VLAN Over VPN Works, But How to Handle DNS?
-
I’ve set up a ProtonVPN gateway group on my pfSense box and routed one of my VLANs through it. The gateway group includes two VPN interfaces, each set at a different tier (tier 1 and 2), and traffic from the VLAN is correctly routed through the VPN as expected.
What I’m trying to figure out now is how to handle DNS for that VLAN. Currently, the rest of my network uses Unbound, which listens on all interfaces and works fine in general. But for this VLAN, I’d like DNS queries to go through the VPN as well (ProtonVPN’s DNS servers).
I’m not entirely sure whether I need to disable Unbound for this VLAN altogether or if there’s a way to configure Unbound to forward DNS requests from this VLAN to the VPN’s DNS servers, instead of using the general DNS setup (which uses Quad9 DoT).
The goal is to have DNS traffic from this VLAN follow the same VPN path as the rest of the traffic going out through the tier 1 VPN gateway in the group.
I’ve spent days trying to understand the moving parts, any guidance or suggestions on how to achieve this setup would be really appreciated!
-
@iggybuddy6 The DNS settings used by clients are decided/configured on the client. The easiest way to get your clients to use the proton VPN DNS servers is to make sure they use DHCP and learn their DNS that way around.
Then on your DHCP server configuration settings in pfsense, override the DNS servers given to the clients on that specific VLAN. -
@keyser
Thanks for the answer.
When I tried to force the dns on the vlan (10.10.99.0/24) dhcp server the clients were unaware on how to route traffic to 10.2.1.1 or 10.2.2.1 (the 2 dns addresses on the 2 VPN interfaces).
Those routes are unknown. The fw rules create an abstraction for the traffic (the client doesn’t know its routed via vpn).. where clients need instead to be aware of vpn dns routes.
How would u achieve that exactly? -
@iggybuddy6 I’m not sure I understand how your setup is created/working then. How is your pfSense able to reach those DNS servers if it doesn’t know the route to them? If your pfSense know the route to them, your clients should as well if they use pfSense as the default gateway.
-
@keyser
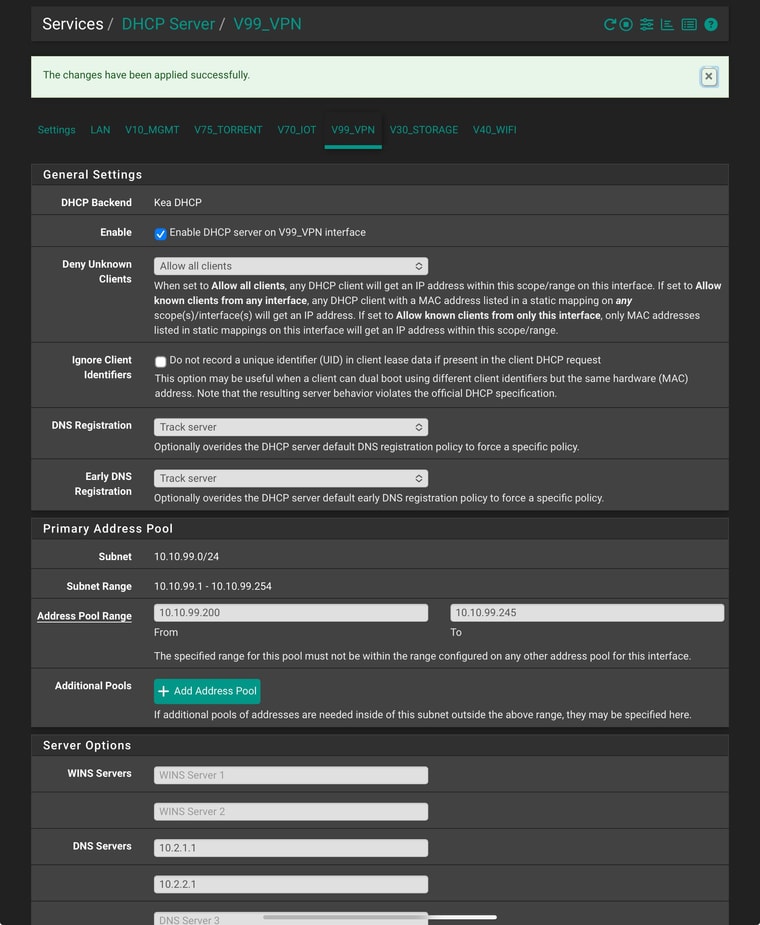
Thanks again for the reply. It was maybe a fw rules issue.V99_VPN uses the 2 VPN servers DNS.
I can now see the traefik client go over vpn dns and seems ok now.Does this look like a good setup to you?
I’m just learning pfsense. Thx a lot


-
@iggybuddy6 It seems to work as intended. I can’t really comment on the setup as I cannot see the whole picture. But I assume everything is as intended as you are also using the ProtonVPN endpoints as DNS servers.
-
@keyser thanks a lot

