Wireguard Site-to-site not passing traffic
-
Can I dump the config somehow or screen shots ?
Pinging the endpoints, I can ping from the remote to the main OK, but the main to remote does not ping.
So guessing something on my main setup. -
@MartynK said in Wireguard Site-to-site not passing traffic:
Can I dump the config somehow or screen shots ?
Screenshots is probably the best option.
Pinging the endpoints, I can ping from the remote to the main OK, but the main to remote does not ping
Okey, not ideal.
-
-
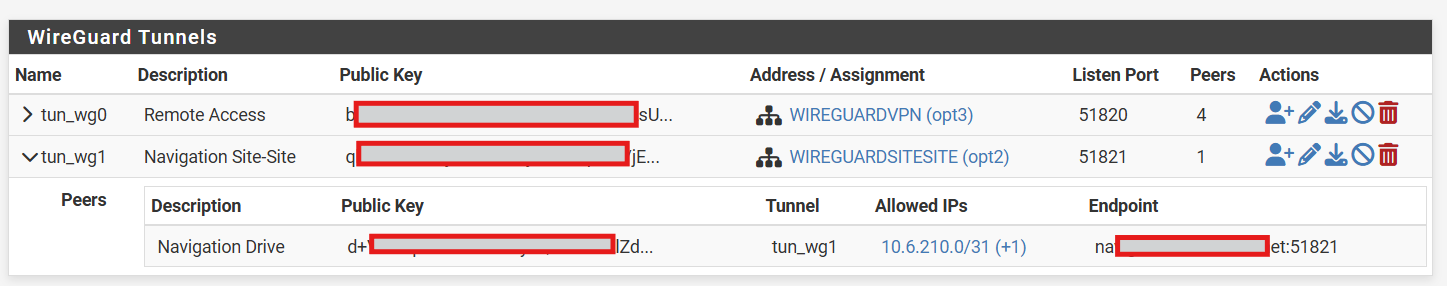
Remote Site
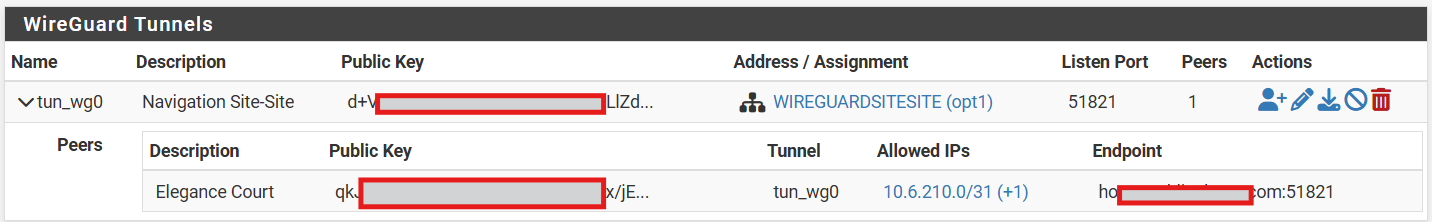
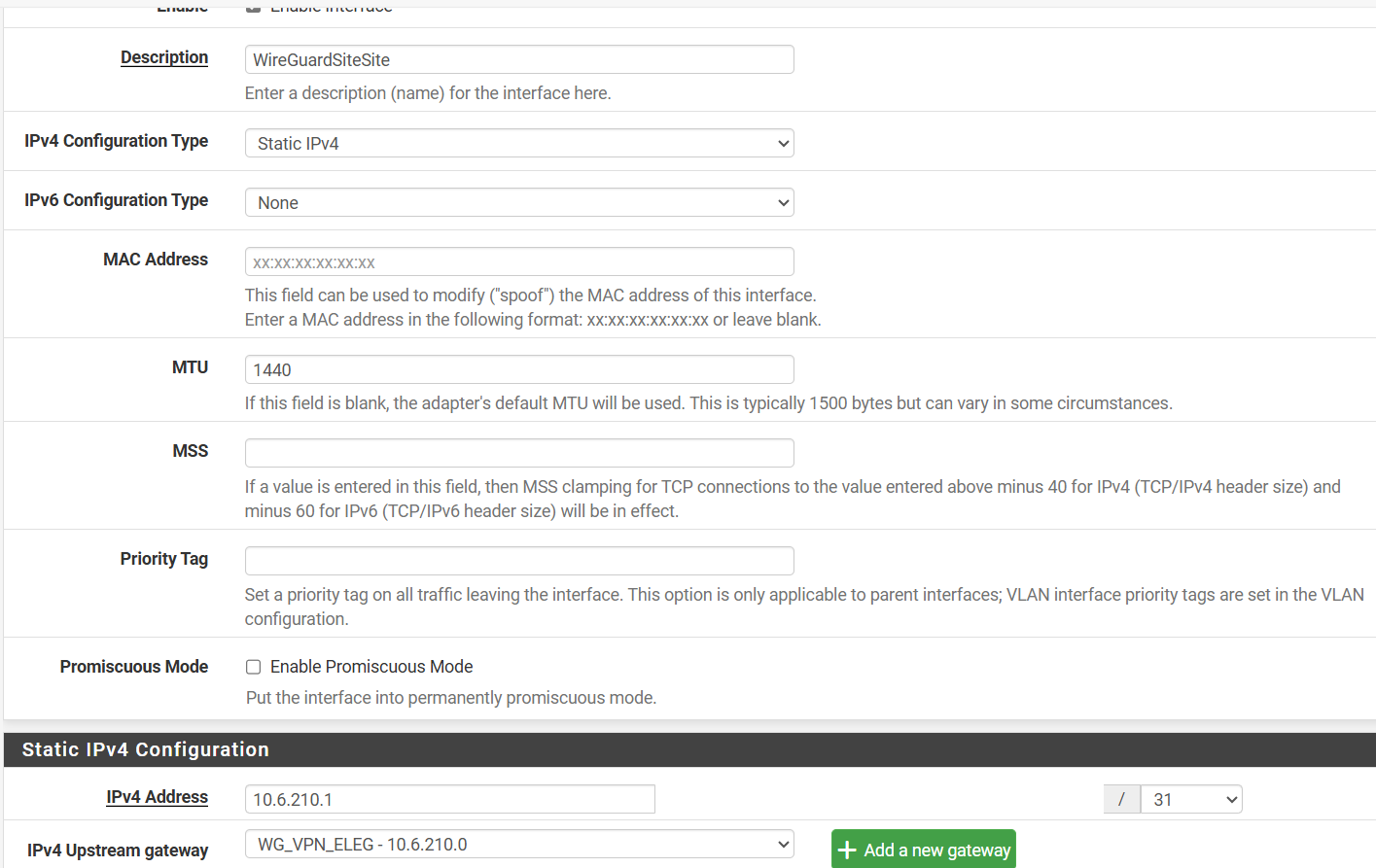
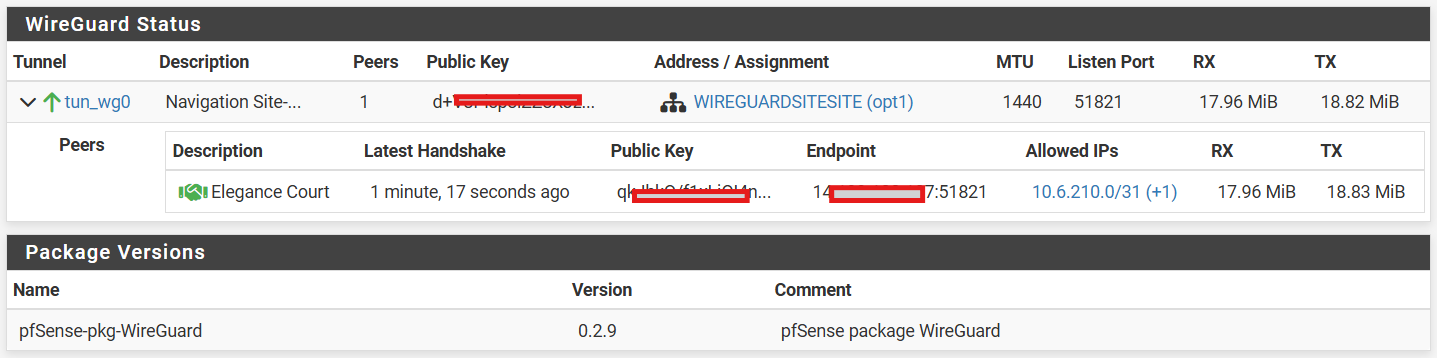
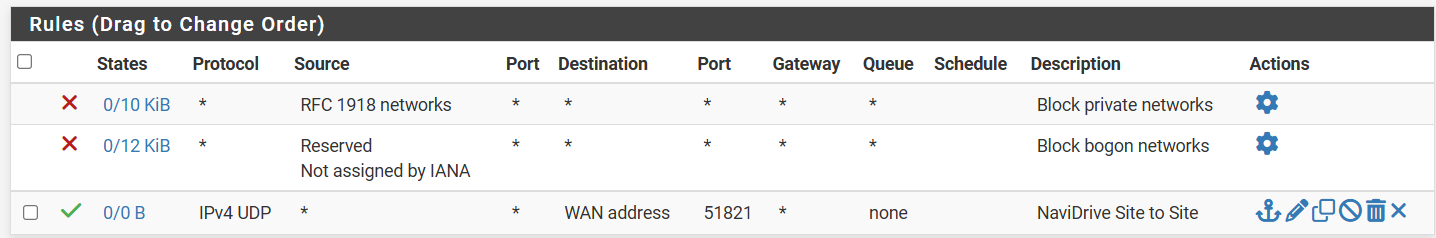
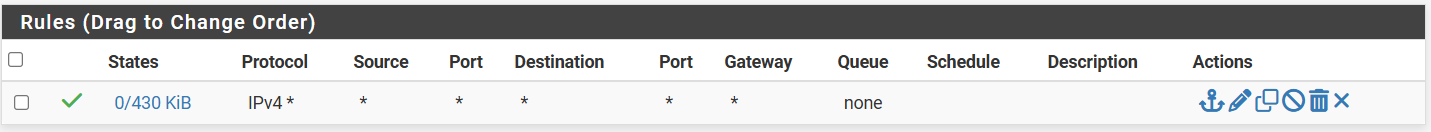
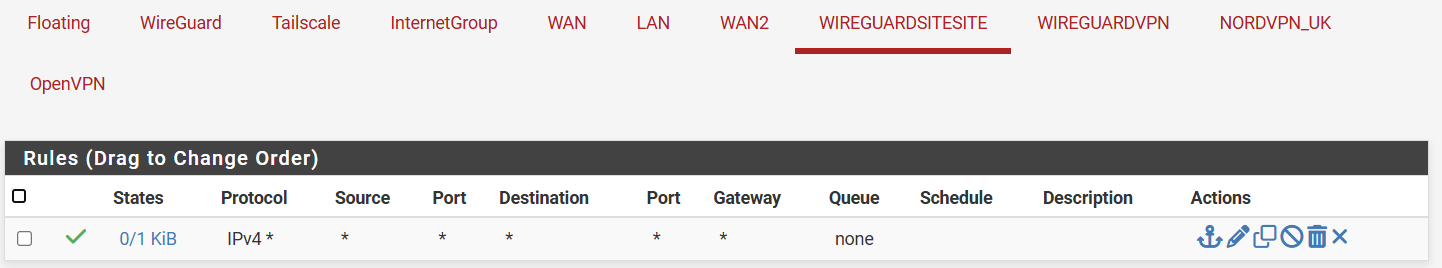
-
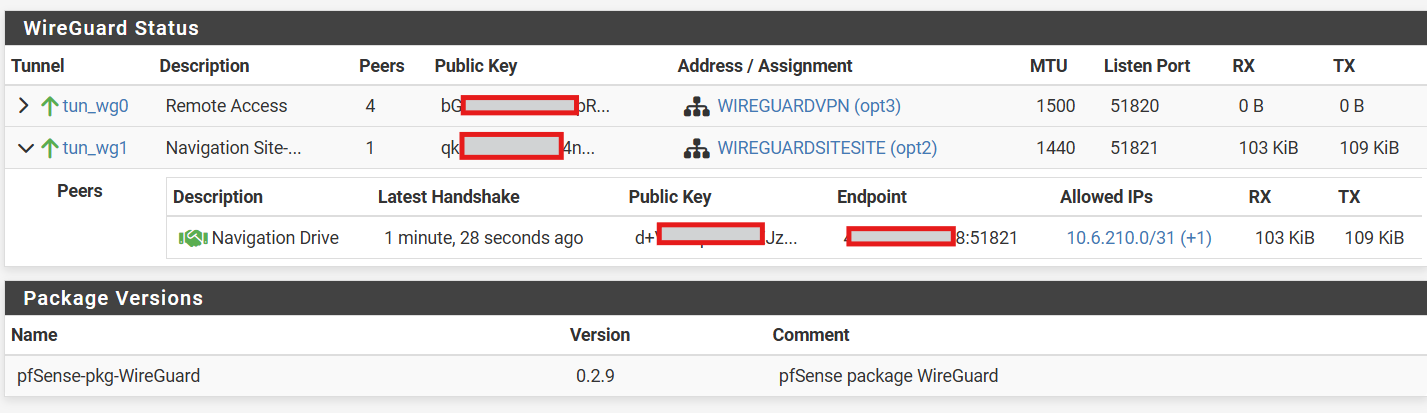
