pfBlockerNG not logging anything by default?
-
hey forum. maybe someone can help me with pfBlocker. I have this nice overview on pfsense mainpage but it logs nothing.
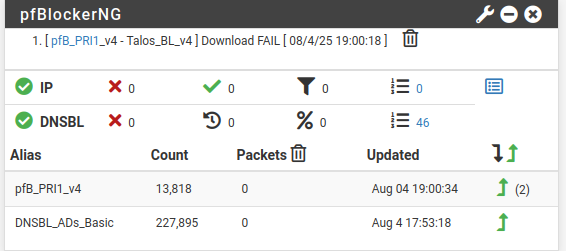
I found a related thread that never got resolved however https://forum.netgate.com/topic/175045/pfblockerng-not-logging-everything
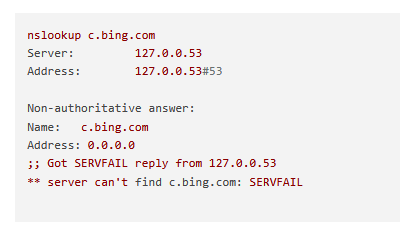
Is this normal behaviour? I am using the default out of the box settings here.When doing a nslookup of a blocked domain I seem to be getting the correct response.
nslookup c.bing.com
Server: 127.0.0.53
Address: 127.0.0.53#53Non-authoritative answer:
Name: c.bing.com
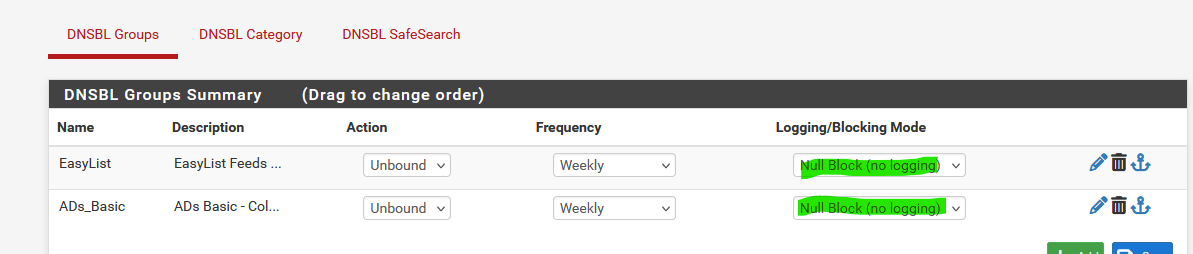
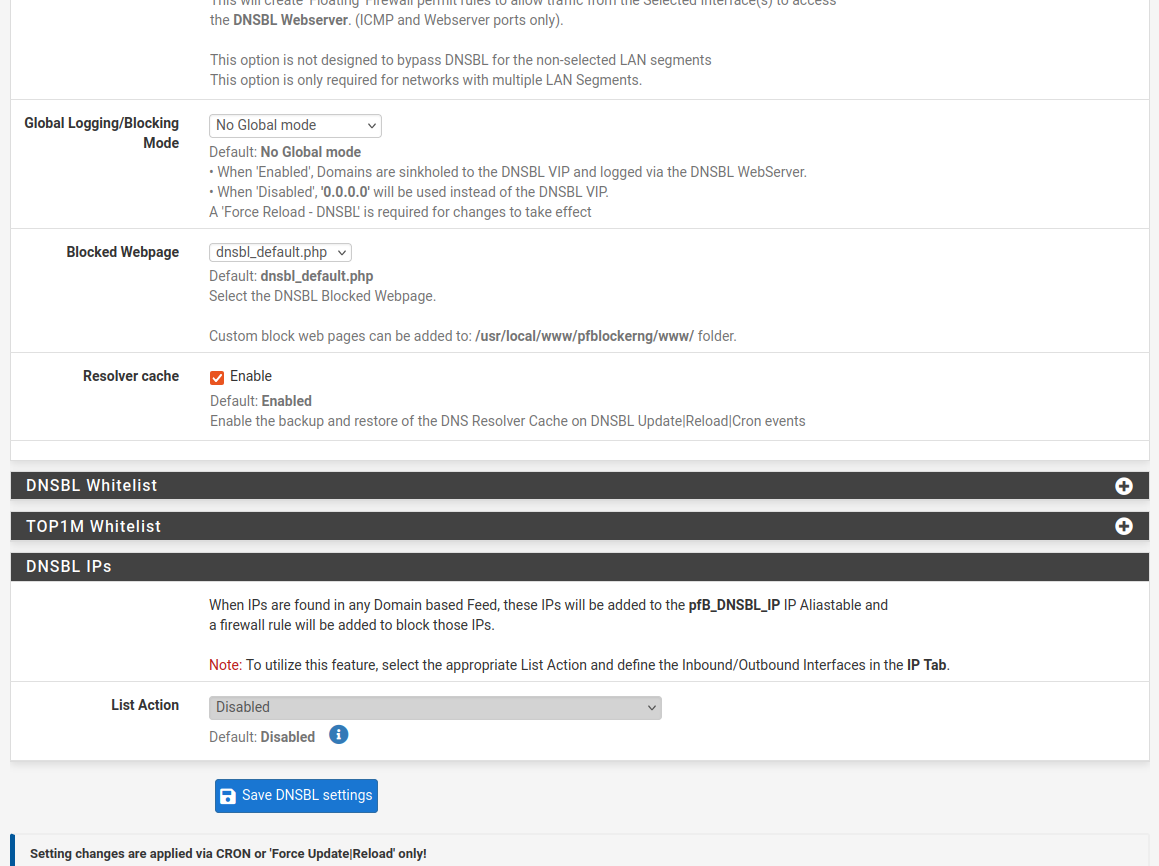
Address: 10.10.10.1But I don't see anything logged in the main tab. Do I need to change something in this setting here:
Global Logging/Blocking Mode
By default it is set to "No Global Mode"
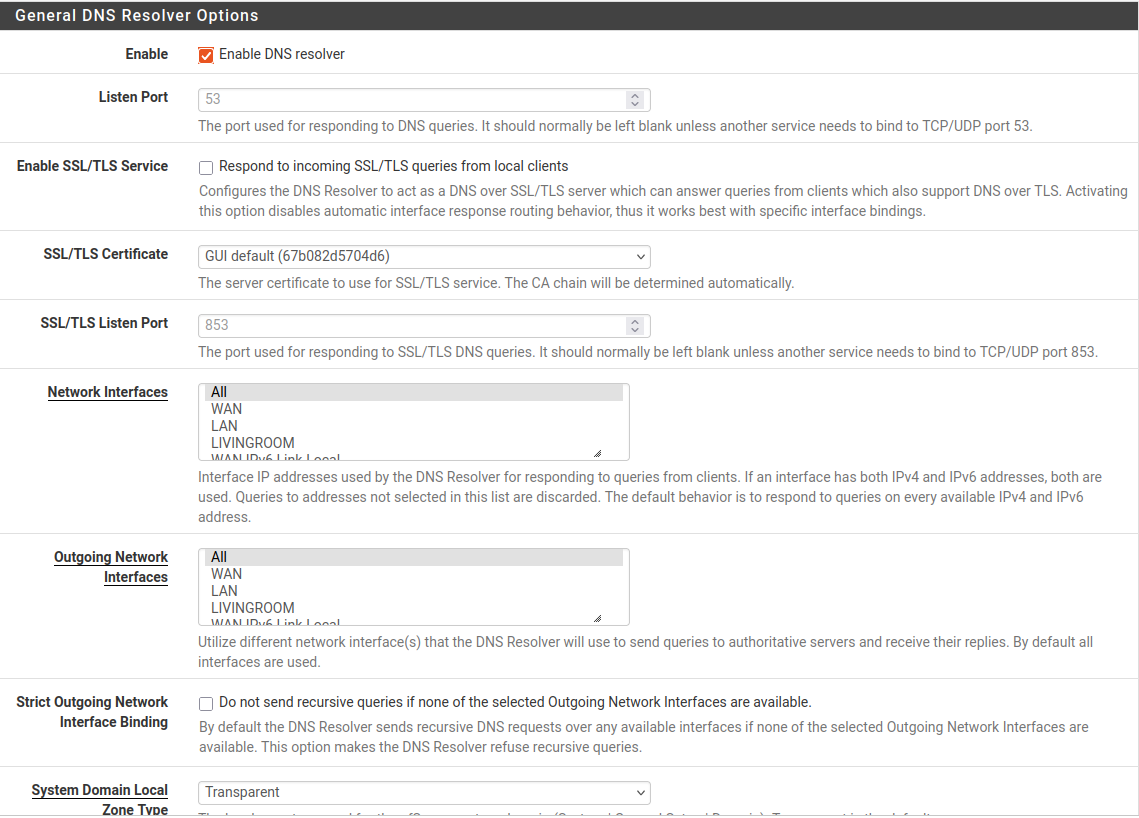
Under alerts I see my nslookups but it only shows "unknown" and not the actual website. I also expect more than just this to show up here when browsing the web. What do i need to change to get this to resolve properly? I have searched already and couldn't find a good answer. I am using Unbound btw. and this under general setup:
-
@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
