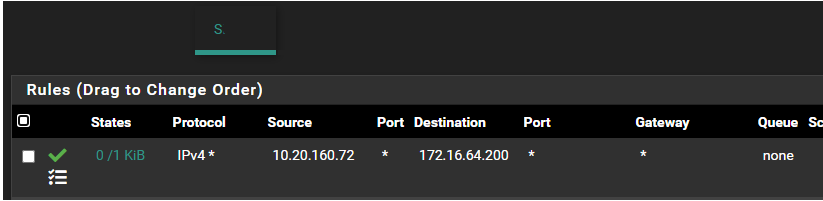
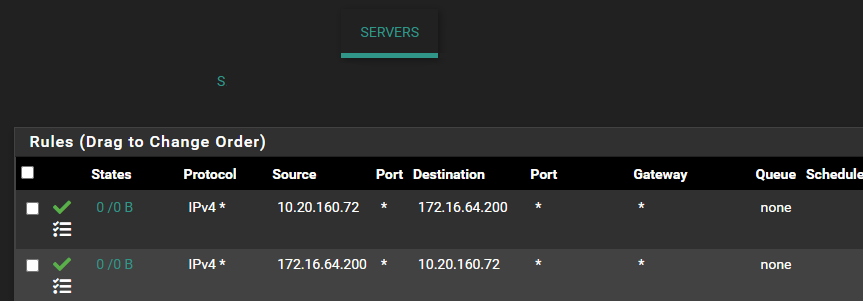
Intervlan traffic being blocked
-
What about the Servers interface though? The 172 network.
-
@planedrop For the route
-
@greatbush I think we are getting closer, if that is your entire routing table, then pfSense does not have a clue where to route the 172 network, so it's just going to send it to it's default route which is likely your gateway, unless I am misunderstanding something about your configuration.
Is the Servers interface properly configured? Not the S but the Servers one.
-
@greatbush The server network is fine. It can reach my other subnets without any issue. Hmm. I don't know if this is going to help. the 10.20.160.x was the network at another site and an ipsec tunnel was setup for that site.
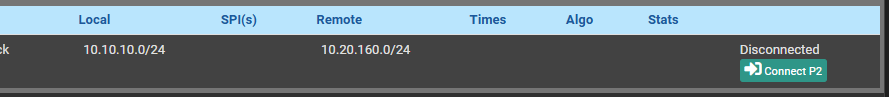
