[2.8.1.b] Multiple limiter issue
-
@NWOSwamp I noticed the same incorrect behaviour in the first 25.07-rc (July09), I have yet to test the latest (July15-rc)
For reference: https://forum.netgate.com/post/1220637
-
@pst I have tested the June15 25.07-RC and the same problems exist there. Certain limiter combinations just doesn't work in the 2025 releases of pfSense. @stephenw10 , is Netgate aware and actively working on resolving the current limiter issues, or do I need to raise yet another redmine?
Here's todays results from 25.07.r.20250715.1733:
test #1 LAN Limiters
Setup:
- Limiters configured on LAN 100Mb/s DL 50Mb/s UL
- policy routing IPv4 only (IPv6 LAN rules disabled)
Preparation:
- reset firewall state table
Results:
- speedtest.net DL 96Mb/s UL 47Mb/s
Conclusions:
- LAN speeds matches the configured LAN limiters (Success)
[begin update]
the LAN rule:
@676 pass in quick on igb1 route-to (igb0 <GW-ip>) inet from <LAN__NETWORK:3> to any flags S/SA keep state (if-bound) label "USER_RULE: Default allow all from LAN" label "id:1746203437" label "gw:WAN_DHCP" ridentifier 1746203437 dnqueue(6, 5) [ Evaluations: 1191 Packets: 732499 Bytes: 714877597 States: 77 ] [ Inserted: uid 0 pid 0 State Creations: 78 ] [ Last Active Time: Sat Jul 19 15:32:33 2025 ]the LAN state:
igb1 tcp 137.226.34.45:9001 <- 192.168.0.10:60316 ESTABLISHED:ESTABLISHED [2830908969 + 262144] wscale 7 [3555634996 + 63616] wscale 8 age 00:00:48, expires in 23:59:59, 84:101 pkts, 40230:41100 bytes, rule 676 id: 80bd946800000000 creatorid: 76926c2a route-to: <GW-ip>@igb0the WAN state:
igb0 tcp <WAN-ip>:4417 (192.168.0.10:60316) -> 137.226.34.45:9001 ESTABLISHED:ESTABLISHED [3555634996 + 63616] wscale 8 [2830908969 + 262144] wscale 7 age 00:00:48, expires in 23:59:59, 84:101 pkts, 40230:41100 bytes, rule 306, allow-opts id: 81bd946800000000 creatorid: 76926c2a route-to: <GW-ip>@igb0I'm not sure if the limiter is supposed to add another state, but I couldn't find one. As this case is working fine, I assume there is no additional state when using a LAN limiter.
[end update]
test #2 LAN+WAN Limiters, policy routing
Setup:
- Limiters configured on LAN 100Mb/s DL 50Mb/s UL
- policy routing IPv4 only (IPv6 LAN rules disabled)
- Limiter configured on WAN 200Mb/s DL 150Mb/s UL
- buffer-bloat floating rule on WAN (Netgate recepie)
Preparation:
- reset firewall state table
Results:
- speedtest.net DL 196Mb/s UL 145Mb/s
Conclusions:
- LAN speeds matches the configured WAN limiters (Failure)
[begin update]
the LAN rule:
@677 pass in quick on igb1 route-to (igb0 <GW-ip>) inet from <LAN__NETWORK:3> to any flags S/SA keep state (if-bound) label "USER_RULE: Default allow all from LAN" label "id:1746203437" label "gw:WAN_DHCP" ridentifier 1746203437 dnqueue(6, 5) [ Evaluations: 443 Packets: 137929 Bytes: 133343647 States: 80 ] [ Inserted: uid 0 pid 0 State Creations: 87 ] [ Last Active Time: Sat Jul 19 15:23:31 2025 ]the WAN rule:
@342 pass out quick on igb0 route-to (igb0 <GW-ip>) inet from <WAN-ip> to any flags S/SA keep state (if-bound) label "USER_RULE: From bufferbloat recipe" label "id:1750159398" label "gw:WAN_DHCP" ridentifier 1750159398 dnqueue(2, 1) [ Evaluations: 20977 Packets: 1198815 Bytes: 1126546123 States: 103 ] [ Inserted: uid 0 pid 0 State Creations: 166 ] [ Last Active Time: Sat Jul 19 15:23:30 2025 ]the LAN state:
igb1 tcp 142.250.74.106:443 <- 192.168.0.10:58800 ESTABLISHED:ESTABLISHED [799371312 + 261376] wscale 8 [2304724535 + 262656] wscale 8 age 00:01:21, expires in 23:59:03, 20:23 pkts, 8918:4625 bytes, rule 677 id: 94a3946800000000 creatorid: 76926c2a route-to: <GW-ip>@igb0the WAN state:
igb0 tcp <WAN-ip>:59630 (192.168.0.10:58800) -> 142.250.74.106:443 ESTABLISHED:ESTABLISHED [2304724535 + 262656] wscale 8 [799371312 + 261376] wscale 8 age 00:01:21, expires in 23:59:03, 20:23 pkts, 8918:4625 bytes, rule 342 id: 95a3946800000000 creatorid: 76926c2a route-to: <GW-ip>@igb0[end update]
test #3 LAN+WAN Limiters, default routing
Setup:
- Limiters configured on LAN 100Mb/s DL 50Mb/s UL
- default routing IPv4 only, IPv6 LAN rules disabled
- Limiter configured on WAN 200Mb/s DL 150Mb/s UL
- buffer-bloat floating rule on WAN (Netgate recepie)
Preparation:
- reset firewall state table
Results:
- speedtest.net DL 193Mb/s UL 48Mb/s
Conclusions:
- DL LAN speed matches the configured WAN DL limiter (Failure)
- UL LAN speed matches the configured LAN UL limiter (Success)
[begin update]
the LAN rule:
@677 pass in quick on igb1 inet from <LAN__NETWORK:3> to any flags S/SA keep state (if-bound) label "USER_RULE: Default allow all from LAN" label "id:1746203437" ridentifier 1746203437 dnqueue(6, 5) [ Evaluations: 745 Packets: 723716 Bytes: 689917885 States: 78 ] [ Inserted: uid 0 pid 0 State Creations: 170 ] [ Last Active Time: Sat Jul 19 15:09:14 2025 ]the WAN rule:
@342 pass out quick on igb0 route-to (igb0 <GW-ip>) inet from <WAN-ip> to any flags S/SA keep state (if-bound) label "USER_RULE: From bufferbloat recipe" label "id:1750159398" label "gw:WAN_DHCP" ridentifier 1750159398 dnqueue(2, 1) [ Evaluations: 8204 Packets: 735203 Bytes: 697785013 States: 102 ] [ Inserted: uid 0 pid 0 State Creations: 398 ] [ Last Active Time: Sat Jul 19 15:09:14 2025 ]the LAN state:
igb1 tcp 64.233.164.188:5228 <- 192.168.0.10:56610 ESTABLISHED:ESTABLISHED [3711352026 + 261888] wscale 8 [1875466931 + 267776] wscale 8 age 00:01:13, expires in 23:59:32, 9:12 pkts, 2442:7559 bytes, rule 677 id: da78946800000000 creatorid: 76926c2athe WAN state:
igb0 tcp <WAN-ip>:40446 (192.168.0.10:56610) -> 64.233.164.188:5228 ESTABLISHED:ESTABLISHED [1875466931 + 267776] wscale 8 [3711352026 + 261888] wscale 8 age 00:01:13, expires in 23:59:32, 9:12 pkts, 2442:7559 bytes, rule 342 id: db78946800000000 creatorid: 76926c2a route-to: <GW-ip>@igb0[end update]
[addendum]
Limiter configuration:[25.07-RC][admin@felicity.local.lan]/root: dnctl sched list 00001: 200.000 Mbit/s 0 ms burst 0 q65537 50 sl. 0 flows (1 buckets) sched 1 weight 0 lmax 0 pri 0 droptail sched 1 type FQ_CODEL flags 0x0 0 buckets 0 active FQ_CODEL target 5ms interval 100ms quantum 1514 limit 10240 flows 1024 ECN Children flowsets: 1 00002: 150.000 Mbit/s 0 ms burst 0 q65538 50 sl. 0 flows (1 buckets) sched 2 weight 0 lmax 0 pri 0 droptail sched 2 type FQ_CODEL flags 0x0 0 buckets 0 active FQ_CODEL target 5ms interval 100ms quantum 1514 limit 10240 flows 1024 ECN Children flowsets: 2 00005: 100.000 Mbit/s 0 ms burst 0 q65541 50 sl. 0 flows (1 buckets) sched 5 weight 0 lmax 0 pri 0 droptail sched 5 type FQ_CODEL flags 0x0 0 buckets 0 active FQ_CODEL target 5ms interval 100ms quantum 1514 limit 10240 flows 1024 ECN Children flowsets: 5 00006: 50.000 Mbit/s 0 ms burst 0 q65542 50 sl. 0 flows (1 buckets) sched 6 weight 0 lmax 0 pri 0 droptail sched 6 type FQ_CODEL flags 0x0 0 buckets 0 active FQ_CODEL target 5ms interval 100ms quantum 1514 limit 10240 flows 1024 ECN Children flowsets: 6 [25.07-RC][admin@felicity.local.lan]/root: dnctl pipe list 00001: 200.000 Mbit/s 0 ms burst 0 q131073 2000 sl. 0 flows (1 buckets) sched 65537 weight 0 lmax 0 pri 0 droptail sched 65537 type FIFO flags 0x0 0 buckets 0 active 00002: 150.000 Mbit/s 0 ms burst 0 q131074 2000 sl. 0 flows (1 buckets) sched 65538 weight 0 lmax 0 pri 0 droptail sched 65538 type FIFO flags 0x0 0 buckets 0 active 00005: 100.000 Mbit/s 0 ms burst 0 q131077 2000 sl. 0 flows (1 buckets) sched 65541 weight 0 lmax 0 pri 0 droptail sched 65541 type FIFO flags 0x0 0 buckets 0 active 00006: 50.000 Mbit/s 0 ms burst 0 q131078 2000 sl. 0 flows (1 buckets) sched 65542 weight 0 lmax 0 pri 0 droptail sched 65542 type FIFO flags 0x0 0 buckets 0 active [25.07-RC][admin@felicity.local.lan]/root: dnctl queue list q00001 50 sl. 0 flows (1 buckets) sched 1 weight 0 lmax 0 pri 0 droptail q00002 50 sl. 0 flows (1 buckets) sched 2 weight 0 lmax 0 pri 0 droptail q00005 50 sl. 0 flows (1 buckets) sched 5 weight 0 lmax 0 pri 0 droptail q00006 50 sl. 0 flows (1 buckets) sched 6 weight 0 lmax 0 pri 0 droptail -
Yup we are aware of it.
Can we see the rules you are using to apply those Limiters?
Do you see states opened matching those rules?
-
@stephenw10 I have updated the post with the details you asked for (I hope...). Yes, there are states opened matching the rules.