By default it is set to "No Global Mode"
That means you've selected (default, probably) :
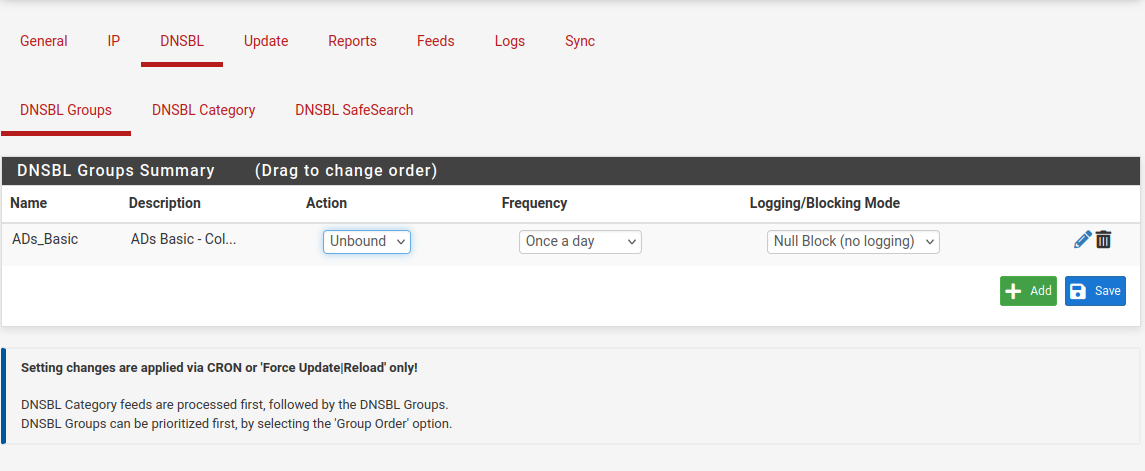
Here : Firewall > pfBlockerNG > DNSBL
so, for every DNSBL feed you use, pfBlockerNG will use the seclted log mode :
You didn't show what mode you actually selected, but I'll bet it is (pretty worthless) DNSBL Webserver/VIP" mode, as I saw that a request for a blocked host name (your example c.bing.com) pfBlockerNG resturn 10.10.10.1 which is the DNSBL web server IP.
The unknown indication :
This means that, while "c.bing.com" was found in the 'main' DNSBL list, pfBlockerNG doesn't know (anymore) from which DNSBL list this host name "c.bing.com" came from.You've tried this :
Firewall > pfBlockerNG > Update and select "Reload" & "All" ? -
@Gertjan Unfortunately I have set it exactly like in your screenshots. The default was DNSBL webserver and I changed it to Null Block like in your screenshot. All it does is return 0.0.0.0 in nslookup. But even if I try different domains they don't get logged anymore in alerts like the first time I tried it.
I also did a "Update" and "Reload". I haven't tried the "Cron" option yet. Does Cron do anything differently?Unrelated I am seeing this error in the Ipv4 lists. The lists are empty.
