Logging my daily changing WAN-address
-
@stephenw10 said in [somewhat solved] Easy solution for logging my daily changing WAN-address:
You could create a patch that adds that line to rc.newwanip and set it to auto-apply.
Yes that would be an option!
But now I found a new "problem": Snort cannot handle the pppoe0 interface (with if_pppoe) and exits with this error:
"FATAL ERROR: Cannot decode data link type 51"
so there is more work to do I switched back to "mpd" because i need Snort working ...
I switched back to "mpd" because i need Snort working ... 
-
Hmm, using in-line mode?
-
@stephenw10 said in [somewhat solved] Easy solution for logging my daily changing WAN-address:
Hmm, using in-line mode?
No, legacy mode ...
-
OK digging....
-
@stephenw10 said in [somewhat solved] Easy solution for logging my daily changing WAN-address:
OK digging....
I have post a question also in IDS/IPS adressed to Bill Meeks
-
Yup replicated it here. Digging deeper...
-
@stephenw10 said in Logging my daily changing WAN-address:
Yup replicated it here. Digging deeper...
The problem is within the Snort binary package. The new
if_pppoedriver apparently returns a datalink type of DLT_PPP_ETHER (which is integer code '51'). But the Snort C source code is only looking for DLT_PPP (which is integer code '9'). Because the switch...case logic does not match on DLT_PPP_ETHER, thedefaultstatement at line 3257 prevails and Snort executes a fatal error and terminates.The code in question is within snort.c beginning at line 3118. Here is the module source code:
/* * Function: SetPktProcessor() * * Purpose: Set root decoder based on datalink */ // TBD add GetDecoder(dlt) to decode module and hide all // protocol decoder functions. static int SetPktProcessor(void) { const char* slink = NULL; const char* extra = NULL; int dlt = DAQ_GetBaseProtocol(); switch ( dlt ) { case DLT_EN10MB: slink = "Ethernet"; grinder = DecodeEthPkt; break; #ifdef DLT_LOOP case DLT_LOOP: #endif case DLT_NULL: /* loopback and stuff.. you wouldn't perform intrusion detection * on it, but it's ok for testing. */ slink = "LoopBack"; extra = "Data link layer header parsing for this network type " "isn't implemented yet"; grinder = DecodeNullPkt; break; case DLT_RAW: case DLT_IPV4: slink = "Raw IP4"; extra = "There's no second layer header available for this datalink"; grinder = DecodeRawPkt; break; case DLT_IPV6: slink = "Raw IP6"; extra = "There's no second layer header available for this datalink"; grinder = DecodeRawPkt6; break; #ifdef DLT_I4L_IP case DLT_I4L_IP: slink = "I4L-ip"; grinder = DecodeEthPkt; break; #endif #ifndef NO_NON_ETHER_DECODER #ifdef DLT_I4L_CISCOHDLC case DLT_I4L_CISCOHDLC: slink = "I4L-cisco-h"; grinder = DecodeI4LCiscoIPPkt; break; #endif case DLT_PPP: slink = "PPP"; extra = "Second layer header parsing for this datalink " "isn't implemented yet"; grinder = DecodePppPkt; break; #ifdef DLT_I4L_RAWIP case DLT_I4L_RAWIP: // you need the I4L modified version of libpcap to get this stuff // working slink = "I4L-rawip"; grinder = DecodeI4LRawIPPkt; break; #endif #ifdef DLT_IEEE802_11 case DLT_IEEE802_11: slink = "IEEE 802.11"; grinder = DecodeIEEE80211Pkt; break; #endif #ifdef DLT_ENC case DLT_ENC: slink = "Encapsulated data"; grinder = DecodeEncPkt; break; #else case 13: #endif /* DLT_ENC */ case DLT_IEEE802: slink = "Token Ring"; grinder = DecodeTRPkt; break; case DLT_FDDI: slink = "FDDI"; grinder = DecodeFDDIPkt; break; #ifdef DLT_CHDLC case DLT_CHDLC: slink = "Cisco HDLC"; grinder = DecodeChdlcPkt; break; #endif case DLT_SLIP: slink = "SLIP"; extra = "Second layer header parsing for this datalink " "isn't implemented yet\n"; grinder = DecodeSlipPkt; break; #ifdef DLT_PPP_SERIAL case DLT_PPP_SERIAL: /* PPP with full HDLC header*/ slink = "PPP Serial"; extra = "Second layer header parsing for this datalink " " isn't implemented yet"; grinder = DecodePppSerialPkt; break; #endif #ifdef DLT_LINUX_SLL case DLT_LINUX_SLL: slink = "Linux SLL"; grinder = DecodeLinuxSLLPkt; break; #endif #ifdef DLT_PFLOG case DLT_PFLOG: slink = "OpenBSD PF log"; grinder = DecodePflog; break; #endif #ifdef DLT_OLDPFLOG case DLT_OLDPFLOG: slink = "Old OpenBSD PF log"; grinder = DecodeOldPflog; break; #endif #endif // NO_NON_ETHER_DECODER default: /* oops, don't know how to handle this one */ FatalError("Cannot decode data link type %d\n", dlt); break; } if ( !ScReadMode() || ScPcapShow() ) { LogMessage("Decoding %s\n", slink); } if (extra && ScOutputDataLink()) { LogMessage("%s\n", extra); snort_conf->output_flags &= ~OUTPUT_FLAG__SHOW_DATA_LINK; } #ifdef ACTIVE_RESPONSE Encode_Init(); #endif return 0; }The fix might be as simple as adding this additional code to the switch...case test, but that assumes the raw PPP data is exactly same between the old
mpddriver and the newif_pppoedriver:case DLT_PPP_ETHER: slink = "PPP"; extra = "Second layer header parsing for this datalink " "isn't implemented yet"; grinder = DecodePppPkt; break; -
 B bmeeks referenced this topic on
B bmeeks referenced this topic on
-
Yup, that's exactly what we thought. Just waiting for a build to test....
