Unknown DHCP ping
-
@deleted said in Unknown DHCP ping:
option-request DNS-server DNS-search-list
Huh? I showed you how to find the actual mac address of the device. Not sure what your looking up, you can not lookup a link-local address to find the maker, like you can from a mac address.
See in my example where it says cisco on that a4:9b:cd address..
You can look them up on plenty of websites..
https://maclookup.app/search/result?mac=a4:9b:cd
If your not seeing this link-local address in your NDP table, then sniff, ie do a packet capture.. It will show you the mac address.
That traffic is a dhcpv6.. https://en.wikipedia.org/wiki/DHCPv6
Once you know the mac address, you should be able to get a clue to what device is asking for dhcpv6.
edit: here is a packet capture showing the mac, set your view options to full, set the port to 547
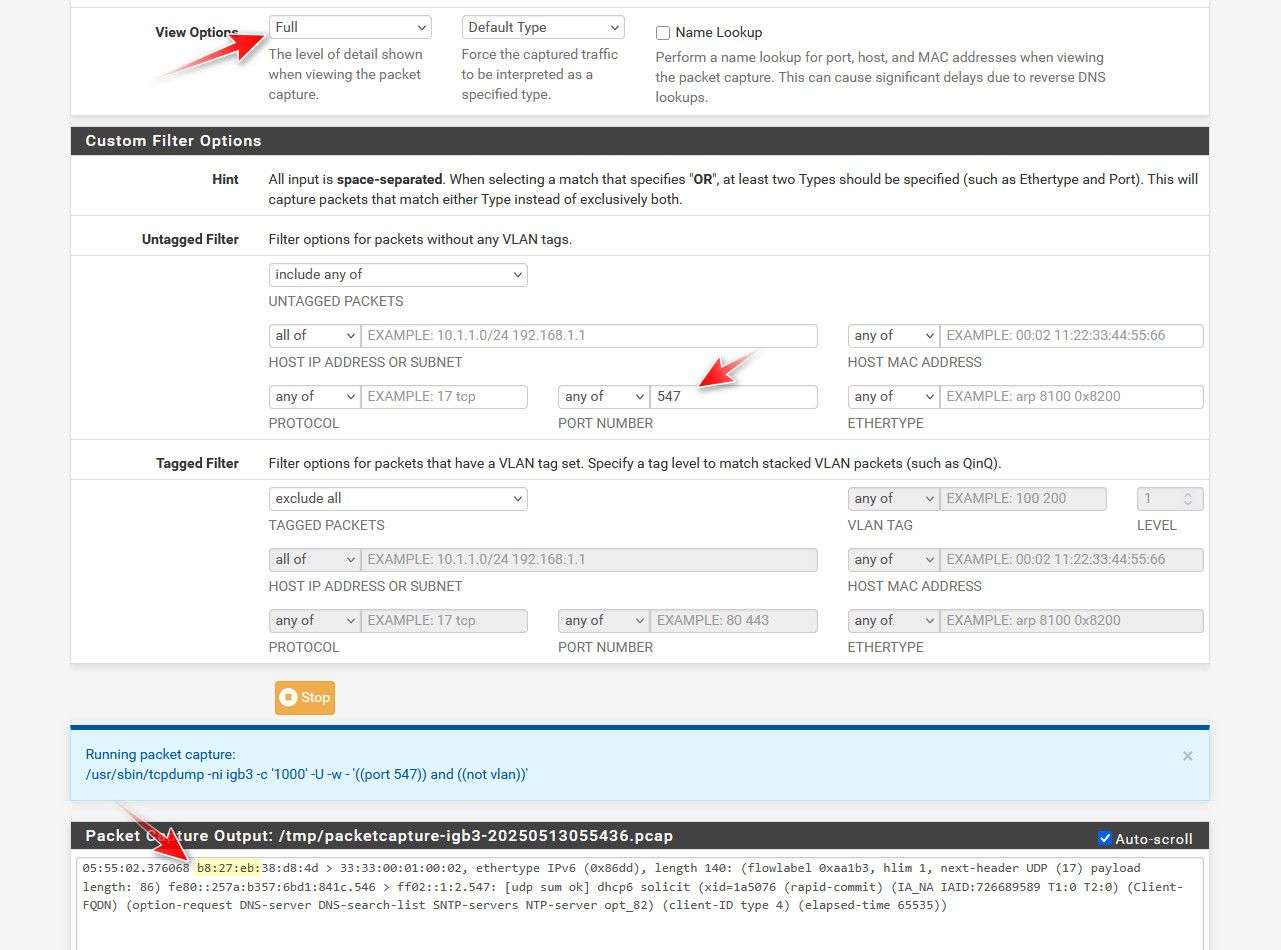
If I lookup the mac of the sender, that b8:27:eb I see that is my raspberry pi
https://maclookup.app/search/result?mac=b8:27:eb
Those dns-server dns-search-list are options the dhcpv6 client is asking for.. See on the last line of sniff above you see the options, mine is also asking for sntp and ntp servers..
