Wireguard gateway connection issues when using domain names for peer endpoints
-
@chrcoluk Thank you!! I'm going to give it a try tomorrow probably! Hopefully I can figure it out. I'll let you know!
-
@chrcoluk Hi again chrcoluk, I started researching bind and started to understand it more. But I happened to try setting domain name again for wireguard peer endpoint field.
I noticed that when I did this, I immediately got WAN_ISP interface blocks with source: being my mullvad wireguard gateway ips and destination: my quad9 public ips using dns over tls port 853 set at system -> General setup -> DNS Servers.
These are the blocks in the firewall log:
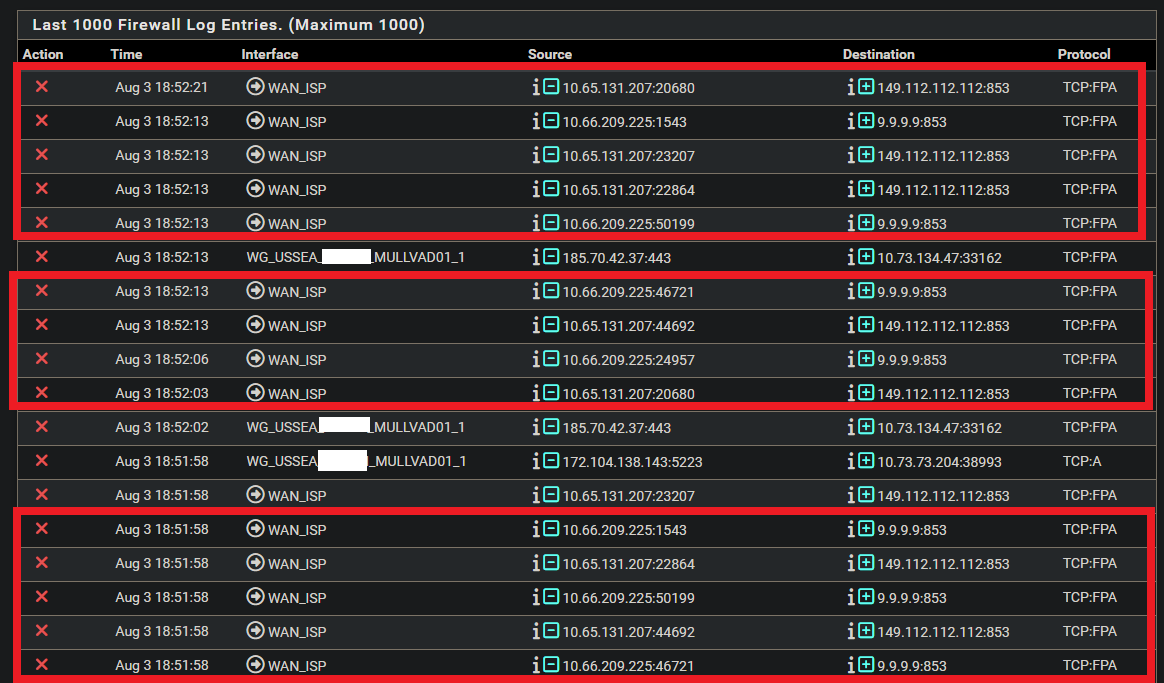
and if I hover over the red X, I see:
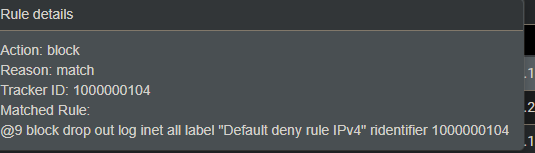
Could this be causing my issue? How can I find this block rule and remove it? I looked at firewall rules on WAN interface and I don't think I saw a WAN rule that matched that ID when I hover over the red Xs:
