Is is possible to set up pfSense with a VPN provider in this "toggleable" way?
-
@anallama guides from many vpn providers are shit - that is the technical term yes..
Many of them will say you need to use their dns, and will say you have to route everything through them and change your outbound nat to manual.. All of that is nonsense.. You don't need to do any of that..
Don't pull routes, don't use their dns, and just set hybrid outbound nat and set a nat to the vpn interface you're using to connect to them.
They may block trying to use any other dns then theirs through the connection, believe nord was intercepting dns - they prob still are..
But you sure and the hell do not need to route your dns through them or use theirs if you don't want to - have pfsense just use some dot server if you want your dns encrypted, etc.
-
@johnpoz said in Is is possible to set up pfSense with a VPN provider in this "toggleable" way?:
and just set hybrid outbound nat and set a nat to the vpn interface you're using to connect to them.
Can you direct me to the best place to read up on this part specifically?
-
@anallama already linked to policy routing section.
Here is example
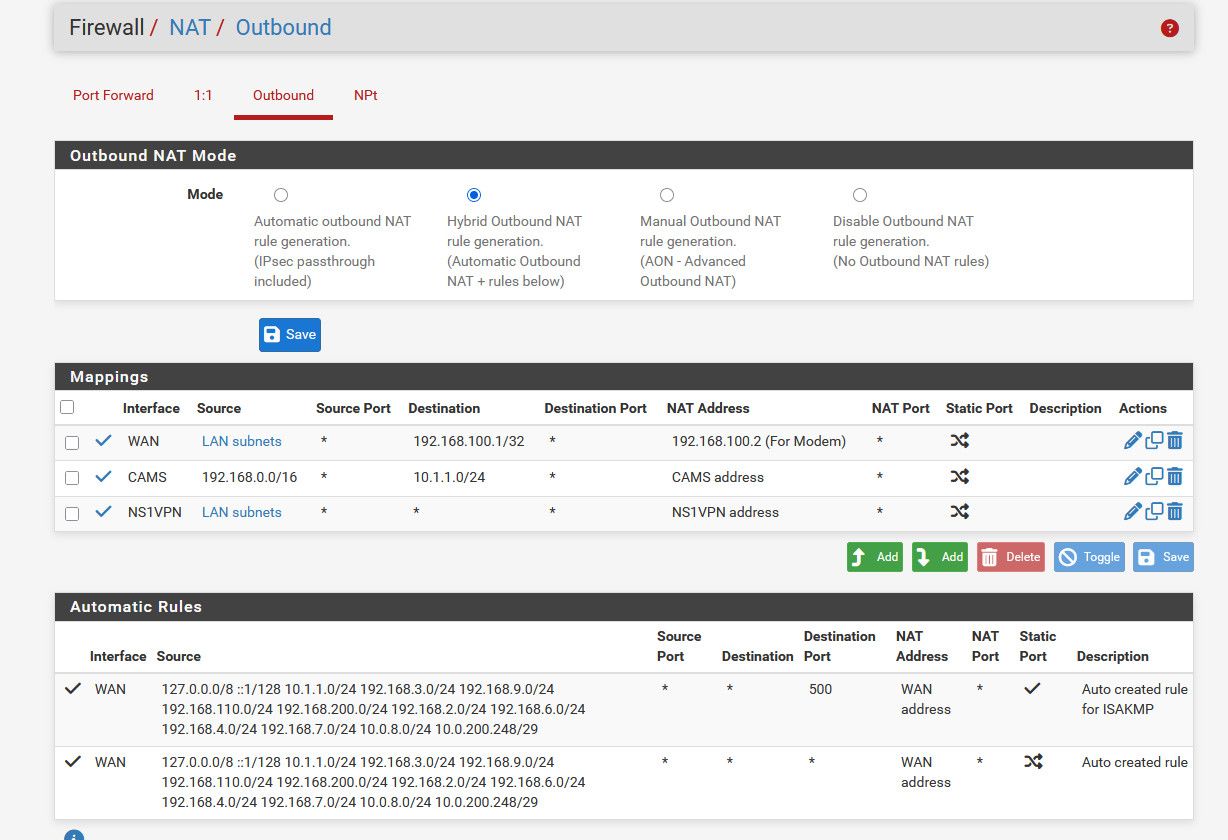
All of my normal networks are just auto - and nat to my normal wan address.. But I have a special nat, that if I route traffic out my vpn interface (ns1vpn) in my case it will nat to that address.
Clicky a policy route to send something out my vpn - it does so, toggle that rule off and now back to normal routing and just going out my normal wan.
