NTP Service: How to allow 'ntpq' queries to the server without requiring authentication
-
I use the NTP service on pfSense for my local network. It is also exposed on the Internet as part of pool.ntp.org. I have suitable defaults in place under ACLs, plus slightly more permissive ones for my local network. That is all working fine but one thing is bugging me; I want to be able to use ntpq either on the pfSense system itself, or from a system in the local network, to issue various queries to examine server stats (for example the ntpq 'ifstats' query). However, some of these queries require authentication and I am at a loss as to how to overcome this.
I tried setting up NTP keys in the main NTP service screen but I really don't think that is what is required (those seem to be for the pfSense NTP client to authenticate itself to an upstream server).
Is there any ntpd configuration option to disable client authentication for all operations, ideally for just specific clients, such that all ntpq queries will work?
-
@ChrisJenk said in NTP Service: How to allow 'ntpq' queries to the server without requiring authentication:
. However, some of these queries require authentication and I am at a loss as to how to overcome this.
could you give an example of query your wanting to do that requires auth.. I run ntpq on pfsense and not sure what your trying to query that wouldn't work?
-
@johnpoz Having played more with it it seems like only the ntpq 'ifstats' command needs authentication (no idea why). While the output from that would be interesting/useful I guess I can live without it...
-
@ChrisJenk hmmm
ifstats
Display statistics for each local network address. Authentication is required.To be honest I have never used that - I will take a look see..
And yeah if for sure wants auth ;)
[24.11-RELEASE][admin@sg4860.home.arpa]/root: ntpq ntpq> ifstats Keyid: -
@ChrisJenk here you go..
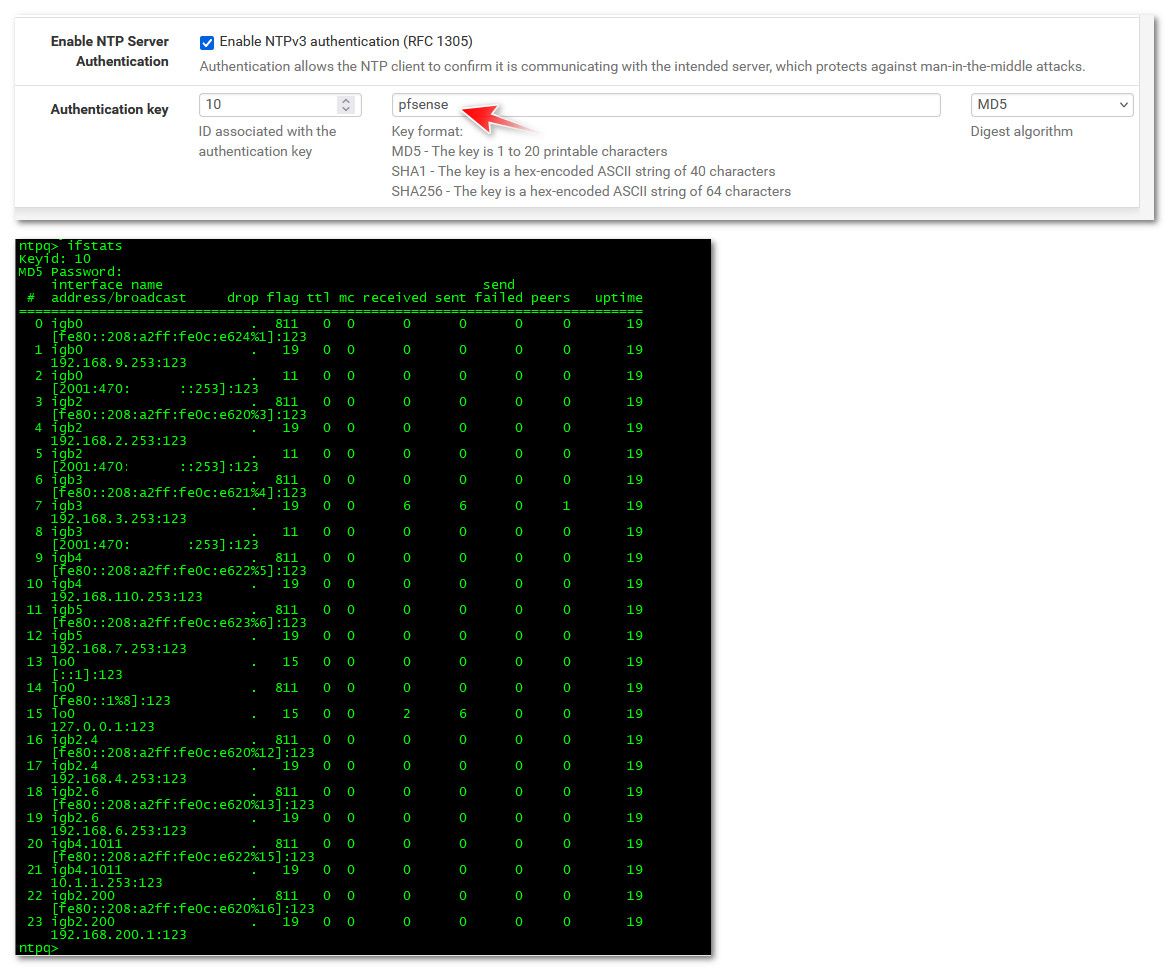
I snipped out my public IPv6 that were listed.