===[ IPv4 Process ]================================================= [ Abuse_Feodo_C2_v4 ] Reload . completed .. Empty file, Adding '127.1.7.7' to avoid download failure. ------------------------------ Original Master Final ------------------------------ 0 1 1 [ Pass ] ----------------------------------------------------------------- [ Abuse_SSLBL_v4 ] Reload . completed .. Empty file, Adding '127.1.7.7' to avoid download failure. ------------------------------ Original Master Final ------------------------------ 0 0 0 [ Pass ] ----------------------------------------------------------------- -
here are all the settings
-
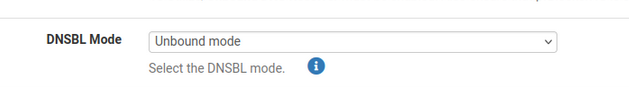
This is the ancient 'legacy' mode. Consider the Unbound mode as the method not to use.
I presume you use the resolver (unbound), and have these set :
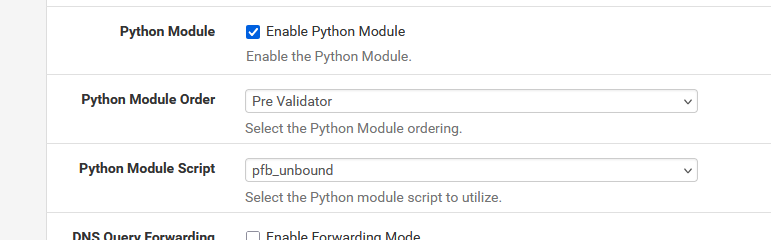
so, use the more modern (since 2022 ?) "Python mode".
Python mode mode is way faster, more details, etc.
Afaik : The "cron" is used for log rotation and stats maintenance. It's also use to determine if it's time to try to re download IP and DNSBL files. -
@Gertjan I have not set that in Unbound. No Python Module is active there. I saw that in another thread but I don't think it will change anything. Also which of these settings for the unbound python mode should be enabled here?