edit2: Now to turn ipv6 off on my raspberry pi
I set
net.ipv6.conf.all.disable_ipv6 = 1in
/etc/sysctl.confI also set
service procps reloadin
/etc/rc.localThen did a
sysctl -pnow if I look on my pi you will notice it no longer has a link-local IPv6 address even
root@pihole:/home/pi# ifconfig eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.3.10 netmask 255.255.255.0 broadcast 192.168.3.255 ether b8:27:eb:38:d8:4d txqueuelen 1000 (Ethernet) RX packets 1910131 bytes 194224986 (185.2 MiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 1909435 bytes 257026039 (245.1 MiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0Which before it did, and notice in my sniff above that was the link-local sending the request for dhcpv6
root@pihole:/home/pi# ifconfig eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.3.10 netmask 255.255.255.0 broadcast 192.168.3.255 inet6 fe80::257a:b357:6bd1:841c prefixlen 64 scopeid 0x20<link> ether b8:27:eb:38:d8:4d txqueuelen 1000 (Ethernet) RX packets 1909789 bytes 194202989 (185.2 MiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 1909069 bytes 256976581 (245.0 MiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 -
Hi @johnpoz, thanks for your detailed reply with all the info.
I understand so far.
I also looked there as you did on the screenshot.However, just as you read, the “option-request DNS server ...” entry and thought it was an attack.
However, I have now been able to find out the MAC and as suspected it is the pfsense itself.
I double-checked everything directly in the bios of the server.
No DHCP is running. Everything is static or off.I have also looked through every menu of the sense to see if I have overlooked anything.
However, no option was found.However, you are right, I know the option "net.ipv6.conf.all.disable_ipv6" as well.
Would it be a solution if I put the option in the advanced settings / system fine-tuning?Thanks again for the very detailed answer.
(Unfortunately I don't have enough points and a thumbs up to give). -
@deleted I wouldn't try that with pfsense, it runs on freebsd - which is sim to linux, but not exactly.. So it might be a bit different.
Where exactly are you seeing that? I assumed it was in your firewall log? So its pfsense asking for IPv6 via dhcp on its wan?? if so just set pfsense wan to not do IPv6 on its wan..
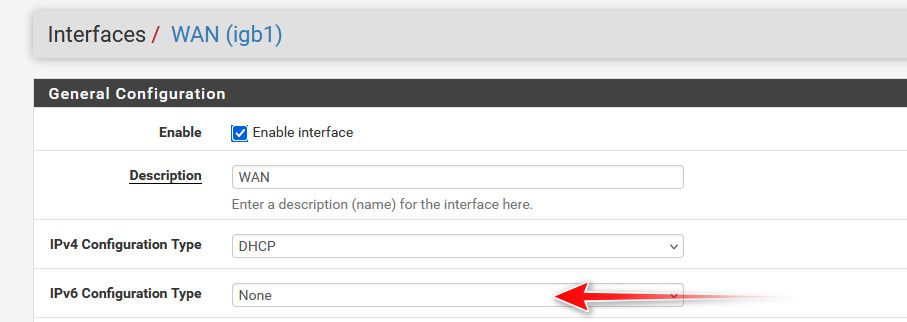
Pfsense shouldn't log that it trying for dhcp - unless you unchecked the ipv6 box..

If you uncheck that box, then yeah it creates block rules for anything IPv6. But just setting none on your wan interface for ipv6 would stop it from asking for IPv6 via dhcpv6
-
This is the entry in the log:

I have configured my interface exactly as shown in your picture.
Except that it has a static IPv4.
The Allow IPv6 field is deactivated.The settings were already set as they were, I didn't update anything.
Or is it in FreeBSD?
-
@deleted so its not pfsense sending it.. Why would the firewall log outgoing traffic from pfsense?
I have now been able to find out the MAC and as suspected it is the pfsense itself.
