NAT Reflection Issue with Dual WAN Setup in pfSense 2.7.2
-
Hi everyone,
I'm currently running pfSense 2.7.2 with a dual WAN setup:
WAN1: Static IP
WAN2: DHCP
Gateway failover and redundancy are working fine. However, I'm facing an issue with NAT reflection.I’ve published a web service (e.g., netgate.com) using NAT port forwarding. External access works perfectly — users can reach the service via the domain name. But internally, when I try to access netgate.com, it fails unless I use the internal IP address directly.
Initially, I created the NAT rules with “Filter rule association” set to “Add associated filter rule” (the default). But when I changed it to “Pass” or “None” and manually created the corresponding firewall rule, internal access started working as expected.
So my question is:
- Is this behavior expected?
- Has anyone else experienced this issue?
- Is manually creating the firewall rule the correct solution, or is there a better way to handle NAT reflection in dual WAN setups?
Any feedback or insights would be greatly appreciated!
Thanks in advance.
-
@TonyArizin said in NAT Reflection Issue with Dual WAN Setup in pfSense 2.7.2:
Initially, I created the NAT rules with “Filter rule association” set to “Add associated filter rule”
This only adds a rule to the WAN. For access from inside your network using NAT reflection, you have to add a rule manually to the internal interface.
-
The LAN rule already has the source set to all and all ports going out are open.
-
@TonyArizin
The destination has to be the local IP of the server, not the public one, since this is, what you want to access in fact. -
First of all, thank you for your answer.
So, does that mean that in the LAN firewall rule, the source should be any and the destination should be the internal address of the web publishing server?
In addition, there is already a LAN firewall rule with the source set to any and the destination set to any. Does that mean that I need to add what you mentioned in addition to this?
-
The default LAN to any rule should pass that traffic.
What rule did you add exactly?
-
protocol is ipv4*
source is *(any)
port is also *(any)
destination *(any)
I created a rule like this, but the only special thing is that I set the gateway to be a gateway group. -
@TonyArizin
Stating a gateway turns the rule into a policy-routing rule. Then all matching traffic is forced to the gateway.
Hence this rule doesn't allow access to internal destinations. -
Yup, that^

-
First of all, thank you for your answer.
Then, if I specify a gateway other than the default, do I need to create a LAN rule for it? Can you show me an example of a LAN rule that I need to create?
-
Yes if you are policy routing traffic from LAN via a specific gateway you need another rule above that to allow traffic to other local destinations that avoids policy routing.
So for example:
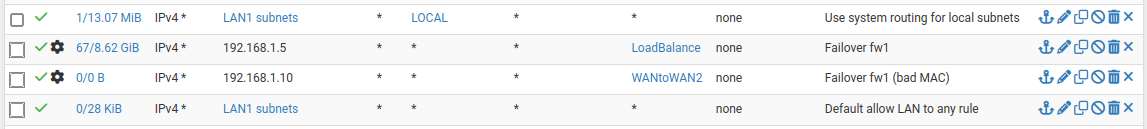
There I'm using an alias 'LOCAL' that contains all the subnets I need to bypass policy routing for.
-
I understand.
I think you set the source to LAN subnets and the destination to 'LOCAL', but can you actually use the internal IP of the web publishing servers I mentioned as an alias for 'LOCAL'?
-
Yes as long as it matches the traffic against a rule that's above the policy routing rule that will work.