NAT broken after Reboot
-
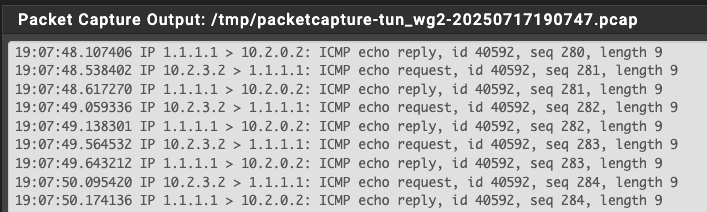
"The misconception that WireGuard inevitably generates logs is probably based on the fact that, by default, it requires a static (and therefore identifiable) connection between the VPN app and the VPN server. To get around this, we hardcoded our apps to begin every WireGuard VPN connection using the same internal IP address (10.2.0.2).
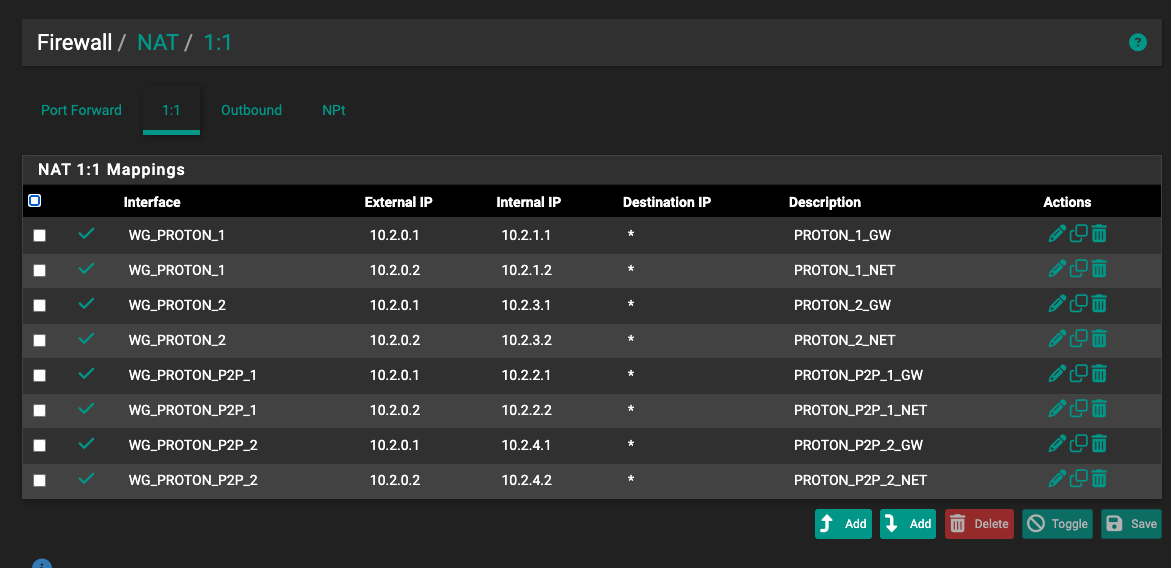
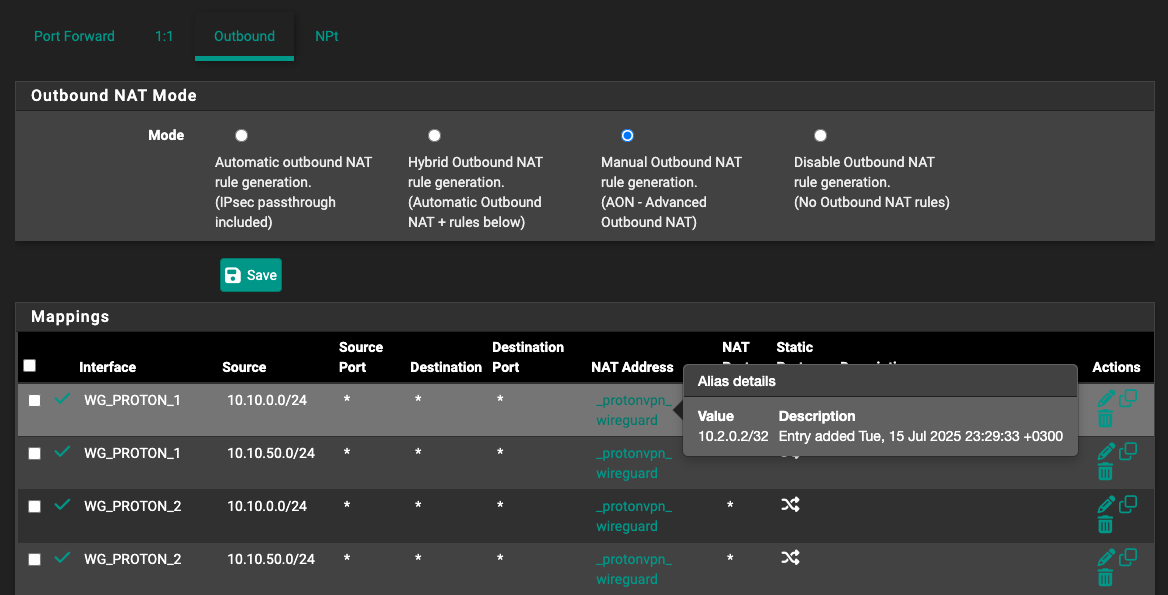
To allow more than two people to be connected to the same VPN server at the same time on WireGuard, we use double network address translation (NAT) to dynamically provision sessions.
