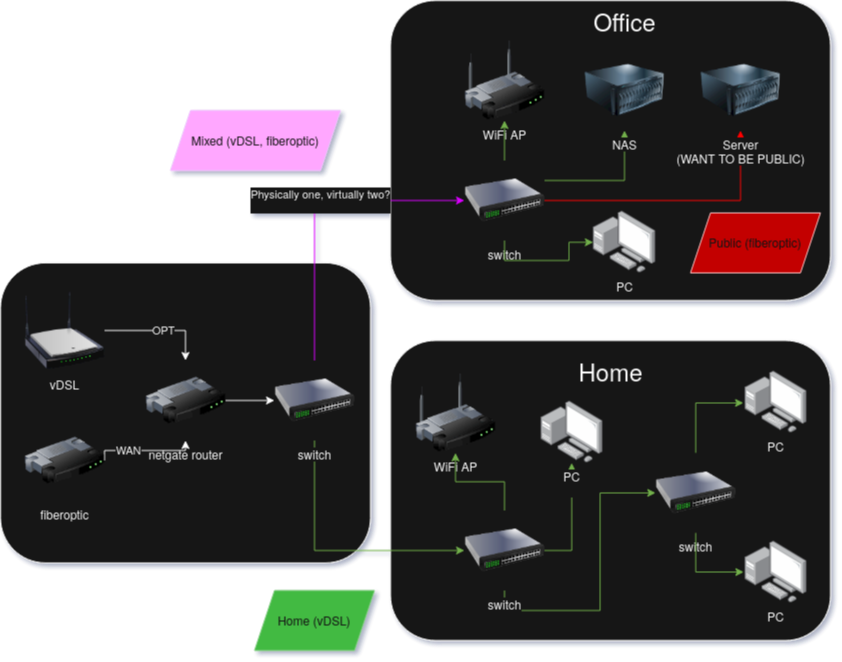
how to separate two WAN connetions into home internet and work internet virtually
-
@stephenw10
 pfsense+ 24.11
pfsense+ 24.11 -
I'm kind of out of my depth here, I'd appreciate any tips on how to solve this issue :)
Anyone got any ideas? -
Is it just the inbound traffic that's failing or are you also seeing outbound not using the correct WAN?
Try to ping the target server from pfSense itself. It should respond.
Then try again but set the ping source IP to some other interface. Does it still respond?
-
- PUBLIC_OPT1(servers VLAN) > server works
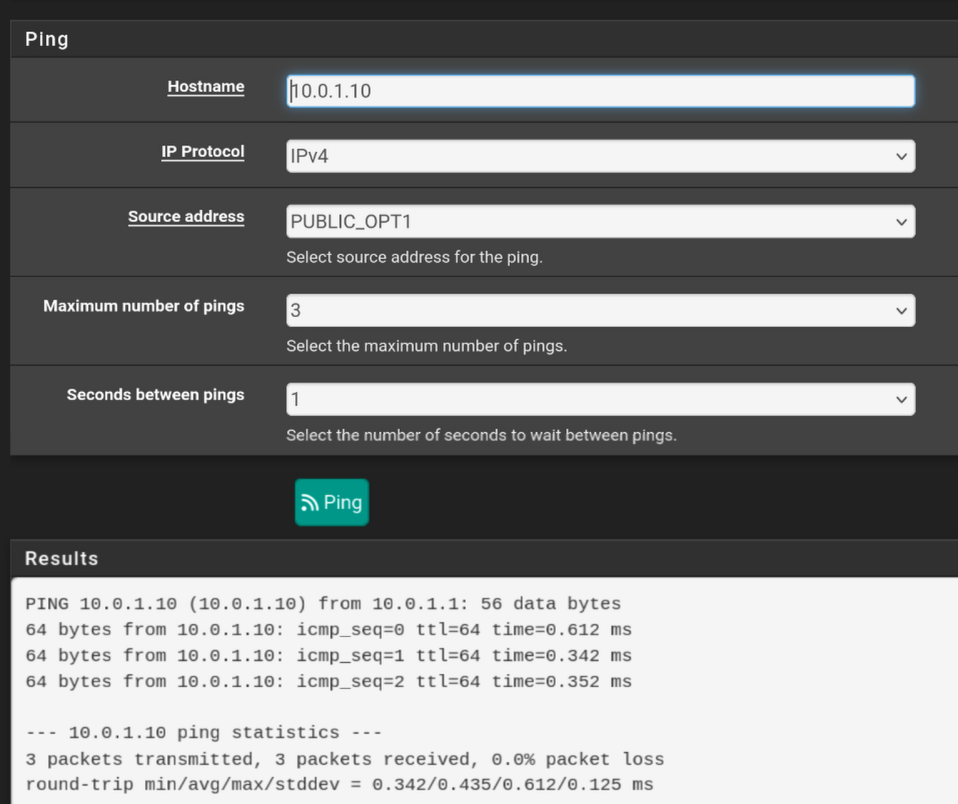