-
@iggybuddy6 I’m using a very similar setup with NordVPN. You can set the DNS on the DHCP interface settings .
However, that means DNSBL won’t see that traffic if you override. So what I did was leave them blank but then manually set the NordVPN DNS IPs on my TVs and other devices that I want to use the VPN DNS.
This way unbound still see the traffic and dnsbl blocks will work but the dnsleak test will show only the DNS you set manually on each device.
I’m always split between not using DNSBL at all VS using it. But today I’ve settled on keeping the DHCP DNS settings untouched and instead set the VPN DNS manually on each device. Because he VPN will still work even when not using nord’s DNS it’s just that the traffic isn’t hidden completely but the location set by your VPN, Miami, New York, etc will work exactly the same.
-
@hydn thx for the link outlining your setup. I will go through it.
For my use case I care more about privacy (having traffic and dns within the VPN) and I’m currently willing to give up the extra dnsbl checks. I plan to block/redirect anything else (sw/devices) trying to override the VPNs DNS. -
@keyser mmh now it’s not working again. I’m not sure if the issue is with NAT rules. I haven’t changed anything and nslookup go on timeout with state no traffic.


-
Whether you keep DNSBL or not remember that there is malware blocking available via Cloudflare DNS and Quad9. Check them out if you haven’t already. But of course you lose logging, privacy of doing it locally and pfblockers geoIP, category blocking etc.
It’s a lot to give up if you enjoy that data and control.
-
@hydn Appreciate the heads-up.
In general settings, I’m using Quad9 over DoT. The network uses the DNS Resolver with pfBlockerNG and DNSBL, listening on the network interface addresses. This all works fine.
What I’m now trying to do is to isolate part of the network by using a VLAN and route all its traffic—including DNS—exclusively through the VPN. From a privacy perspective having VPN traffic and DNS within the VPN seems to be the safest approach. I’m fine giving up some control and filtering provided by pfBlockerNG and popular public DNS.
I’m still not quite sure how to set this up properly. I tried configuring the VLAN’s DHCP server to hand out the VPN’s internal DNS IPs (10.2.1.1 and 10.2.2.1) for the 10.10.99.0/24 subnet. It looked like it was working earlier, but now DNS queries are timing out.
I have disabled DNS Resolver on the vlan 99 interface.
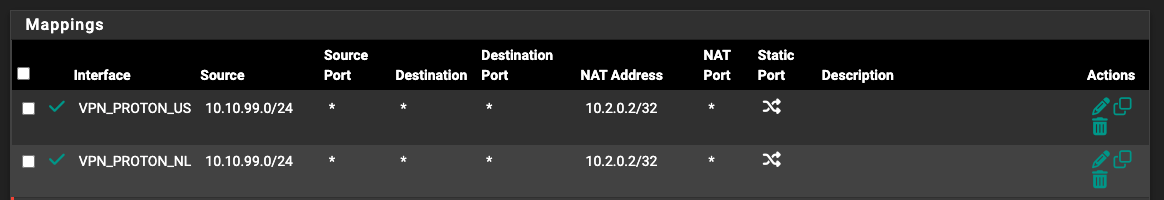
The 2 Gateway VPN IPs are used as dns servers on my host /etc/resolv.conf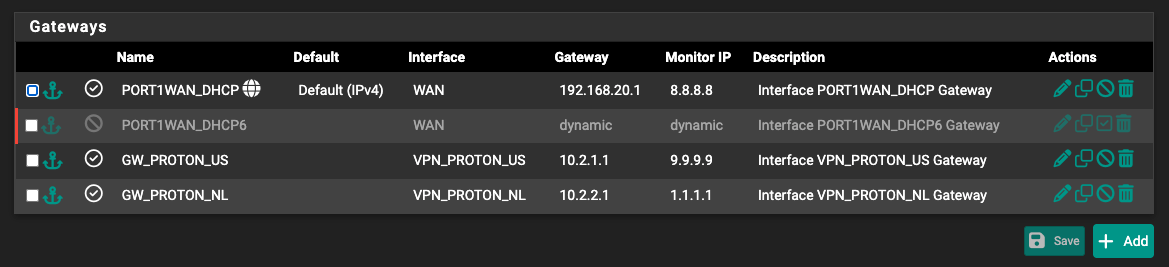
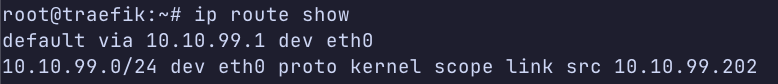
nslookup timeout
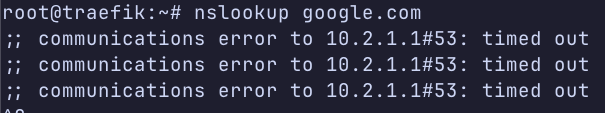
Traffic going out from VLAN to VPN DNS
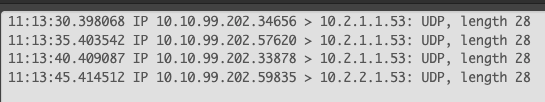
traffic seems coming back from the VPN (this is correct as I have 1:1 NAT on 10.2.0.2 to 10.2.1.1)
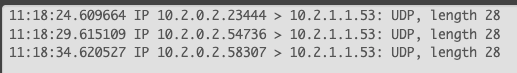
I suppose on the VLAN I should see traffic response coming in from 10.2.1.1 but I do not and that is why I see "timed out".
The nat seems to work I think. I am confused on why the DNS response is not properly routing back to the client
my 1:1 NAT

my outbound