As far as others' reports of limiters not working, they seems to suggests the rules that were working in 2.7.2 no longer works in 2.8.0, so that should be an easy test case to run. I've never run 2.7.2 but remember having limiters enabled at some point in 24.0x (not sure if I still have them in my defunct 24.11 setup)
-
@stephenw10
I have a nearly step-by-step, from a fresh install, how I duplicated the issue in my original post. I wiped out my lab, I recreated from that post (hopefully accurately). The testing & results should be pretty close. LMK if you're looking for something different.2.7.2
Rules:# User-defined rules follow anchor "userrules/*" pass out quick on { vtnet0 } $GWWAN_DHCP inet from <WAN IP> to any ridentifier 1752945005 keep state dnqueue( 1,2) label "USER_RULE: Bufferbloat" label "id:1752945005" label "gw:WAN_DHCP" pass in quick on $LAN inet from $LAN__NETWORK to any ridentifier 0100000101 keep state dnpipe ( 3,4) label "USER_RULE: Default allow LAN to any rule" label "id:0100000101" #Limiter Info:
Limiters: 00001: 20.000 Mbit/s 0 ms burst 0 q131073 50 sl. 0 flows (1 buckets) sched 65537 weight 0 lmax 0 pri 0 AQM CoDel target 1us interval 1us ECN sched 65537 type FIFO flags 0x0 0 buckets 0 active 00002: 100.000 Mbit/s 0 ms burst 0 q131074 50 sl. 0 flows (1 buckets) sched 65538 weight 0 lmax 0 pri 0 AQM CoDel target 1us interval 1us ECN sched 65538 type FIFO flags 0x0 0 buckets 0 active 00003: 2.000 Mbit/s 0 ms burst 0 q131075 50 sl. 0 flows (1 buckets) sched 65539 weight 0 lmax 0 pri 0 droptail sched 65539 type FIFO flags 0x0 0 buckets 0 active 00004: 5.000 Mbit/s 0 ms burst 0 q131076 50 sl. 0 flows (1 buckets) sched 65540 weight 0 lmax 0 pri 0 droptail sched 65540 type FIFO flags 0x0 0 buckets 0 active Schedulers: 00001: 20.000 Mbit/s 0 ms burst 0 q65537 50 sl. 0 flows (1 buckets) sched 1 weight 0 lmax 0 pri 0 droptail sched 1 type FQ_CODEL flags 0x0 0 buckets 0 active FQ_CODEL target 1us interval 1us quantum 1514 limit 10240 flows 1024 ECN Children flowsets: 1 00002: 100.000 Mbit/s 0 ms burst 0 q65538 50 sl. 0 flows (1 buckets) sched 2 weight 0 lmax 0 pri 0 droptail sched 2 type FQ_CODEL flags 0x0 0 buckets 0 active FQ_CODEL target 1us interval 1us quantum 1514 limit 10240 flows 1024 ECN Children flowsets: 2 00003: 2.000 Mbit/s 0 ms burst 0 q65539 50 sl. 0 flows (1 buckets) sched 3 weight 0 lmax 0 pri 0 droptail sched 3 type FIFO flags 0x0 0 buckets 0 active 00004: 5.000 Mbit/s 0 ms burst 0 q65540 50 sl. 0 flows (1 buckets) sched 4 weight 0 lmax 0 pri 0 droptail sched 4 type FIFO flags 0x0 0 buckets 0 active Queues: q00001 50 sl. 0 flows (1 buckets) sched 1 weight 0 lmax 0 pri 0 AQM CoDel target 1us interval 1us ECN q00002 50 sl. 0 flows (1 buckets) sched 2 weight 0 lmax 0 pri 0 AQM CoDel target 1us interval 1us ECNInterpreted Rules:
@84 anchor "userrules/*" all [ Evaluations: 73 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 9606 State Creations: 0 ] [ Last Active Time: N/A ] @85 pass out quick on vtnet0 route-to (vtnet0 <WAN Gateway>) inet from <WAN IP> to any flags S/SA keep state label "USER_RULE: Bufferbloat" label "id:1752945005" label "gw:WAN_DHCP" ridentifier 1752945005 dnqueue(1, 2) [ Evaluations: 73 Packets: 14677 Bytes: 15410930 States: 20 ] [ Inserted: uid 0 pid 9606 State Creations: 51 ] [ Last Active Time: Sat Jul 19 18:14:14 2025 ] @86 pass in quick on vtnet1 inet from <LAN__NETWORK:1> to any flags S/SA keep state label "USER_RULE: Default allow LAN to any rule" label "id:0100000101" ridentifier 100000101 dnpipe(3, 4) [ Evaluations: 22 Packets: 14738 Bytes: 15555983 States: 15 ] [ Inserted: uid 0 pid 9606 State Creations: 22 ] [ Last Active Time: Sat Jul 19 18:14:14 2025 ]Example states:
all tcp 23.239.29.5:443 <- 192.168.1.100:41090 ESTABLISHED:ESTABLISHED [3531538492 + 2147156224] wscale 7 [440337916 + 2147025152] wscale 7 age 00:00:34, expires in 23:59:27, 15:18 pkts, 2254:10378 bytes, rule 86, dummynet pipe (3 4), log id: 09f07b6800000000 creatorid: ae2f1b15 origif: vtnet1 all tcp <WAN IP>:1291 (192.168.1.100:41090) -> 23.239.29.5:443 ESTABLISHED:ESTABLISHED [440337916 + 2147025152] wscale 7 [3531538492 + 2147156224] wscale 7 age 00:00:34, expires in 23:59:27, 15:18 pkts, 2254:10378 bytes, rule 85, log id: 0af07b6800000000 creatorid: ae2f1b15 route-to: <WAN Gateway>@vtnet0 origif: vtnet02.8.0
Rules:# User-defined rules follow anchor "userrules/*" pass out quick on { vtnet0 } $GWWAN_DHCP inet from <WAN IP> to any ridentifier 1752945012 keep state dnqueue( 1,2) label "USER_RULE: Bufferbloat" label "id:1752945012" label "gw:WAN_DHCP" pass in quick on $LAN inet from $LAN__NETWORK to any ridentifier 0100000101 keep state dnpipe ( 3,4) label "USER_RULE: Default allow LAN to any rule" label "id:0100000101" #Limiter Info:
Limiters: 00001: 20.000 Mbit/s 0 ms burst 0 q131073 50 sl. 0 flows (1 buckets) sched 65537 weight 0 lmax 0 pri 0 AQM CoDel target 1us interval 1us ECN sched 65537 type FIFO flags 0x0 0 buckets 0 active 00002: 100.000 Mbit/s 0 ms burst 0 q131074 50 sl. 0 flows (1 buckets) sched 65538 weight 0 lmax 0 pri 0 AQM CoDel target 1us interval 1us ECN sched 65538 type FIFO flags 0x0 0 buckets 0 active 00003: 2.000 Mbit/s 0 ms burst 0 q131075 50 sl. 0 flows (1 buckets) sched 65539 weight 0 lmax 0 pri 0 droptail sched 65539 type FIFO flags 0x0 0 buckets 0 active 00004: 5.000 Mbit/s 0 ms burst 0 q131076 50 sl. 0 flows (1 buckets) sched 65540 weight 0 lmax 0 pri 0 droptail sched 65540 type FIFO flags 0x0 0 buckets 0 active Schedulers: 00001: 20.000 Mbit/s 0 ms burst 0 q65537 50 sl. 0 flows (1 buckets) sched 1 weight 0 lmax 0 pri 0 droptail sched 1 type FQ_CODEL flags 0x0 0 buckets 0 active FQ_CODEL target 1us interval 1us quantum 1514 limit 10240 flows 1024 ECN Children flowsets: 1 00002: 100.000 Mbit/s 0 ms burst 0 q65538 50 sl. 0 flows (1 buckets) sched 2 weight 0 lmax 0 pri 0 droptail sched 2 type FQ_CODEL flags 0x0 0 buckets 0 active FQ_CODEL target 1us interval 1us quantum 1514 limit 10240 flows 1024 ECN Children flowsets: 2 00003: 2.000 Mbit/s 0 ms burst 0 q65539 50 sl. 0 flows (1 buckets) sched 3 weight 0 lmax 0 pri 0 droptail sched 3 type FIFO flags 0x0 0 buckets 0 active 00004: 5.000 Mbit/s 0 ms burst 0 q65540 50 sl. 0 flows (1 buckets) sched 4 weight 0 lmax 0 pri 0 droptail sched 4 type FIFO flags 0x0 0 buckets 0 active Queues: q00001 50 sl. 0 flows (1 buckets) sched 1 weight 0 lmax 0 pri 0 AQM CoDel target 1us interval 1us ECN q00002 50 sl. 0 flows (1 buckets) sched 2 weight 0 lmax 0 pri 0 AQM CoDel target 1us interval 1us ECNInterpreted Rules:
@85 anchor "userrules/*" all [ Evaluations: 66 Packets: 0 Bytes: 0 States: 0 ] [ Inserted: uid 0 pid 0 State Creations: 0 ] [ Last Active Time: N/A ] @86 pass out quick on vtnet0 route-to (vtnet0 <WAN Gateway>) inet from <WAN IP> to any flags S/SA keep state (if-bound) label "USER_RULE: Bufferbloat" label "id:1752945012" label "gw:WAN_DHCP" ridentifier 1752945012 dnqueue(1, 2) [ Evaluations: 66 Packets: 163790 Bytes: 206160499 States: 21 ] [ Inserted: uid 0 pid 0 State Creations: 41 ] [ Last Active Time: Sat Jul 19 18:15:26 2025 ] @87 pass in quick on vtnet1 inet from <LAN__NETWORK:1> to any flags S/SA keep state (if-bound) label "USER_RULE: Default allow LAN to any rule" label "id:0100000101" ridentifier 100000101 dnpipe(3, 4) [ Evaluations: 25 Packets: 154598 Bytes: 192395490 States: 14 ] [ Inserted: uid 0 pid 0 State Creations: 23 ] [ Last Active Time: Sat Jul 19 18:15:26 2025 ]Example states:
vtnet1 tcp 23.239.29.5:443 <- 192.168.1.100:41256 ESTABLISHED:ESTABLISHED [4281932605 + 64128] wscale 7 [3565815079 + 63872] wscale 7 age 00:00:34, expires in 23:59:27, 15:18 pkts, 2255:10378 bytes, rule 87, dummynet pipe (3 4) id: d9f57b6800000000 creatorid: 9d03805d vtnet0 tcp <WAN IP>:42673 (192.168.1.100:41256) -> 23.239.29.5:443 ESTABLISHED:ESTABLISHED [3565815079 + 63872] wscale 7 [4281932605 + 64128] wscale 7 age 00:00:34, expires in 23:59:27, 15:18 pkts, 2255:10378 bytes, rule 86 id: daf57b6800000000 creatorid: 9d03805d route-to: <WAN Gateway>@vtnet0 -
The major difference there is the state binding. Note they are bound to
allin 2.7.2 but interface bound in 2.8.0.Did you try reverting that change in 2.8.0 to see if that makes any difference?
The other thing is that I expect to see the limiters in the reverse order on the outbound rule but it could be you're just testing that way? That might explain one of the test failures you saw above.
Also that's the non-policy routing situation?
-
@stephenw10 said in [2.8.1.b] Multiple limiter issue:
The major difference there is the state binding. Note they are bound to
allin 2.7.2 but interface bound in 2.8.0.Did you try reverting that change in 2.8.0 to see if that makes any difference?
It did not make a difference between
Interface Bound StatesandFloating Stateson 2.8.0.vtnet1 tcp 23.239.29.5:443 <- 192.168.1.100:42446 ESTABLISHED:ESTABLISHED [1351492337 + 63360] wscale 7 [4004094591 + 63616] wscale 7 age 00:00:39, expires in 23:59:58, 26:28 pkts, 3531:19177 bytes, rule 87, dummynet pipe (3 4) id: df107d6800000000 creatorid: 9d03805d vtnet0 tcp <WAN IP>:17951 (192.168.1.100:42446) -> 23.239.29.5:443 ESTABLISHED:ESTABLISHED [4004094591 + 63616] wscale 7 [1351492337 + 63360] wscale 7 age 00:00:39, expires in 23:59:58, 26:28 pkts, 3531:19177 bytes, rule 86 id: e0107d6800000000 creatorid: 9d03805d route-to: <WAN Gateway>@vtnet0and
all tcp 23.239.29.5:443 <- 192.168.1.100:55138 ESTABLISHED:ESTABLISHED [2584166382 + 63360] wscale 7 [3625120434 + 63488] wscale 7 age 00:00:40, expires in 24:00:00, 40:45 pkts, 4557:37927 bytes, rule 87, dummynet pipe (3 4) id: 04137d6800000000 creatorid: 9d03805d origif: vtnet1 all tcp <WAN IP>:49985 (192.168.1.100:55138) -> 23.239.29.5:443 ESTABLISHED:ESTABLISHED [3625120434 + 63488] wscale 7 [2584166382 + 63360] wscale 7 age 00:00:40, expires in 24:00:00, 40:45 pkts, 4557:37927 bytes, rule 86 id: 05137d6800000000 creatorid: 9d03805d route-to: <WAN Gateway>@vtnet0 origif: vtnet0The other thing is that I expect to see the limiters in the reverse order on the outbound rule but it could be you're just testing that way? That might explain one of the test failures you saw above.
