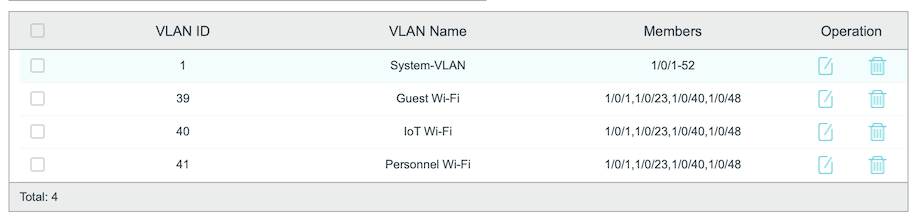
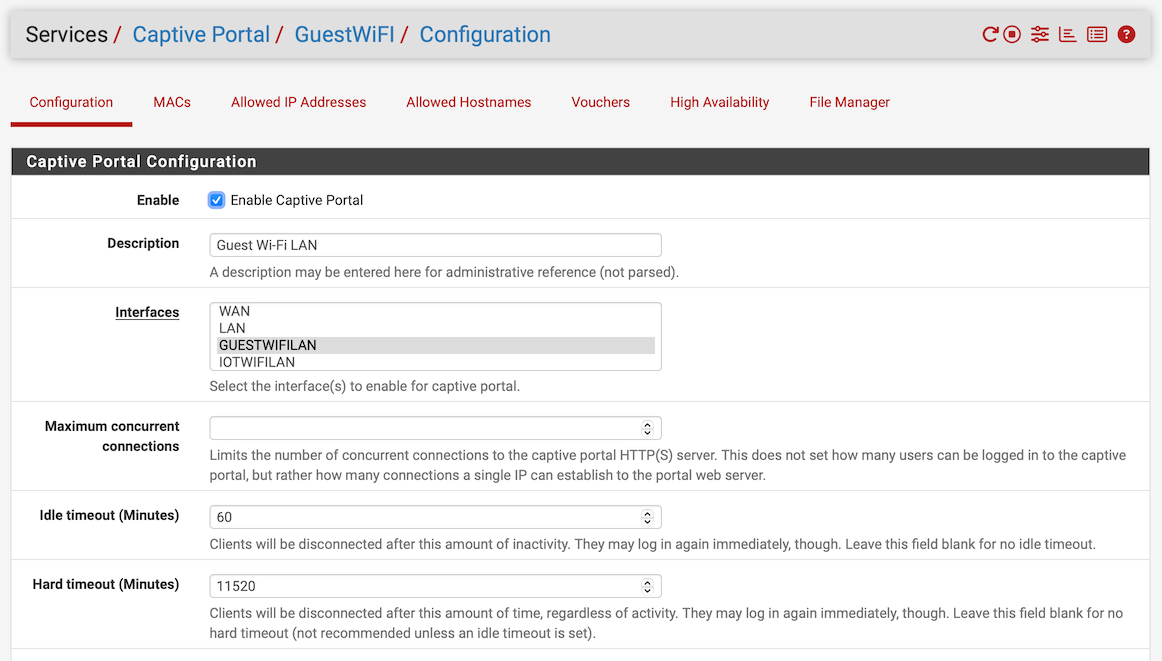
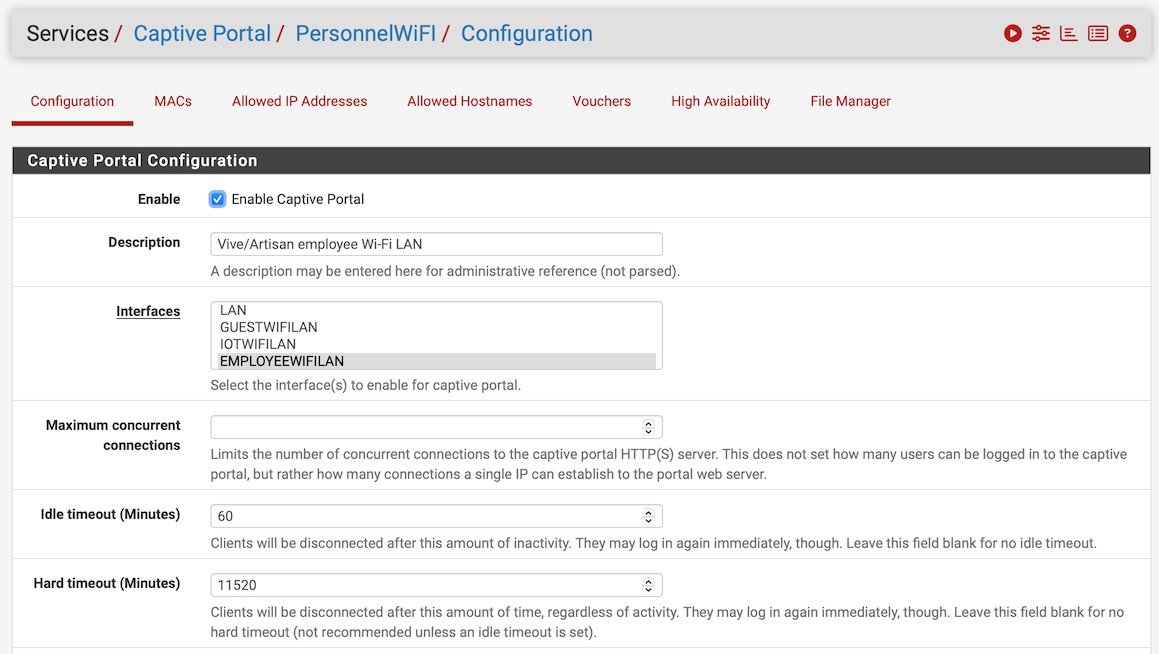
Two VLANs set up alike, one does not get Internet
-
@viragomann: So, I was mistaken. Hosts on the guest network do get IP addresses. DHCP is not the problem. Still, I cannot ping 192.168.39.1. It’s so weird!
Access points are Ubiquiti managed by a CloudKey Gen 2 Plus. It has DHCP guarding enabled, and the registered DHCP server is configured correctly. In that it is no different from the other VLANs using those access points.
