LAN not in ARP table
-
Greetings,
I was able to successfully install and configure my first PFSense firewall, on an ION 2000.
Took a couple of days to get everything setup. My last step, which is always my last step is to reboot the system. After rebooting I lost connectivity to my GUI. I do have a serial connection, I also just noticed that my LAN IP is not showing in the arp table. The rest of the network is in the ARP table correctly.
Port 0 is my gateway. port 1 is my LAN. The WAN port from the Firewall is connected to the Uplink port on the switch (polling okay). And the LAN port is a regular connection on the switch (not polling).
PFSense is definitely monitoring the Gateway 192.168.99.1, I can see the traffic, and blocking done in the logs.
I am using PFSense for DNS. MY LAN connection on PFSense is doing DHCP. WAN is static.
My network is fine. I definitely feel the protection. I am using a computer on this network, now. But something must be wrong if I cannot see my LAN in the firewall.
My ISP router has FIOS in, additional connection to LAN. (no other connections). Firewall in the router is turned-off.
DHCP, and DNS are both fine - I can see the traffic from DNS in the logs. The static servers are being used.
I appreciate any suggestions.
-
If you run
ifconfigand the CLI do you see the LAN interface with the correct MAC and IP?@EndUserOnly said in LAN not in ARP table:
The WAN port from the Firewall is connected to the Uplink port on the switch (polling okay). And the LAN port is a regular connection on the switch
The same switch? You have those separated with VLANs in the switch?
-
@stephenw10 I have not configured any VLANS (yes the same switch). Router, (switch), Firewall.