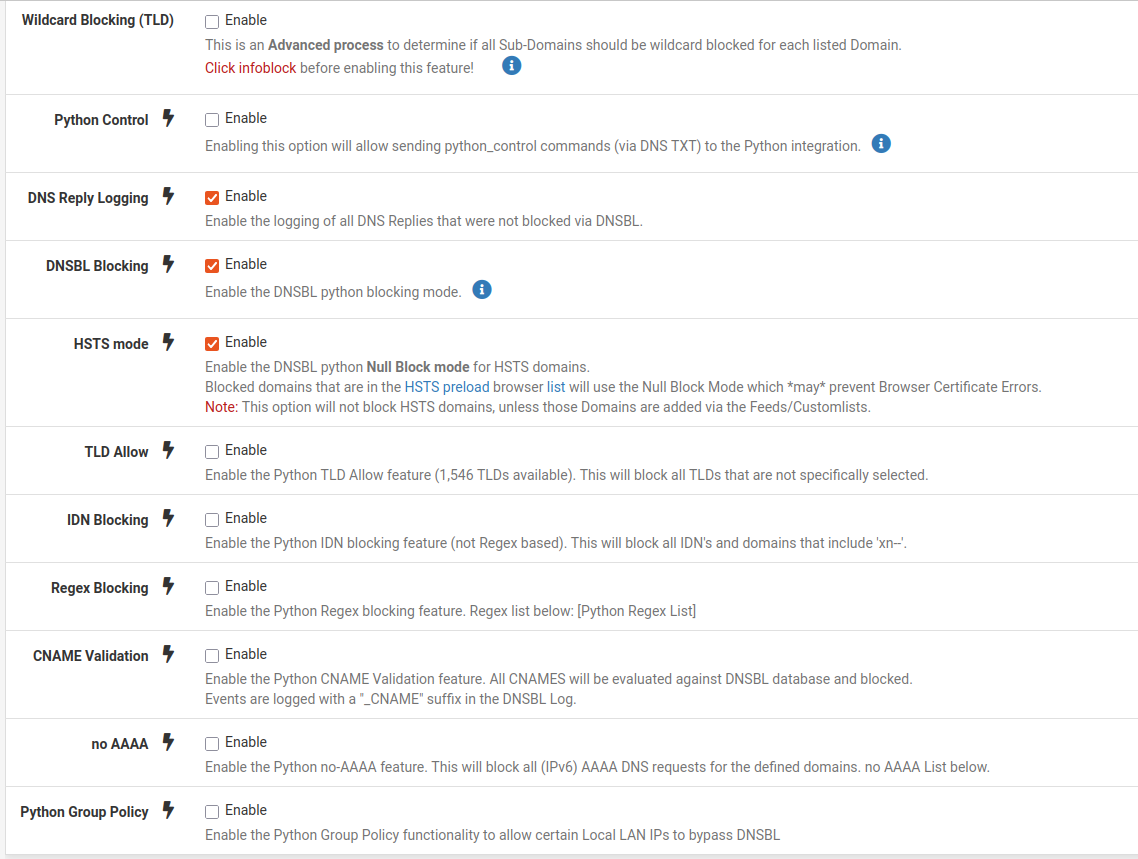
I also have no script to select under Unbound:
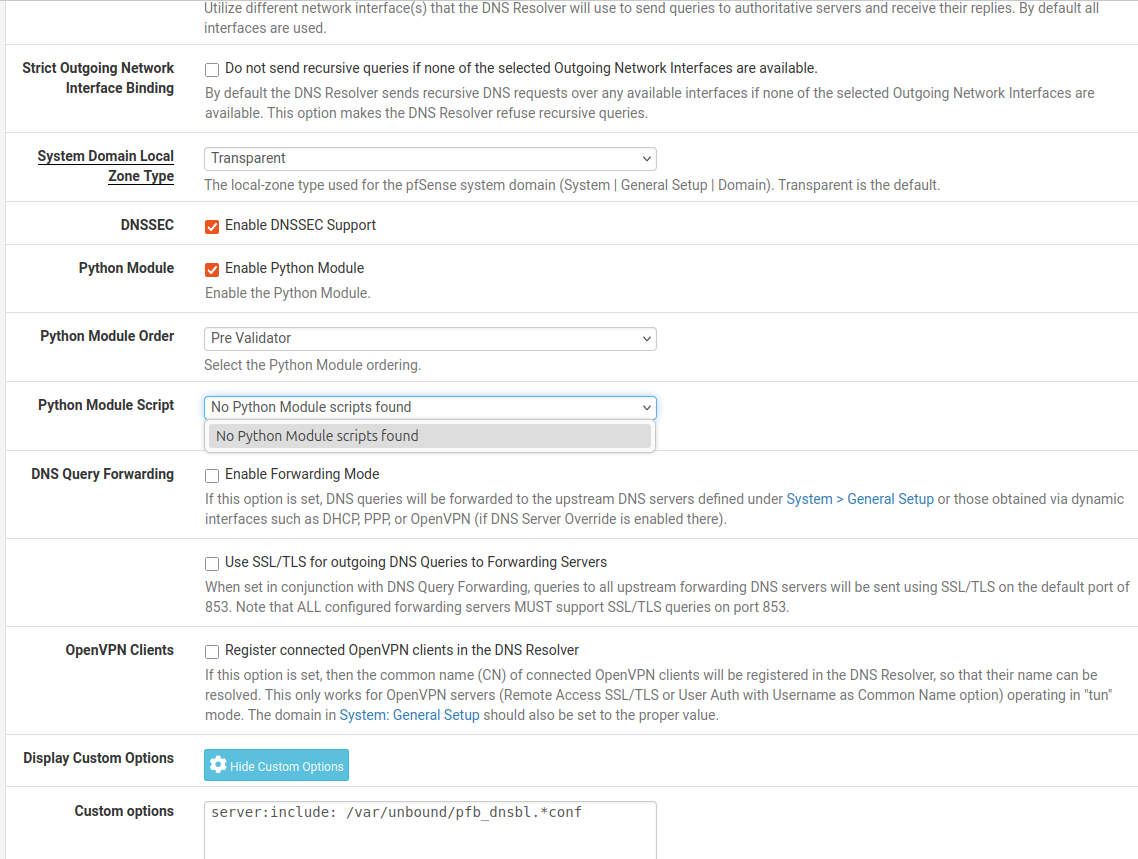
-
@Gertjan After changing to Unbound python mode I see some stuff. It also shows me a different response now in nslookup. This is new ";; Got SERVFAIL reply from 127.0.0.53
** server can't find c.bing.com: SERVFAIL" Is this supposed to happen?nslookup c.bing.com Server: 127.0.0.53 Address: 127.0.0.53#53 Non-authoritative