Netgate 2100 VLAN confusion
-
Thanks for the suggestions.... No VLAN works. went back to my fresh Unifi AP-lite connected to TP-Link SG108E, connecting to Netgate SG4860. as fresh install with all components fresh "factory-restore". Did fresh config with two VLAN and works fine.
Did same test on a Proctli FW-2B vault,,, VLANs work fine.
Returned to configuring to my new SG2100 Netgate... no VLAN works. It must be something simple I'm not seeing. Could someone show me your config for 1 or 2 VLANS?Failed to mention.... on the TP-Link switch... Port1 = Unifi AP (VLANS 101; 201); Port 8 = uplink to Netgate switch port 1
Thanks for your patience. -
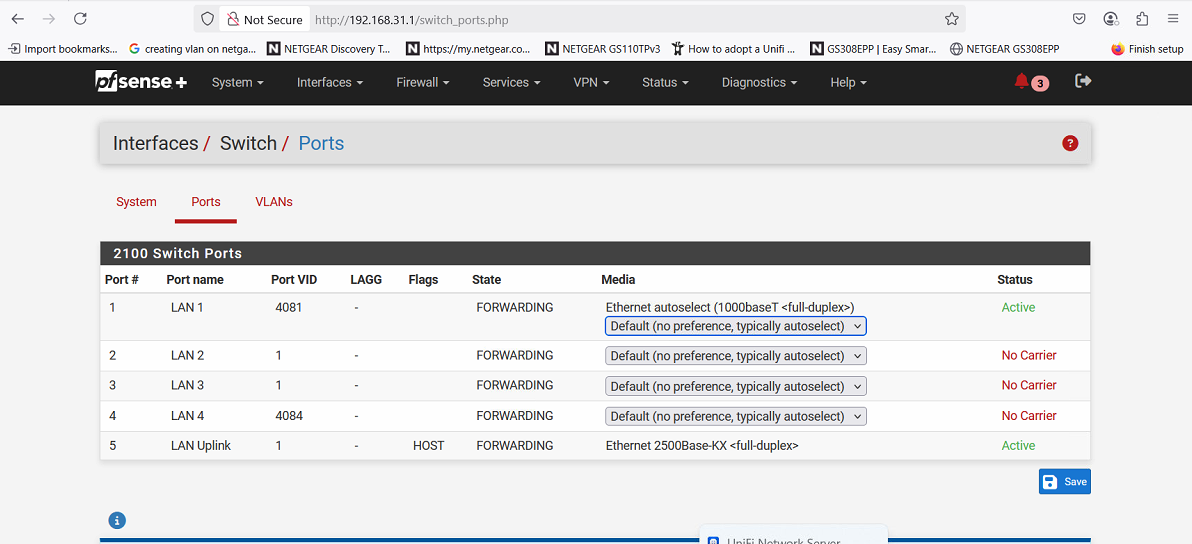
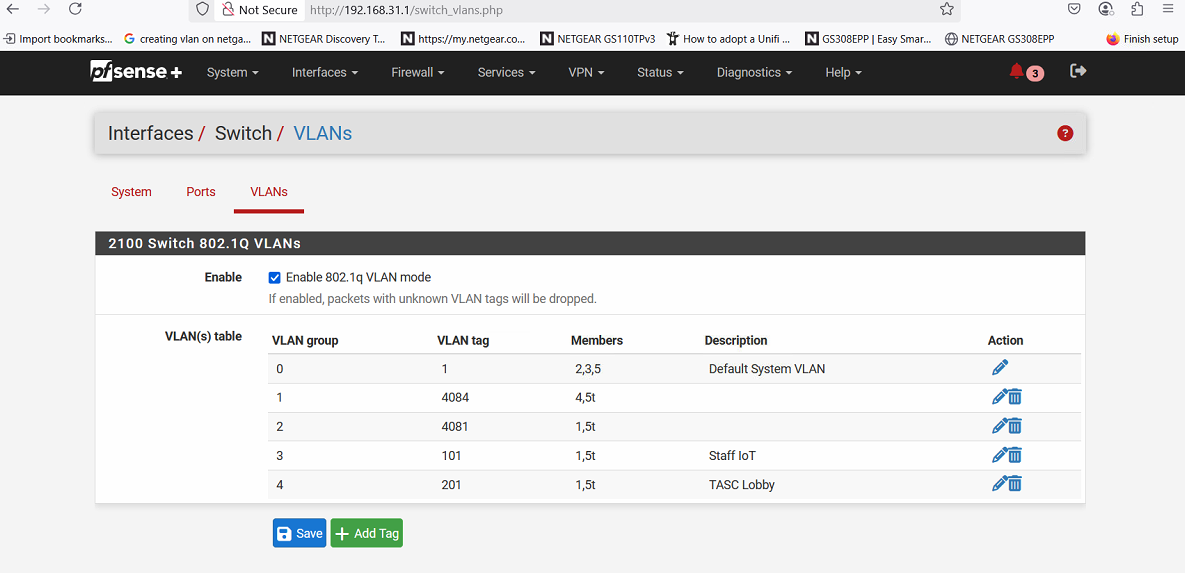
@detox one observation: In Interfaces / Switch / VLANs you have multiple VLAN groups (2,3 and 4) where port 1 is an untagged (native) member of. That can't be, one port can only have one native/access VLAN, the other VLANs have to be tagged.