The lan side interfaces should not be requesting IPv6 unless you had them set for dhcp for IPv6, the IPv6 setting on your lan side interfaces should be NONE as well.
When you disable IPv6 it does create block rules - that could be blocking outbound? But an outbound block log normally shows direction arrow..
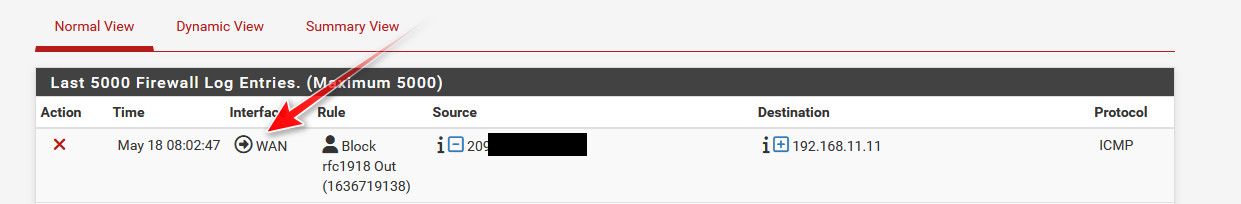
Please show us how you determined the mac address of this traffic and that it pfsense itself. If the interface for IPv6 is set to none - it wouldn't be sending dhcpv6 requests.
I do not disable IPv6 because I do use it for testing.. By default IPv6 is allowed - ie that check box is checked.. So I am not exactly sure the rules it creates when you uncheck it.. But it would seem odd that it would block outbound traffic and not log that it is outbound traffic like the above picture, where my outbound rule blocks rfc1918 going out my wan.
But if an interface is set to none for IPv6 - it sure wouldn't be sending dhcpv6 requests.. I doubt its pfsense mac address sending that to be honest.. Unless you have the lan01 interface set to dhcpv6.. And even if you did I would think the block all ipv6 if set for outbound blocking it would log the direction, which from what you posted that is an inbound block.. So into the lan01 interface, not traffic leaving the interface into the lan01 network.
edit: so I disabled IPv6 by unchecking the box, and it does create an outbound rule
You can view the full ruleset
https://docs.netgate.com/pfsense/en/latest/firewall/pf-ruleset.htmlNot all rules are shown in the gui, there are some hidden rules to see you have to use the above linked instructions.
# Block all IPv6 block in quick inet6 all ridentifier 1000000003 label "Block all IPv6" block out quick inet6 all ridentifier 1000000004 label "Block all IPv6"But as you see if the pfsense interface was sending it - it would show that it was in the outbound direction.
I enabled dhcp for ipv6 on my test interface - and you can see pfsense with default logging on, logs that in the outbound direction, since your log does not show this - then the traffic was inbound into your lan01 interface - and not from pfsense itself
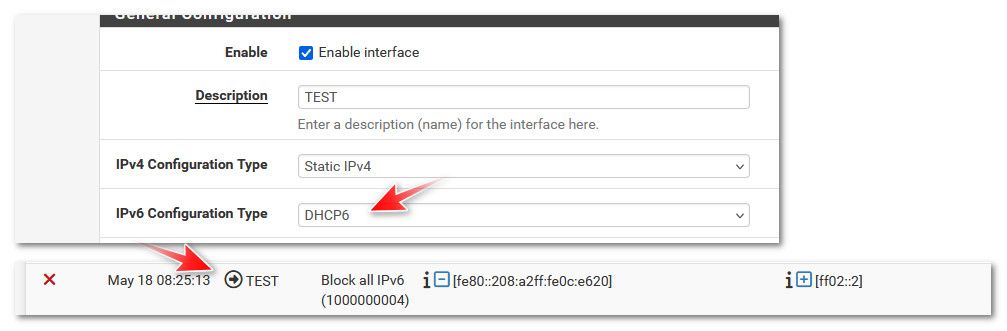
And you can also tell that was inbound because of the rule ID, 1000000003 vs the 4 one which is the outbound rule.
-
@johnpoz
I really can't tell you what's happening here.But yes, you're right, I can remember the arrows.
But I haven't seen any for a long time.
Neither in my pfSense-dark-BETA theme nor in the original pfSense theme. (Just looked.)
However, I perceived this more as a design change and don't attach so much importance to whether there is an arrow or not.Which version of pfSense are you using?