answer: Name: c.bing.com Address: 0.0.0.0 ;; Got SERVFAIL reply from 127.0.0.53 ** server can't find c.bing.com: SERVFAILUnder alerts I see this now:
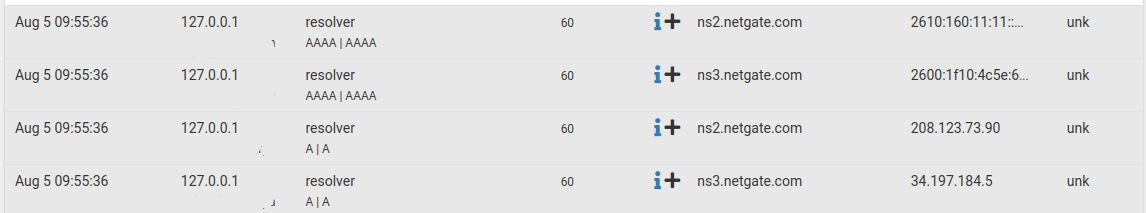
Soure is almost every time 127.0.0.1 and my pfsense domainAlso any idea why I see this when I am not using google dns?
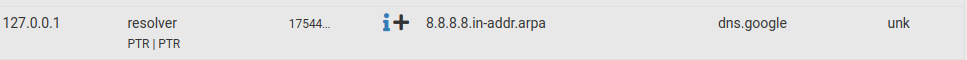
-
Is it normal to see these entries under Reports -> DNSBL Reply Stats? I have filtered for feodotracker.
