unable to set NVA pfsense between subscriptions Hub and spoke toploy
-
Hello everyone I hope you can help me in this case. thanks
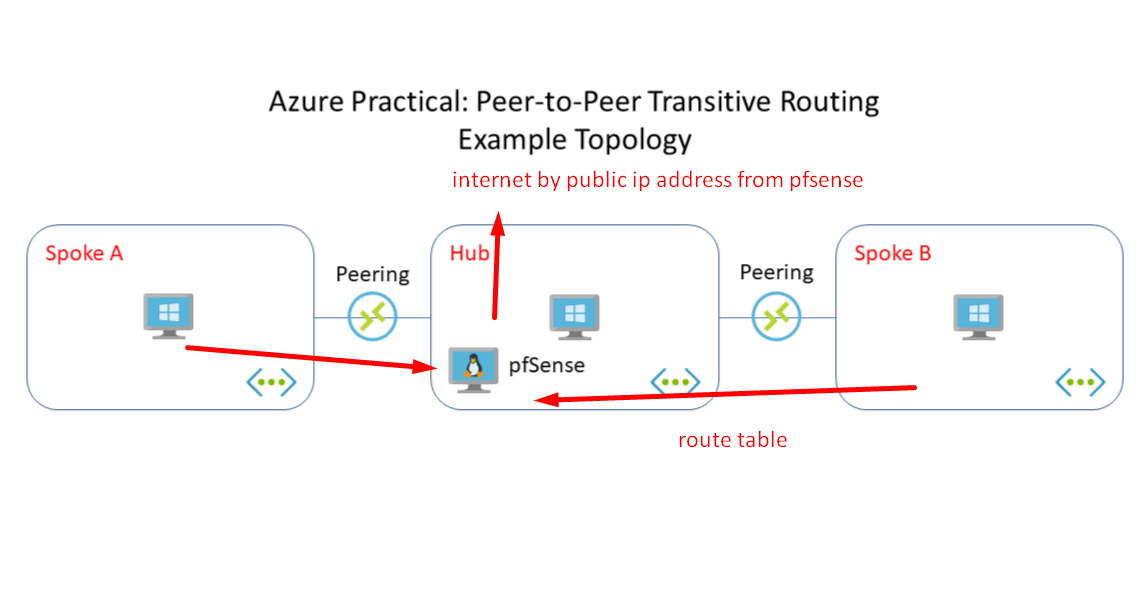
I have 3 subscriptions, I got them connected to hub from peering connection, that works properly I can communicate normally, so then I want to use a network virtual appliance from pfsense to establish internet connection from the hub to the spokes subscriptions vnets, basically I install pfsense plus from market place in azure into a subnet inside the vnet of the subscription of hub, I enable public IP to the same nic of the private ip that from the vm, I set forwarding on the nic too, then once is up in running with the suggest information of pfsense I get inside the GUI and I move forward to the setup of the application as default, finish the setup, then I move to the spokes vnets and configure the route using this configuration.
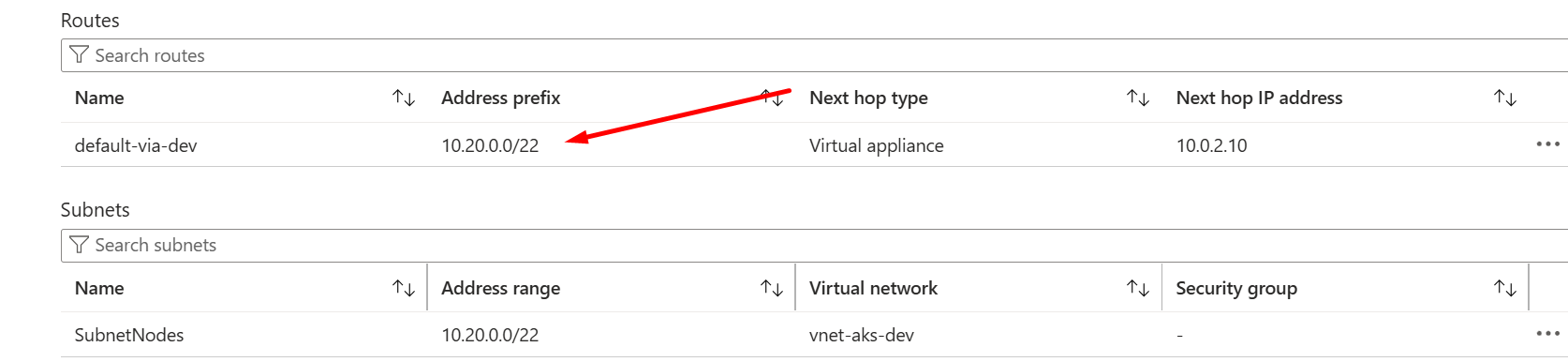
default-via-dev
0.0.0.0/0
Virtual appliance
10.0.2.10 {this ip is from the interface that use a internal ip to connect even if I set a public ip address}, and associate a subnet of the spoke vnet, later I create a vm inside that subnet of the vnet spokes but I'm unable to get access to internet. Can someone please help me to check what is missing on my configuration? thanks
-
Ok so this is all directly routed? No VPNs involved?