I don't know if this might be causing issues. -
@planedrop Server network
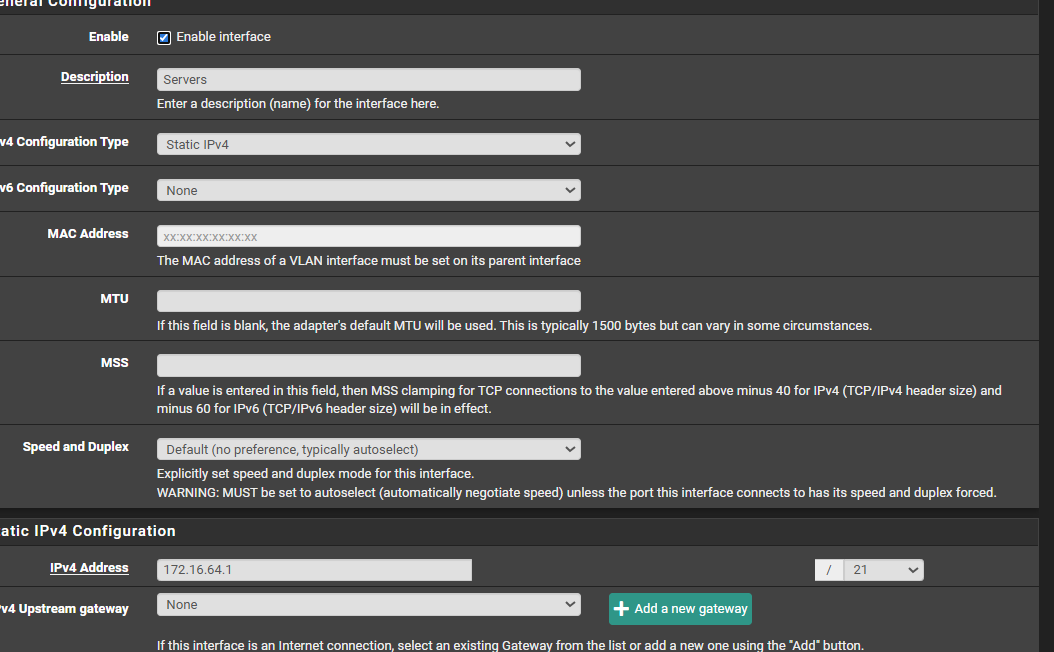
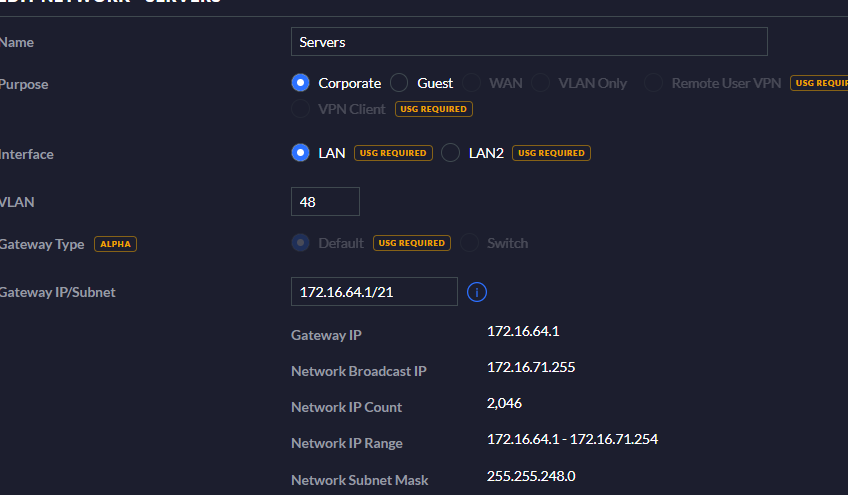
-
@greatbush I don't think IPsec is the issue here, you would see the ICMP responses on the Servers interface if that was the case, they just wouldn't route back to the S interface.
Again though, it looks to me like pfSense doesn't have a routing table entry for the 172. network so those echo request are never going to get to a device on any network, it'll just send them through it's default gateway, which is presumably your internet provider.
Also, why are you configuring actual networks on the Unifi side? Those should be VLAN only networks since you're using a 3rd party gateway (pfSense) for them. I don't think that is what is breaking things here but was worth mentioning.
