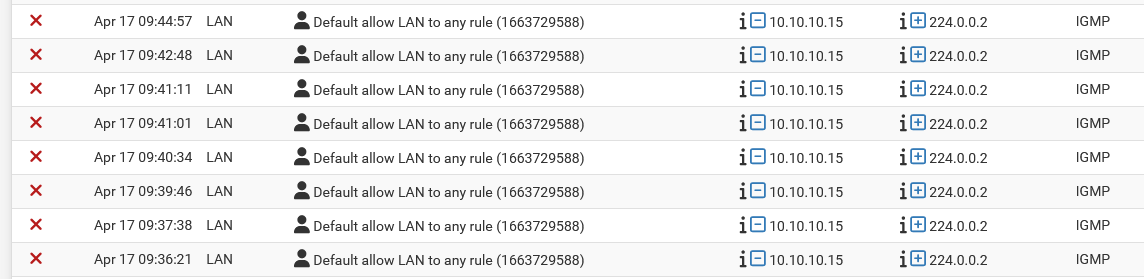
How to disable this event from being logged on firewall?
-
@stephenw10 Not sure I know what to do there, I don't need to block pinging. Can you help me understand what is happening here?
-
@CreationGuy that is not ping (ICMP) that is IGMP
https://en.wikipedia.org/wiki/Internet_Group_Management_Protocol
You could as mentioned create a specific rule to allow it or deny it - that doesn't log. Or you could just turn off default deny logging and create whatever rules you want to log, say a tcp/udp block at the end that that logs.
-
The igmp logging behaviour changed recently. It was actually broken for years and now works as intended. But that is unexpected for most users. Note that log is shown as blocked by the pass rule!
-
Any device on the LAN vlan is allowed to communicate to any other vlan. Some other vlans such as IoT or Security camera cannot talk to any other vlan.
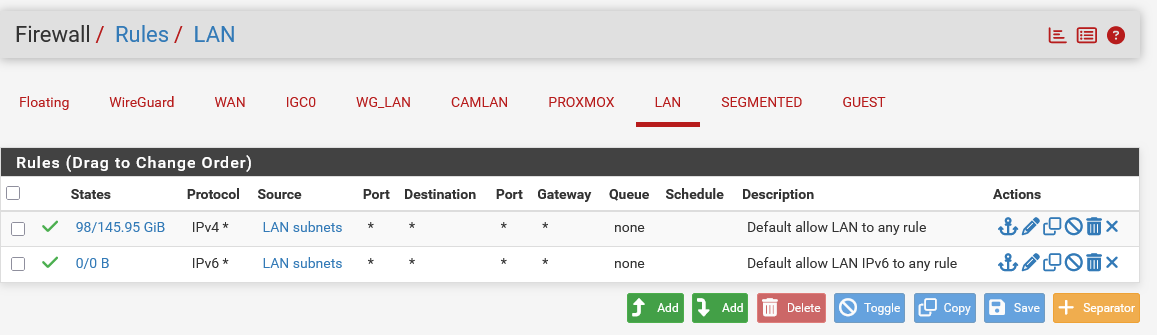
This is the LAN rules -
@CreationGuy well simple thing to do would be a put a rule on top to destination 224.0.0.2 either allow or deny and not log it. This would go for any interface.
Or just pick IGMP as the protocol.
Or better yet is what is that 10.10.10.15 device - why is it sending a IGMP? Do you need it too for something else on your network - maybe you can just turn it off on that device? 224.0.0.2 is "The All Routers multicast group address"
I wouldn't think normal devices should be sending that out. Do you have a switch or something that is capable of routing?
-
@johnpoz It's an iphone - I'll have to look and see what would be causing that on the device.
-
@CreationGuy iphone is sending out igmp? Really - I have 2 iphones.. I have never seen this.. odd..
224.0.0.251 to port 5353 (mdns) would make sense, but to 224.0.0.2 seems odd to me from an iphone.
-
@johnpoz It's odd. Two other iphones are not doing this. I'll have to see if it's trying to broadcast music or if its bonjour. Really strange.
Edit:, I made the rule, but it's still getting logged.
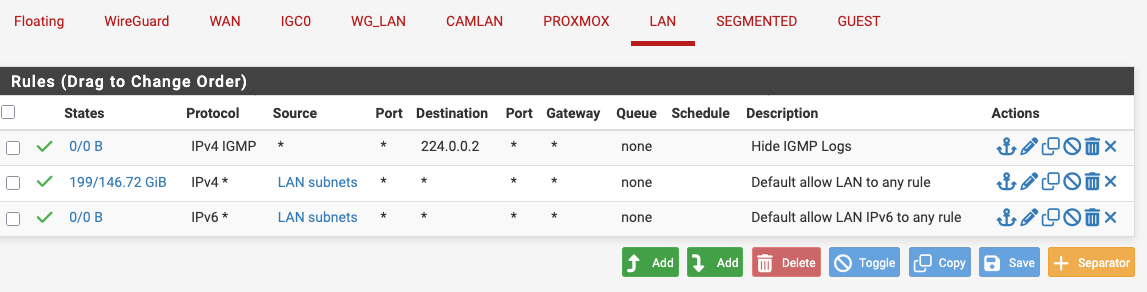
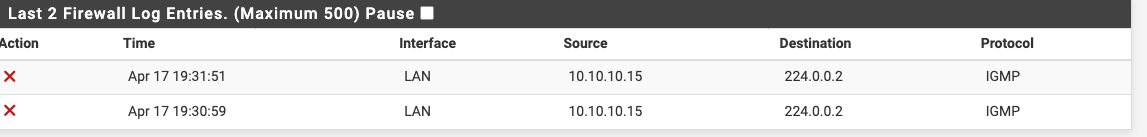
-
@CreationGuy that is odd that is not triggering.. see the 0/0 - do you have floating rule?
That for sure should trigger.. I mean it is IGMP.. If you don't have a floating rules - I would check your state table - its possible I guess that since it is the allow rule of lan that "blocking" that a state was created
I would search your state table for anything with destination of that 224.0.0.2 and if there is kill them.
Not exactly sure how the broadcast stuff works for music over bonjour - but its odd that it would send it to the all routers address.. But that is for sure a possibility with a high probability of that being the source of the traffic.
Personally not a fan of any of that bonjour stuff - never use it myself and have never done anything with music broadcast with apple, I want to play music I just connect to my plex server which has all my music on it. Not really a fan of stuff that just sends out traffic for no reason ;) my plex server drives me nuts sending out UPnP/SSDP to 239.255.255.250 shit, which I am not using every 10 seconds, I finally blocked it that the port on the switch ;) Since I could not find anyway to kill it in plex, even when you turn off all of the features that should enable that to be sent out.. Drove me nuts for way to long ;)
Which is why stopping it at the source is better option, if you're not actually using it, sure you can do some stuff so pfsense doesn't log it, or blocks it etc.. But since its multicast - every other device on that L2 is going to see that traffic..
edit: other thing you could try if no floating rules, and no states is change that from igmp, to just IPv4 with that 224.0.0.2 destination you have set.. That for sure should trigger.
-
Probably needs
Allow IP optionsset in the advanced rule options. -
@stephenw10 yup that would be another way @CreationGuy but his rule above his lan allow should trigger and not log that igmp traffic.. and no other rules should be evaluated.. So it shouldn't still see the igmp traffic on his lan allow and block it because of the IP options setting.