Still feels like I am grasping at straws.
-
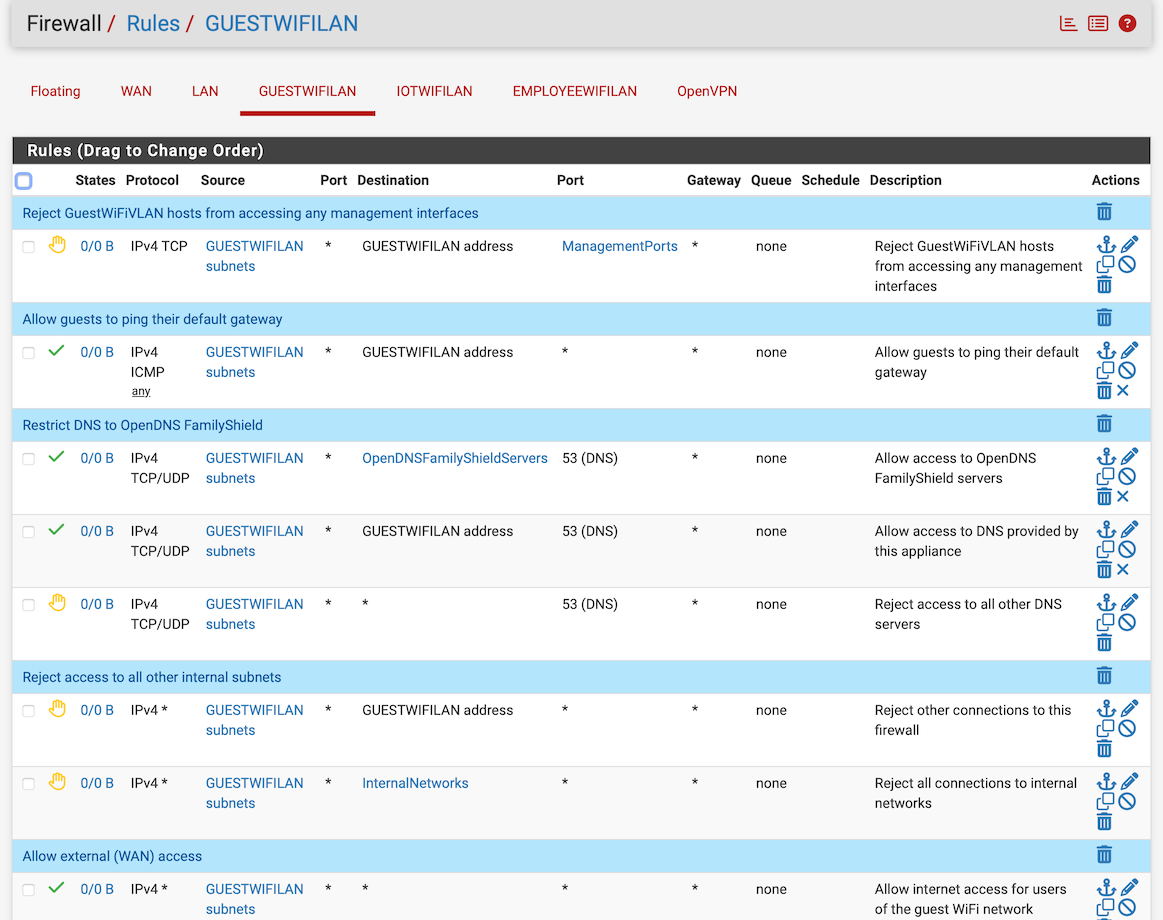
@DominikHoffmann The fact that there are no hits on any of the firewall rules on the GUESTWIFILAN interface suggests either switching or the traffic is being dropped off on the wrong VLAN.
-
@marvosa: Yes, you have a point. My problem is that it looks like I have checked everywhere that could be occurring and have found nothing. Obviously I am missing something.
I ran another test. I set my Ethernet-to-USB-C adapter to untag VLAN-ID 39 and plugged it directly into the Netgate-2100’s configured LAN port. Same behavior. I have the screenshots to demonstrate it:
The DHCP server assigns an IP and provides all the necessary information about the subnet:
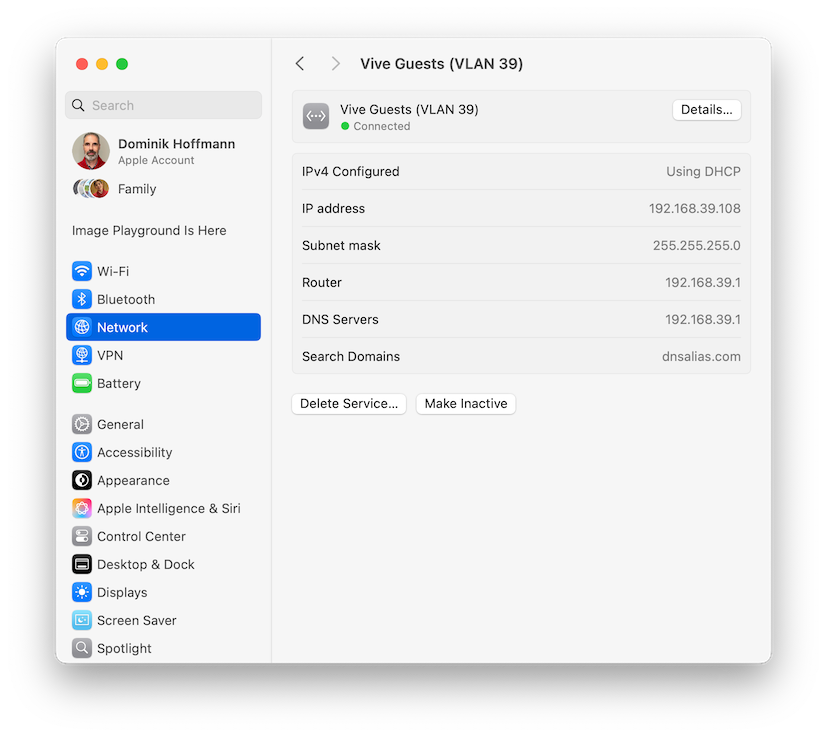
And, yet, I cannot ping the router address of 192.168.39.1:
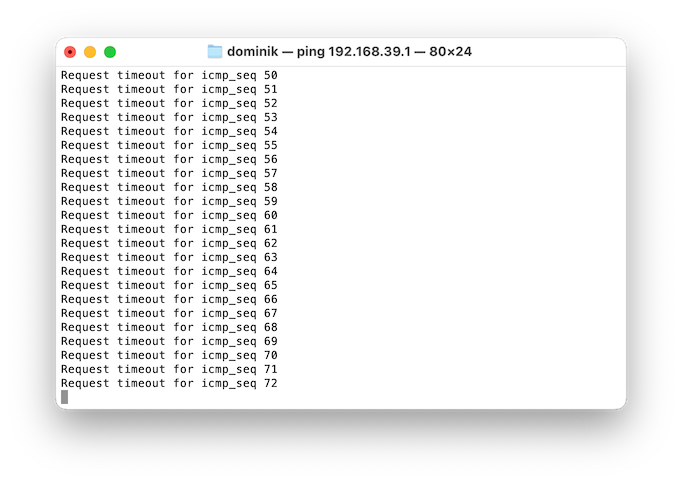
This clearly eliminates the smart switch and the Ubiquiti Wi-Fi controller as possible culprits. It’s all in the 2100. I will look into this further.