- OPT > server doesn't work
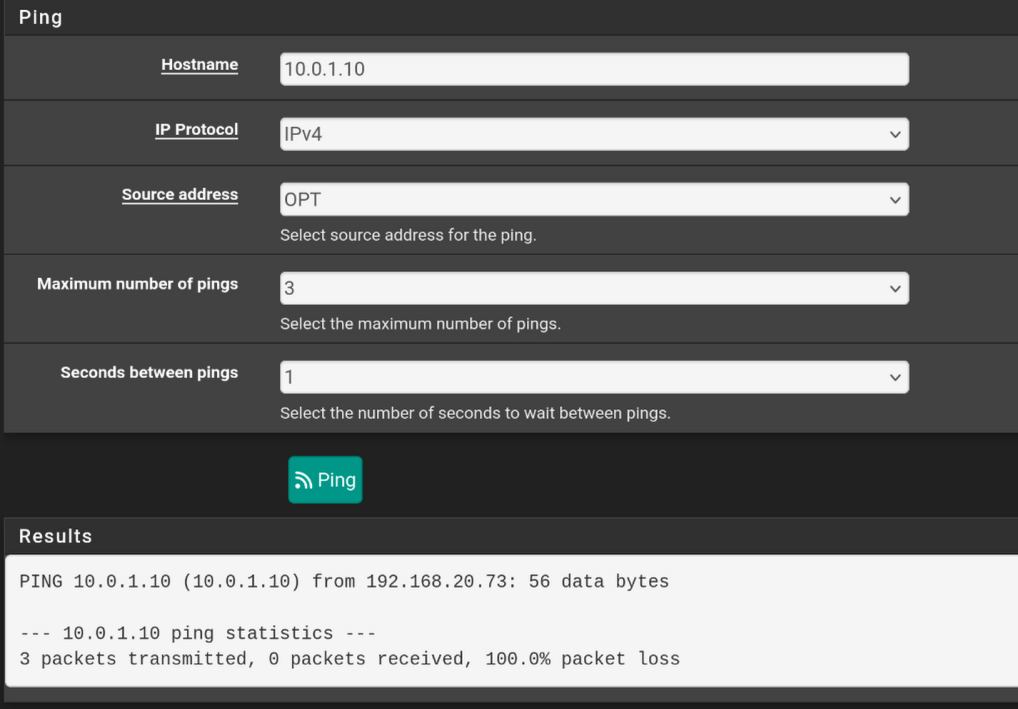
- WAN > server doesn't work
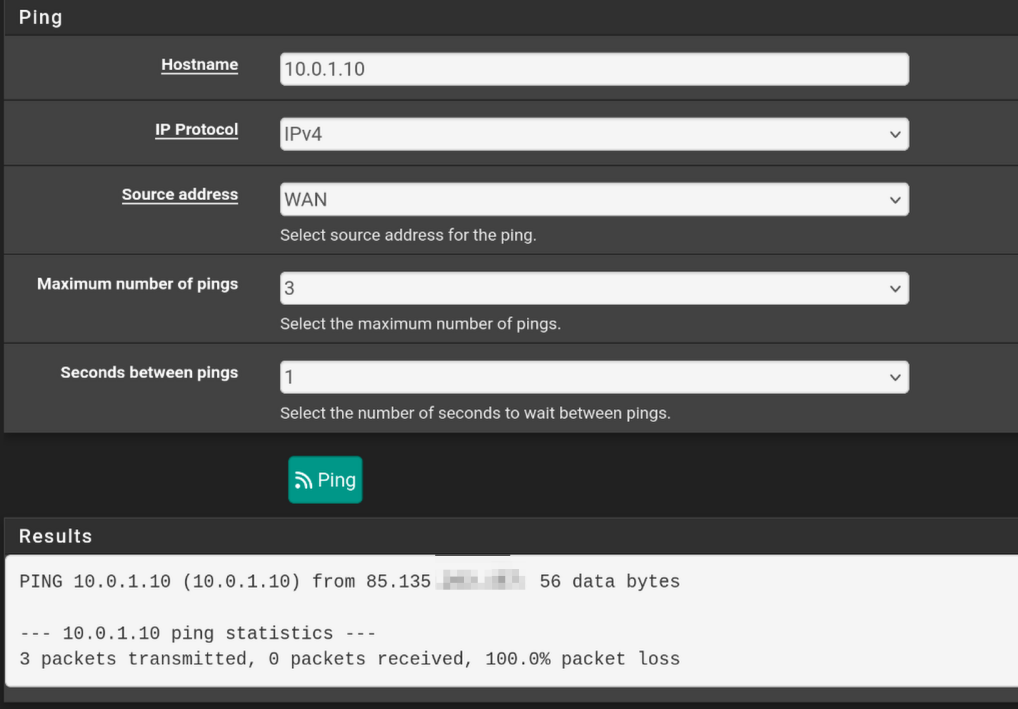
- Public IP > server doesn't work
Though I'm not sure if I'm using the wrong address? The interfaces' ips are in different subnets, so I don't know if they should be able to ping.
My server has access to the internet, ping 1.1.1.1 from the server works. I don't really know which WAN it's using though. I assume WAN and not OPT, because the only way I got the vlan to work is by keeping default vlan untagged and add vlan 10 as tagged. How could I force only vlan 10 to be what the server has access to?
