SNAT IPsec not work
-
Good afternoon, I'm trying to configure a Source NAT for my IPsec tunnels. I tried NAT/BINAT and it worked. However, I have more than one network, in this case only 4 /24 networks to be translated. I saw in the documentation that PFsense supports NAT overload, which seems to be a common outbound NAT. However, I've already configured it and it's not working. My IPsec is policy based. Can anyone help me?
-
@alvescaio
Can you give some more details on what you intend achieve and what you tried? -
I configured Outbound NAT by translating the source that comes from the openvpn network 192.168.70.0/24 to the network 10.193.10.0/24 which is a local network that is advertised in phase 2 of the IPsec vpn with a client, so far it worked, but when I made the rule for a second network 192.168.60.0/24 to translate to the same network and travel in the same tunnel, the NAT is not applied and the traffic is going out to the WAN.
-
@alvescaio
Can you be a bit more precise, please?For the OpenVPN tunnel you have a NAT rule in the phase to to nat it to a single IP in the LAN subnet, as I got it?
Well, this should give the VPN clients access to the remote site.But I don't understand this sentence:
@alvescaio said in SNAT IPsec not work:
but when I made the rule for a second network 192.168.60.0/24 to translate to the same network and travel in the same tunnel
What is the "second network"?
Which "same network"?
Which tunnel? -
Let's go, I have 5 networks coming from openvpn, that is, there are 5 networks accessed remotely by the company's employees, I need to make these employees connected via openvpn access the clients that have IPsec VPNs connected with pfsense, for example: I have a client whose destination IP is 10.0.9.8 and I access it via IPsec vpn, I want to translate all my openvpn networks to the 10.193.10.0/24 network which is the network advertised as local in the IPsec tunnels that access the clients. The problem is that when I do BINTAR it works, but it is limited to a single network, that is, it does not meet what I need, in this case I would have to use outbound nat, however the network is not being natated, when I try to communicate the traffic goes out through the WAN instead of entering the IPsec VPN
-
@alvescaio
You cannot do this with outbound NAT rules. You have to do the translation in IPSec phase 2.
And yes, it's not possible to create multiple BINAT phase 2 with the same remote subnet. This is not going to work, since pfSense cannot translate the remote network to multiple local networks at once.What you can do is translating the OpenVPN tunnel networks to a single IP free within the local subnet. This allows only one-way access for plausible reasons.
For instance, I assume, 10.193.10.0/24 is your local subnet, 10.0.9.0/24 the remote and you need to enable communication between both.
I also assume, IPs above of 10.193.10.200 are not in use, 192.168.60.0/24 is OpenVPN tunnel network A, 192.168.70.0/24 is B.So you can create additional phase 2 for A:
local: 192.168.60.0/24
NAT: address > 10.193.10.201
remote: 10.0.9.0/24phase 2 for B:
local: 192.168.70.0/24
NAT: address > 10.193.10.202
remote: 10.0.9.0/24and so on.
Then move the original phase 2 for your LAN down to the bottom, so that the NAT rules can take effect.
-
Thanks, but I have a question. Assuming I have 5 openvpn networks to do this, will I have to do 5 phases 2? And how would this work on the client side? Because he will only see my native network 10.193.10.0/24, he will only have one phase 2 on his side while I would have 5?
-
@alvescaio said in SNAT IPsec not work:
Assuming I have 5 openvpn networks to do this, will I have to do 5 phases 2?
Not really necessarily, but each network has to be part of the "local network" in the NAT phase2 at least. This means, if you can set the network mask so that it includes all you can also go with a single phase 2.
In any case you can only use a single NAT address.
And how would this work on the client side? Because he will only see my native network 10.193.10.0/24, he will only have one phase 2 on his side while I would have 5
The NAT address has to be part of this network.
Maybe not all IPSec implementations accept this, however. -
So on my side, phase 2 would be like this?
192.168.70.0/24 - SNAT 10.193.10.0/24
client network - x.x.x.x
192.168.60.0/24 - SNAT 10.19310.0/24
client network - x.x.x.x
and so on?
-
@alvescaio said in SNAT IPsec not work:
So on my side, phase 2 would be like this?
Tried to explain that above:
So you can create additional phase 2 for A:
local: 192.168.60.0/24
NAT: address > 10.193.10.201
remote: 10.0.9.0/24phase 2 for B:
local: 192.168.70.0/24
NAT: address > 10.193.10.202
remote: 10.0.9.0/24and so on.
But maybe I understood your aims wrongly.
-
I created the second phase 2, it appears up in the dashboard, but it does not appear listed in ipsec > status

file:///home/caiochagas/Imagens/Capturas%20de%20tela/Captura%20de%20tela%20de%202025-05-07%2020-42-14.png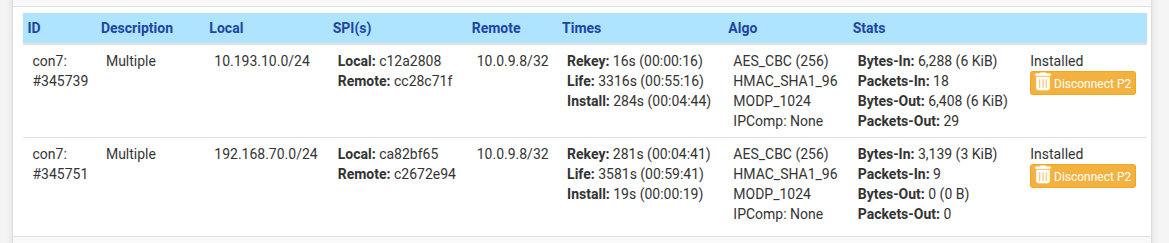 file:///home/caiochagas/Imagens/Capturas%20de%20tela/Captura%20de%20tela%20de%202025-05-07%2020-43-23.png
file:///home/caiochagas/Imagens/Capturas%20de%20tela/Captura%20de%20tela%20de%202025-05-07%2020-43-23.png -
Hello my friend, some news?
-
Morning my friend, some news about topic?