@MartynK Mmmmh, it does look ok. And looking at the RX and TX on the remote, it looks as some traffic is leaving over the tunnel. But the same values on the main site are very low.
I assume you have no other 10..../xx route that overlaps with with 10.6.210.0/31?
And do you have added static routes for the the local network(s) you want to route? And the networks you want to route on the main site and the remote site do not overlap?
-
@patient0 The numbers on the main site being low was because I rebooted the FW a little while ago, you never know if something was just odd.
The only other thing I have using a 10. address is 10.100.0.1 for a NORD VPN.
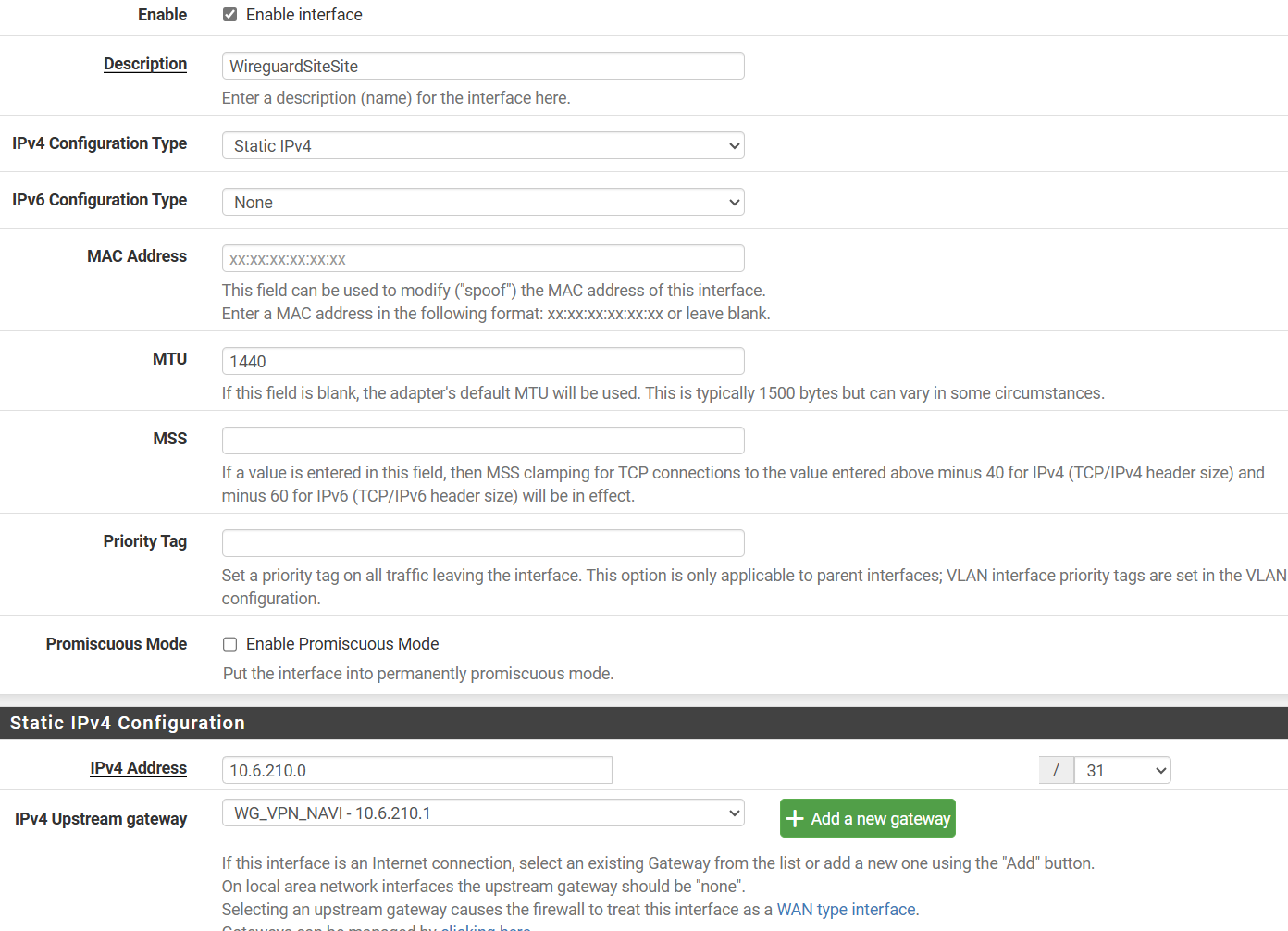
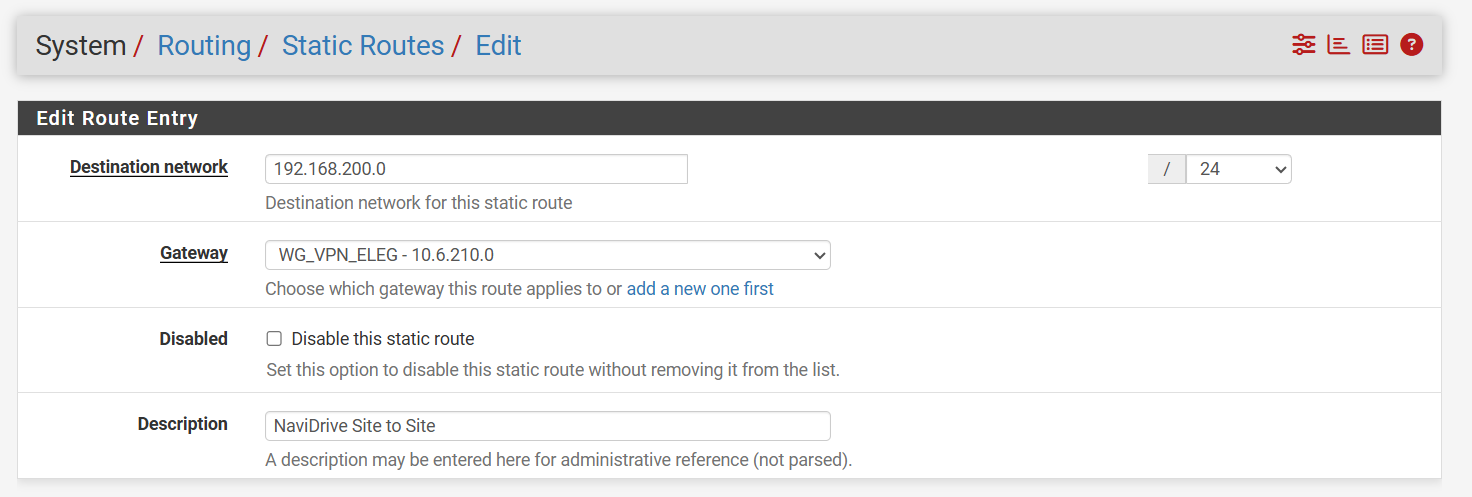
My two network ranges are 192.168.100.0 and 192.168.200.0The static routes are there as follows:
Host:
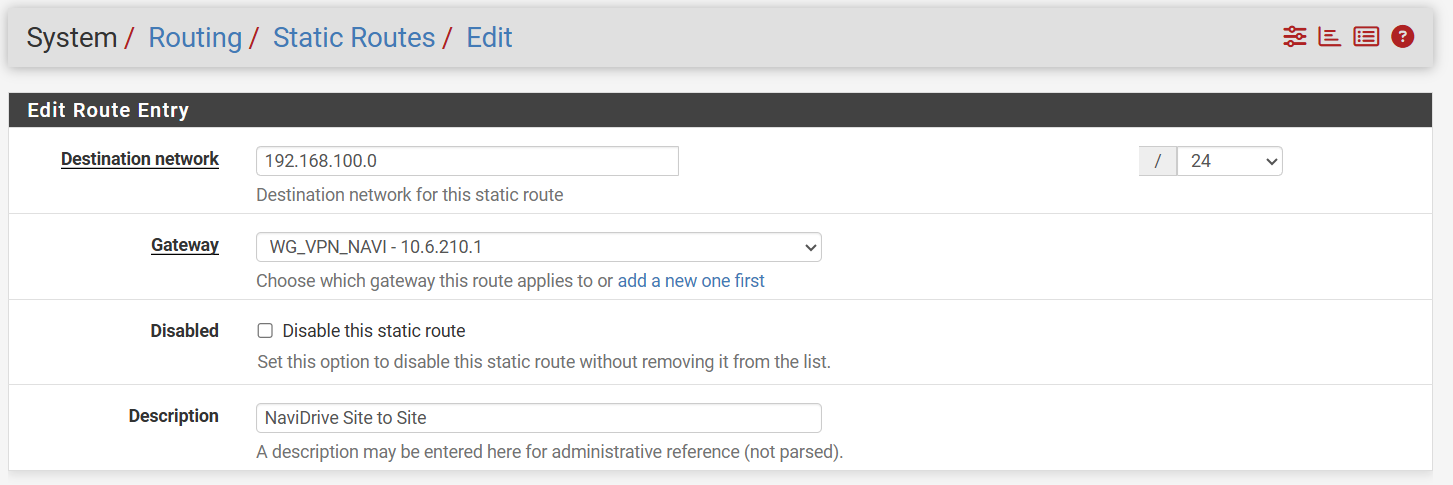
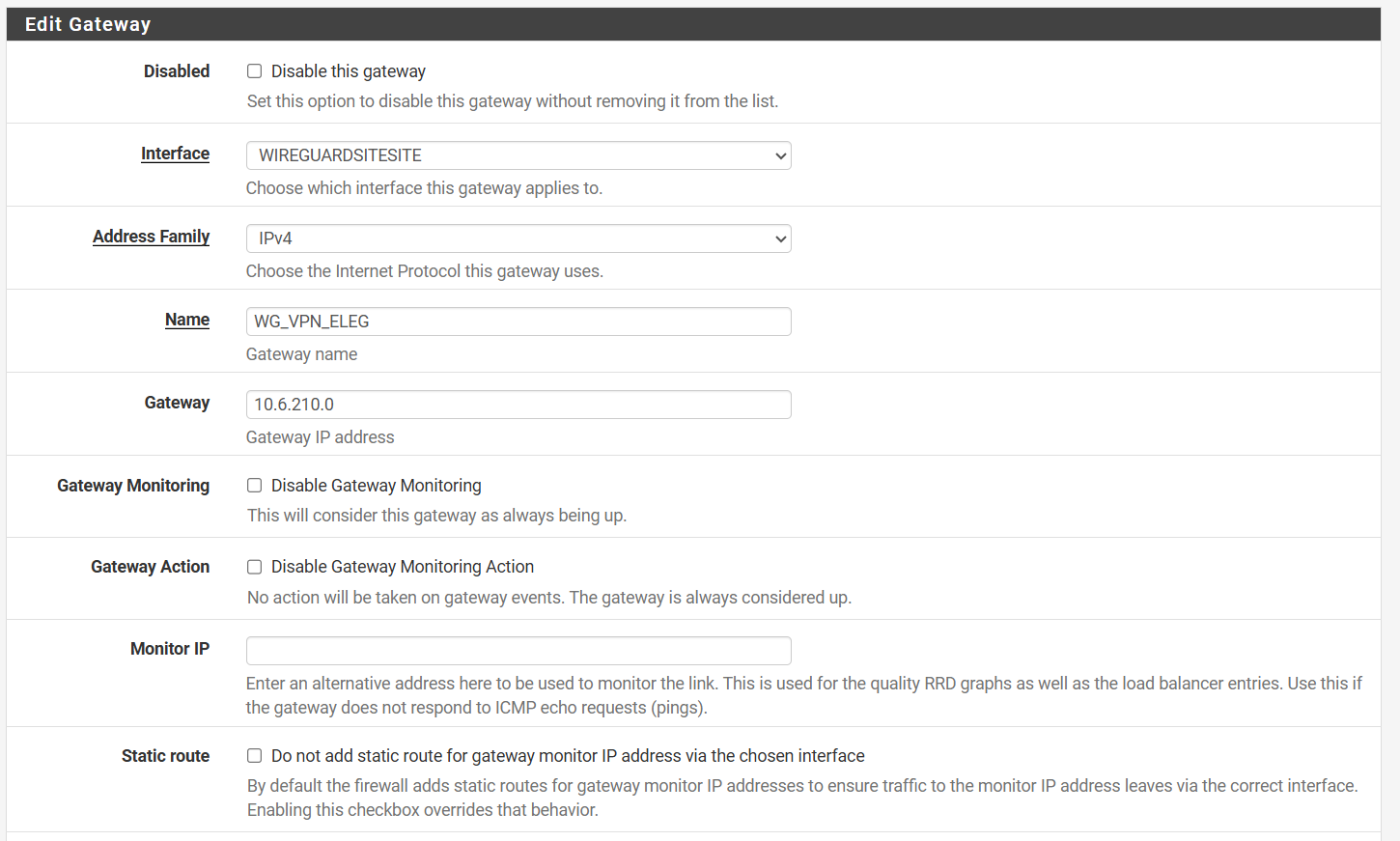
Remote:
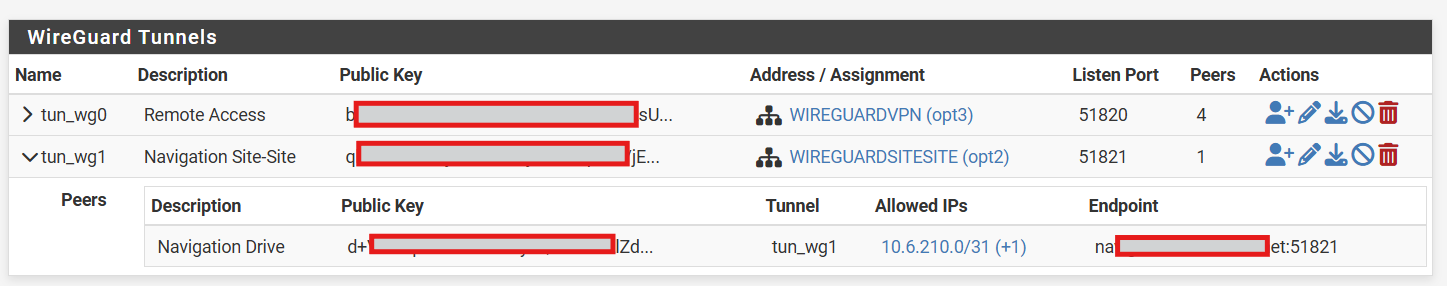
I am wondering if there is an issue with two WireGuard instances running, one for my remote access and another for the site to site as per:
-
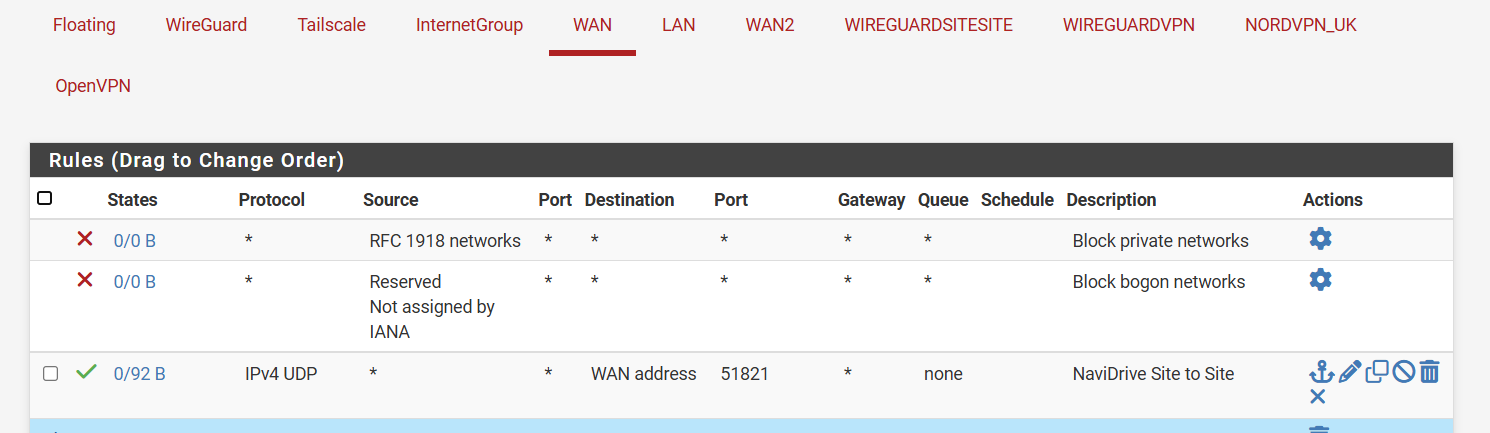
@patient0 Usually the allowed IPs for the WG-Connection itself is set to /32 and nothing else, so include only the IP of the other side. The guide might be wrong here. Also you should set MTU and MSS to 1420 on both sides. And check your Interface named "WireGuard", it should have no rules at all.
-
@MartynK said in Wireguard Site-to-site not passing traffic:
The only other thing I have using a 10. address is 10.100.0.1 for a NORD VPN.
That is surely ok, it only would be an issue if you got a route for something like 10.0.0.0/8. A route for 10.100.0.1/24 or similar is not overlapping at all.
My two network ranges are 192.168.100.0 and 192.168.200.0
If .100.0/24 is the network on the remote and .200.0/24 on the host, then you have set it correct.
I am wondering if there is an issue with two WireGuard instances running
No, multiple Wireguard tunnels on different ports are absolutely fine.
-
@patient0 I tried changing to a /32 and nothing worked.
I changed the MTU and MSS to 1420 nothing changed.
I rebooted both FWs and now it seems to work
-
@patient0 Thanks so much for your time in looking at this, not sure what happened.
I must admit I have had the same problem with DHCP before, did not take the settings until a reboot.
-
@MartynK that's ok, it's a bit odd that a reboot was necessary. Maybe it was the MTU changes?