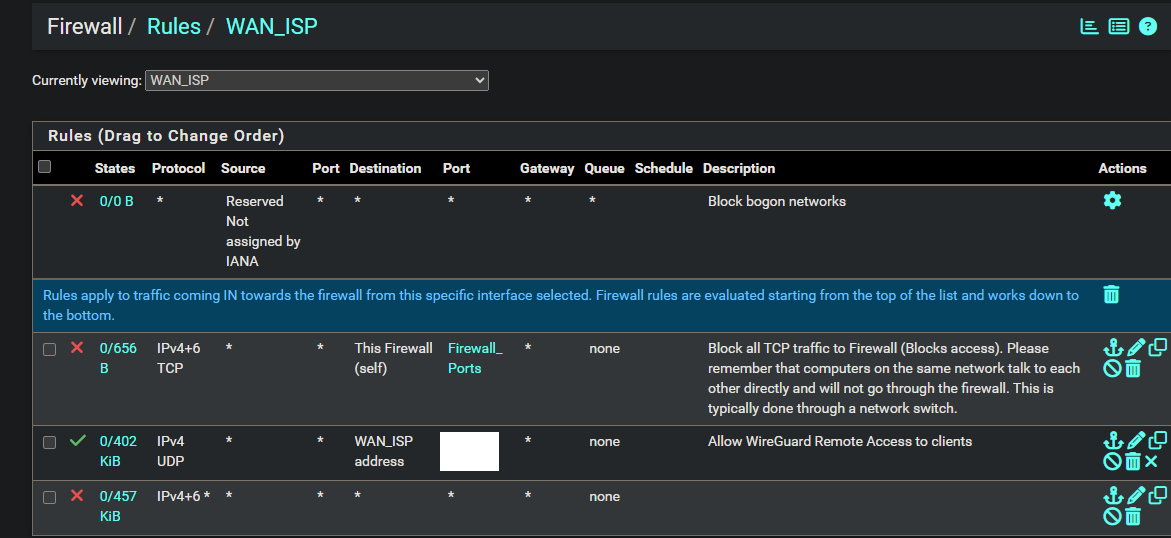
Thank you
EDIT: after doing some digging I think this is some sort of default rule that cannot be removed? Do you know if there is some allow rule I can create to make this work in a secure manner? The only thing is, I think the wireguard mullvad gateways IPs can/will change...
-
@pfsenseuser10293 WAN is for inbound traffic. by default all outbound is allowed.
Did you change default outbound block/allow setting?
-
@chrcoluk Not that I can think of (at least intentionally)
- I have pfblockerng enabled. For IP tab, I only have a few TOR lists to block.
It has these interface settings:
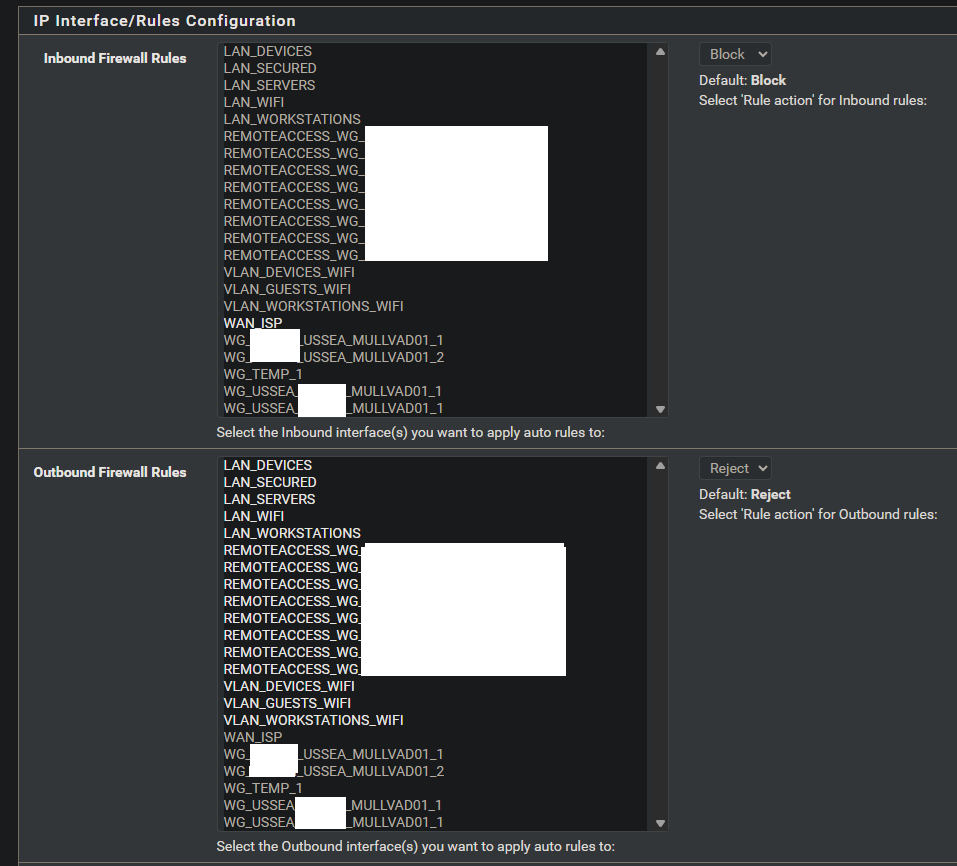
-
DNSBL has a bunch of custom ad blocking lists and DNSBL safesearch has DNS over HTTPS/TLS/Quic blocking enabled but this is DNS not "default deny rule ipv4" as stated by the block entry. The DNSBL firewall rules are set to not be permitted on any wireguard interface and WAN isn't even selectable.