-
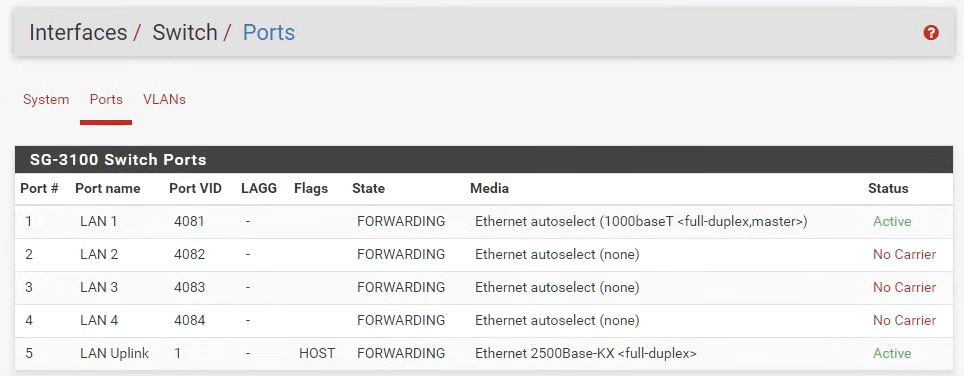
@DominikHoffmann Can you post what's shown on Interfaces -> Switch -> Ports?
-
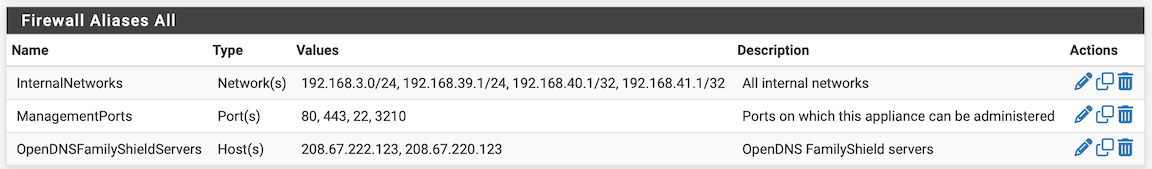
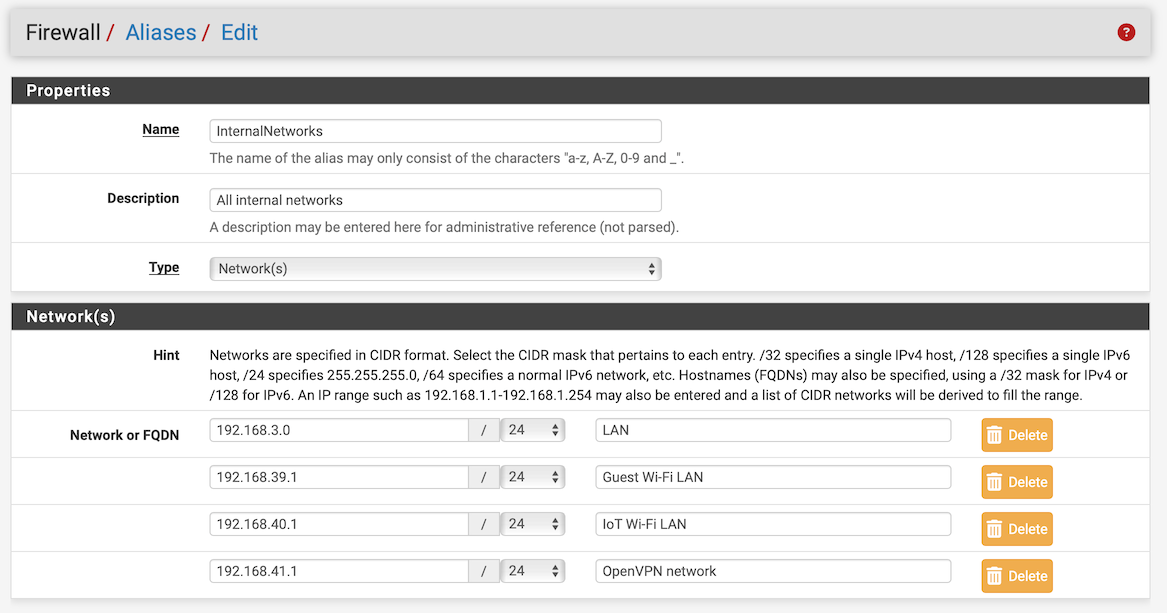
@DominikHoffmann on a unrelated note: in an early screenshot, in the alias 'InternalNetworks', two networks - 192.168.40.x and 192.168.41.x - have a subnet mask of /32.
Is that still the case and is that what you want?