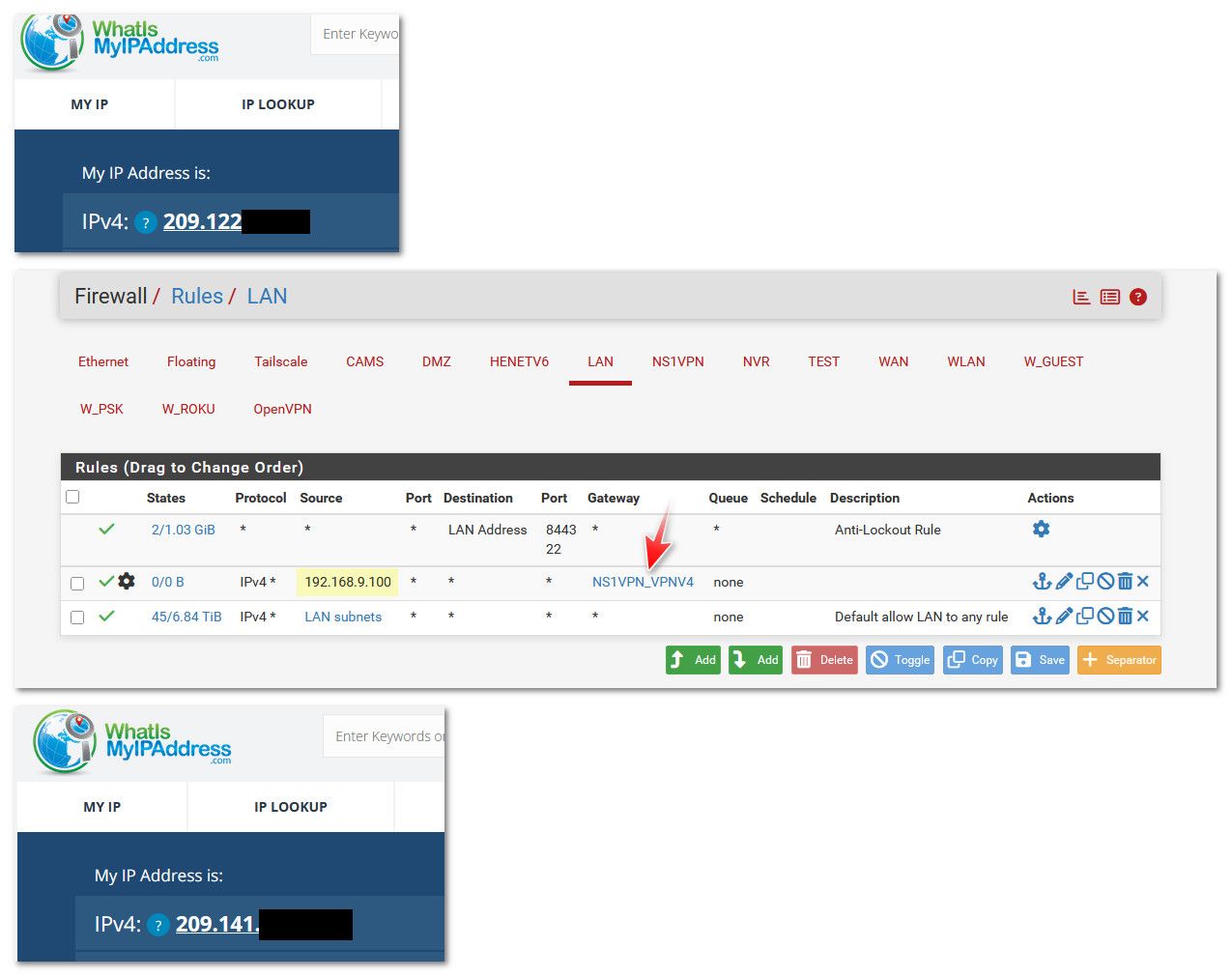
So as example - my normal IP 209.122.x.x out on the internet, then route it out my vpn and I am seen as my vpn exit IP 209.141.x.x.
-
In your last image, the 192.168.9.100 is the pfsense router address? Can I just select "WAN address" generally rather than specifying the exact IP?
