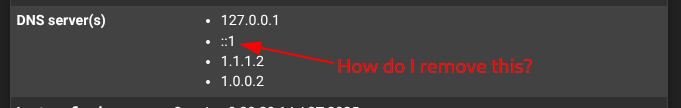
How can I remove this IPv6 DNS entry? (post 2.8.0 upgrade)
-
@Gertjan thanks! Interesting.
I tried to thumbs up but can’t. lol
2.7.2 that didn’t show up. That version didn’t need it? Or just didn’t show it?
I probably will edit the widget. Subtle changes like this bug me. It’s meaningless I’m sure but it was one of the few little changes I noticed post 2.8.0 upgrade.
I’m in the process of removing pfBlockerNG because when you disabled DNSBL (using quad9 instead) the pfBlockerNG widget has no option to hide it 🫤 you can uncheck it in services widget but not from the pfBlockerNG widget.
I asked here just to be sure I wasn’t missing a setting or something. Which is exceedingly likely for me. Ha
-
A (perhaps) cleaner way is to set the DNS behaviour to 'Use remote, ignore local'. Then add back 127.0.0.1 like:
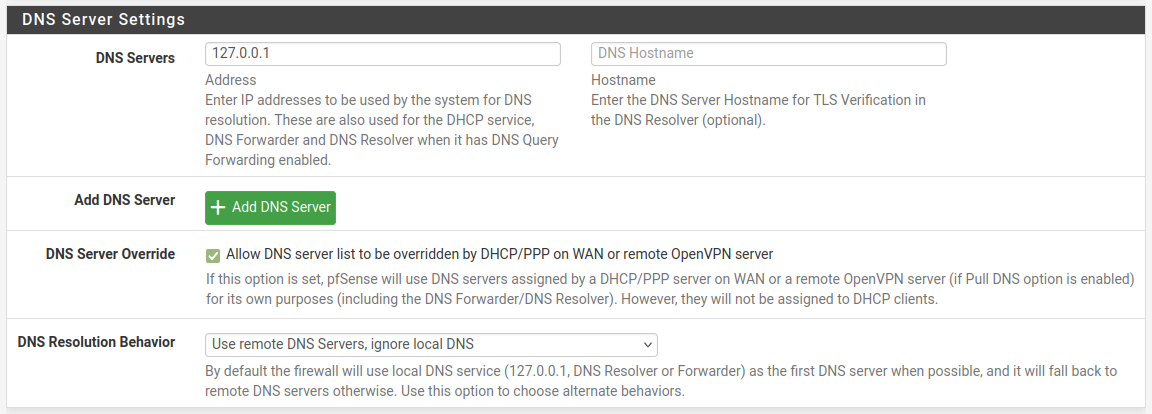
But remember to remove localhost there if you ever change back because it will throw an error trying to add it twice.
Or just ignore it since it's not a problem. It's just v6 localhost, the same as v4 localhost isn't a problem.
-
@hydn
Don't worry, I the stephenw10 for you ^^
the stephenw10 for you ^^
Way cleaner and better indeed. -
@stephenw10 ahh!! I see what you did there. Nice.
Will Unbound function the same by doing that? (Meaning local DNS first then out to Quad9 or whatever DNS servers I put in the rows/boxes below that 127.0.0.1?
-
You asked unbound to forward, right ?
If so, it will use the IPs it found in the /etc/resolv.conf file - these :
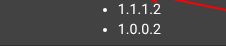
It won't forward to the listed 127.0.0.1 or ::1 as that would loop around indefinitely.
-
Hmm, good question. I believe it will use the servers in order they are set so as long as localhost is first that's what it should do.
But you could always just keep ::1 since it's meant to be there.

