Using VTI IPsec to bypass managed office NAT
-
Hello,
In April this year we moved into a managed office to make life easier on us, as part of the new office we are unable to run our own WiFi and the wall sockets dropped me onto a network where I could see other devices in other offices. This did not fill me with confidence so I looking into my options and pfSense was recommended to allow me to place a block between my office devices and the office LAN at large, this has been in place now for several months with no issues.
Now to the tricky part - as part of my backup routine for the 3 webservers that I look after I need to to access the QNAP device that is in the office behind the pfsense network. As a result I spun up a VPS from IONOS, and installed pfSense on it to act as a accessible end-point for FTP.
The network running 2.8.0 on both sites and they have the following config:
Site 1 - Remote Site (IONOS)
Internal IP Range: 10.80.1.0/24
IPsec VTI: 10.80.99.1
OpenVPN: 10.80.98.0/24Site 2 - Local Site (Managed Office)
Internal IP Range: 10.80.2.0/24
IPsec VTI: 10.80.99.2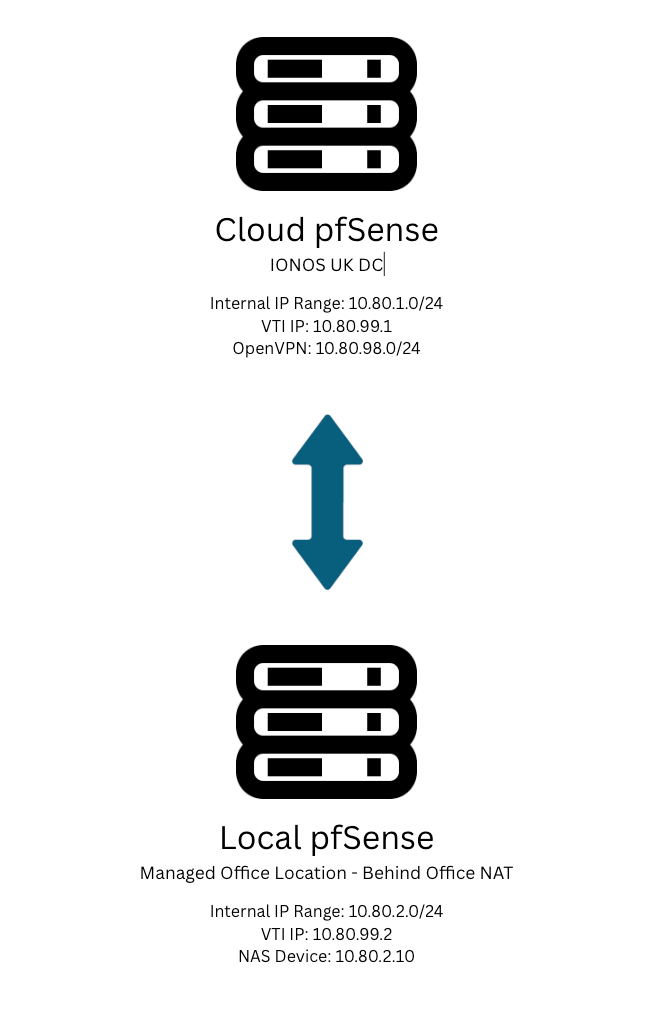
I have three objectives that I would like to achieve
-
Have any incoming FTP activities come via site 1 and be forwarded onto the QNAP NAS on site 2 and have the QNAP reply via site 1
-
Be able to access both site 1 & site 2's internal networks from OpenVPN
-
If site 3 does come online I would like to be able to access all three subnets using site 1 as the hub, and sites 2 & 3 as spokes.
Note I did have this working but something happened to the site 2 machine and I didn't have a recent backup and when I performed a clean install again I was unable to get it to play ball again. Now have some free time I would like to get it back up and running.
Currently the IPsec VPN is up, P2 is installed on both sides of the connction and from Gateways I can see the Gateways are both online with no packet loss. If I SSH onto Site 1 I am able to ping the QNAP device with no issues, and from my mac on site 2 I am able to ping the remote pfsense local IP, along with being able to ping both gateways from either end.