Are you NATing the spokeA and spokeB subnets out of the pfSense WAN? Did you add rules for that if so or static routes for auto-outbound NAT rules?
Check the state table in Diag > States when you try to connect out from one of the spokes. What states do you see created?
Did you enable IP Forwarding in Azure for the pfSense VM?
-
 S stephenw10 moved this topic from Problems Installing or Upgrading pfSense Software on
S stephenw10 moved this topic from Problems Installing or Upgrading pfSense Software on
-
@hdavila
Ok so this is all directly routed?
yes directly route it
No VPNs involved?
not there aren't
I just left the rules as default,
Are you NATing the spokeA and spokeB subnets out of the pfSense WAN?
that's is what I want to achieve, connect my vms from spokes thought the NVA from the hub subscription to get internet from the public ip . No gateways set....
Did you add rules for that if so or static routes for auto-outbound NAT rules?
none just default settings, this is my current configuration the only route table from spokeA, thats the internat ip, of the vm pfsense
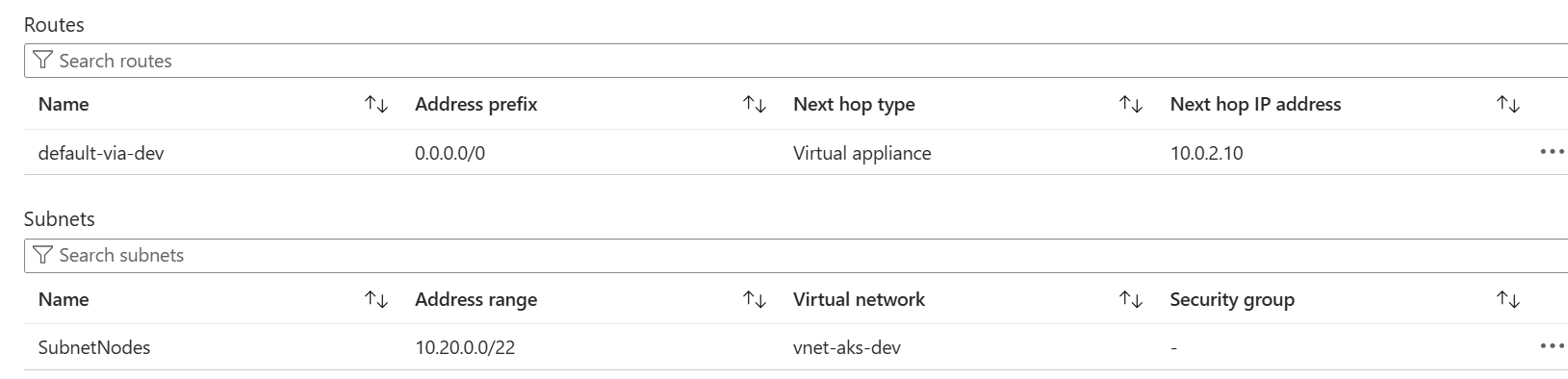
Check the state table in Diag > States when you try to connect out from one of the spokes. What states do you see created?