I use pfSense+ ver. 24.11I have made a larger section so that you can see that it is the same view:
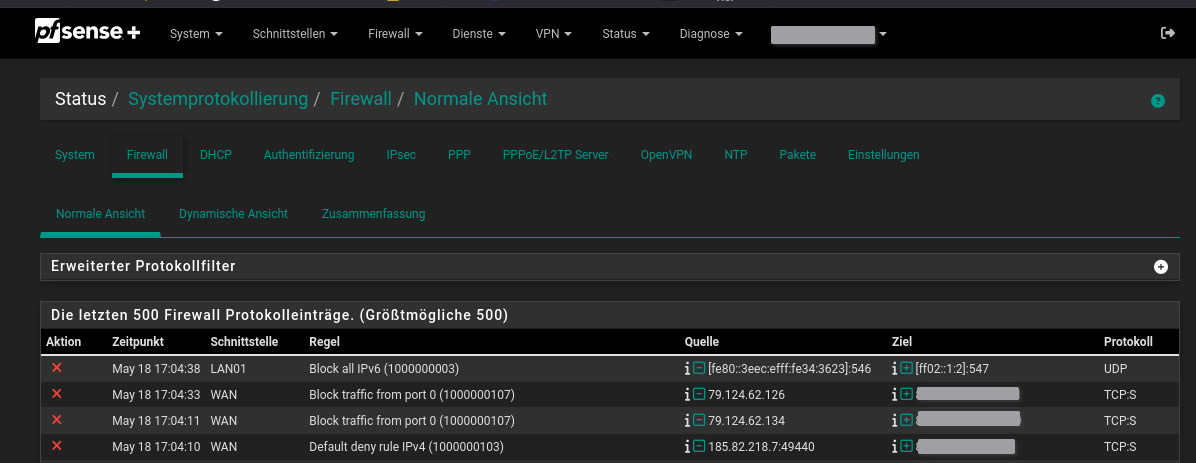
I ended up doing exactly the same as you;

I then searched for the MAC in the ARP table and was able to assign the IP of the BNC access of the server on which pfSense is running.
As I said, I have checked the bios several times but I have no IPv6 or DHCP running which could generate the entry.
-
@deleted Super Micro Computer, Inc. is what that 3c:ec:ef shows up as.. That is what your pfsense is running on.. Show the mac address on your pfsense.
ifconfig..
I am running 24.11+ as well.
Is pfsense running on a vm where it would be using the same mac as the host? That traffic is blocked inbound into the interface - it is not pfsense sending it - it can not send inbound traffic into its own interface.
-
Smells like IPMI set to use a shared NIC.
-
@stephenw10 yup another possibility for sure.
edit: Odd that your seeing inbound port 0.. I don't think I have seen traffic like that.. That source IP is cloudvps-net??
-
Yes, it runs on a SuperMicro 1537.
However, it is not a VM or similar, but a dedicated 1U server.I even bought it from Netgate in the store, so I didn't use my own hardware in this case.
-
@deleted what cables are plugged in exactly from the pfsense box? is there an ipmi interface that is plugged into your lan switch?
please show your ipconfig on pfsense.. Your not going to see inbound into your lan01 interface - unless for example you have some sort of shared ipmi interface that shares the same mac but has its own port.
Or maybe its off by 1 on the mac..
example - my pfsense interfaces - the mac is off by 1 for each interface
igb2: flags=1008843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST,LOWER_UP> metric 0 mtu 1500 description: WLAN options=4e120bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,WOL_MAGIC,VLAN_HWFILTER,RXCSUM_IPV6,TXCSUM_IPV6,HWSTATS,MEXTPG> ether 00:08:a2:0c:e6:20 inet 192.168.2.253 netmask 0xffffff00 broadcast 192.168.2.255 inet6 fe80::208:a2ff:fe0c:e620%igb2 prefixlen 64 scopeid 0x3 media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> igb3: flags=1008843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST,LOWER_UP> metric 0 mtu 1500 description: DMZ options=4e120bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,WOL_MAGIC,VLAN_HWFILTER,RXCSUM_IPV6,TXCSUM_IPV6,HWSTATS,MEXTPG> ether 00:08:a2:0c:e6:21 inet 192.168.3.253 netmask 0xffffff00 broadcast 192.168.3.255 inet6 fe80::208:a2ff:fe0c:e621%igb3 prefixlen 64 scopeid 0x4 media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> igb4: flags=1008843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST,LOWER_UP> metric 0 mtu 1500 description: NVR options=4e120bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,WOL_MAGIC,VLAN_HWFILTER,RXCSUM_IPV6,TXCSUM_IPV6,HWSTATS,MEXTPG> ether 00:08:a2:0c:e6:22 inet 192.168.110.253 netmask 0xffffff00 broadcast 192.168.110.255 inet6 fe80::208:a2ff:fe0c:e622%igb4 prefixlen 64 scopeid 0x5 media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> igb5: flags=1008843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST,LOWER_UP> metric 0 mtu 1500 description: W_Roku options=4e120bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,WOL_MAGIC,VLAN_HWFILTER,RXCSUM_IPV6,TXCSUM_IPV6,HWSTATS,MEXTPG> ether 00:08:a2:0c:e6:23 inet 192.168.7.253 netmask 0xffffff00 broadcast 192.168.7.255 inet6 fe80::208:a2ff:fe0c:e623%igb5 prefixlen 64 scopeid 0x6 media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>So really like to see which interface of pfsense has that mac 3c:ec:ef:34:36:23
-
This post is deleted! -
Yes, the connection is connected to a LAN switch.