-
Opened a bug to track: https://redmine.pfsense.org/issues/16229
-
@stephenw10 said in Logging my daily changing WAN-address:
Yup, that's exactly what we thought. Just waiting for a build to test....
Note that Suricata likely has the same issue. See my comment in this thread for the relevant section of source code: https://forum.netgate.com/topic/197701/error-on-snort-with-if_pppoe/8.
-
I see this issue still exists in Suricata on 25.07.1 - the redmine bug ticket has been open 3 months, but doesn't look like there has been any action on it.
On Suricata, if you leave the service running against an if_pppoe interface, it will continuously log "Error: pcap: datalink type 51 not yet supported" into suricata.log for the PPPoE interface and eventually fill the disk (if not caught).
-
@Bob.Dig said in Logging my daily changing WAN-address:
Is there a package where I can log only my dynamic IP-address on WAN?
I can't test this because I'm static - but I think if you simply want to log the IP changing on the WAN, a script and a cron job might do the trick --
hopefully there are no typos
you need to change "/path/to" to some appropriate directory ( perhaps something in var/log)
you need to change usewebinterfacehere" to the name of your WAN interface, you can get that from ifconfig (em0, mvneta0, or whatever it is on your system)call the script whatever you like. mywanwatcher.sh find a suitable directory for it
make it executable, schedule it with cron at some reasonable interval (every 5 minutes)You might need to add a rotation if the file grows to big or simply off load it and start a new one every 1000 lines or so
# File to store the previous IP address PREVIOUS_IP_FILE="/path/to/previous_ip.txt" # Log file to record changes LOG_FILE="/path/to/ip_change_log.txt" # Specify the interface to check INTERFACE="usewebinterfacehere" # Get the current WAN IP address CURRENT_IP=$(ifconfig $INTERFACE | grep 'inet ' | awk '{print $2}') # Check if the previous IP file exists if [ -f "$PREVIOUS_IP_FILE" ]; then # Read the previous IP address PREVIOUS_IP=$(cat "$PREVIOUS_IP_FILE") # Compare the current IP with the previous IP if [ "$CURRENT_IP" != "$PREVIOUS_IP" ]; then echo "IP address has changed from $PREVIOUS_IP to $CURRENT_IP" # Log the change to the log file echo "$(date): IP address changed from $PREVIOUS_IP to $CURRENT_IP" >> "$LOG_FILE" # Update the previous IP file with the new IP echo "$CURRENT_IP" > "$PREVIOUS_IP_FILE" fi else # If the file does not exist, create it and store the current IP echo "$CURRENT_IP" > "$PREVIOUS_IP_FILE" fi -
@jrey (Bob) said in Logging my daily changing WAN-address:
Is there a package where I can log only my dynamic IP-address on WAN?
World's most simple solution : your mail box. This means you have the WAN IP thus a possible remote access possible where ever your are.