-
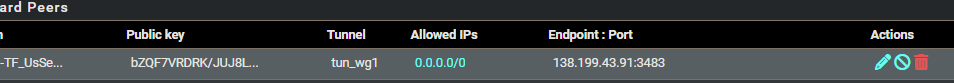
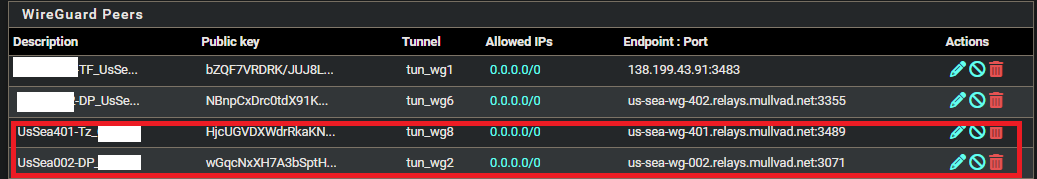
All of my wireguard interfaces have this block rule:
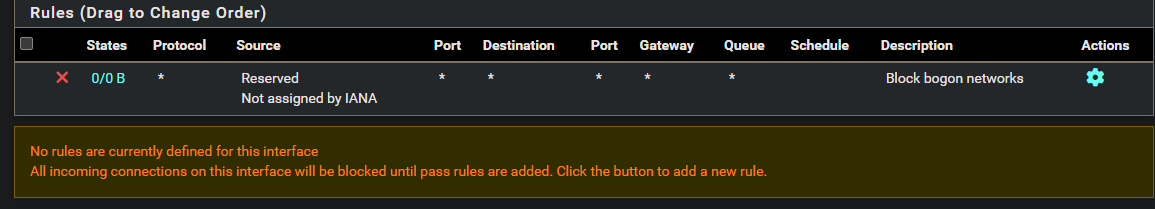
None of those match the tracking id: 1000000104 that is stated by in the block entry
-
Suricata is enabled but only on two interfaces completely unrelated (A IoT network for example). Also shows no blocks in the log for suricata.
-
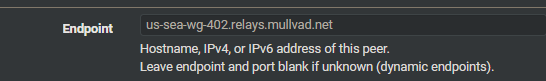
For wireguard mullvad peers I created, allowed ips are all set to: 0.0.0.0/0
-
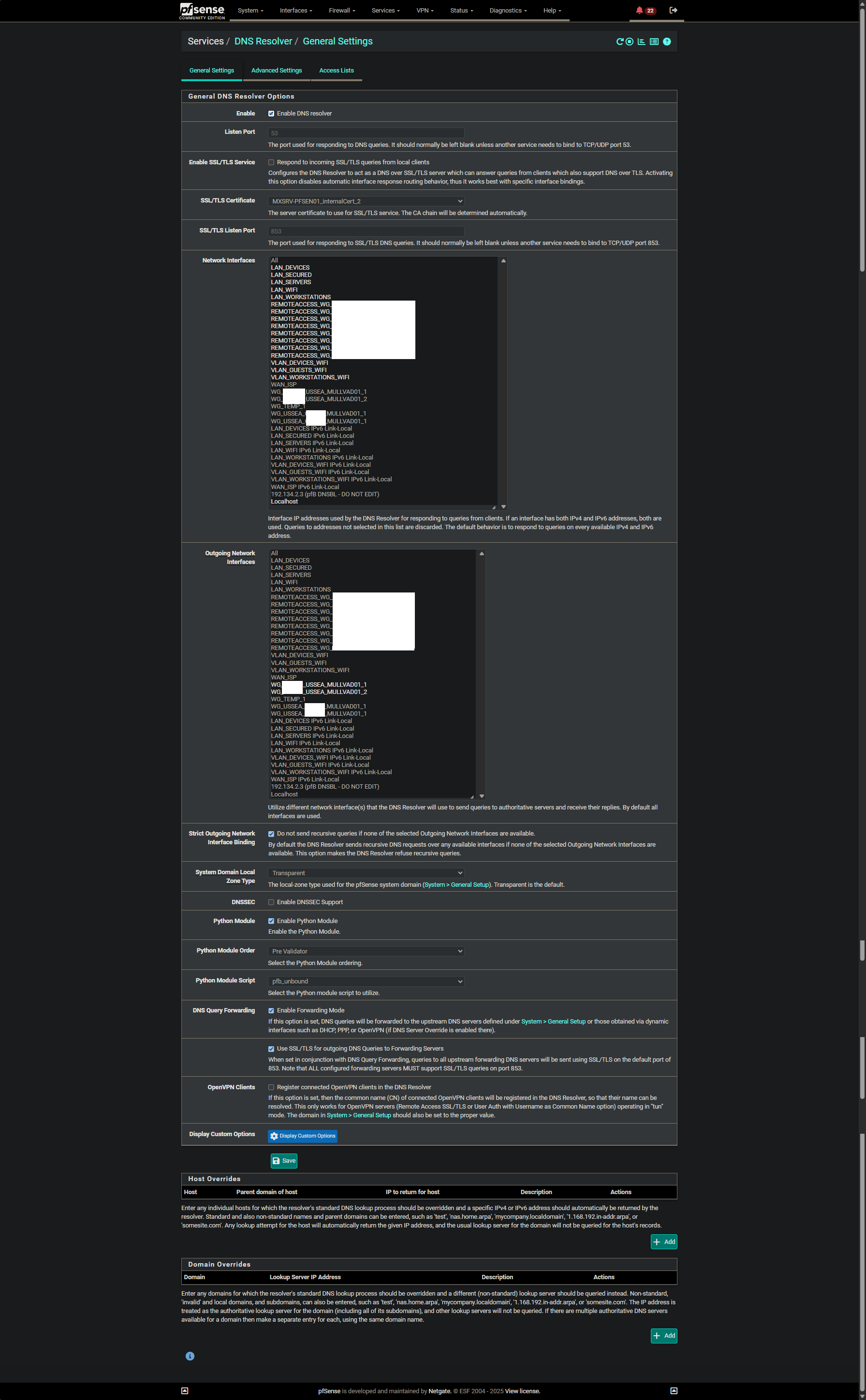
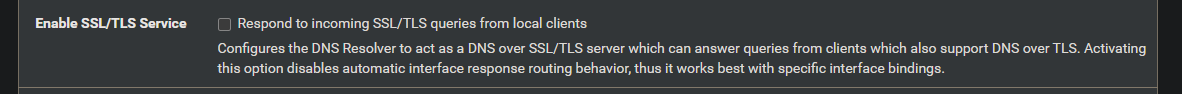
DNS Resolver settings has this rule unchecked, do I have to enable this?
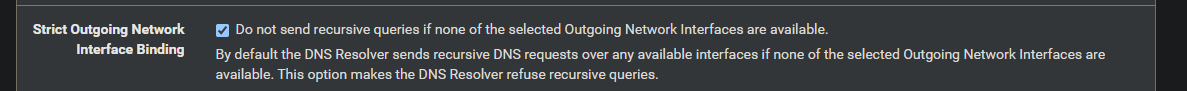
It also has this enabled (which I know isn't enabled by default):
- Floating rules only has the pfblockerng rules in it.
This is all I can think of right now.
-
I tried testing remove quad9 from the DNSBL safesearch blocking and reloaded pfblockerng but the blocks on the firewall to quad9 still appear.
-
@chrcoluk Under System logs -> Firewall -> Normal view where the blocks to quad9 were appearing on wan interface, I also tested clicking the + sign on the desintation column "EasyRule: Pass this traffic" for all the entries. After that I restarted wireguard and it some how made the issue worse. None of the wireguard interfaces go up now. Before, at least some of them would successfully come online. They're all Offline, Packetloss 100% now, even after removing the new WAN interface allow rules and restarting wireguard. I had to add the IP address to the mullvad wireguard peer endpoint.
