SSH "attacks"
-
I just setup a new router from a backup of my old device -- I was looking at logs to be sure things were running smoothly.
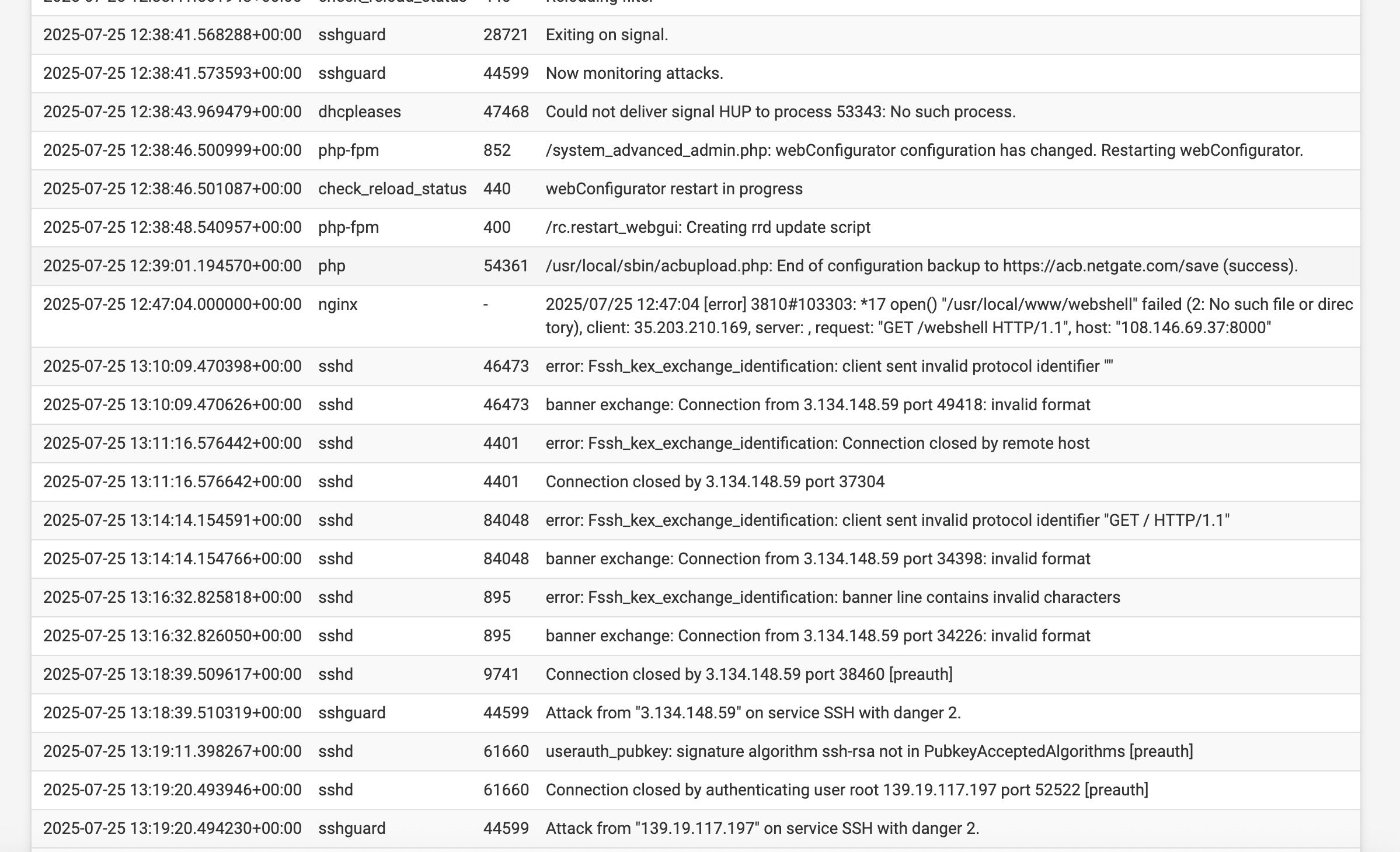
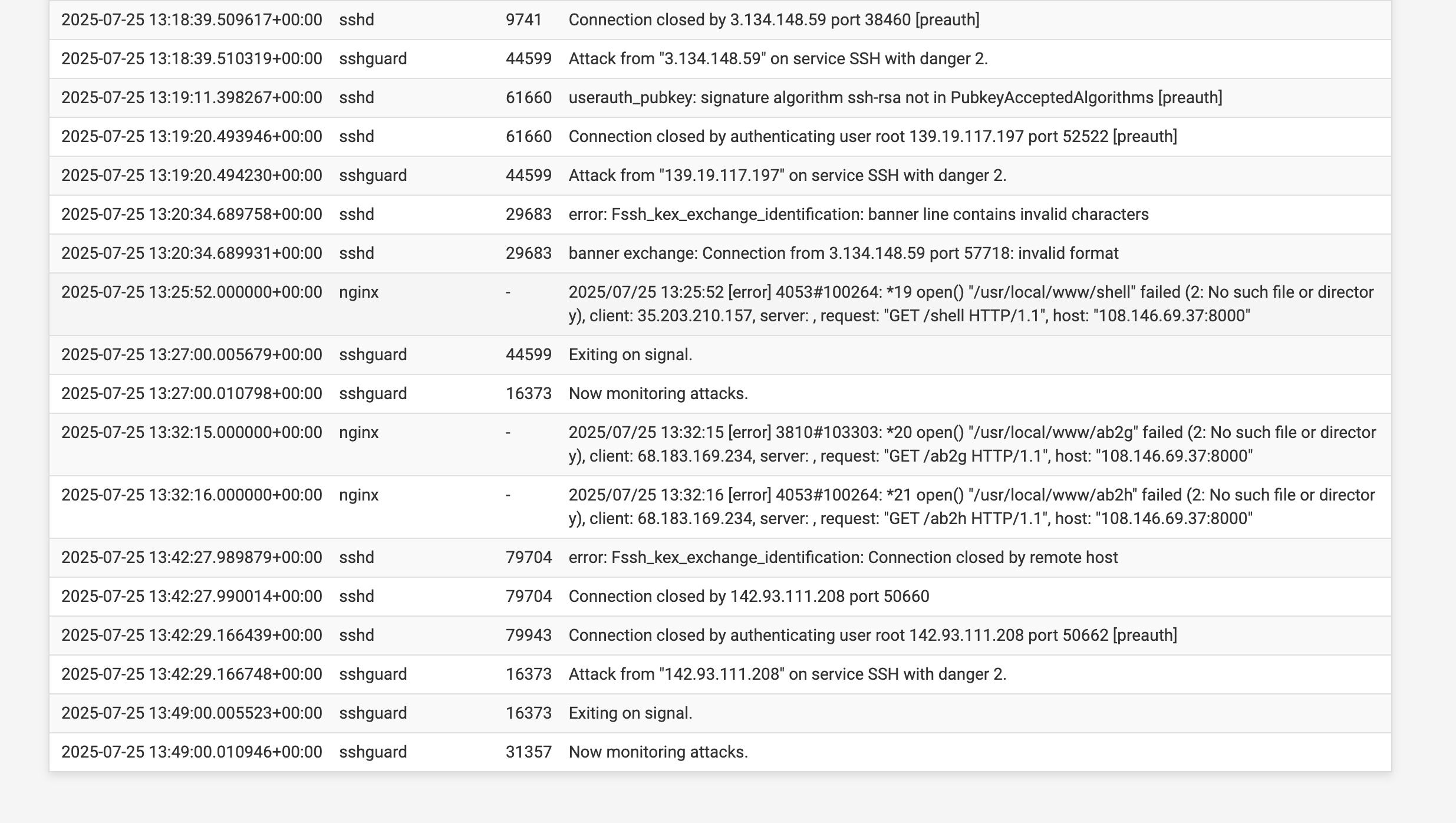
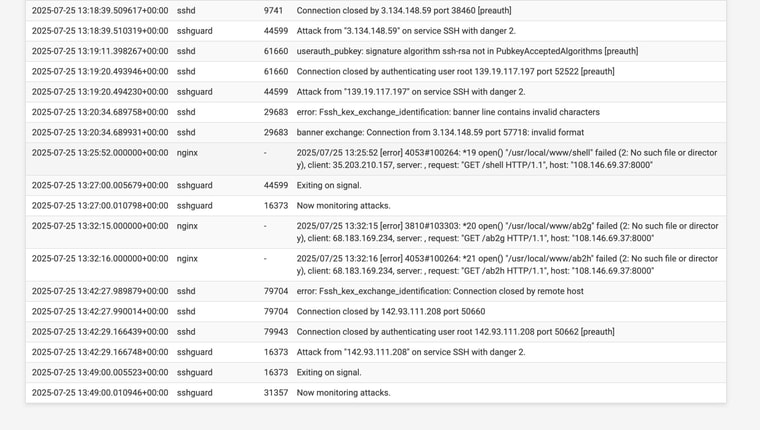
I admitedly dont look often enough!I saw all these SSH attacks. (One I'm not sure is even depicted here was "level 10"
The only thing I did was change SSH access to require password and key (from password alone).
After that I still see attacks (see attached)
Suggestions? Is. this a problem!
-
do you have ssh port 22 open on your WAN?