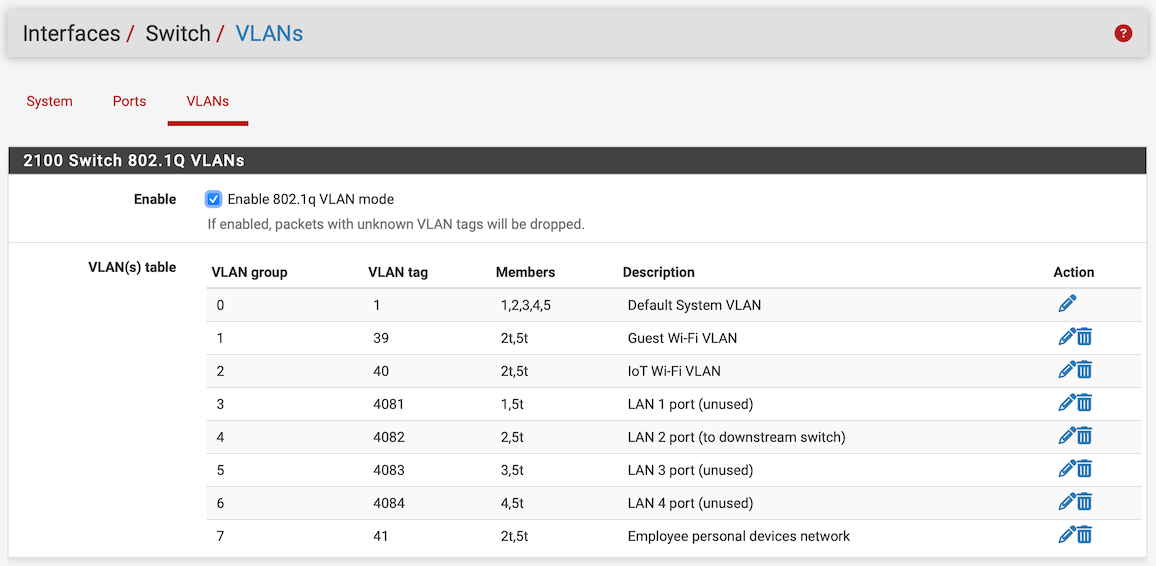
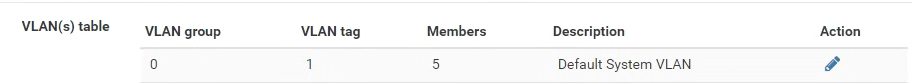
And I'm pretty sure your "Interface / Switch / VLANs" is not setup as it should.
All ports are still part of the VLAN group 0/VLAN tag 1. But one port should only be in one VLAN group untagged, check Netgate doc: Configuring the Switch Ports.
-
@marvosa said in Two VLANs set up alike, one does not get Internet:
@DominikHoffmann Can you post what's shown on Interfaces -> Switch -> Ports?
@patient0 said in Two VLANs set up alike, one does not get Internet:
@DominikHoffmann
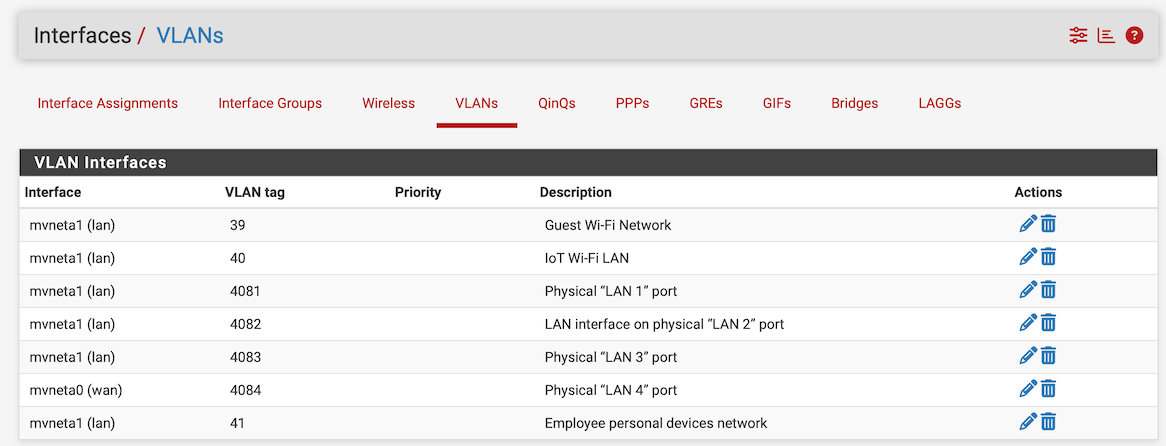
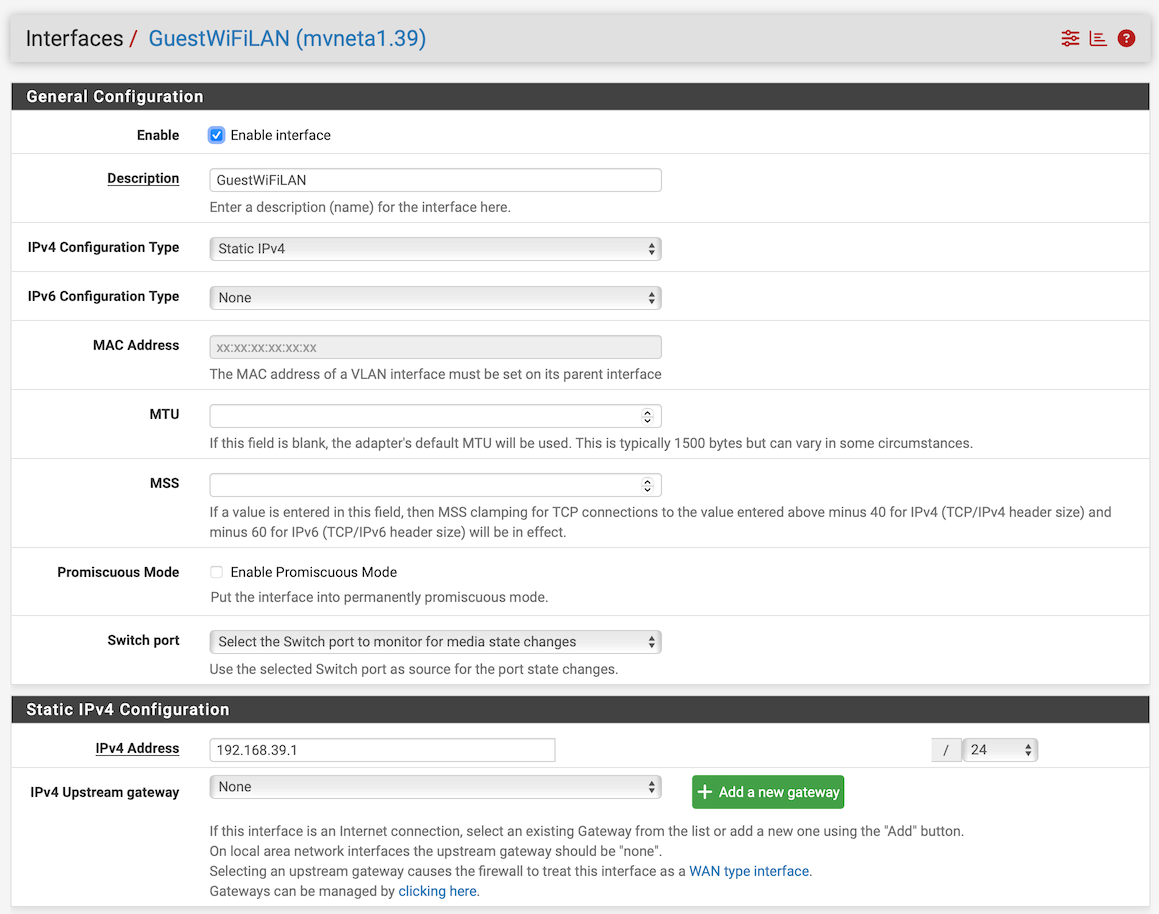
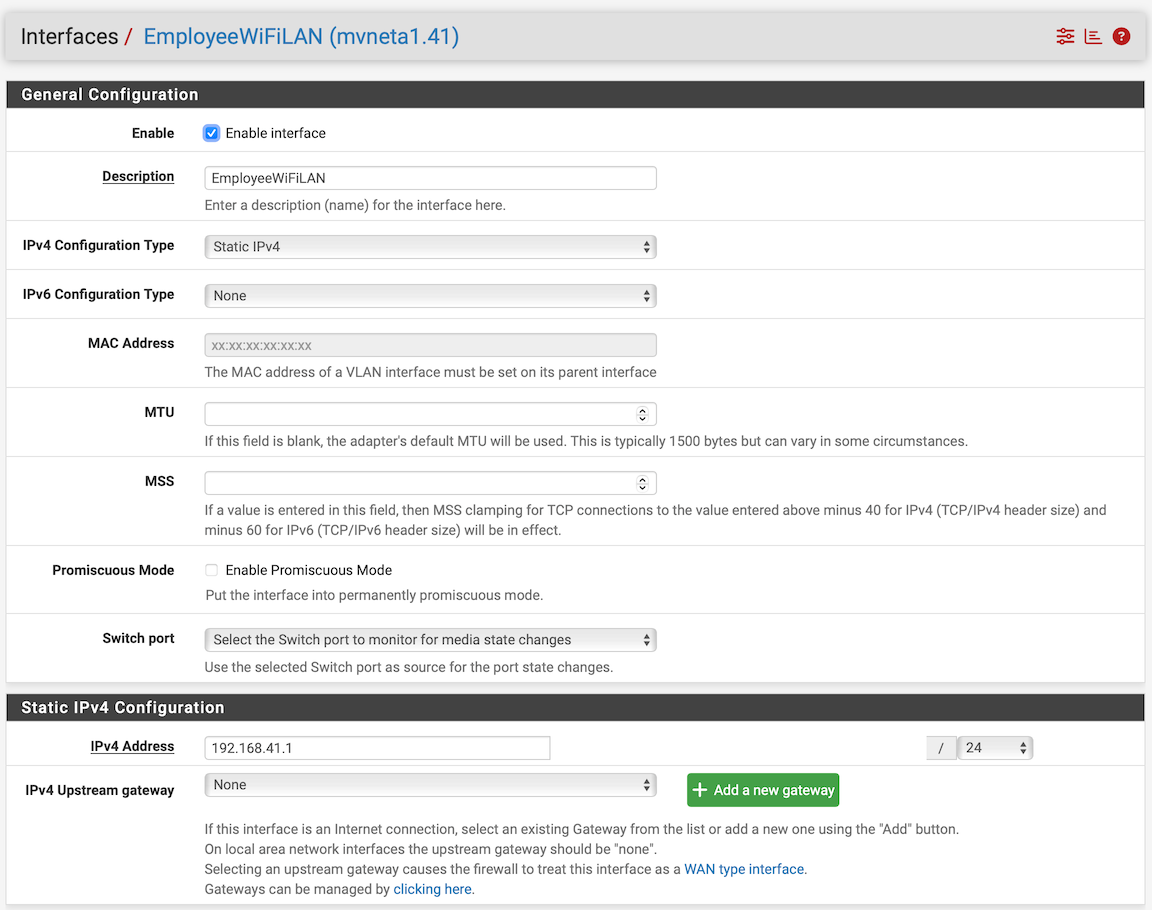
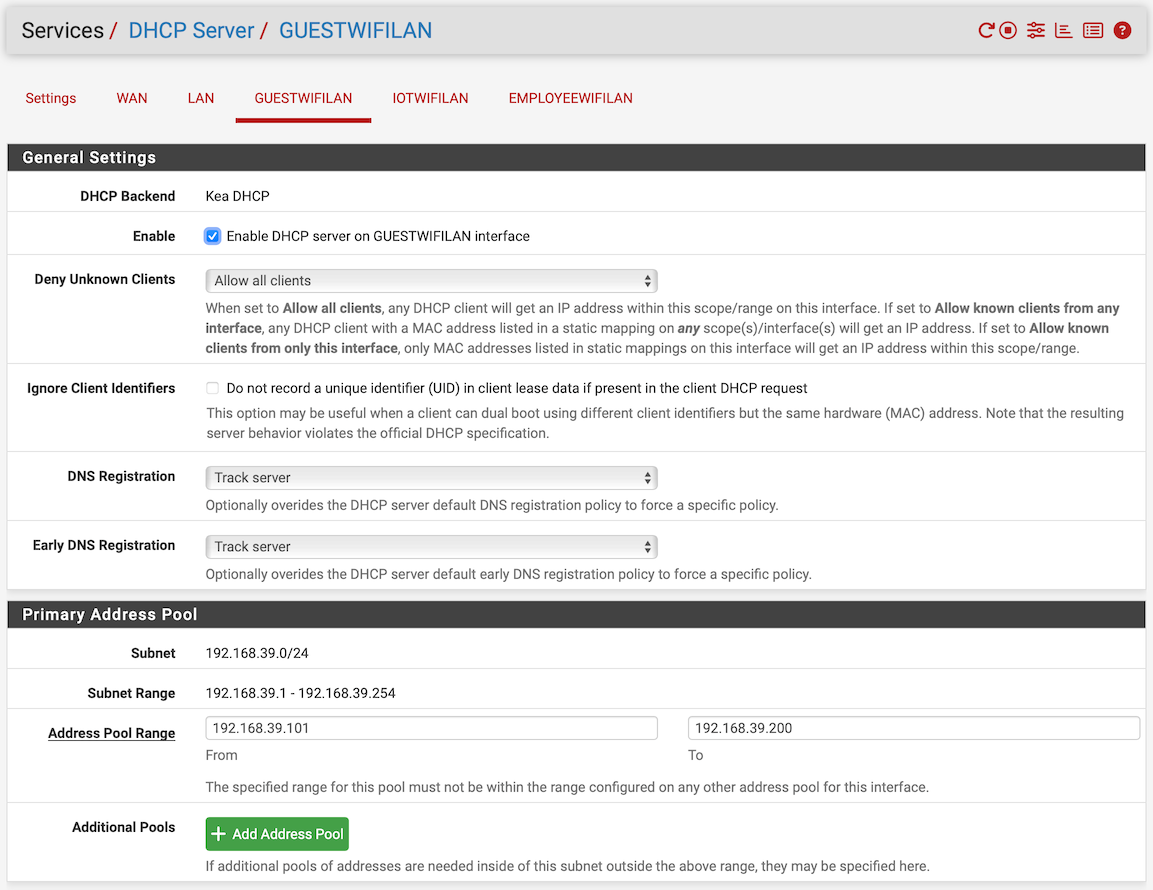
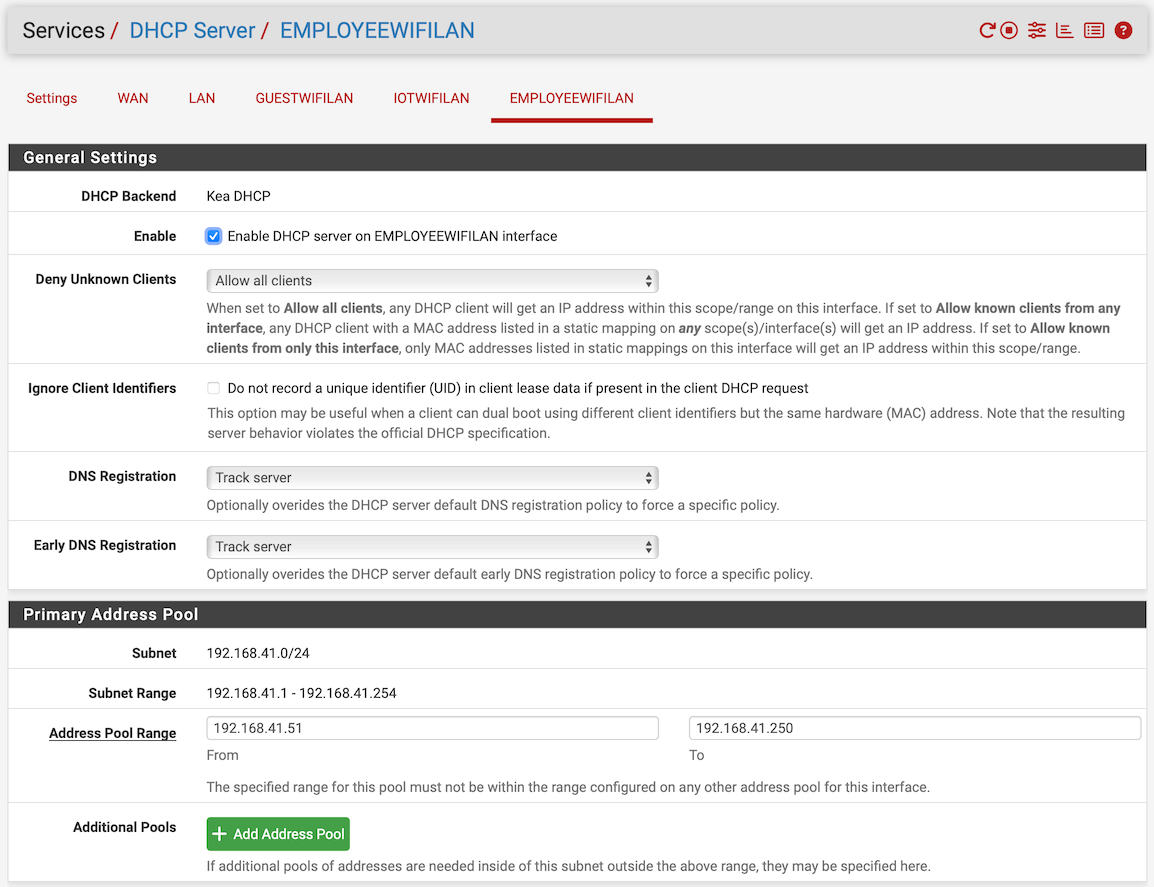