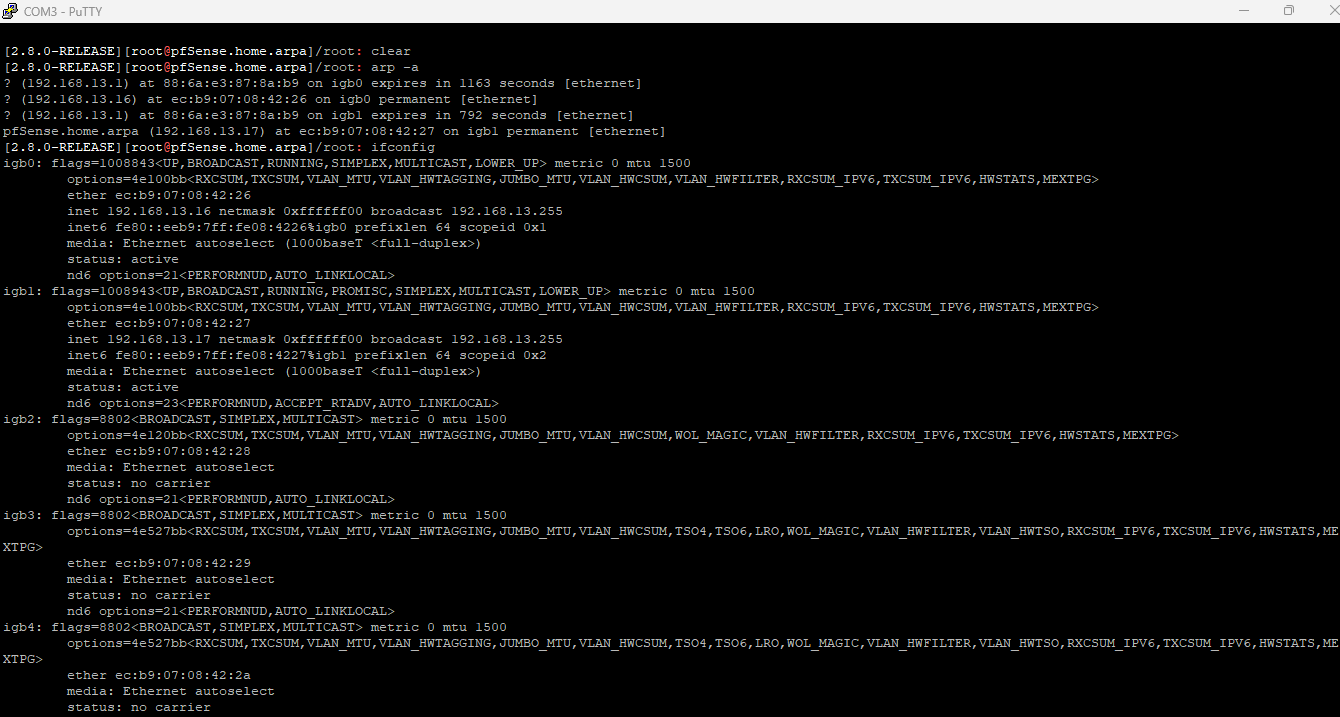
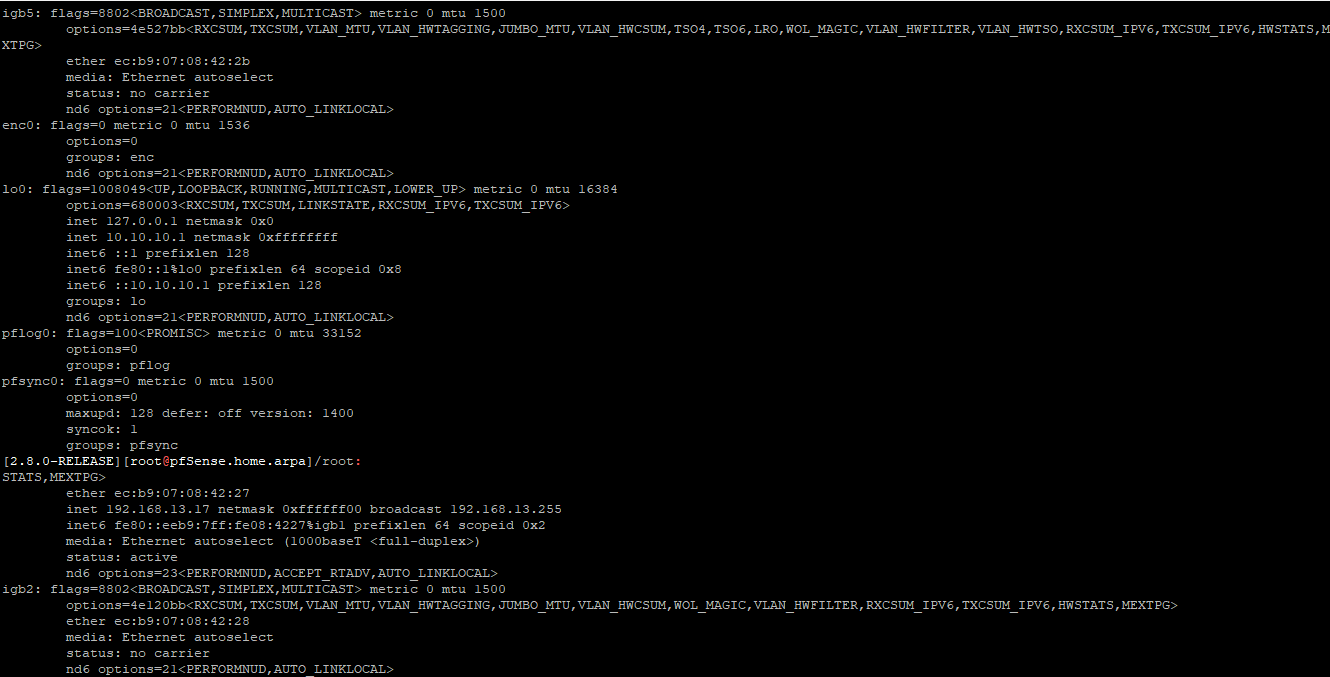
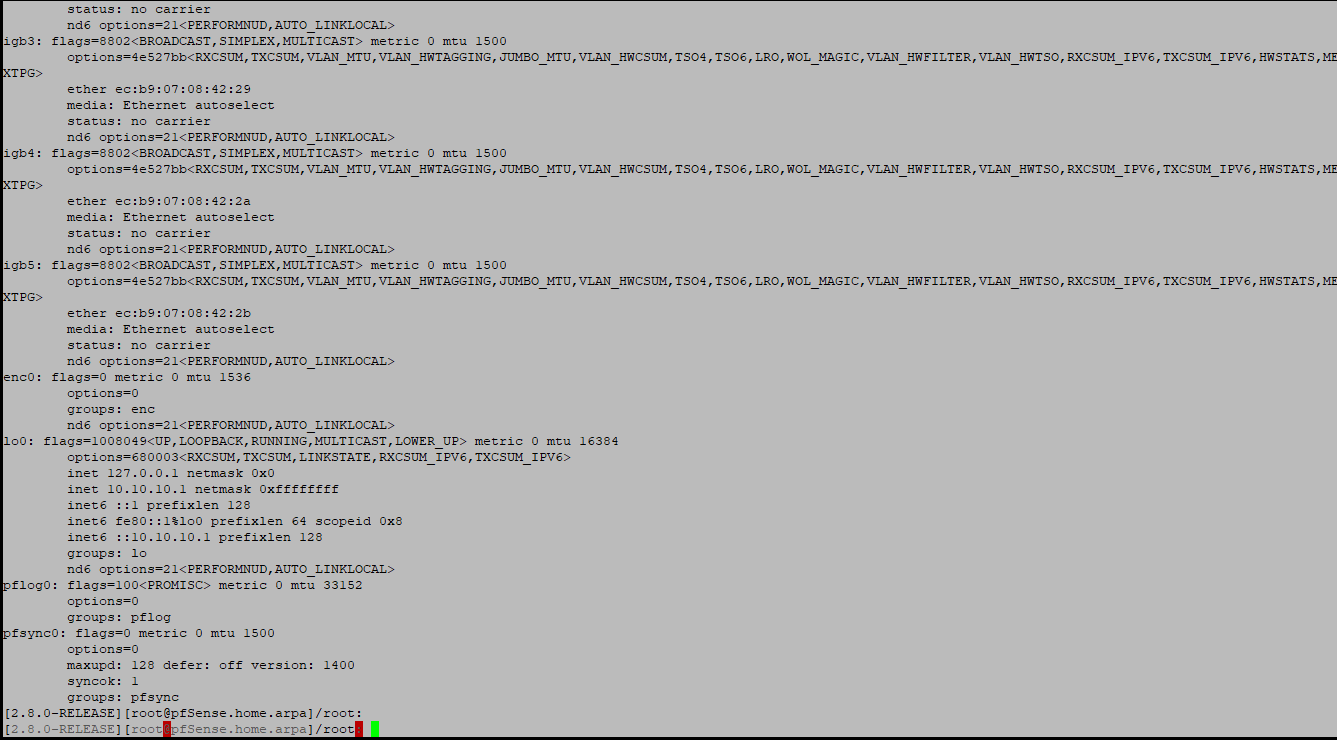
igb0 and igb1 are both showing UP in ifconfig. (good question missed that).
-
Hmm, both interfaces in the same switch is going to be an issue. They should be in different broadcast domains for routing to work correctly.
But that shouldn't prevent local interfaces/addresses appearing in the ARP table.
What exactly do you see from arp -a and ifconfig? For example:
[25.07-RC][admin@4860.stevew.lan]/root: arp -a 4860.stevew.lan (192.168.23.1) at 00:08:a2:0d:16:15 on igb0 permanent [ethernet] ? (172.21.16.8) at f4:6b:8c:90:b4:d8 on igb1 expires in 1061 seconds [ethernet] ? (172.21.16.238) at bc:24:11:5c:2a:1c on igb1 expires in 1156 seconds [ethernet] ? (172.21.16.1) at 00:08:a2:0c:c9:91 on igb1 expires in 1200 seconds [ethernet] ? (172.21.16.4) at 0c:80:63:69:c2:de on igb1 expires in 1014 seconds [ethernet] ? (172.21.16.23) at 00:08:a2:0d:16:16 on igb1 permanent [ethernet] [25.07-RC][admin@4860.stevew.lan]/root: ifconfig igb0 igb0: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 description: LAN options=4e100bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,VLAN_HWFILTER,RXCSUM_IPV6,TXCSUM_IPV6,HWSTATS,MEXTPG> ether 00:08:a2:0d:16:15 inet 192.168.23.1 netmask 0xffffff00 broadcast 192.168.23.255 inet6 fe80::208:a2ff:fe0d:1615%igb0 prefixlen 64 scopeid 0x1 inet6 fe80::1:1%igb0 prefixlen 64 scopeid 0x1 media: Ethernet autoselect status: no carrier nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> -
-
.17 is my LAN, .16 is my WAN. I do not remember .17 being there before. Did not change situation. I did resets on both the interface and IP address today (still trouble shooting). No change.