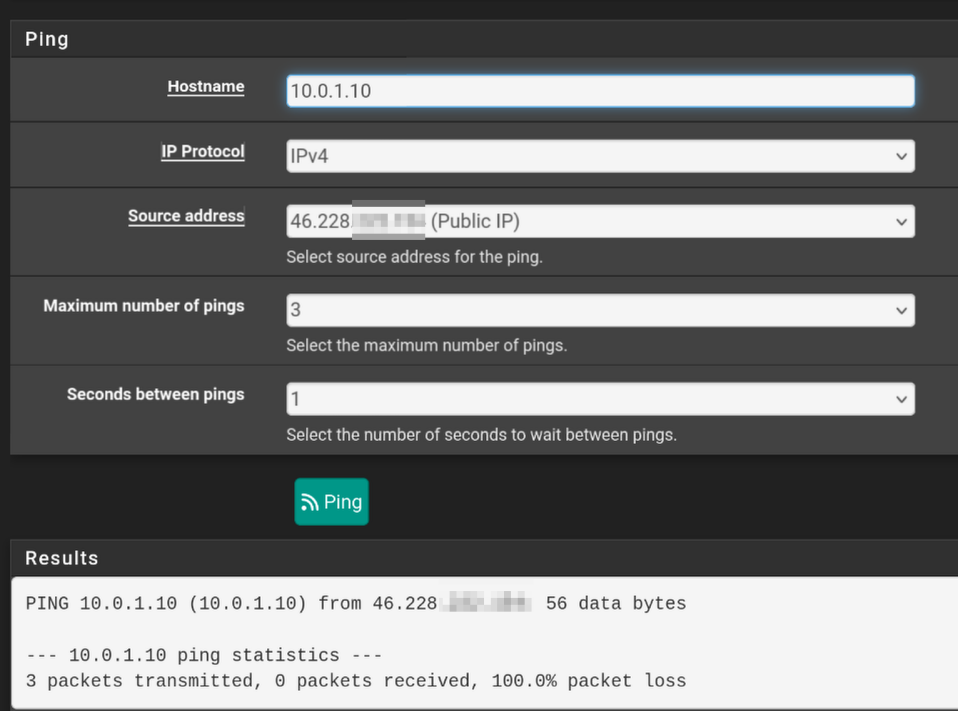
- PUBLIC_OPT1(servers VLAN) > server works
-
@Djkáťo said in how to separate two WAN connetions into home internet and work internet virtually:
My server has access to the internet, ping 1.1.1.1 from the server works. I don't really know which WAN it's using though.
Start a continuous ping on the server. Check the states created on the firewall. it should be pretty obvious which WAN it's using.
I see your OPT interface is using a private subnet. That implies there is another layer of NAT upstream of it, some other router. That would need to be configured to pass all incoming traffic to pfSense.
-