It is a Cat 6a patch cable.(Have a little patience. If I try to post everything at once it will be marked as spam.)
ix0: flags=1008843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST,LOWER_UP> metric 0 mtu 1500 description: server options=48138b8<VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,WOL_UCAST,WOL_MCAST,WOL_MAGIC,VLAN_HWFILTER,HWSTATS,MEXTPG> ether 3c:ec:ef:bf:98:ba inet 192.168.7.1 netmask 0xfffffff8 broadcast 192.168.7.7 inet6 fe80::3eec:efff:febf:98ba%ix0 prefixlen 64 scopeid 0x1 media: Ethernet autoselect (10Gbase-Twinax <full-duplex,rxpause,txpause>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> ix1: flags=8943<UP,BROADCAST,RUNNING,PROMISC,SIMPLEX,MULTICAST> metric 0 mtu 1500 description: thc options=48138b8<VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,WOL_UCAST,WOL_MCAST,WOL_MAGIC,VLAN_HWFILTER,HWSTATS,MEXTPG> ether 3c:ec:ef:bf:98:bb inet 192.168.8.1 netmask 0xfffffffc broadcast 192.168.8.3 inet6 fe80::3eec:efff:febf:98bb%ix1 prefixlen 64 scopeid 0x2 media: Ethernet autoselect status: no carrier nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> igb0: flags=1008843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST,LOWER_UP> metric 0 mtu 1500 description: media options=48120b8<VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,WOL_MAGIC,VLAN_HWFILTER,HWSTATS,MEXTPG> ether 3c:ec:ef:bd:09:48 inet 192.168.6.1 netmask 0xfffffff0 broadcast 192.168.6.15 inet6 fe80::3eec:efff:febd:948%igb0 prefixlen 64 scopeid 0x3 media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> igb1: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 description: office options=48120b8<VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,WOL_MAGIC,VLAN_HWFILTER,HWSTATS,MEXTPG> ether 3c:ec:ef:bd:09:49 inet 192.168.9.1 netmask 0xfffffff8 broadcast 192.168.9.7 inet6 fe80::3eec:efff:febd:949%igb1 prefixlen 64 scopeid 0x4 media: Ethernet autoselect status: no carrier nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> igb2: flags=8802<BROADCAST,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=48120b8<VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,WOL_MAGIC,VLAN_HWFILTER,HWSTATS,MEXTPG> ether 3c:ec:ef:bd:09:4a media: Ethernet autoselect status: no carrier nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> igb3: flags=8802<BROADCAST,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=48120b8<VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,WOL_MAGIC,VLAN_HWFILTER,HWSTATS,MEXTPG> ether 3c:ec:ef:bd:09:4b media: Ethernet autoselect status: no carrier nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> igb4: flags=1008843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST,LOWER_UP> metric 0 mtu 1500 options=4e527bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,TSO4,TSO6,LRO,WOL_MAGIC,VLAN_HWFILTER,VLAN_HWTSO,RXCSUM_IPV6,TXCSUM_IPV6,HWSTATS,MEXTPG> ether 3c:ec:ef:be:04:b4 inet6 fe80::3eec:efff:febe:4b4%igb4 prefixlen 64 scopeid 0x7 media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> igb5: flags=1008943<UP,BROADCAST,RUNNING,PROMISC,SIMPLEX,MULTICAST,LOWER_UP> metric 0 mtu 1500 description: lan01 options=48120b8<VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,WOL_MAGIC,VLAN_HWFILTER,HWSTATS,MEXTPG> ether 3c:ec:ef:be:04:b5 inet 192.168.1.1 netmask 0xfffffff0 broadcast 192.168.1.15 inet6 fe80::3eec:efff:febe:4b5%igb5 prefixlen 64 scopeid 0x8 media: Ethernet autoselect (1000baseT <full-duplex>) status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> enc0: flags=0 metric 0 mtu 1536 options=0 groups: enc nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> lo0: flags=1008049<UP,LOOPBACK,RUNNING,MULTICAST,LOWER_UP> metric 0 mtu 16384 options=680003<RXCSUM,TXCSUM,LINKSTATE,RXCSUM_IPV6,TXCSUM_IPV6> inet 127.0.0.1 netmask 0x0 inet 10.10.10.1 netmask 0xffffffff inet6 ::1 prefixlen 128 inet6 fe80::1%lo0 prefixlen 64 scopeid 0xa groups: lo nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> -
So none of those interfaces.