And I'm pretty sure your "Interface / Switch / VLANs" is not setup as it should.I am showing the corresponding configuration screens:

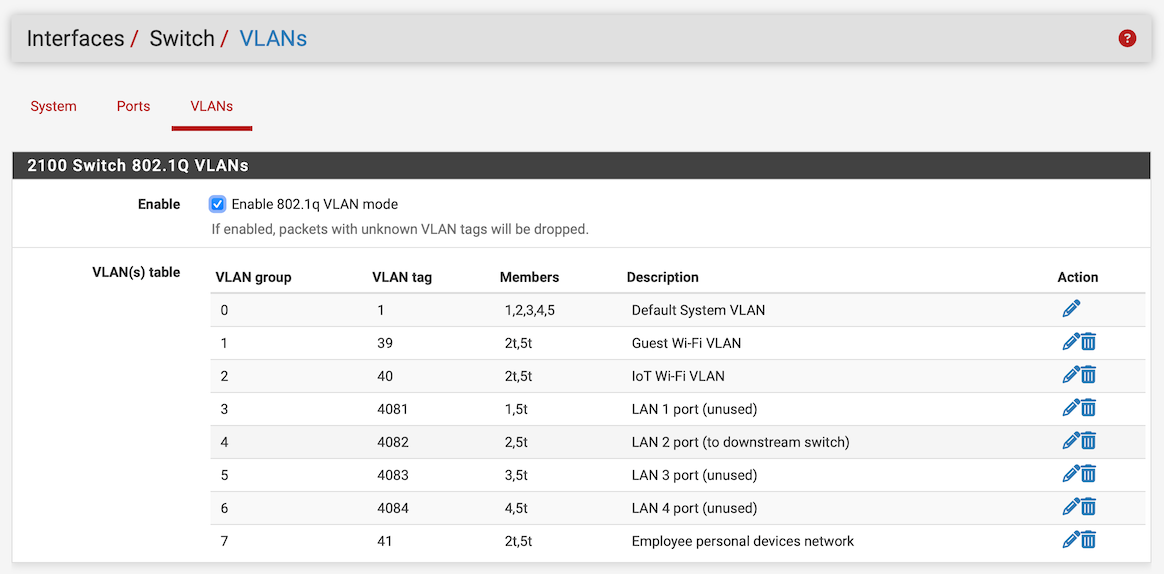
@patient0 said in Two VLANs set up alike, one does not get Internet:
on a unrelated note: in an early screenshot, in the alias 'InternalNetworks', two networks - 192.168.40.x and 192.168.41.x - have a subnet mask of /32.
I have corrected that:
It made no difference.
-
This post is deleted! -
@DominikHoffmann I'm afraid you have not setup the VLANs correctly on the 2100. They can't be all in Port VID 1. Have a look at the documentation I linked.
The example is for port 4, VLAN 4084 and shows what you have to set. E.g. set Port VID to 4084 in Interfaces / Switch / Ports, remove port 