after upgrade to 24.11: squid doesn´t start
-
@19pegr69 said in after upgrade to 24.11: squid doesn´t start:
Hallo,
after upgrading to 24.11 squid can not be started
I always get this:
/pkg_edit.php: The command '/usr/local/sbin/squid -f /usr/local/etc/squid/squid.conf' returned exit code '1', the output was 'ld-elf.so.1: /usr/local/sbin/squid: Undefined symbol "_ZTTNSt3__118basic_stringstreamIcNS_11char_traitsIcEENS_9allocatorIcEEEE"'Would be curious, if your system was also updated from CE or just an older Plus version. Hope our workaround works for you, too.
-
This post is deleted! -
Thanks with the updates to fix the major security concerns upstream, I assume that this package will not be removed as the concerns for removing it have been addressed. Please see attached..
This was the email from the Squid development team...
"The Squid Project apologizes for being late in responding to the publication of 55 vulnerabilities disclosed by Joshua Rogers of Opera Software at https://megamansec.github.io/Squid-Security-Audit/ We thank Joshua for discovering these bugs and sharing their details with us. The surprise publication caught us off guard, but Squid developers had worked on addressing some of the disclosed vulnerabilities since before that publication. This message summarizes Squid's status on October 9th, 2024. As of Squid v6.8, the vast majority of high-impact vulnerabilities have been addressed. The following disclosed vulnerabilities are still present: ### Vulnerability “strlen(NULL) Crash Using Digest Authentication” This vulnerability is still present in Squid v6.11. A fix is expected in Squid v6.12, due any day now. Digest authentication is disabled by default; the current workaround is to avoid Digest authentication. To verify whether your Squid configuration is vulnerable, check whether it contains "auth_param” directive. Configurations with auth_param directives mentioning "digest" scheme may be vulnerable. ### pipeline_prefetch (HTTP pipelining of client-to-Squid requests) All reported pipelining-related vulnerabilities may still be present in Squid v6. Pipelining code will probably be removed in master branch and become unavailable in Squid v7. Pipelining is disabled by default. If you do not need pipelining (or do not know for sure that you need it), do not enable that performance optimization. To verify whether your Squid configuration is vulnerable, check whether it contains a pipeline_prefetch directive. Configurations containing a pipeline_prefetch directive set to a positive value may be vulnerable. ### ESI (Edge Side Includes) Most reported ESI-related vulnerabilities are still present in Squid v6. ESI code has been removed in the master branch and will not be available in Squid v7. ESI is disabled in the default build starting with Squid v6.10. In earlier versions, ESI code is enabled by default, but the risk is moderate because exploiting this family of vulnerabilities requires Squid to be configured as a reverse proxy for a malicious origin server. If you do not need ESI (or do not know whether you need it), disable it with `--disable-esi` (default for Squid v6.10 and later). To verify whether your Squid build is vulnerable, run `squid -v`. Squid v6.9 and earlier versions may be vulnerable unless the output contains `--disable-esi`. Squid v6.10 and later versions may be vulnerable if the output contains `--enable-esi`. ### Squid v5 Some fixes were backported to Squid v5, but we lack the resources necessary to support that old version. Folks running Squid v5 and earlier versions should either upgrade to the latest v6 release or rely on their integrator/distributor for support. -- Francesco Chemolli Squid Software Foundation"So it's now fixed upstream and the new version in the package reflects the updated version. Again there is still some software convergence going on with the updates.
Thanks for all you do.
-
Indeed the plan was to remove it from the package repo; it's still there since there haven't been significant challenges to keeping it and it gives more time for those using it to plan ahead. At this time there is no maintainer for the pfSense package and there are no plans to maintain it.
