Is it normal to log this traffic?
-
@marchand-guy rules have a setting to log or not.
Why would you need this rule? Packets between devices on the same subnet don’t go through the router.
-
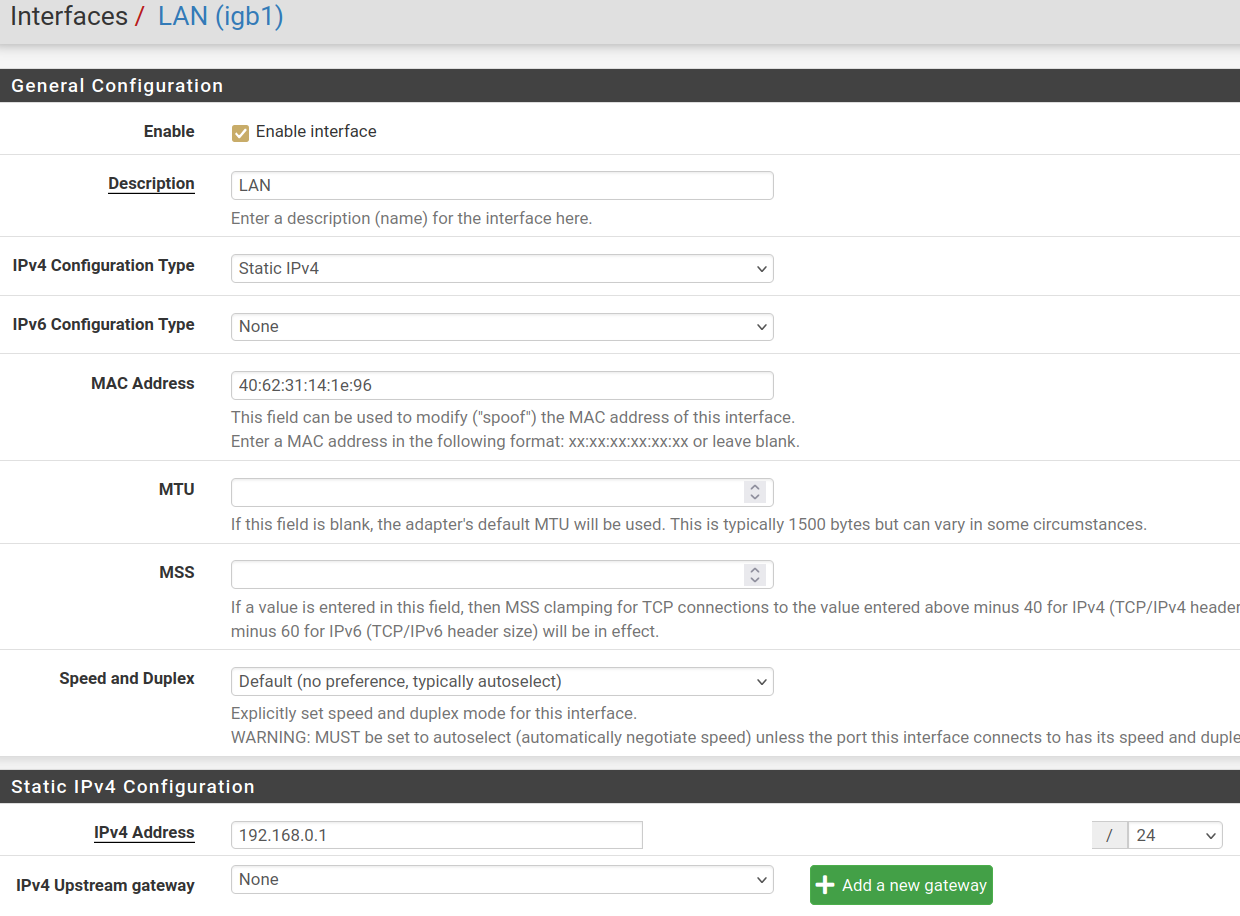
@patient0 Trying to show what you asked, it got me looking harder at my LAN interface definition.
I found this under "Static IPv4 Configuration"
IPv4 address 192.168.0.1 /24
Maybe changing that to 192.168.0.0 /24 wil correct the situation? -
@marchand-guy said in Is it normal to log this traffic?:
Maybe changing that to 192.168.0.0 /24 wil correct the situation?
No, the configuration of your LAN interface is correct.
But @SteveITS question stands and you show us a screenshot of the firewall rules for LAN and an example of the log we may be able to help.
Traffic from your LAN to 192.168.0.1 is normal for a lot of things, like DNS queries, NTP, DHCP. But traffic from one computer on LAN to another computer on LAN is not supposed to go through the firewall.
And in pfSense if there is no rule on an interface, all traffic is blocked. That's why after a fresh installation you have two 'Allow all' rules (1x IPv4 and 1x IPv6) in the firewall rules for the default LAN interface.
-
@patient0 I know about loging on/off. It's the fact that I seem to need this rule that bugs me.
Here we are:


-
Obviously traffic to the pfSense IP itself needs to pass the firewall. Usually you would not need a rule for that because by default there is a pass all rule for LAN traffic. If you have removed/disabled that though you need to add rules to pass the traffic you want.
-
@stephenw10 There you go! Thank you. I probably removed the default LAN rule when I installed the firewall. Hence the need to put it back. Did not notice it since the other interfaces did not have any. Except for the WAN with the RFC and private auto rules.
-
@stephenw10 Just for curiosity, was the default LAN rule looking like this?

Thanks -
Never mind.
Found the answer at
https://docs.netgate.com/pfsense/en/latest/firewall/rule-list-intro.htmlThanks
-
Nope, the default rules look like:

That allows traffic from LAN clients to access anything. So including both the LAN address (for sevices like dns, ntp etc) and external destinations.
It's included on LAN because the vast majority of installs will want to pass that. At least initially. But it's only added to LAN. Once you start adding more interfaces you probably want more complex rules.
-
@stephenw10 That is what I saw on the link I gave. You need to scroll down.

-
Ah, yes. Cross-posted!
-
@stephenw10 Good. And that is why I deleted it. Too permissive. What suprised me is the need to create a LAN rule to allow the LAN addresses to communicate with the LAN gateway, that also happens to be the firewall. Normally, you don't need a rule if you communicate within a LAN (not crossing a boundary). I guess that is special case since the target is the firewall and you need to control what reaches it, even it's own network.
-
@marchand-guy I would say most firewalls have a deny by default setup. However most/many software firewalls have a rule to allow their own subnet. Windows for instance accounts for that by defining different rules for public or private marked networks.