4 from VLAN group 0. That is exactly how you have to do for all the ports since you created VLANs for each switch port.
On the 2100 port 1 to 4 are on a hardware switch and the way you separate them into single ports is by assign them to VLANs.
-
@DominikHoffmann, it looks like multiple things may need to be addressed.
-
As @patient0 mentioned, it appears the VLAN table on Interfaces -> Switch -> VLANs needs to be adjusted. You'll want to remove members 1-4 from group 0, e.g similar to this.:
-
It looks like the switchports on the Netgate are misconfigured. From the vids and articles I've seen, your Interfaces -> Switch -> Ports section should look something like this:
-
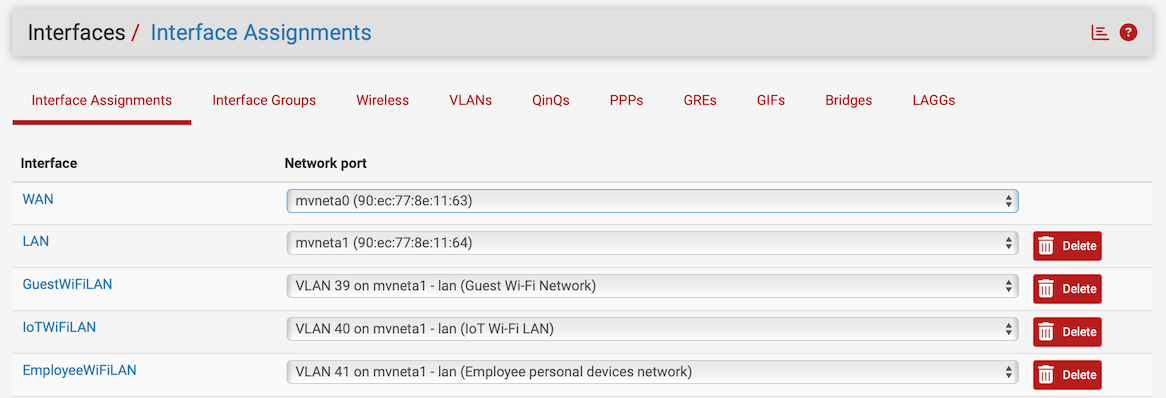
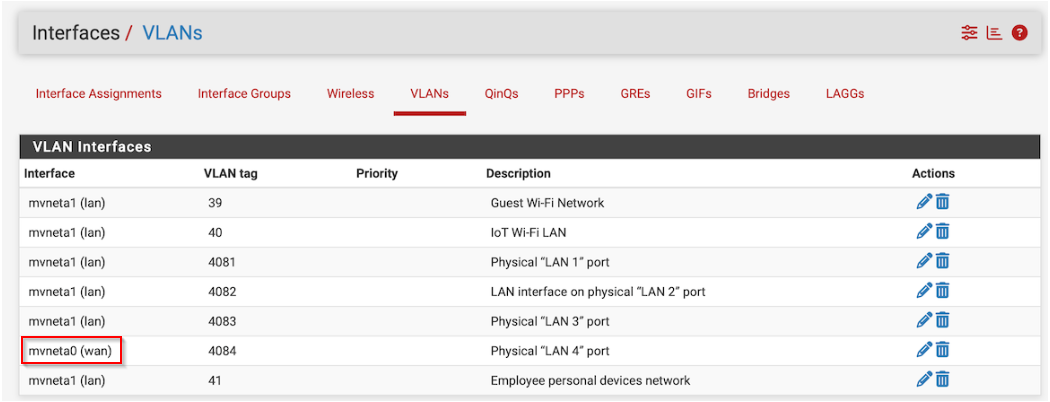