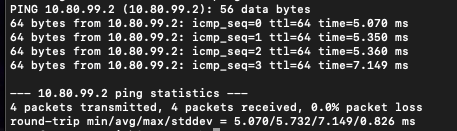
Site 1 - Ping Results & Gateway Monitoring
Gateway to site 2 is up and running with a roundtrip of around 60ms
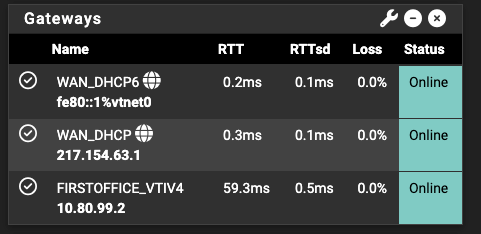
Pinging site 2 pfSense box showing a similar average:
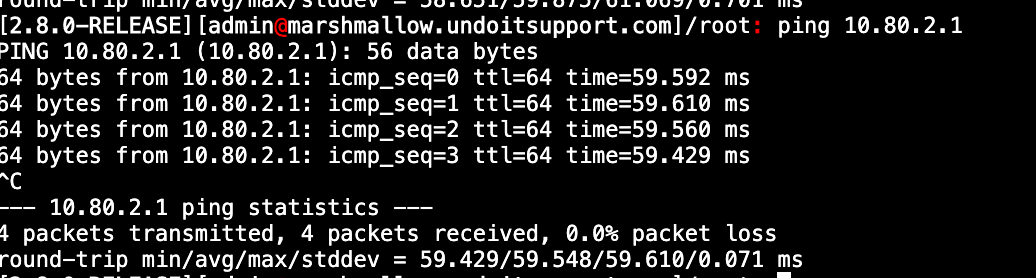
Ping site 1 Gateway IP:
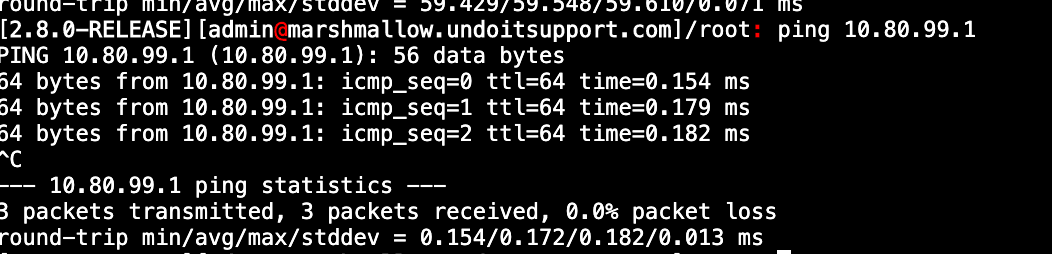
Ping site 2 Gateway IP:
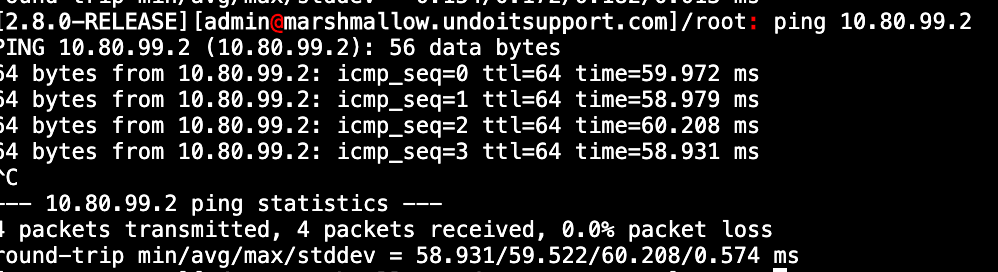
Site 2 - Ping Results & Gateway Monitoring
Gateway to site 1 is up and running with a roundtrip of 60ms:
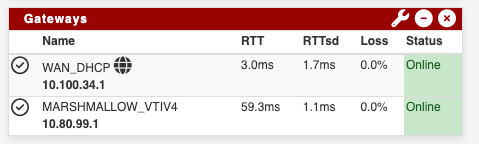
Site 2 - Ping from Site 2 to Site Gateway:
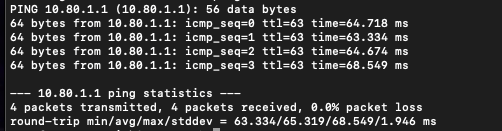
