How to modify large firewall rule sets
-
@tinfoilmatt 'ruleset page'?
-
@michmoor
Firewall / Rules / [INTERFACE NAME] -
@tinfoilmatt you misunderstand my issue. I care about trackingID not rule descriptions.
-
@michmoor You misunderstand my "alternatve suggestion."
-
@tinfoilmatt but its not really doable. Modifying over 300 rules to include trackingID in a description
For new rules going forward - sure.
Better solution in my mind would be a trackingID column. -
@michmoor Yes. Clearly that's what you're demanding.
-
@tinfoilmatt
well......yeah.....hence the post to figure out if its searchable via another way........... -
@michmoor said in How to modify large firewall rule sets:
@tinfoilmatt
well......yeah.....hence the post to figure out if its searchable via another way...........To put it disingenuously? Sure. And that's what I offered, at which point you suggested I misunderstood.
-
@tinfoilmatt ok......
-
If you have the ID you can just search the ruleset for it:
[25.03-BETA][root@fw1.stevew.lan]/root: pfctl -vsr | grep 1736810441 pass in log quick on mvneta0 inet proto tcp from <LAN__NETWORK> to 208.123.73.69 flags S/SA keep state (if-bound) label "USER_RULE: Connections to ews" label "id:1736810441" ridentifier 1736810441Or if you have the ID you likely have the rule number like:
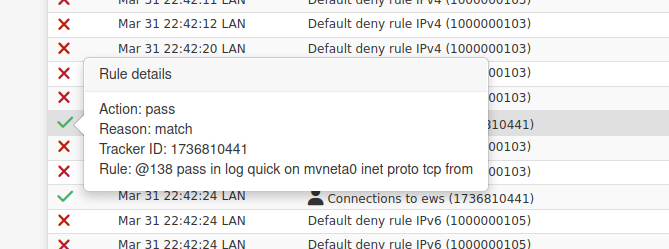
In which case you can use the rules view in Diag > pftop