If I understand this, the labeling of my limiter matches the GUI. GUI option is labeled
In / Out Pipeso I have the first one labeledWAN-in-q&LAN-in, the secondWAN-out-q&LAN-out. I verified bandwidths amounts set in the limiters and the order in the rules are correct and consistent between the two versions.Also that's the non-policy routing situation?
I'm not PBRing in this case. At one site, I have 2 WANs and PBR some devices when the primary fails. There are no limiters on any PBR rule. The floating rule on the primary WAN has the same Bufferbloat limiters. The other site has a single WAN and no PBR.
-
@NWOSwamp said in [2.8.1.b] Multiple limiter issue:
It did not make a difference between Interface Bound States and Floating States on 2.8.0.
Ok good to know.
@NWOSwamp said in [2.8.1.b] Multiple limiter issue:
GUI option is labeled In / Out Pipe so I have the first one labeled WAN-in-q & LAN-in, the second WAN-out-q & LAN-out.
But it also says:
If creating a floating rule, if the direction is In then the same rules apply, if the direction is Out the selections are reversed,
And here the rule is indeed a floating OUT rule so for the WAN side they should be reversed. As unintuitive as that is! -
@stephenw10 said in [2.8.1.b] Multiple limiter issue:
But it also says:
If creating a floating rule, if the direction is In then the same rules apply, if the direction is Out the selections are reversed,
And here the rule is indeed a floating OUT rule so for the WAN side they should be reversed. As unintuitive as that is!Yep, thanks. Get it and am aware of that. I never remember which way is straight and which is reversed. To make it easier for my feeble memory, if I need to edit or recreate the rule, is to follow the label. The limiter has the correct bandwidth. I donno, makes sense to me but definitely see it confuses anyone else. Maybe there's an easier way...
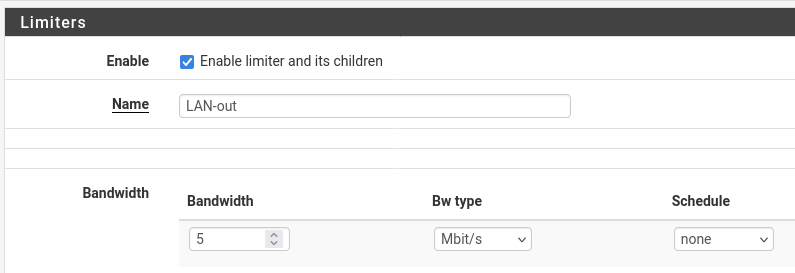
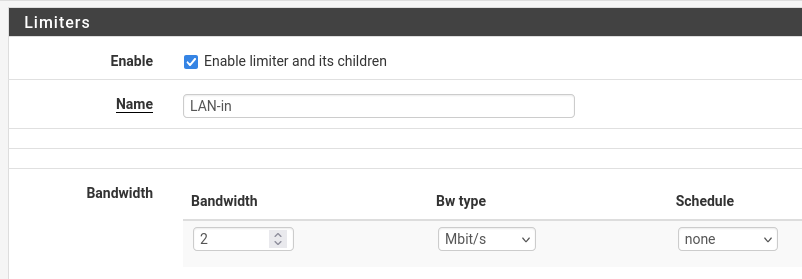
-
Ah OK I see, the names threw me!
-
Same behavior is present in the latest RC (2.8.1.r.20250808.1925).
-
I suspect the root cause here is the same as this: https://redmine.pfsense.org/issues/15770