-
I've got a successful handshake on Wireguard at least (sorry, I'm aware that I've placed this post under OpenVPN, Wireguard setup seems a lot simpler)
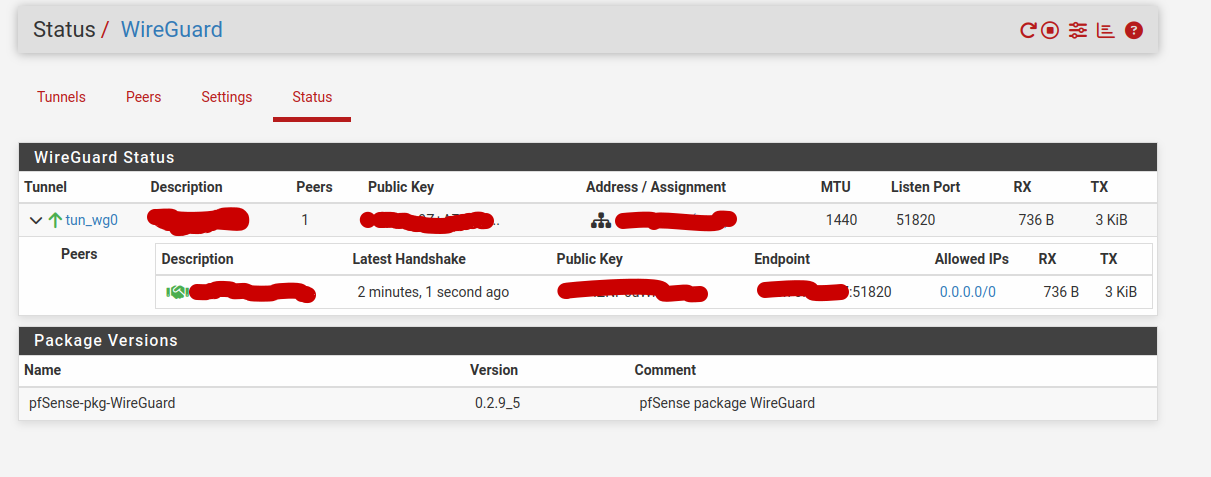
I'm not sure what the auto-created rules present on mine but missing from yours do.
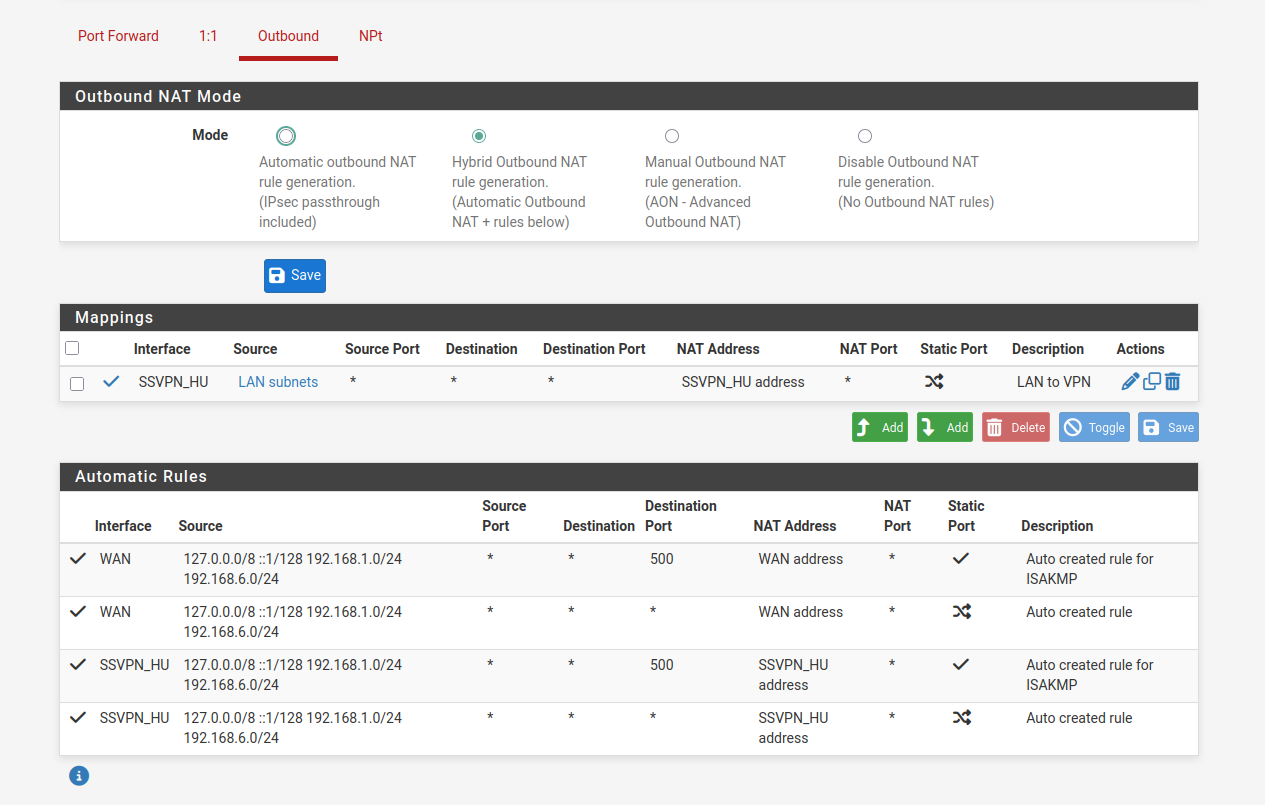
As soon as I enable this rule below, my internet connection stops working. Without it enabled, my IP remains listed as my ISP's.