Site 2 - Ping Site 2 Gateway
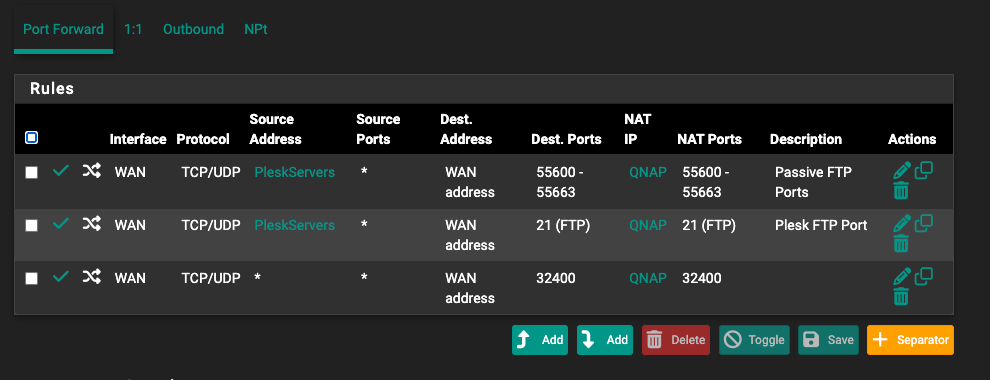
Site 1 - Firewall / NAT / Rules
This is going to be the entry point to the network this is where I have created the Port Forwards for the FTP access onto the QNAP on site 2.
Port Forward Rules:
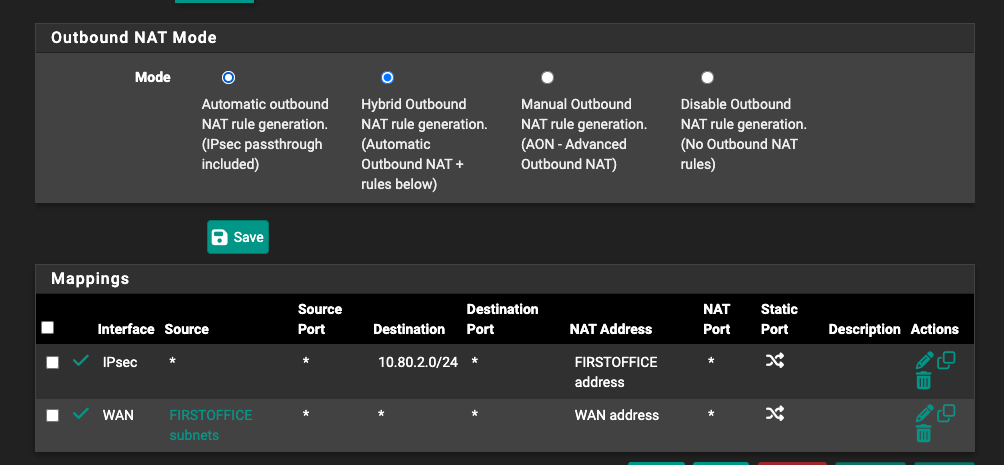
Outbound NAT is set to Hybrid and I have added the following two rules that I was advised in my previous post:
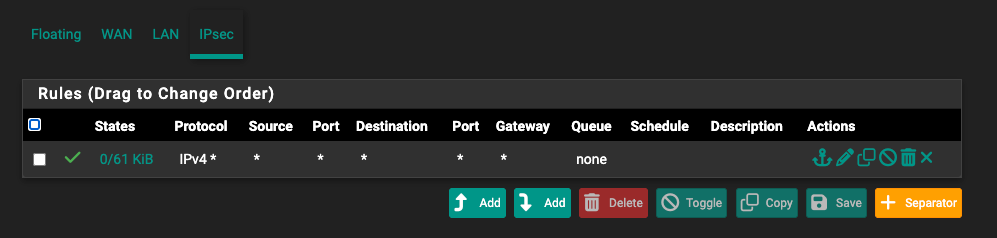
IPsec Firewall rules:
Site 2 - Firewall / NAT / Rules
I have configured the QNAP device to use Site 1 as its remote gateway so that all traffic sent by the device will get send over the link and exit from site 1.