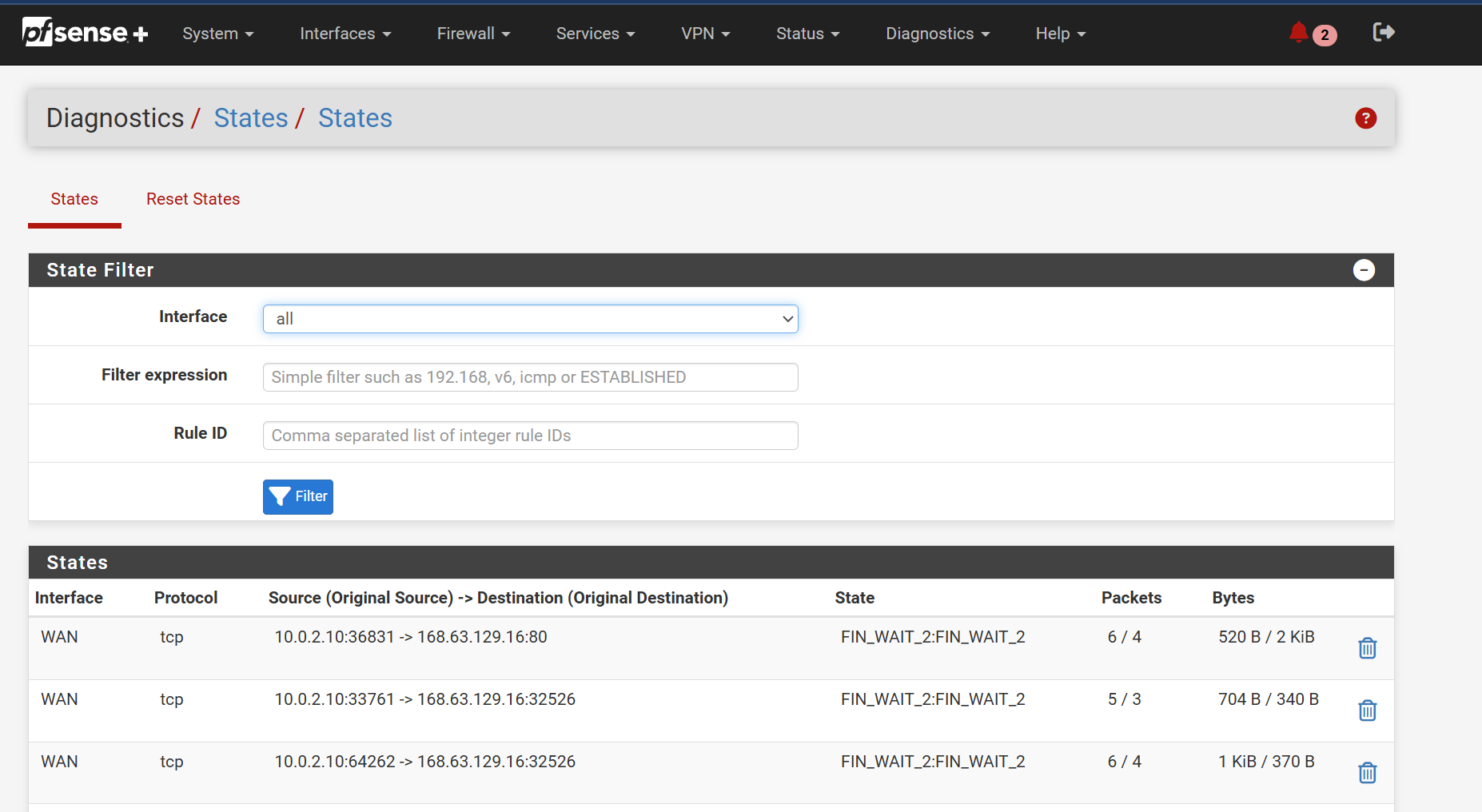
nothin from 10.20.0.0 my ip from test vm on spoke subnet is 10.20.4.4
azureuser@test-nva:~$ curl www.google.com
curl: (28) Failed to connect to www.google.com port 80 after 300581 ms: Timeout was reached
azureuser@test-nva:~$ ip route
default via 10.20.0.1 dev eth0 proto dhcp src 10.20.0.4 metric 100
10.20.0.0/22 dev eth0 proto kernel scope link src 10.20.0.4 metric 100
10.20.0.1 dev eth0 proto dhcp scope link src 10.20.0.4 metric 100
168.63.129.16 via 10.20.0.1 dev eth0 proto dhcp src 10.20.0.4 metric 100
169.254.169.254 via 10.20.0.1 dev eth0 proto dhcp src 10.20.0.4 metric 100
Did you enable IP Forwarding in Azure for the pfSense VM? yes
I have a few question, so when I create the vm it came with one nic should I create another one, is necesary ? the current one have a local and public ip.