The setup :Set one up here :
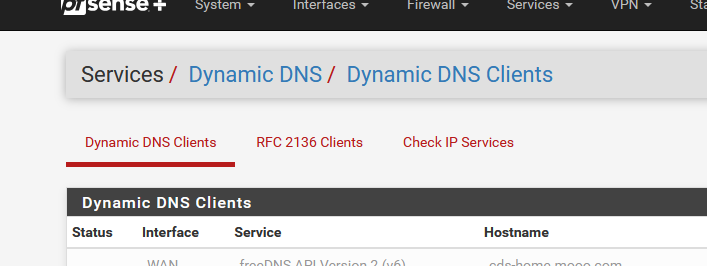
and set up this :
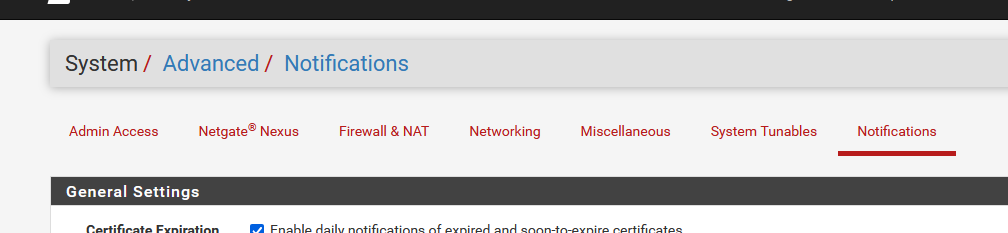
and done.
edit : no script, no maintenance.
-
revised
actually that first echo "IP address has changed .." you want to remove that line or the cron job will attempt to email the output and typically that emailing service is not available.and if you want to trim the file to when it hits 1000 lines something like this in that same if statement should do the trick .
revised sample so the previous IP file and log go to /var/log
commented out the echo (I don't have cron email configured)
and added a trim the file back to the last 10 lines when it hits 1000 line# File to store the previous IP address PREVIOUS_IP_FILE="/var/log/previous_ip.txt" # Log file to record changes LOG_FILE="/var/log/ip_change_log.txt" # Specify the interface to check INTERFACE="usewaninterfacehere" # Get the current WAN IP address CURRENT_IP=$(ifconfig $INTERFACE | grep 'inet ' | awk '{print $2}') # Check if the previous IP file exists if [ -f "$PREVIOUS_IP_FILE" ]; then # Read the previous IP address PREVIOUS_IP=$(cat "$PREVIOUS_IP_FILE") # Compare the current IP with the previous IP if [ "$CURRENT_IP" != "$PREVIOUS_IP" ]; then # uncomment the following line if your cron is configured to email job output # echo "IP address has changed from $PREVIOUS_IP to $CURRENT_IP" # Log the change to the log file echo "$(date): IP address changed from $PREVIOUS_IP to $CURRENT_IP" >> "$LOG_FILE" # Update the previous IP file with the new IP echo "$CURRENT_IP" > "$PREVIOUS_IP_FILE" # Check the number of lines in the log file LINE_COUNT=$(wc -l < "$LOG_FILE") if [ "$LINE_COUNT" -ge 1000 ]; then # Trim the log file to keep only the last 10 lines tail -n 10 "$LOG_FILE" > "$LOG_FILE.tmp" && mv "$LOG_FILE.tmp" "$LOG_FILE" fi fi else # If the file does not exist, create it and store the current IP echo "$CURRENT_IP" > "$PREVIOUS_IP_FILE" fito test since I'm on a static IP I did the following
created the script in /usr/local/pkg
made it executable chmod 755 (whatever you called it). in my test I used mywanwatcher.sh
run the script confirmed the file "previous" file was created in /var/log
edit the "previous" Ip recorded there to simulate the IP would change
run the script again. log file created and tells me that
at the date/time IP address changed from xx to yyNo I'm not testing the 1000 line trimmer
just change the INTERFACE variable at the top - should be fine.
works as expect

-
@Gertjan said in Logging my daily changing WAN-address:
your mail box
A log or clutter of email are very different things. maybe Bob has some other use for the logged information other than just a notification?
The original request was "where I can log", and not "where I can get notified when"
At least now there is a choice and in fact nothing to say you could not do both.Personally if wanted this information logged I'd send it to syslog - on the other hand not sure what the reason for logging or notifying when the WAN changes would be in the first place. I'm on a static IP, but I'm sure Bob must have some reason for the "where can I log" request.
Do one, do both, do nothing, and at the end of the day - really up to Bob how to proceed with the various options presented. -
@Gertjan As explained before, I will get flooded with emails about some vpn gateway going down. I have those configured as failover and/or load-balancing and a lot of them.
-
@jrey said in Logging my daily changing WAN-address:
schedule it with cron at some reasonable interval (every 5 minutes)
Thanks jrey but this is no a slick as the old solution, which would be triggered only on a PPPoE reconnect.
Also I am not in need for solution anymore because I will change my setup shortly to have another router before pfSense (again) and with that, I get good "logging" from that (via email) and I don't need do do PPPoE on pfSense anymore. This has not to with anything talked about in this thread, it is just a "design" decision.

-
@Bob.Dig
No worries.