Another discrepancy I noticed, unless done by design for your use case, is on the Interfaces -> VLANs section. VLAN 4084 was created on the WAN interface instead of the LAN:
-
This is unrelated to the main issue, but regarding your "InternalNetworks" alias, I would modify the line items for Guest, IOT, and OpenVPN to reflect the actual network addresses. It's possible that what's listed may be accomplishing the same thing, depending on how the alias interprets it, but ideally, you'd want to list the network address if the intent is to block the network. I.e.:
192.168.39.0/24 - Guest Wi-Fi LAN
192.168.40.0/24 - IoT Wi-Fi LAN
192.168.41.0/24 - OpenVPN network -
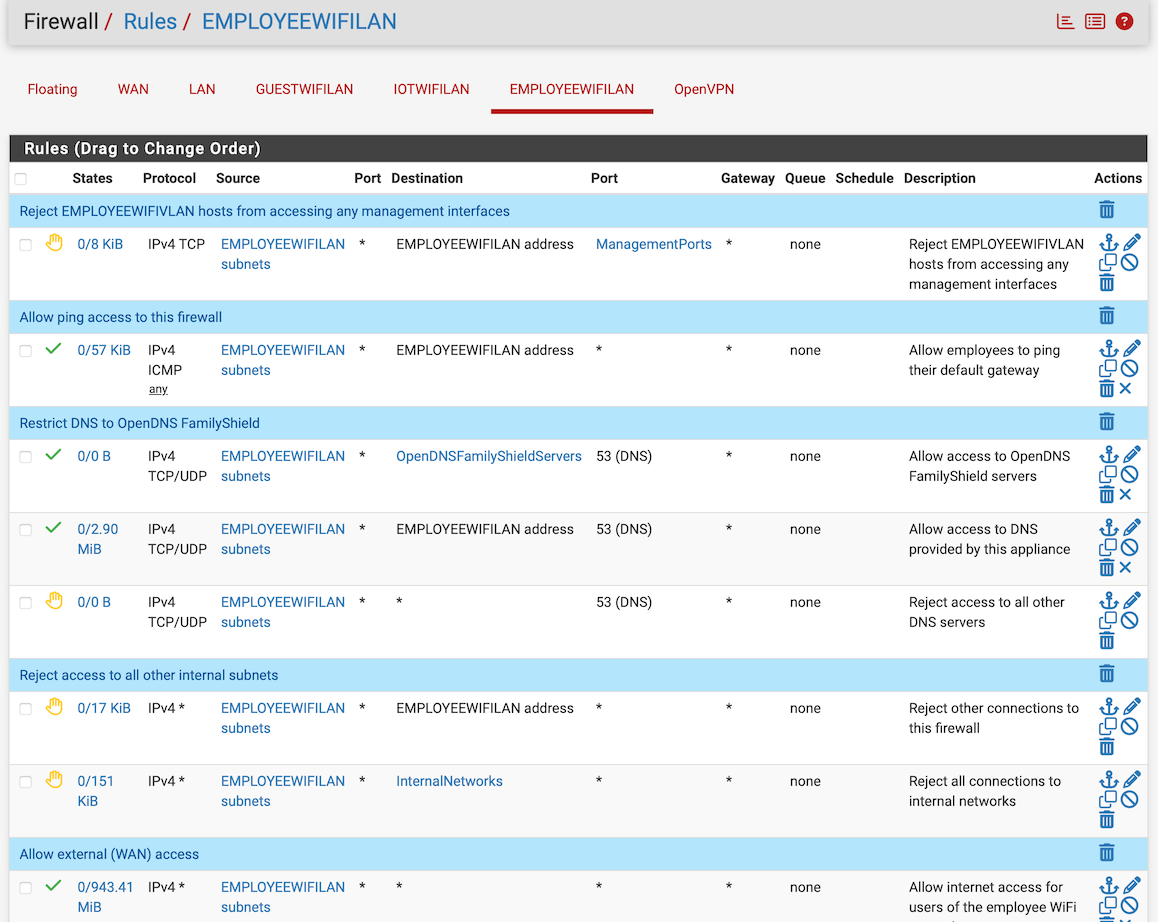