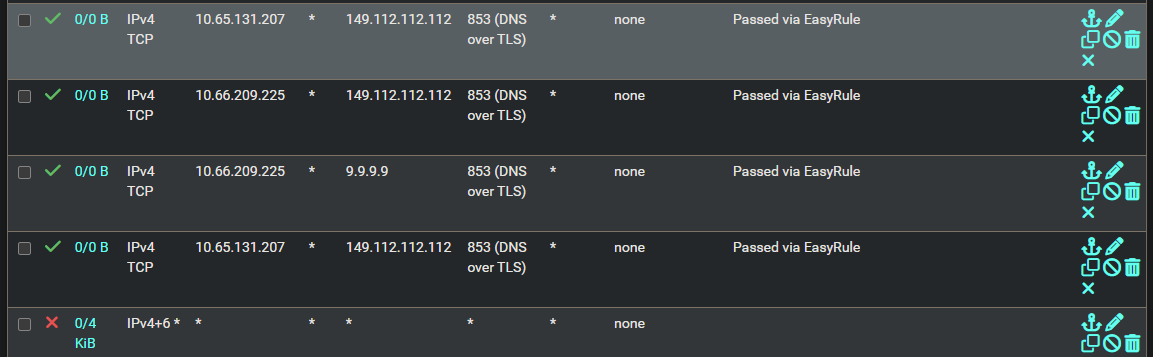
I think this just may be a distraction. I will focus back on understanding and doing the bind method
-
@chrcoluk going back to the Bind method: I think I understand what it's doing; making localhost (pfsense) bypass unbound but i'm really confused on what settings to change on Bind..
been trying to find resource online for editing it.
-
Hi again,
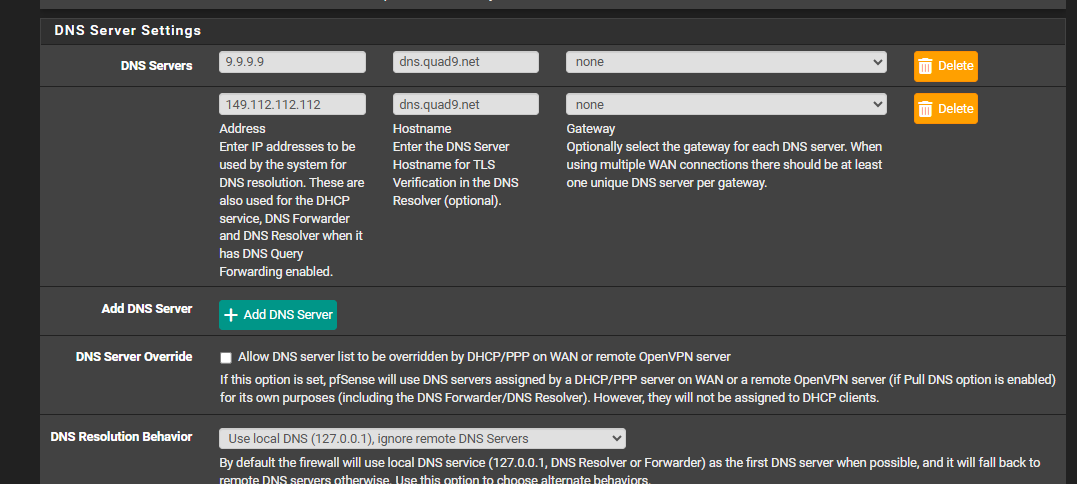
Interestingly, after playing around with more settings, this seems to have fixed is completely!:
in system -> general setup:
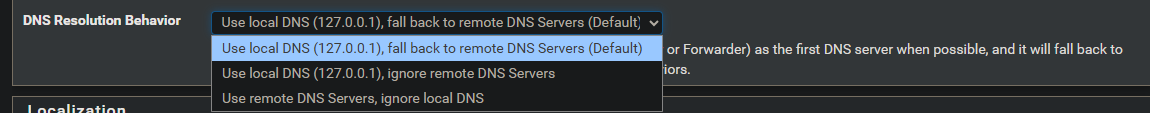
I change it from:
use local DNS (127.0.0.1), ignore remote DNS Servers to
Use local DNS (127.0.0.1), fall back to remote dns servers (default)I dont seem to be getting DNS leaks (from dnscheck.tools) and now I can restart, stop/start wireguard and all wireguard gateways come up really fast now.
Do you know what Use local DNS (127.0.0.1), fall back to remote dns servers (default) is doing? and why this works? Any privacy concern using this?
Thank you!
-
@pfsenseuser10293 using localhost will make it use the service you have configured whether thats unbound or bind. otherwise pfSense can query forwarders directly.
It will probably be fine how you set it now, pfSense only needs DNS for its own updates, news widget on dash, and to connect to the VPN's.
I did forget about that option.
-
@chrcoluk SWEEEEEEEEEEEEEEEEET. Thank you so much for your help!!!! I guess I dont need to do the bind method then! Thank goodness!!