@stephenw10 said in how to separate two WAN connetions into home internet and work internet virtually:
That implies there is another layer of NAT upstream of it, some other router
The ISP explained it as it being the fiberoptic router I got installed. I was wondering about it as well. How can I have a private IP on my OPT interface but have them claim I have a public IP?
So should I reach out to my ISP and ask about this?
-
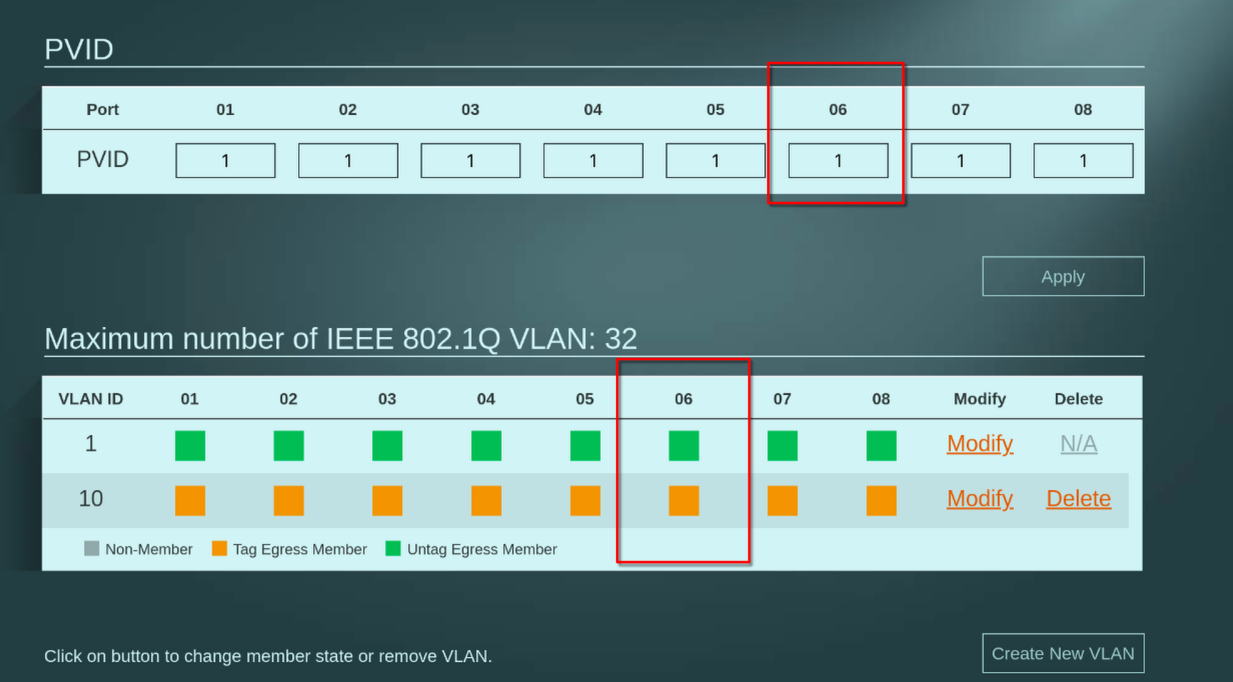
I have just tried isolating the server to only vlan 10 like this:

and after I added a firewall rule to allow LAN > PUBLIC_OPT1, I can access it on 10.0.1.10! And I bet it's only using OPT now.
