3 35.6 32.5 39.2 1.4 3. 10.0.1.161 1.2% 85 35.4 36.1 33.6 39.1 1.3However when I have this same remote client try to reach the ATT router @ 192.168.50.254/24 -- here is output:
(10.1.0.200) -> 192.168.50.254 (12025-03-09T14:10:01-0500 Keys: Help Display mode Restart statistics Order of fields quit Packets Pings Host Loss% Snt Last Avg Best Wrst StDev 1. 10.1.0.1 0.0% 5 0.1 0.3 0.1 0.7 0.3 2. 10.99.210.1 0.0% 5 36.2 35.9 34.0 38.1 1.5 3. (waiting for reply)I did set up a static route at the 10.0.1.1/23 router of: 192.168.50.254/32 out the WAN_DHCP interface on the 10.0.1.1/23 router, however this didn't seem to accomplish much.
I'm aware a WAN interface on pfsense is treated much differently than a LAN interface as a NAT is employed here, but I'm not sure how to configure the NAT. In a way after thinking about it, I'm almost describing a multiwan situation, where I want 192.168.50.0/24 addresses to leave the network out the WAN interface located on 10.0.1.1@23 and the default WAN should be NIC 1. I'm just sure how to set things up. Not sure if policy based routing is necessary here.
Any suggestions?
-
@kevdog I have pretty much the same setup except my "modem" is an LTE router on WAN2 for my site B.
And it looks to me like you have done everything right, including trying to add the static route on 10.0.1.1 (Site B).
And since you are able to access (or ping at least) the modem from site B, unless you have made some other changes you should also be able to do that from site A.I'm assuming you have set a static route on site A for 192.168.50.254 throught the WG interface, since 10.1.0.200 -> 192.168.50.254 goes via the WG interface.
So I would start by testing to disable "Block private networks and loopback addresses" settings for the WAN interface on site B.
Also, check the logs on site B for any signs of the traffic being blocked in either direction. Compare your two tests to find any differences. -
Hey thanks for replying.
I'm really struggling to make this workCurrently I have a split tunnel network I'm trying to setup here (essentially what I'm describing).
Out of desperation I tried tunneling all traffic from site A to Site B over the WG interface. I created a static route on pfsense (10.1.0.1) of 0.0.0.0/0 to be routed over WG interface and included 0.0.0.0/0 as allowed networks.
On pfsense at site B, I turned off blocking bogon or private LAN addresses.
The resultant however was the same. Site A Clients could all reach clients on Site B (tested with ping and ssh), however no Site A client could connected to the internet beyond the router. (which includes AT&T modem as this device sits on the external side of the WAN nic).
How do I get the WG interface at SiteB to route the connection out the WAN interface? Nothing is showing up being blocked in firewall logs
-
Well it took some dumb look running across this Netgate post to help me solve my problem.
What I had neglected with my setup, was to add an outbound NAT rule.
So to solve this I did the following:
- On both pfsense installations I created an alias "WG_Tunnel_Net" as defined by network 10.99.210/30. I also created an Alias ATT_Router_Net as 192.168.50.0/24
- On both pfsense installations I set the Firewall-NAT-Outbound to Hybrid
- On Pfsense defined by 10.0.1.1/23 10.99.210.1/30, I defined about output NAT rule - Interface WAN, Source WG_Tunnel_Net, Source Port *, Destination ATT_Router_Net, Destination Port *, NAT Address WAN Address.
- The rule above basically looks like:
WAN WG_Tunnel_Net * ATT_Router_Net * WAN Address * - On pfsense defined by 10.1.0.1/23 10.99.210.2/30, I defined the following NAT rule:
NIC 5 Interface WG_Tunnel_NET * NIC 5 Subnets * Nic 5 Address *
After activating the Outbound NAT rules. I could successully ping 192.168.50.254 from 10.1.0.200
My traceroute [v0.95] (10.1.0.200) -> 192.168.50.254 (192.168.50.254) 2025-03-18T22:20:37-0500 Keys: Help Display mode Restart statistics Order of fields quit Packets Pings Host Loss% Snt Last Avg Best Wrst StDev 1. 10.1.0.1 0.0% 67 0.2 0.2 0.1 0.8 0.1 2. 10.99.210.1 0.0% 66 37.2 35.5 33.7 38.1 1.2 3. 192.168.50.254 0.0% 66 35.4 36.4 34.1 40.1 1.4 -
@kevdog Great that you got it to work!
It is a bit strange though that you would have to add the outbound rule yourself. I have my Outbound NAT set to Auto and I have e.g. my LTE router's subnet in the outbound rule (masquerade).
Perhaps you should test this and remove the static route to 192.168.50.254 and add it back again to see if it isn't added?
-
These rules weren't added on both my pfSense box installations, I'm aware what masquerade is and does from working with iptables, however I don't see any masquerade option within pfSense, and definitely no rules were added automatically to help me allievate this situation. I'm not even sure what the automatic rule should look like but I do have a bunch of them on each installation.