-
so the description here says:
(still current setting, my wife is streaming on TV, and if the network goes down one more time I'm pretty sure she'd divorce me.)I do have forwarding enabled:
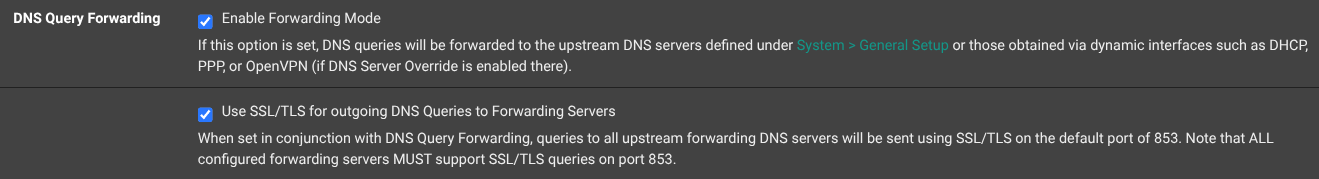
EDIT:
Question: What do I lose by removing the local DNS and disabling unbound and pointing DNS to the remote DNS provider servers? -
pfSense itself would just query the external server directly.
Clients behind pfSense would no longer have any DNS so you would need to pass the external servers to them directly via DHCP.
There would be no DoT. No caching. No filtering, if you're using that.
-
@stephenw10 said in How can I remove this IPv6 DNS entry? (post 2.8.0 upgrade):
so you would need to pass the external servers to them directly via DHCP.
The DNS entries I add in general settings are automatically populated in DHCP for each interface, is that not the case?
So if I remove unbound the DNS servers set here would not be used by the interfaces with DHCP?:
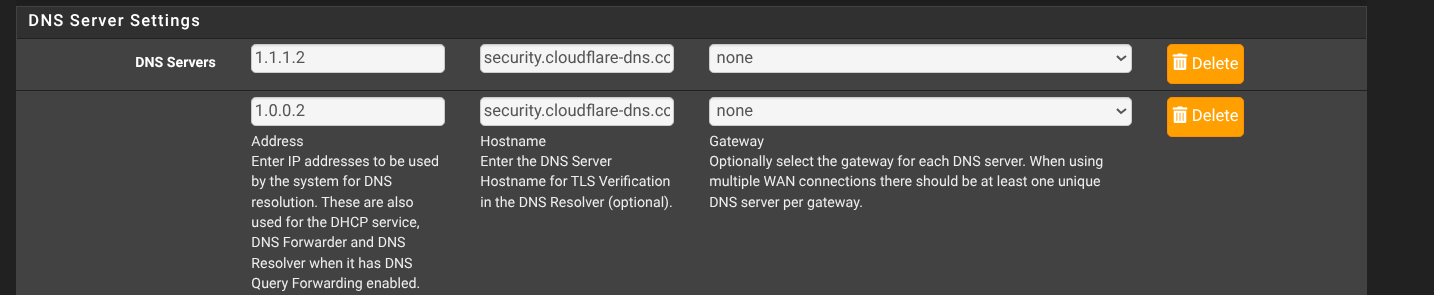
My issue is that DoT isn't working locally via 127.0.0.1 only via the remove DNS.
-
No. By default the DHCP server on each interface uses the interface IP as DNS to send to clients. That means using Unbound on pfSense. You can add servers manually to each DHCP instance if you need to.
@hydn said in How can I remove this IPv6 DNS entry? (post 2.8.0 upgrade):
My issue is that DoT isn't working locally via 127.0.0.1 only via the remove DNS.
DoT only works where it's configured and that's between Unbound and Cloudflare. You can enable DoT on Unbound itself as a server and clients could then use it to Unbound if they are configured to do so. And clients could potentially use DoT to clouldflare directly if they are configured to do it.
-
@stephenw10 Ok I understand. I enabled it between local clients but I get a warning on my iPhone when connecting to the hotspot about privacy.
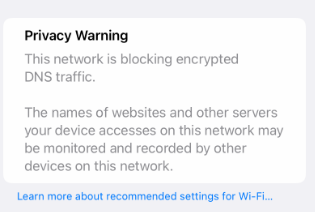
I can connect to it, and it works but just warns about privacy.
Edit:
 Edit: Also according to this it would mean DoT over 853 is indeed working?.
Edit: Also according to this it would mean DoT over 853 is indeed working?. -
Yes port 853 is DoT. You could also check the firewall states in Diag > States for that.
The iphone is probably trying to connect to some remote servers dircetly. Are you blocking external DNS for clients?
-
@stephenw10 yes you are correct. It was to their own 853 servers (apple’s pricate browsing feature). I’m not sure exactly what I changed but the warning is gone now.