I did just see that you're using Broadcom NICs though, check out this just in case cuz it might affect pings: https://docs.netgate.com/pfsense/en/latest/hardware/tune.html#packet-loss-with-many-small-udp-packets:~:text=and%20disable%20msix.-,Packet%20loss%20with%20many%20(small)%20UDP%20packets,-%C2%B6
-
@greatbush route for server
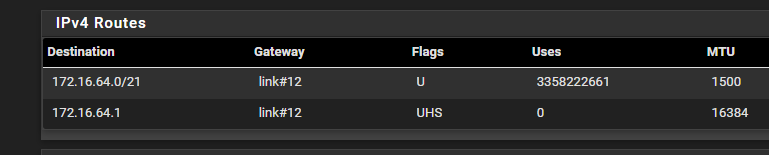
I inherited the network so i am going with the flow. I have made the changes and its the same result for the ping. I was able to get the ping to work last week friday but i was not keeping track on the changes i was making. Will creating a static route help? I read that this isn't needed since pfsense knows the route
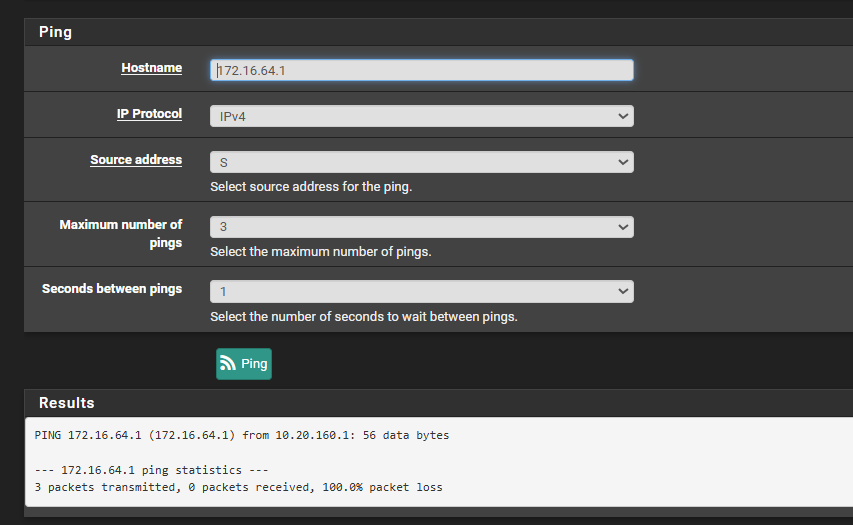
-
@greatbush on your sniff - what is the mac address - have no idea why you searched for 10.20.x.x as a src IP?
-
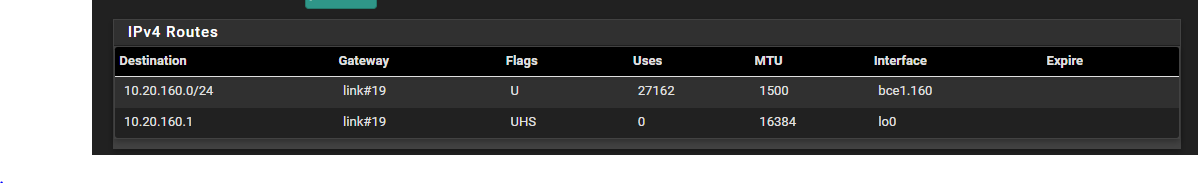
@greatbush There is no way your system is working how you think it is - where are the rest of your networks??
Here is a routing table on pfsense with multiple interfaces.
Here is a snip of mine.
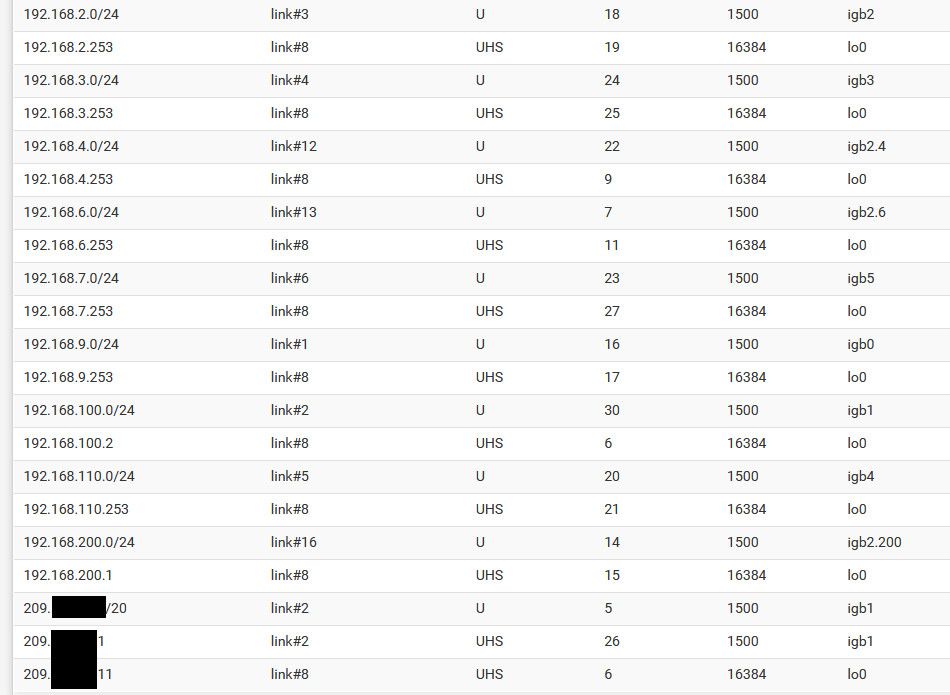
See multiple local interface, some native some vlans - notice a wan route - etc..