-
I cannot see my LAN in the firewall, but other than that everything looks okay. That and I cannot access the GUI. But fortunately I have everything configured, with automated backups, and a config file stored.
I simply am not advanced enough to understand what you mean by separate networks. I should have emphasized I am a home user.
The WAN is being monitored. 192.168.13.1. I can see blocking in the logs. I will probably let sleeping dogs lie. I can do my updates through the console. Thanks for your time.
-
Ah, OK they are in the same subnet which is a conflict. That won't work.
If both interfaces are set as static then just change one of them to a different subnet. But it still should be using a different switch or VLAN.
What exactly are you wanting to use pfSense for here? How do you expect traffic to flow in your network?
-
@stephenw10 Just a casual user. I believe I am already getting the protection I need. After all, the one thing I need is for PFSense to monitor the gateway. That is all. Any traffic through the gateway. very basic. Based on the performance of my system, clearly a lot of junk is being blocked. I can tell by system response. And the freedom I have when using the Internet, as compared to before. I did look into VLAN's, trying to understand how to use one. From the console I can setup the VLAN, but not the firewall rule. I would need the GUI for that. I will find a good Youtube tutorial if I get too bothered.
-
The VLAN you would need would be on the switch in order to separate the WAN and LAN network segments.
Or connect the pfSense WAN to whatever upstream router you have directly so the switch is only the LAN.