and is with dhcp should I change to static ip address? should be something like thisInterface Type IP Address Role WAN Public IP (Azure-assigned) Outbound LAN Private IP Internal network Client gateway thanks for the the attention on this case.
-
OK you will need to add more firewall rules on the WAN to allow traffic from the other subnets if you only have one NIC there.
But I would add another NIC and route the traffic to that instead personally.
If you don't enable IP Forwarding in Azure it will just drop traffic that isn't to or from the VM IP directly. It can't route traffic from other subnets as you are trying to do here.
-
@stephenw10
Forwarding is enable, I setup another nic in the same vm but still not seeing the problem. with the new nic if I try to setup and local ip address I got this error
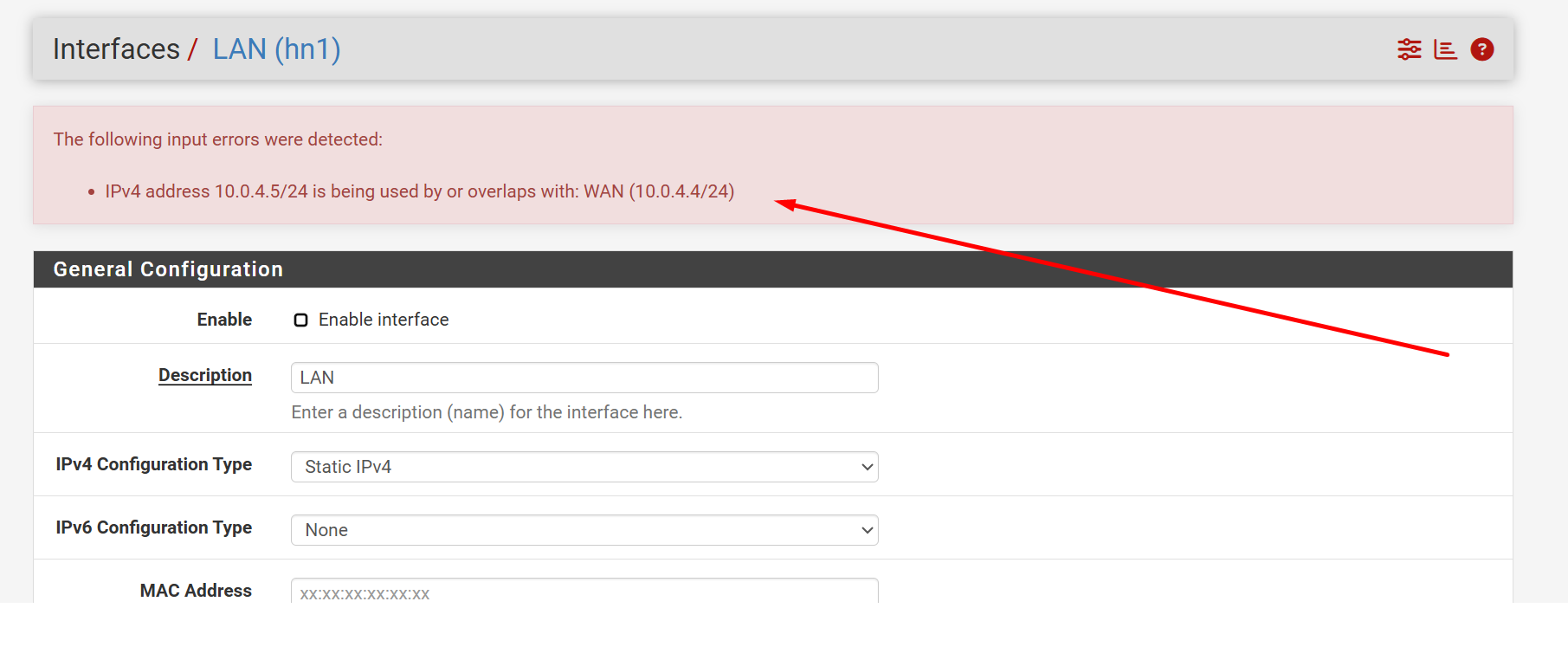
soo both are in dhcp,
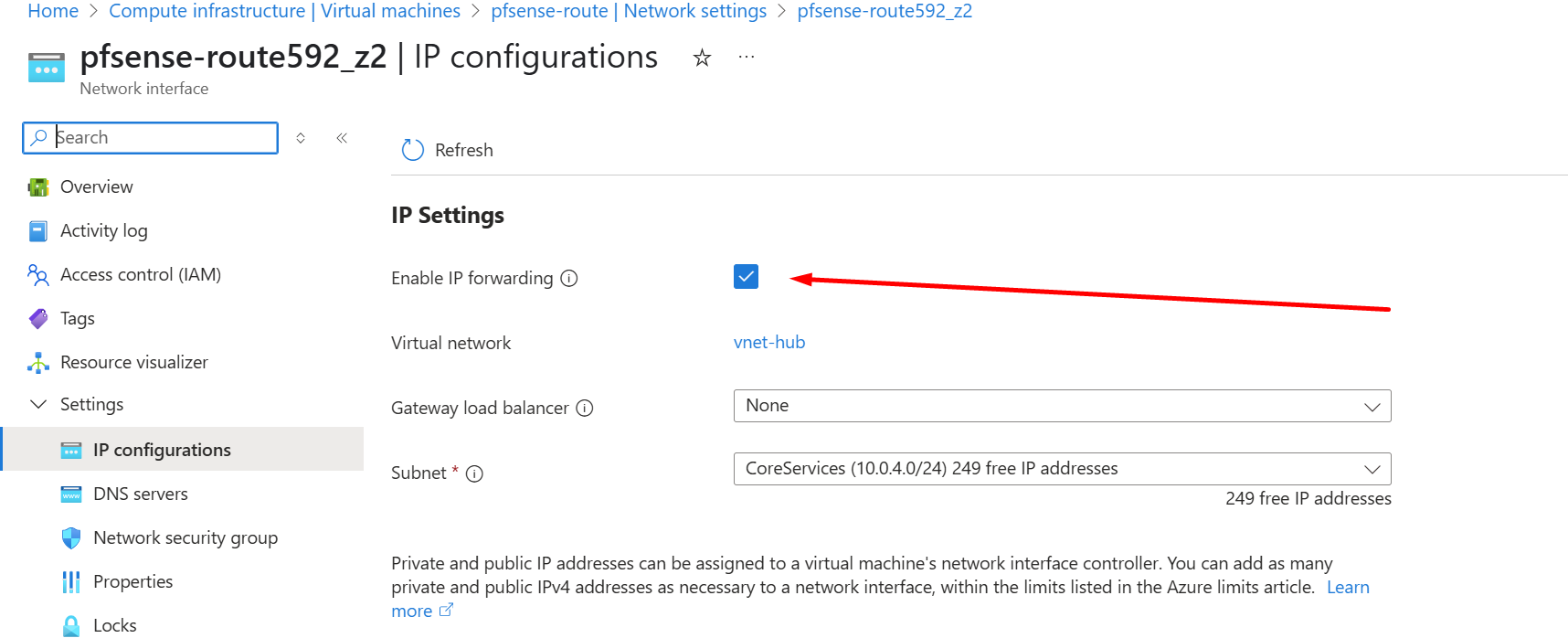
I add the subnet of the peering connection and the subnet of the spoke subscription
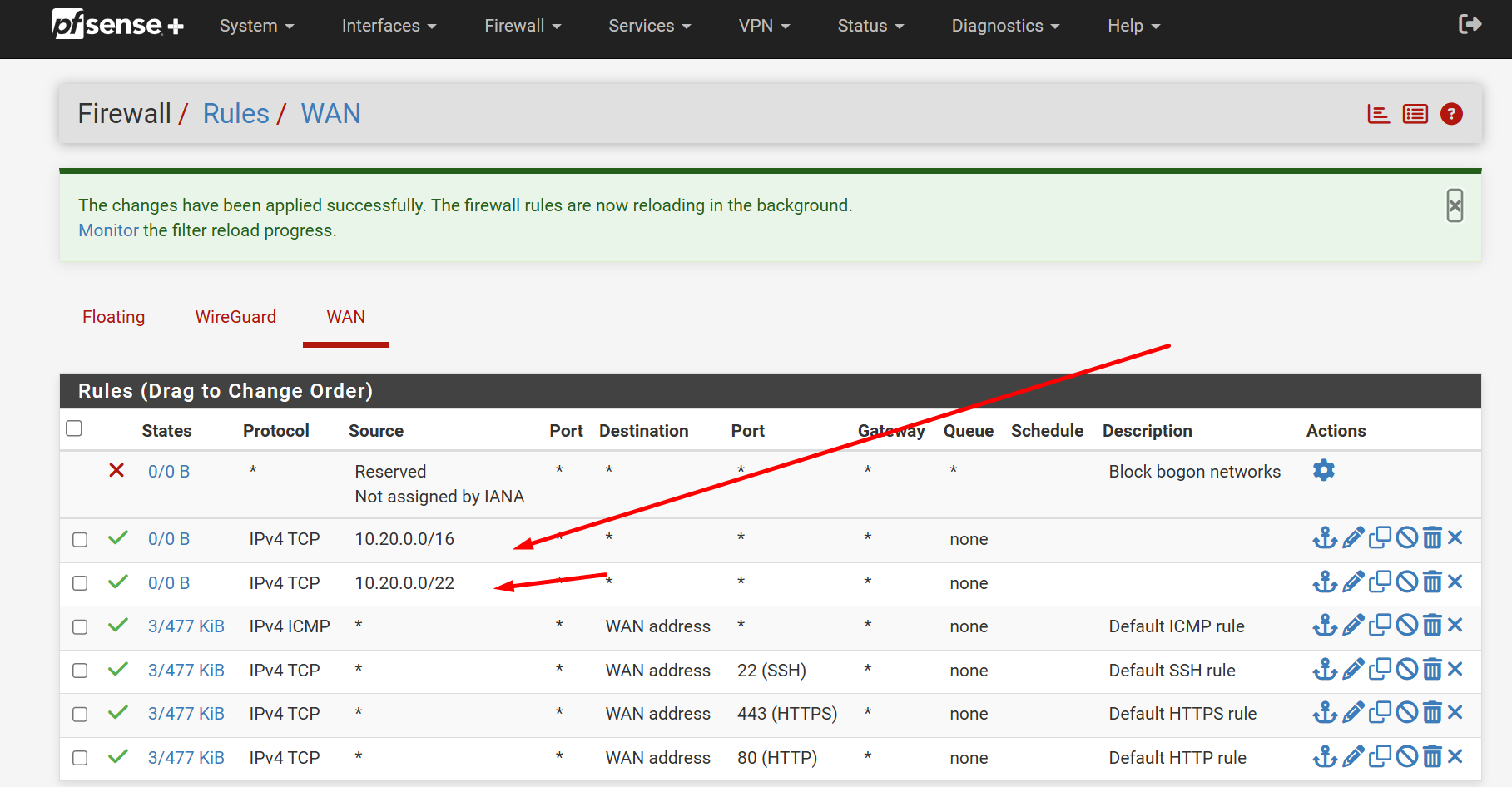
still not working, no internet in the vm or the spoke subscription. anything else that I can check? -
You need to add the new NIC in a different subnet from the WAN and the route traffic to that from the other locations. If you chose to use two NICs at least. Which I would.
Do you see any in coming traffic in the states yet? Or in a pcap on WAN?
-
@stephenw10 ok I got to solve the problem changing my source of the route table URD from 0.0.0.0/0 to my subnet from my spoke subscription 10.20.0.0 from that is working the test vm with internet. now I will test performance to connect a cluster ks8 from each spoke. thanks for the support .