The 1537 has a dedicated NIC for IPMI. Is that connected to the switch? I'd bet that's the MAC you're seeing.
By default we ship those with the IPMI isolated but it is possible to set it up to share a port. You should check that in the bios/ipmi setup.
-
That's right, this is also the MAC of the BNC.
That was also my first thought, that something was wrong there.
But I have checked the bios / settings several times and can confirm that only the static IPv4 is active.Okay, but if you can rule out the source of the error in the pfSense, thank you for looking.
-
@deleted Do you use this feature? If not just unplug it. But it does seem handy
For sure @stephenw10 would be the guy to help you with how to change it so it doesn't send that out, maybe if it shares a port?
I don't see any instruction on how to change IPv6 here
Or in the info with gui.. in the netgate manuals - but I did lookup manual from supermicro, and see this
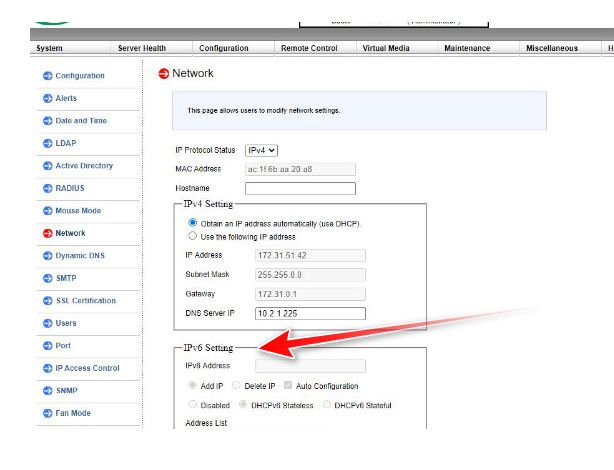
Are you saying you don't see anything for IPv6? Maybe some firmware just needs to be updated?
Other way to skin the cat would be to just not log the noise.. If you check that box to allow IPv6 then those block rules would not be created.. As long as you don't setup or allow IPv6 - its not going to do anything.. And if your still logging it with normal default log, you could create a specific rule not to log that traffic.
I mean the correct fix would be to disable IPv6 in the ipmi software.. But there are normally multiple ways to skin the cat.
Another option would be to turn off logging of default deny log, and then create your own rules to log what you want to see for deny. Not logging this traffic.
-
Just to be clear is the dedicated IPMI port actually connected to anything?
https://docs.netgate.com/pfsense/en/latest/solutions/xg-1537/io-ports.html#other-ports
If it's not then it pretty much has to be the shared port setting.
But, yes, either way you should be able to set the IPMI module to not use IPv6 at all as @johnpoz shows above.
-
Thank you for your efforts.
Yes, the function is good but not important for my scenario.
However, I have just checked again exactly where your arrow is in the menu. No IPv6 active.
And I can definitely confirm that it is the IPMI connection.
After I removed the cable, the entries stop.Then it can only be a bug in the bios. I have checked all settings several times and will look in this right.
Thanks again.
-
@deleted said in Unknown DHCP ping:
I have just checked again exactly where your arrow is in the menu. No IPv6 active.
It's specifically set to 'Disabled' there?
-
Everything that can be off is off.

Something doesn't fit. When I have the solution, I'll let you know.