Outbound NAT is set to Hybrid and I have added the rule that I was advised in my previous post.
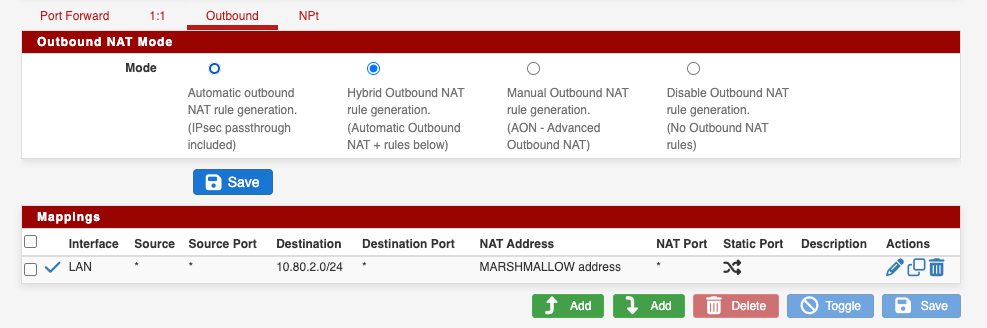
LAN Firewall rules to route all QNAP traffic via the VTI Link:
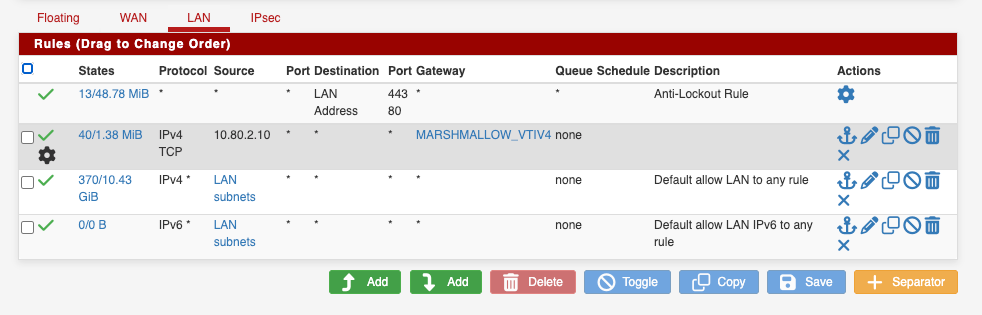
IPsec Firewall rules
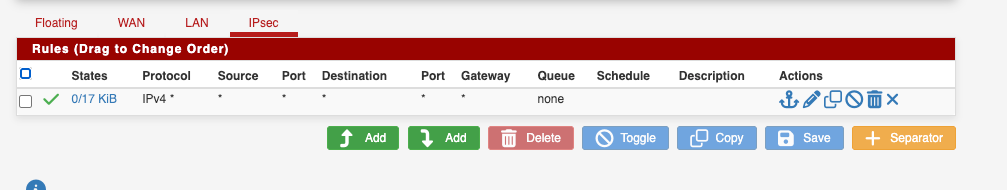
When trying to access the FTP from the Plesk Servers I am getting the error:

I hope that this all makes sense and someone can help me figure it out before I pull my hair out in frustration.
Many thanks
Stan
-