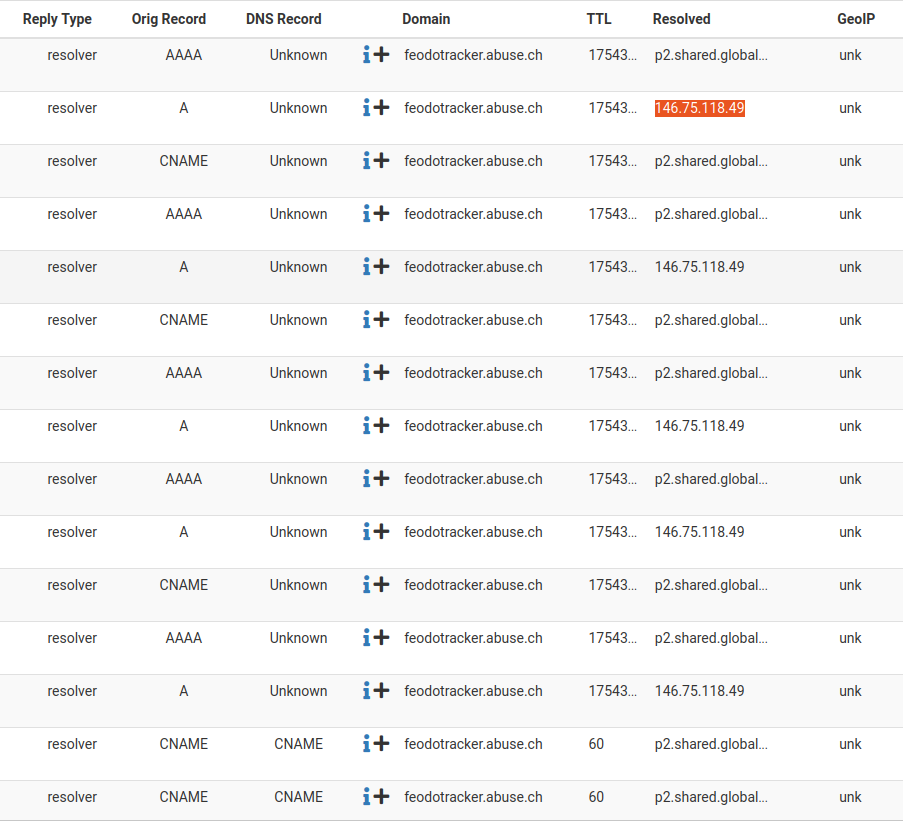
If I look under Overview tab I see stuff happening now but once I click the little 2 to send me to Alerts it shows no Alerts there.
I also see a lot of 127.0.0.1 and sometimes my local IPs. Is there a way to see which device made the connection under 127.0.0.1?I also assume these are supposed to show up once an hour when the new lists are checked?
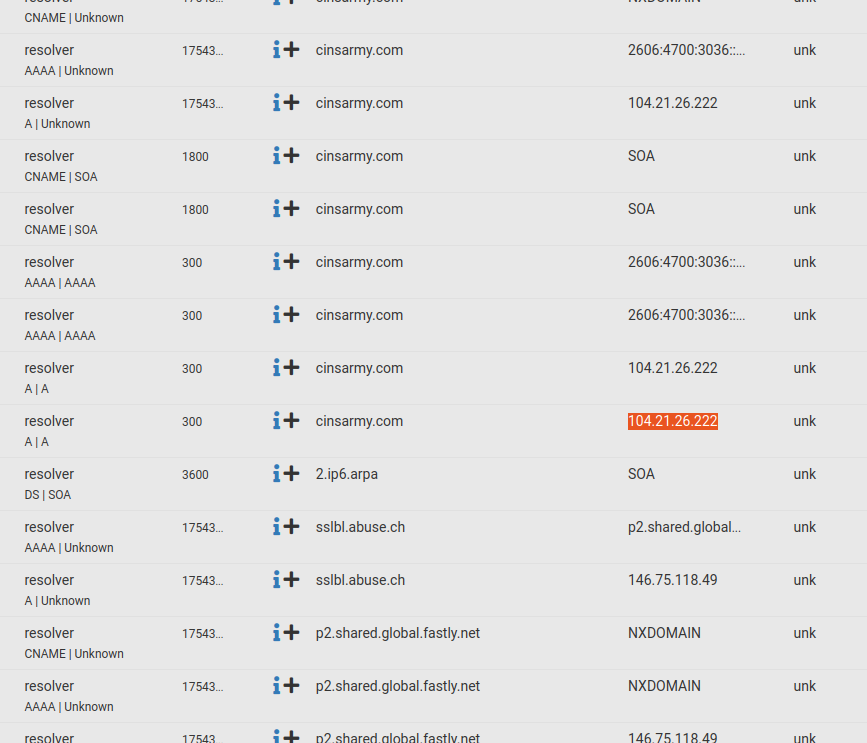
-
@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
After changing to Unbound python mode I
and then Save the unbound/resolver settings.
the Apply (mandatory).Then here :
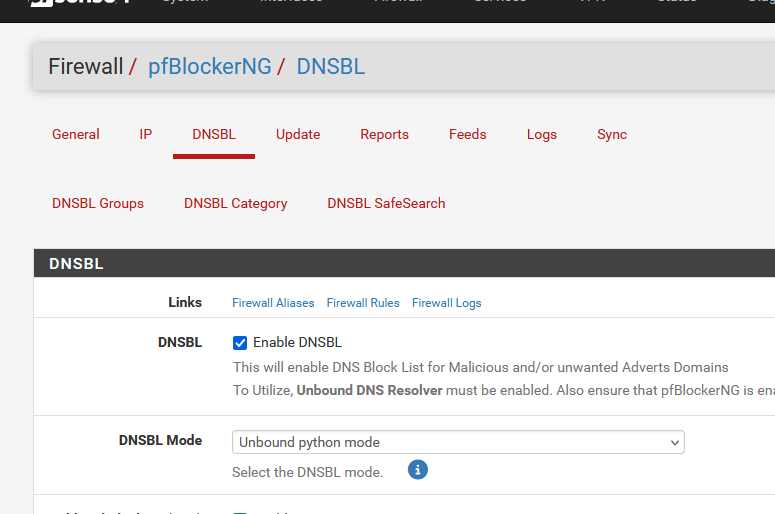
and check that DNSBL Mode is set to Unbound Python mode.