This means when your app connects to one of our VPN servers via WireGuard, the first NAT will rewrite the 10.2.0.2 IP address to a random but unique internal IP address that is assigned to your session. From this point on, WireGuard works like any other VPN: The second NAT rewrites your session IP address again to the VPN server’s public IP address before it connects to your desired website."
wireguard-privacy -
@iggybuddy6 yup, just found those pages...
-
@iggybuddy6 said in NAT broken after Reboot:
Hence I can not use the "normal way" to add multiple Wireguard
You can. Just don't use 10.2.0.2. Use 10.2.0.3 and so on. And use that IP also as the gateway. -
@Bob-Dig
How do you mean? The VPN provider tells what the Internal IP address is. If proton always uses 10.2.0.2 I can not simply choose another IP.I do not think you ever tried to add multiple Proton VPN connections to your pfsense.
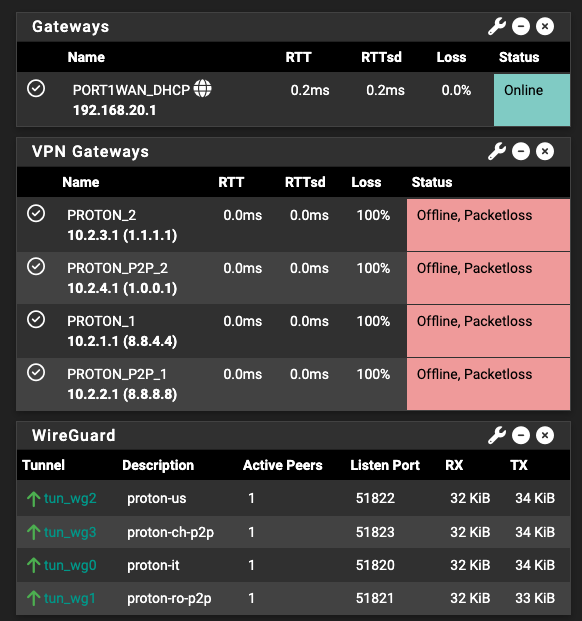
I think we are diverging a bit from the real issue. As I said my setup is working up until I restart the Netgate. After that I need to add a fake Wireguard tunnel to make it work again. Something is off with the behavior ... -
@iggybuddy6 There is another approach suggested in that reddit thread, a comment by CounterI four months ago: https://www.reddit.com/r/ProtonVPN/comments/127zpbe/comment/mi1mq2x/
They ended up not doing 1:1 NAT but added another set of interfaces and NATed those
 (you better read that comment)
(you better read that comment)Maybe that is a cleaner solution?
(fwiw, I've reached my daily goal of learning something new every day
 )
) -
@iggybuddy6 said in NAT broken after Reboot:
I do not think you ever tried to add multiple Proton VPN connections to your pfsense.
You are right, I must have confused this with another VPN-Provider. I am using OpenWRT-VMs for all my Proton-WG-tunnels.
-
@pst I will definitely check this. Thx a lot for pointing that out!
-
@Bob-Dig Sure np.
I was thinking a high level details NAT debug after after reboot and after fixing the problem adding dummy tunnel would trigger an answer pointing me to some known behavior and fix -
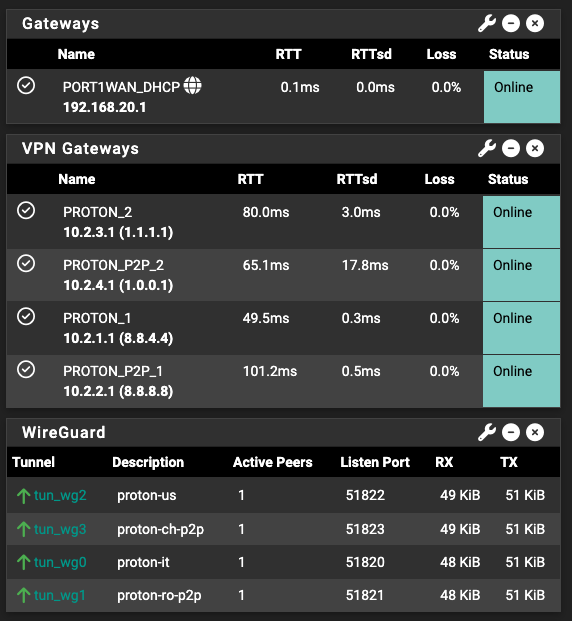
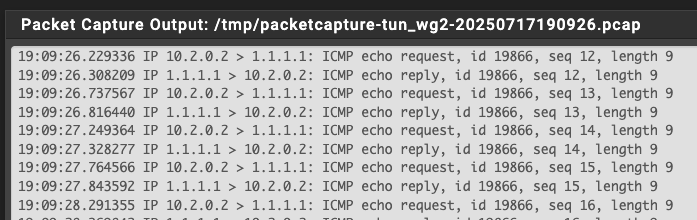
@pst I have tried a couple of wireguard connections using that alternative method and it seems to be working without the need of NAT 1:1 !!!
It looks good so far after rebooting. Thank you so much for pointing out that comment. I have spent so much time and this definitely should make the setup more reliableYou saved me so much time and from a massive headache I can not thank you enough



-
@iggybuddy6 I'm just happy I could help. Today I went from thinking I knew everything about setting up wg on pfSense, to realising I did not, and that is a great reward in itself!
Hopefully your setup will remain stable going forward.