How would pfsense be doing any routing if all it shows is 1 network??
edit: oh I snipped off the top part showing the default route - see how it points to an IP on my wan interface 209.x.x.x network
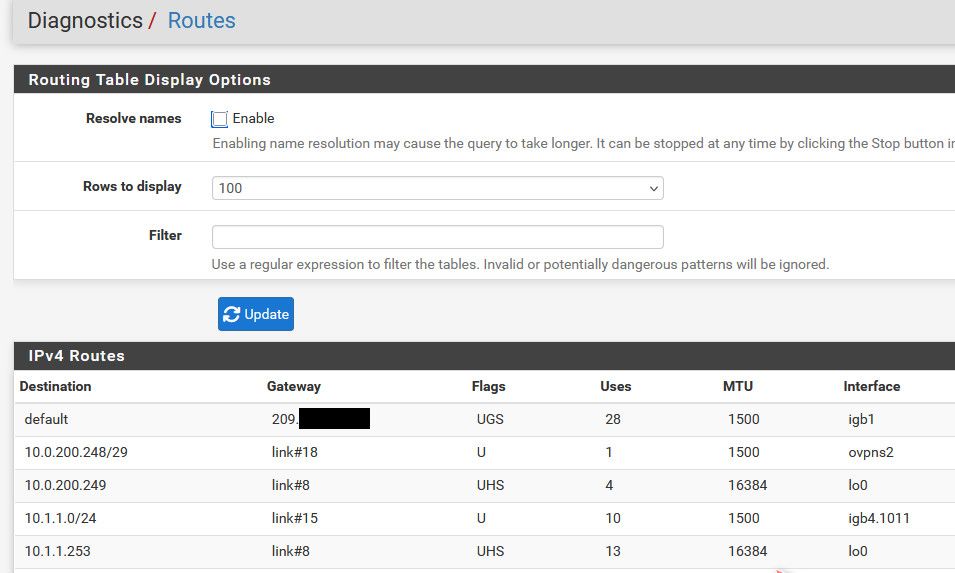
How would pfsense route between 2 networks when it doesn't even show that its connected to it in the routing table?
-
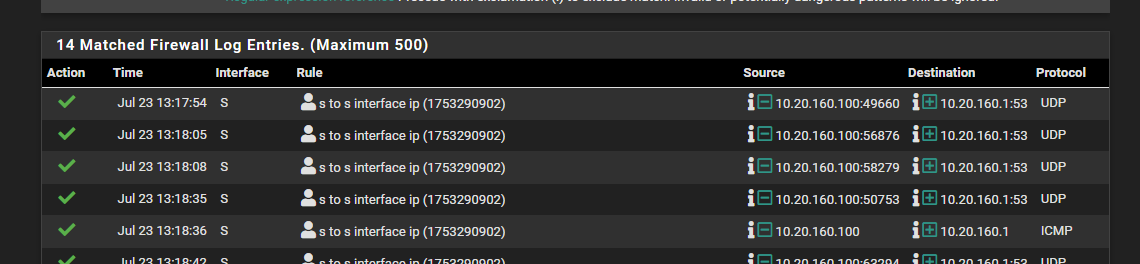
@johnpoz the mac address is 98:fc:84:d1:db:44.