I am not sure what else this might cause you a problem with if your syncing other servers to your pfsense ntp.. I just have pfsense use my ntp server I run on a pi. And most all clients sync with my pi server.. but I do show ntp on pfsense still syncing and clients can still query it.
You can use any password for your key that you want, and should be able to change the digest used.. When I ran ntpq and it asks for the password, just type in the password you used, in my case pfsense was my password I set.
I had restarted ntp - which would explain the low numbers. They are going up
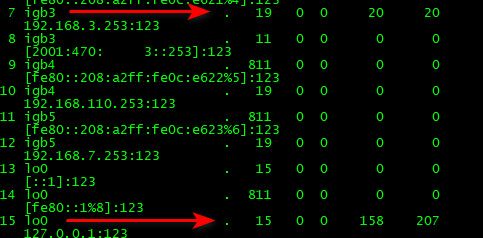
igb3 is the interface pfsense uses to talk to my pi ntp server.
edit:
I am not really user of auth of any kind with ntp.. All my clients on my server talk to my pi ntp server, and psfense syncs off that - I see no reason for "auth" - but I would think from the quick read I did on how to setup the keys, etc. I would think if your going to use pfsense use the gui to setup authing to other servers with ntp on pfsense you should be able to setup more than 1 in the gui. -
@johnpoz Well, that is weird. That is exactly what I did earlier, except that I used an MD5 digest value (created by 'ntp-keygen') as the key and that didn't work. I just tried it again using some easy to remember password (different to yours) and now it works.
For me this is the only reason to use 'auth' but luckily it doesn't interfere with normal NTP client operation (I just verified that so I'll stick with this now.
Cheers.
-
@ChrisJenk my understanding is it creates a md5, or whatever digest you chose from that password you put in, so yeah if you put in some md5 value already and then did an md5 on it again you could prob have a mismatch happen?
But for example if look in the ntp conf in /var/etc, you will see points to key file and an ID number
# Authentication settings keys /var/etc/ntp.keys trustedkey 10 requestkey 10 controlkey 10Then in that key file it just has the password I put in.
[24.11-RELEASE][admin@sg4860.home.arpa]/var/etc: cat ntp.keys 10 MD5 pfsense [24.11-RELEASE][admin@sg4860.home.arpa]/var/etc:Not sure what ntp-keygen produces. But if not 1 to 20 printable chars it might not work.
Key format:
MD5 - The key is 1 to 20 printable charactersWhen I run ntp-keygen it outputs this
[24.11-RELEASE][admin@sg4860.home.arpa]/var/etc: ntp-keygen Using OpenSSL version OpenSSL 3.0.14 4 Jun 2024 Using host sg4860.home.arpa group sg4860.home.arpa Generating RSA keys (512 bits)... RSA 0 6 214 1 63 128 3 1 2 Generating new host file and link ntpkey_host_sg4860.home.arpa->ntpkey_RSAhost_sg4860.home.arpa.3962527817 Using host key as sign key Generating new certificate sg4860.home.arpa RSA-MD5 X509v3 Basic Constraints: critical,CA:TRUE X509v3 Key Usage: digitalSignature,keyCertSign Generating new cert file and link ntpkey_cert_sg4860.home.arpa->ntpkey_RSA-MD5cert_sg4860.home.arpa.3962527817Not sure how you would use that in the ntpq command where it asks for a password.
-
From the ntp doc:
8. Authentication Four commands require authentication to the server: config-from-file, config, ifstats, and reslist. An authkey file must be in place and a control key declared in ntp.conf for these commands to work. If you are running as root or otherwise have read access to the authkey and ntp.conf file, ntpq will mine the required credentials for you. Otherwise, you will be prompted to enter a key ID and password. Credentials once entered, are retained and used for the duration of your ntpq session.