Leave the other options as is - you can come back later and select them - and try to understand what they are doing (I admit that some of them are still rocket sience to me, so I fall back to "KIS, don't activate what I don't understand").Save this page - at the bottom.
Then :
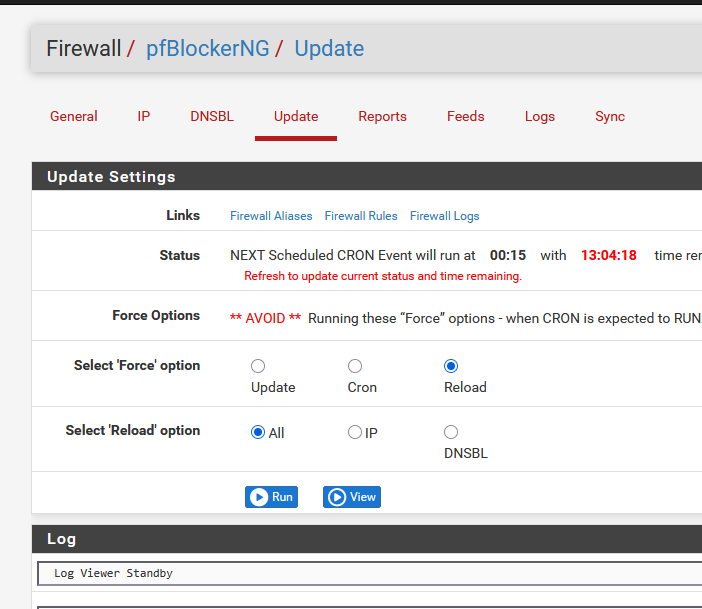
and hit Run.
Check the log produced for any issues - report what you find suspect or don't understand.
-
@Gertjan I did it exactly the way you showed. I posted some of the stuff I don't understand like it showing:
Servfail now. I see some resolves for feodotracker. I assume this is just the updates for the lists and not actually stuff being blocked? I only see 3 blocks so far on the main overview but not in the logs still. I also don't understand all these 127.0.0.1 resolves that don't tell me what device initiated it. Should I be seeing more blocks in general from DNSBL? -
This :
did you execute that on the pfSense command line ?
This :
;; Got SERVFAIL reply from 127.0.0.53 ** server can't find c.bing.com: SERVFAILmeans that the device that you are using was told that its DNS is 127.0.0.53. (that is the device itself !)
But ... non DNS server is listing on that address.
That device, can't you set it to use DHCP ? If you do, it will get an IP, a network, a gateway and a DNS, where the last two will be the pfSense LAN IP. From then on, that device will have a working In tenet connection, local network and DNS. That's why every device you buy (create) use DHCP ... as it works out of the box.If I execute the same command on pfSense, I see :
[25.07-RELEASE][root@pfSense.bhf.tld]/root: nslookup c.bing.com Server: 127.0.0.1 Address: 127.0.0.1#53 Non-authoritative answer: c.bing.com canonical name = c-bing-com.ax-0001.ax-msedge.net. c-bing-com.ax-0001.ax-msedge.net canonical name = ax-0001.ax-msedge.net. Name: ax-0001.ax-msedge.net Address: 150.171.27.10 Name: ax-0001.ax-msedge.net Address: 150.171.28.10 Name: ax-0001.ax-msedge.net Address: 2620:1ec:33:1::10 Name: ax-0001.ax-msedge.net Address: 2620:1ec:33::10Your "127.0.0.53" tells me : the DNS request isn't asked from pfSense, which has some LAN IP and not a localhost IP - but a local DNS (resolver ? forwarder ?) - for for what I know, maybe this process doesn't use pfSense (== unbound => pfBLockerng ...)
hen I execute on a PC, situated on my pfSense LAN , I see :
C:\Users\Gauche>nslookup c.bing.com Serveur : pfSense.hf.tld Address: 2a01:cb19:dead:beef:92ec:77ff:fe29:392c Réponse ne faisant pas autorité : Nom : ax-0001.ax-msedge.net Addresses: 2620:1ec:33:1::10 2620:1ec:33::10 150.171.27.10 150.171.28.10 Aliases: c.bing.com c-bing-com.ax-0001.ax-msedge.netwhere "2a01:cb19:dead:beef:92ec:77ff:fe29:392c" is the LAN (IPv6) of my pfSense.