I used the filer 'eth.addr == 98:fc:84:d1:db:44' and searched the other pcap files but the only thing that shows up is the echo ping request.
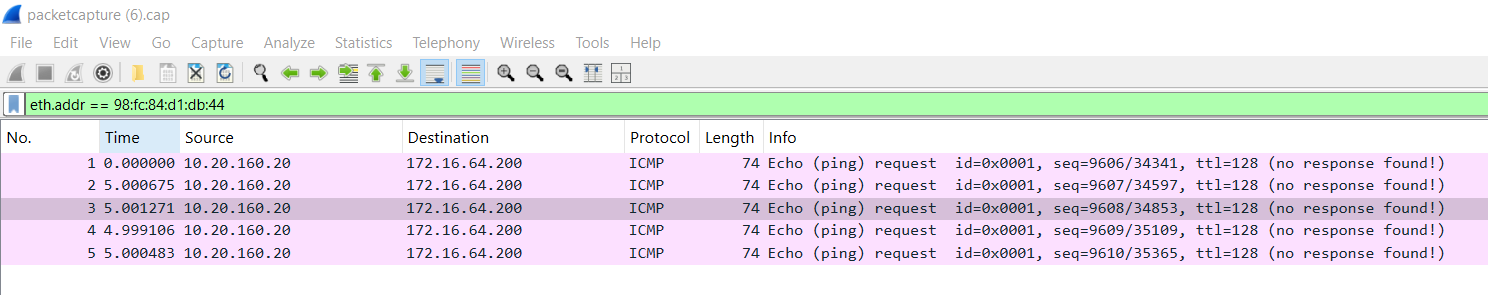
For some reason its not reach the 172.16.64.1 interface.
-
@greatbush Can you send us your entire routing table under Diagnostics > Routes?
No need to send the IPv6 one but the IPv4 one would be good.
Since the allow rule is in place, and it doesn't sound like any floating rules are being used, I'm thinking this is a routing issue.
-
@greatbush Please show the pcap from pinging pfsense IP address on the server network?
We know you can not get to this server - but you also said you can not even ping pfsense IP address on the server network..
And yes like to see your full route table - from what you posted no there is no way your going to get to this other network because from your routing table pfsense doesn't even think its connected to this network.
What is this a about a ipsec tunnel - this 10.20 network is via a ipsec tunnel? What about your 2 unifi switches - no where did you say this network was from other site via a tunnel??
-
@johnpoz @planedrop I will send you a pm
-
@johnpoz The network was at another site. I tore it down and rebuilt the config at my current location.
-
@greatbush said in Intervlan traffic being blocked:
For some reason its not reach the 172.16.64.1 interface.
that is pinging the server at .200 - ping pfsense IP on the server network 172.16.64.1 I believe is what you have posted.
There is a huge difference between not getting an answer from server, and not being able to ping pfsense IP on that network.
All kinds of other issues could be going on to why that server doesn't answer - but pfsense no answering when you ping one of its IPs and your firewall rules allow it, and traffic gets to pfsense is something going on in pfsense.
-
@johnpoz i have tried pinging both .200 and .64.1 and i got the exact same result despite me adding rules for both on the S interface. Pfsense isn't dying, right?
-
@greatbush I have no idea what is going on to be honest - if your rules allow it, and traffic is getting there.. you should get an answer.
Your routing table shows the interfaces there.. Only thing that comes to mind is something wrong with the tag. But your doing the packet capture on the actual vlan interface right. Not the parent interface.
You can ping pfsense IP on the S interface right?
-
@johnpoz yep. my test pc can ping its pfsense interface ip
-
-
@greatbush but that test PC that is different IP 160.100 can not ping the server IP of 64.1 ?
You changed the rules to any S subnet to Server subnet I believe. So yeah you should be able to ping the pfsense server interface IP.
Can we see the full ruleset on the S interface of pfsense.