I also have a curious streamlining question for your firewall rules... at a glance, it would appear blocking management ports on the first line is redundant:
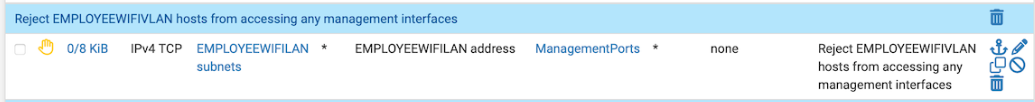
If we're already blocking all traffic to the firewall here:
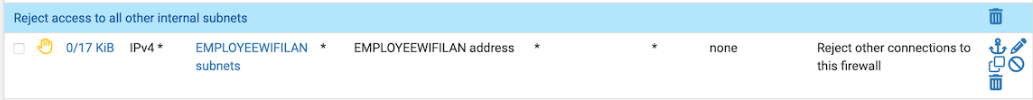
You likely have your reasons, just curious about your thoughts.
-
-
 P patient0 referenced this topic on
P patient0 referenced this topic on
-
So, thanks to various people in my thread specifically about the switch configuration on this system, I have found that the problem is the captive portal on the guest network. Now I have to go fix that. Possibly, I’ll post about that separately.
-
D DominikHoffmann referenced this topic on
-
Indeed, I have to consult the community on how to configure the captive portal, too.