For example:
- VLAN group 2, VLAN tag 4081, members: 1,5t
- VLAN group 3, VLAN tag 101, members: 1t,5t
- VLAN gropu 4, VLAN tag 201, members, 1t,5t
In that example configuration port one's native (Unifi naming, 'access port' in Cisco naming) is 4081 and VLAN 101 and VLAN 201 are tagged on port 1, making port 1 a trunk port.
-
What you were doing initially should have worked. VLANs 101 and 201 were trunked out of port1. As long as the Netgear switch was configured to handle those VLANs and was connected to port 1 it should have worked.
-
oh, i thought your setup was working again? Did the network gods interfere again (= ?
i have this for vlans, mind you it's provisional but working
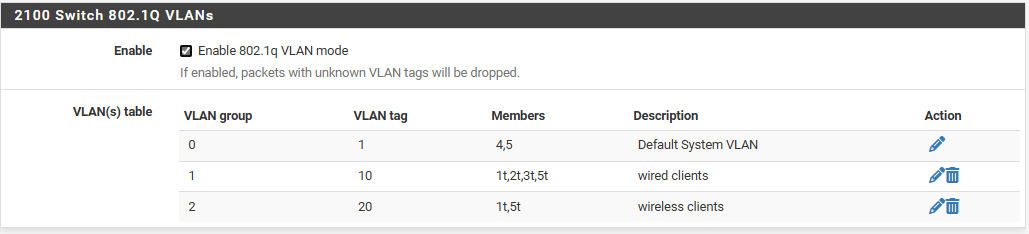
mind you, i have pfsense setup a dhcp server for each vlan so the clients get their appropriate ips -
@stephenw10 Am setting the Netgate2100 back to factory again and try again... One question that came to mind.... On the Interface/switch/VLANS page where the check box for Enable 802.1q is... when I set that... do I need to to add in the system default VLANS (4081/82/82/84)? I really do not need 4 separate ports, I will only be using port 1 as my connection to web. All ports for appliances will be handled by my TP-link / Netgear switch. This will be configured (as example)
port 1 = unifi AP
port 2-6 as untagged ports for printer, pc. etc connected to native VLAN (main network) and to IoT / Guest if a hard connection would be needed
Port 7 for untagged maintenance connection to firewall (maybe)
port 8 = Trunk/uplink to PfSense 2100 socket 1Thanks
-
No you don't need to add anything when you enable dot1q mode. It sets the switch VLAN aware but passes untagged to all ports by default.
-
OK reset to default. first thing I did was flip the switch for 802.1q.