-
@JeGr said in after upgrade to 24.11: squid doesn´t start:
mv /usr/lib/libc++.so.1 /root
I tried and got this error when I try and restart squid. am on 24.11-RELEASE (amd64)
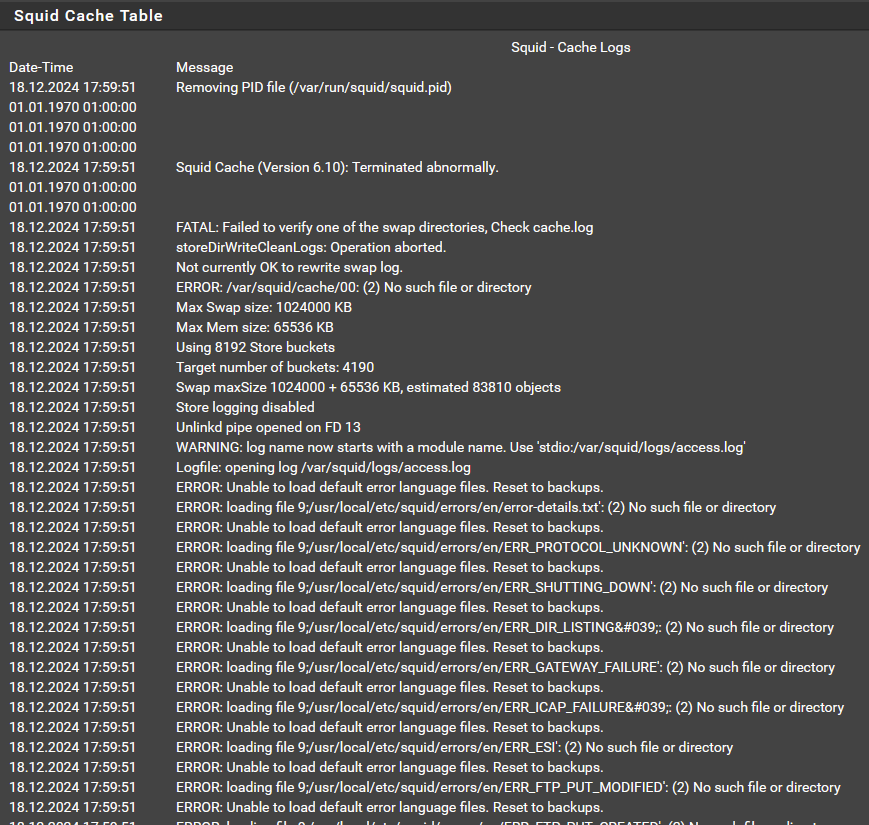
-
@dauhee That looks like missing files or stuff from de-/reinstall not finishing completely. If unsure, you can easily remove the package and install again or reinstall. But that it starts AT ALL is due to the bad library being moved so it now can start again. Everything after is likely a config or install thing but seeing it started up again for you is very nice!
Should be possible to restore or roll back to your config now. Also keep in mind the other patches above that mentioned problems with the config file format (noTLSv1 etc.) that perhaps need to be patched, too.
But that should at least fix the point with it not starting due to the ld-elf.so error message.
Cheers :)
-
@dauhee you need to recreate the linker file to the error log folder it is listed incorrectly again.
https://redmine.pfsense.org/issues/14406
I am thinking that 14406 is the same issue for the error log folder mix up again. It jumps from en to en-us sometimesln -s /usr/local/etc/squid/errors/templates /usr/local/etc/squid/errors/en-us
ln -s /usr/local/etc/squid/errors/templates /usr/local/etc/squid/errors/en
-
For me, it was some whitespace that was causing the fatal error:
in
/usr/local/etc/squid/squid.conf:Among the first lines:
http_port ... SNIP ... options=NO_SSLv3,NO_TLSv1, NO_TLSv1_1, NO_TLSv1^ Notice the whitespace after the commas in the options field. Removing those and running:
squid -k parseensured the config was good now, and I got the service to start. -
How to apply this one? I've added this to System -> Patches -> Fetch
but it seems Apply is not available.
@marcosm said in after upgrade to 24.11: squid doesn´t start:
The issue should be fixed after applying both the previous commit and this one:
https://github.com/pfsense/FreeBSD-ports/commit/009dc5f68e0cf1d1a767d1a9119bcbaface44823 -
@james-braga said in after upgrade to 24.11: squid doesn´t start:
https://github.com/pfsense/FreeBSD-ports/commit/009dc5f68e0cf1d1a767d1a9119bcbaface44823
It's a patch to ports so you need to adjust the Path Strip Count to 4.
-
R ramup referenced this topic on
-
S snow referenced this topic on