Connect Another Firewall with its own LAN into Pfsense
-
Good day,
There's a bunch of scenarios I like to get some clarification on.
I have several public ip addresses.
public ip: X.X.X.25/29
usable ip: X.X.X.25-X.X.X.30My pfsense box has the public ip X.X.X.26 and an internal LAN of 172.x.x.1.
I have another firewall, Firewall B, that has its own LAN network of 192.x.x.
I want to preserve Firewall B LAN network.
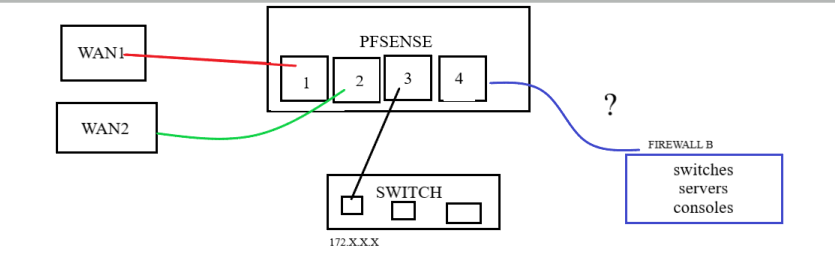
My pfsense has an empty port(4).
To set up the above scenario
-> Connect an ethernet cable from Firewall B into the empty port on pfsense
-> Pfsense -> Interface -> Add the interface (LAN2) -> Enable Interface
-> IPV4 Address: 192.168.1.0 -> Save-> Pfsense -> Rules -> LAN2 -> create rules that will allow traffic from other subnet, vpn tunnel to access this.
Scenario 2. If the above setup works then i am assuming a switch will work just fine.
- If i wanted to go the virtual ip route and give Firewall B its own public ip, after connecting Firewall B into Pfsense, will i have to configure the interface as a LAN interface (like above) and then just do port forwarding?
Thank you
-
@greatbush All that sounds right except you lost me at The VPN comment.
Can you just connect the other router to your ISP? If not yes you can port forward or 1:1 NAT.
-
@greatbush said in Connect Another Firewall with its own LAN into Pfsense:
-> Pfsense -> Rules -> LAN2 -> create rules that will allow traffic from other subnet,
'Firewall B' is probably actually a router with NAT capability. It may well outbound NAT the traffic from the subnet behind it. In that case pfSense would only see the traffic as coming from the LAN2 subnet and rules should be set to match that. But you may be able to disable the NAT in Firewall B.
You might also be able to bridge LAN2 to WAN (or WAN2) so that Firewall B gets a public IP to use directly. That's quite a bit more complex though.
-
@SteveITS No. The, the most import reason being budgets.
-
You can bridge or route with 1:1 NAT to preserve networks.
-
@greatbush You could just connect a switch in front of your firewalls. So that your /29 network goes into the switch and then each firewall can get their own public IP directly.
-
@stephenw10 Firewall B is an actual firewall like Meraki or Palo Alto
-
Then it will probably be NATing by default. You'll need to disable it if you want pfSense to see traffic from the subnet behind it.