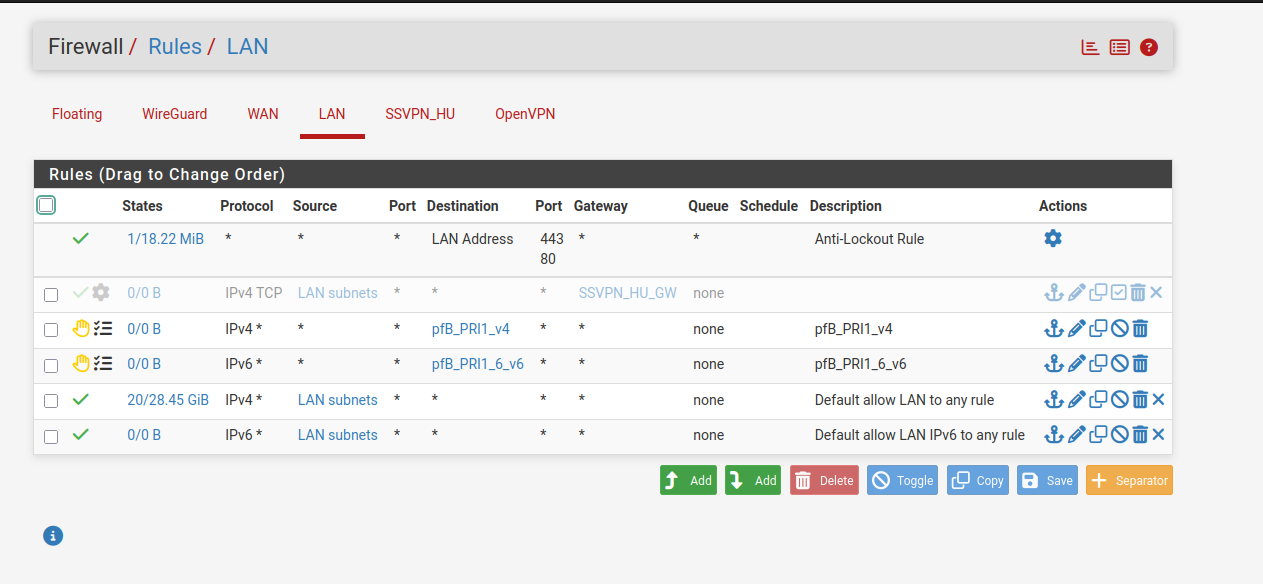
I currently have DoT set up with CIRA servers; I tried setting up the static gateway routing to the VPN endpoint (listed as optional in the documentation), but it did not change that my connection was down. Should I be leaving the default IPv4 gateway as Automatic?
-
@anallama no that is the IP address of the PC I wanted to policy route out that specific gateway - why would you think that is a pfsense IP.. How would pfsense IP be inbound source address into its own lan interface?
-
@johnpoz I'm pretty ignorant of just about everything in networking, that's all I can say
-
@anallama hahah - ok that explains it then ;)
Your default gateway in pfsense should be set to your your normal wan interface that you use for normal isp connectivity.
I use openvpn to connect as client to my vpn server, I haven't used wireguard.
-
@johnpoz alright I'll try and redo it in OpenVPN, and post my probable failures then

-
@johnpoz
Hey so I actually got this working via OpenVPN for my LAN network on the first try...every device in 192.168.1.0/24 now has the VPN provider's public IP. However, the remote access device connected through my OpenVPN Server (tunnel network 192.168.6.0/24) still has my local IP, even when I add equivalent NAT and firewall rules. What do I need to adjust to also send the remote access device through the VPN client? Do I just assign it an IP on the LAN network range instead?