But I wonder where this IP address is coming from. It doesn't match any of my interfaces, and DHCP on that interface is set to give out 10.0.1.0/24. Where did it get this address from?
-
On data I can now access <domain>:2283 and <public_ip>:2283 get the docker container! I guess I just had to do that VLAN setting which forced it to use OPT, wohoo!
You mentioned that if I try to access that on local network it won't work, I'll look into this NAT reflection you mentioned. Thank you so much @stephenw10 for your guidance, it seems to work now :)
-
Yes, in order for inbound traffic to work there it either has to pass the public IP directly to pfSense or forward all traffic to the internal IP that pfSense is using.
Now it looks like it might be configured to forward all traffic because when you tested from an external location you could see states incoming from your real IP. So you may not need to do anything. Though it's almost always better to get the public IP on pfSense directly if you can.
Can you test to some other internal device that you can set the local firewall on?
-
@stephenw10 said in how to separate two WAN connetions into home internet and work internet virtually:
Can you test to some other internal device that you can set the local firewall on?
Sorry, I'm not sure what you mean. Try to access another device from the public IP (by NATing it?), or access server through public IP on another device?
Also, looked into NAT reflection so I can use those domains locally.
Under system>advanced>firewall & NAT, I enabled NAT reflection to Pure NAT, enabled it for 1:1 NAT and automatic outbound NAT, but when I try to access myservice.mysite.tld , the page redirects to myservice.mysite.tld:{pfsense port}, and gives error:Potential DNS Rebind attack detected, see https://en.wikipedia.org/wiki/DNS_rebinding
Try accessing the router by IP address instead of by hostname.So it's not gonna be as easy as turning it on huh...
I also tried services>dns forwarder to add host override for my domains, but that doesn't work either.
How can I make this work? -
@Djkáťo said in how to separate two WAN connetions into home internet and work internet virtually:
Sorry, I'm not sure what you mean. Try to access another device from the public IP (by NATing it?), or access server through public IP on another device?
I mean your server at 10.0.1.10 appears to be refusing the connections. So try pointing the forward to some other device that you know will respond, if only to pings.
You might need to move the pfSense webgui onto a different port in Sys > Adv > Admin Access.
-
@stephenw10 said in how to separate two WAN connetions into home internet and work internet virtually:
I mean your server at 10.0.1.10 appears to be refusing the connections.
As I said above, it's now working when connecting to server from outside though (phone data)? Even through cloudflare (proxied or not), my domains are connecting and doing what I configured on server with caddy, it's working just fine.
I just can't access the domains from my LAN as you described would be the problem. That's the part I'm asking now about.Sorry if I'm being unclear
-
Ah, OK.
So if you have enabled:
Enable NAT Reflection for 1:1 NATandEnable automatic outbound NAT for Reflectionit should work.Try to open something that should be forwarded then check the states. You should see the NAT states on both interfaces applied to make the reflection work.