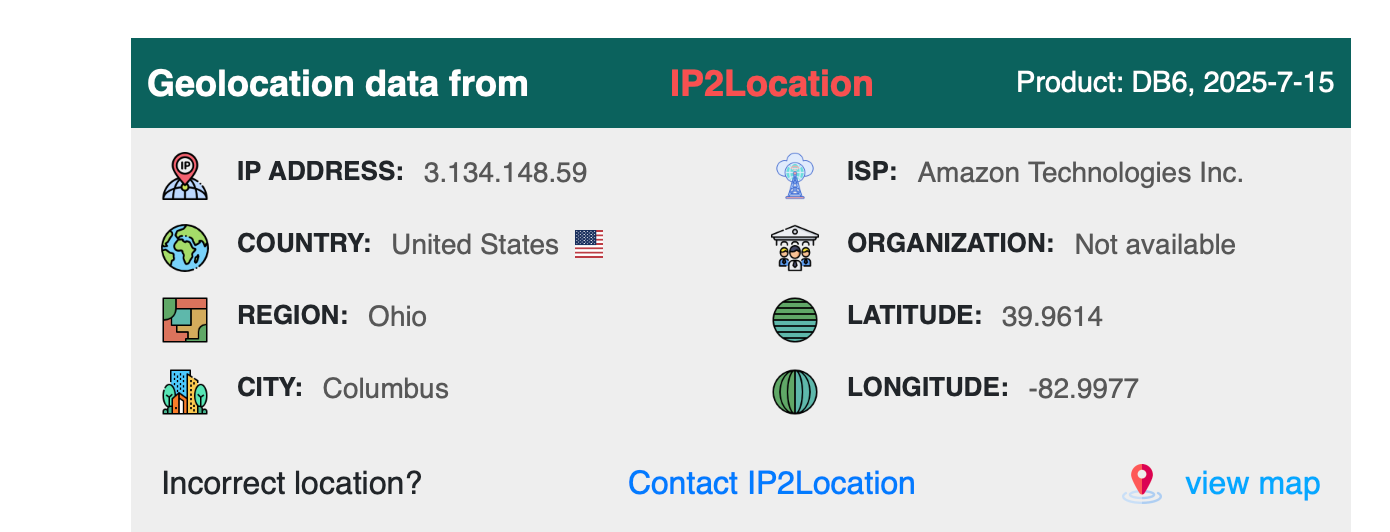
looks like IP address is owned by amazon
-
Thanks I do not
I only have my Wireguard ports open
Is there anyway the attack is coming via WG or Tailscale?
-
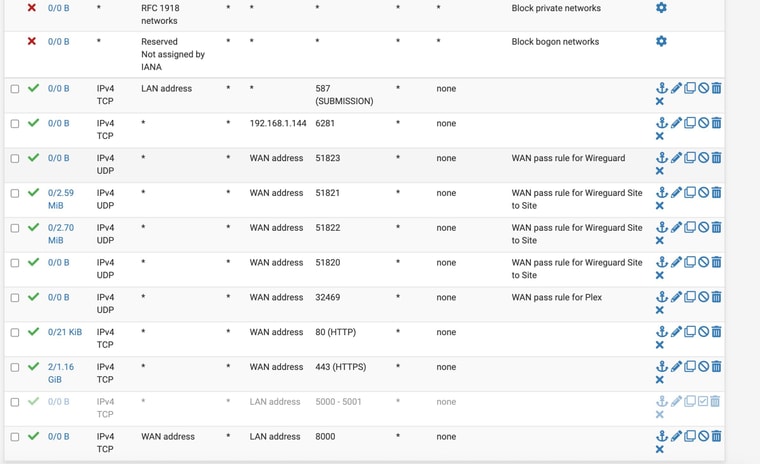
@ahole4sure FWIW the rule for port 587 won't trigger there because a packet from LAN doesn't arrive on WAN.
Do you have any NAT rules defined?
FWIW the "exiting"/"now monitoring attacks" messages are logged when sshguard restarts due to a log file rollover so ignore those.
-
@ahole4sure do you have any floating rules? Is ssh running on standard port 22?
-
No floating rules and ssh on 22
-
@ahole4sure Watch for open states for 22.
if you Status > Filter Reload do the rules load successfully?
-
It could be over a VPN if the other side of that is forwarding connections to you.
But, yes, I would check the states and see which interface has port 22 states on it.