So my next step is to +Add TagVLAN tag = 101
Description = Staff IoT
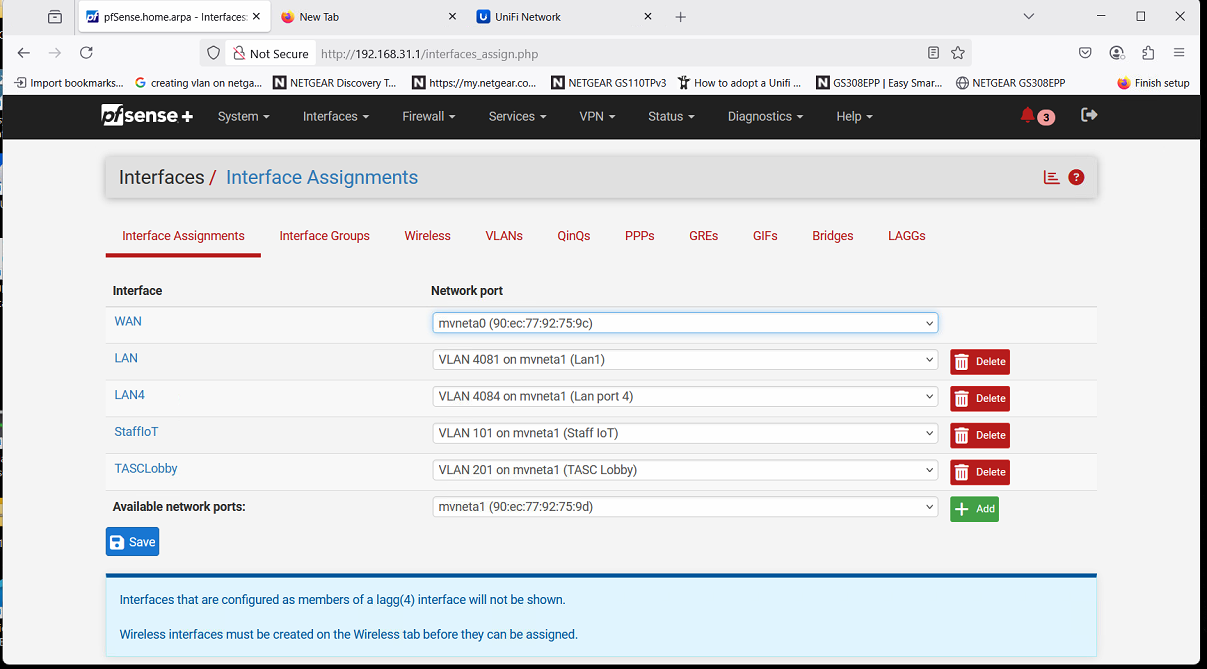
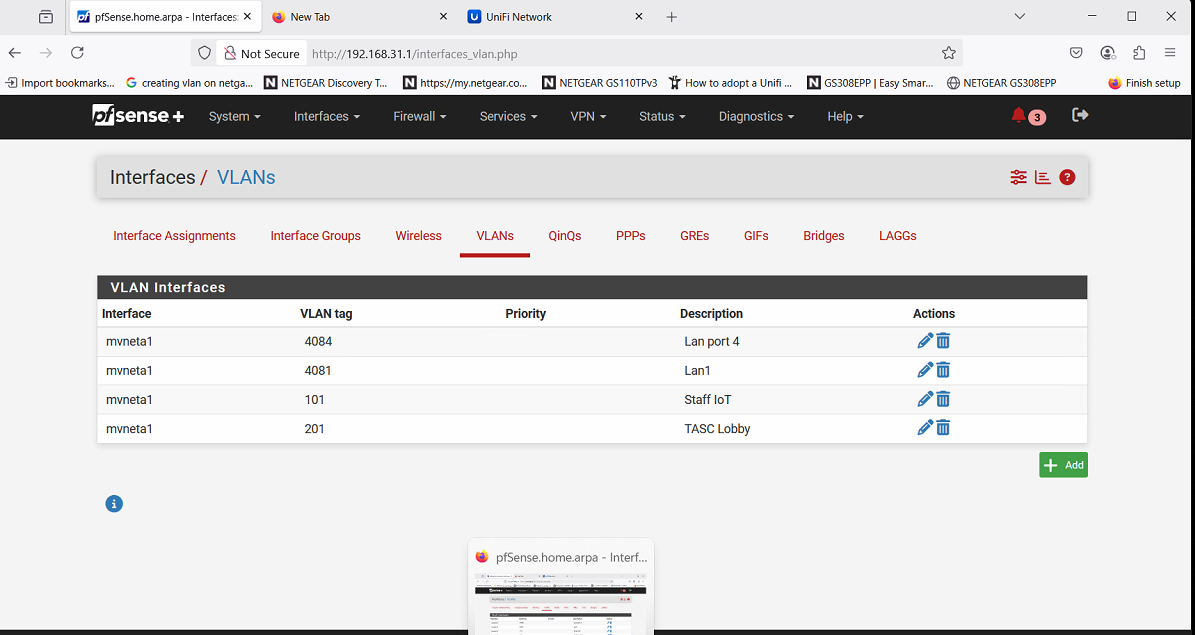
Members = 1t (switch port on Netgate) and 5t (LAN Uplink)THEN... got Interfaces / assignments / VLANS
create VLAN101 as normal
Back to Interface assignment page,,, select VLANS.. enable on port (lan) 1 mvneta1Sorry for the repetition,,,, hoping this works but if not, someone may see my mistake
and.... I do not touch settings on VLAN 1 correct?
-
@stephenw10 I think it is time for a Happy Dance!
Do not know what I did differently, but, under you sage wisdom and tutelage, it is working!!!Now I will save config and start on firewall rules.
Question regarding this..... currently with the only rule being "all pass" I can ping to each net.... 192.168.101 / 201.1
On the Interfaces / Switch / VLAN is shows VLAN 1 with all ports as members of
"Default System VLAN"To prevent hopping from one LAN to another, just create an alias blocking all 'other' networks instead of removing members from Default VLAN?
Thanks again for your help!!
-
You don't need to worry about VLAN1 there, traffic on that is already isolated from the other VLANs.
It's better to pass only what you need to rather than block a big list of things. But either way will work.
-
@b3rt Re-reading your responses and saw the ports being used in the photo... just wanted to confirm what I am seeing..............
VLAN 20 = ports used are 1 and 5, both tagged,, maybe port 1 is AP and port 5 is uplink?VLAN 10 = ports 1;2;3;5 all tagged using static IP? maybe printer, NAS etc? port 5 is uplink?
VLAN 1 = ports 4, 5 port 4 for maintenance laptop and 5 uplink?
If I am correct, then this shows I can remove all ports on Native VLAN except for uplink / Trunk (port 5)?