-
Thanks
Not sure if I did correctly or not but I went to
Diagnostics > States
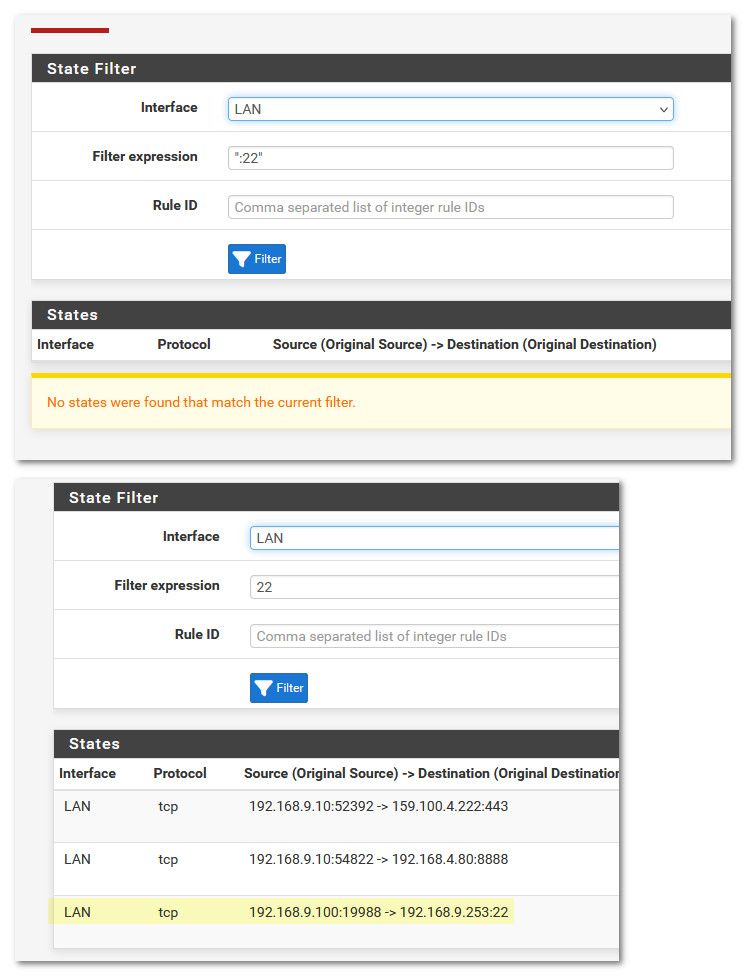
And filter expression - “:22”I got no states actually for :22
There were several results but they were like this as an example. But not really port 22
108.146.69.37:22582 -> 8.8.8.8:53 -
@ahole4sure said in SSH "attacks":
And filter expression - “:22”
that wouldn't be right - in the states just use 22
if you to see something there needs to be an active state.. So if someone tried to hit your ssh like 20 minutes ago, that state would be gone.. If you are hits often enough just keep checking.
-
If you believe its coming in on your vpn - turn off your vpn for a bit.. Do you continue to see hits? Or start a packet capture on your vpn interface for dest port 22 to your wan IP - let it run until you see another entry in your log.. was anything captured?
If you want to validate that your not letting it in via just public IP on your wan - you could go to say can you see me . org and send some traffic to 22.. what does it say - if it gets a SA back then it would be open.. If it times out then its not.
If it is coming in via vpn interface - you could create a rule to block such traffic. That is if there is an actual interface with wireguard - I don't run that..
-
Yup you would only see states while they're still active. So if you are not seeing attacks that often you'd have to get lucky to catch it.
But you should see those by filtering for:
22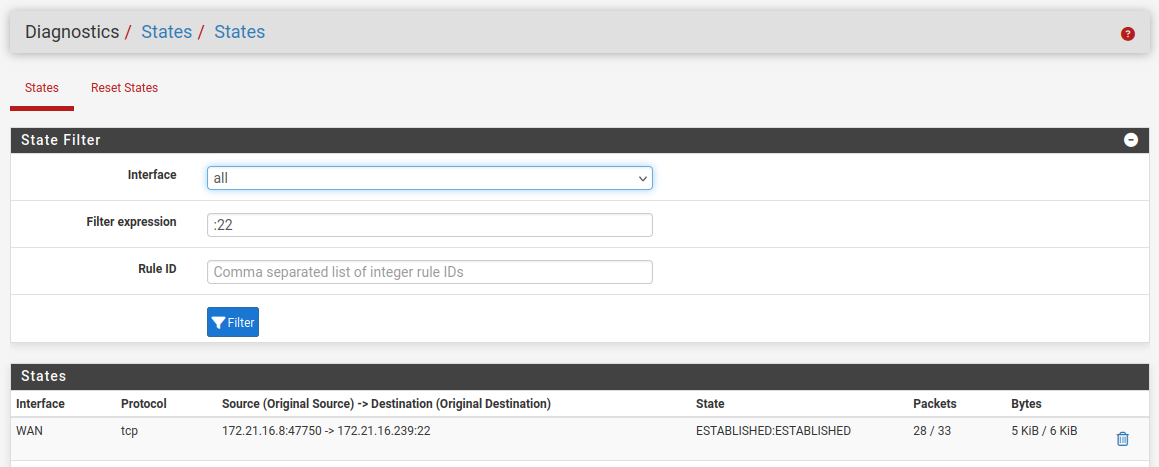
What rules do you have on the VPN interface(s)? It would be unusual to see connections being forwarded to you there though.