"pfSense.hf.tld" is the host name of my pfSense.This means my Windows PC uses pfSense as it's "DNS server", which is nice, as pfSense uses unbound as the server = the resolver, and unbound sues also pfBlockerng to filter.
My unbound settings are prertty default, I resolve with the resolver.@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
Also any idea why I see this when I am not using google dns?
Not you, the person. Your devices, processes that are running on them, if you have something that is android (Google) base will use 8.8.8.8 as their role is : whatever you do, communicate it to Google (that is the deal). So, yeah, 8.8.8.8 (the reverse) can be looked up for.
It won't be pfSense that is looking for the reverse of 8.8.8.8. Netgate isn't Google, pfSense doesn't use 8.8.8.8. 8.8.8.8 is a resolver, pfSense has its own resolver (unbound). -
@Gertjan said in pfBlockerNG not logging anything by default?:
means that the device that you are using was told that its DNS is 127.0.0.53. (that is the device itself !)
But ... non DNS server is listing on that addressBut internet is working. It already uses DHCP. It is a Ubuntu device and afaik that's how the network manager works in Ubuntu. It is a link to another file in the conf. It still resolves to my pfsense 192.168.1.1 and I can see resolves from the Ubuntu devices IP in the logs. It might be a Ubuntu setting but I am not sure.
@Gertjan said in pfBlockerNG not logging anything by default?:
Serveur : pfSense.hf.tld
Address: 2a01:cb19:dead:beef:92ec:77ff:fe29:392cRéponse ne faisant pas autorité :
Nom : ax-0001.ax-msedge.net
Addresses: 2620:1ec:33:1::10
2620:1ec:33::10
150.171.27.10
150.171.28.10
Aliases: c.bing.com
c-bing-com.ax-0001.ax-msedge.netI am getting the same response on a Windows 10 device but c.bing.com is on the blocklist of DNSBL. So it should not work, right?
Maybe the issue comes from running Double-NAT? I have my ISP router (running Quad9DNS) and Pfsense sits behind it with a local IP as WAN IP.
Here are my Unbound settings. General Setup I already showed above.
@Gertjan said in pfBlockerNG not logging anything by default?:
Your devices, processes that are running on them
There should be no device running google anywhere in my network.At least nothing behind pfsense.
-
@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
It is a Ubuntu device
Ah, ok. I'm not familiar with Unbuntu but I do use Debian myself.
Like pfSense (based upon FreeBSD) there is file called /etc/resolv.conf which contains something like :nameserver 127.0.0.1 nameserver ::1 ....which means that programs process running on that system know where to go with their DNS requests.
Guess who listens on port 127.0.0.:53 on pfSense ?
Let's ask ;)
[25.07-RELEASE][root@pfSense.bhf.tld]/root: sockstat -4 | grep ':53'
avahi avahi-daem 61533 13 udp4 *:5353 :
unbound unbound 14531 5 udp4 *:53 :
unbound unbound 14531 6 tcp4 *:53 :
....If you Ubuntu was told that DNS requests have to send to 127.0.0.53 (probably port 53) then there must be a process that handles DNS requests listening on that address:port. If there is none, then you get a service fail or "SERV FAIL" as no DNS service is avaible.
That needs to be set up correced ^^@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
I have my ISP router (running Quad9DNS)
I have also a ISP 'upstream' router. Somewhat mandatory for me as that device knows how to talk to the 'laser led wire' (fiber) and handles the login against my ISP.
My ISP router probably uses the ISP's DNS servers, I'm not sure.
pfSense gets a WAN IP from this ISP router, which will be a RFC1918 like 192.168.10.4.
By default, pfSense won't use an DNS suggestion that comes with the lease from the ISP routers DHCP server, as (my) pfSense resolves.Here are my Unbound settings. General Setup I already showed above
Pretty default so you're good.
-
@Gertjan In my resolv.conf I see this:
GNU nano 7.2 /etc/resolv.conf # /etc/resolv.conf and seeing this text, you have followed the symlink. # # This is a dynamic resolv.conf file for connecting local clients to the # internal DNS stub resolver of systemd-resolved. This file lists all # configured search domains. # # Run "resolvectl status" to see details about the uplink DNS servers # currently in use. # # Third party programs should typically not access this file directly, but only # through the symlink at /etc/resolv.conf. To manage man:resolv.conf(5) in a # different way, replace this symlink by a static file or a different symlink. # # See man:systemd-resolved.service(8) for details about the supported modes of # operation for /etc/resolv.conf. nameserver 127.0.0.53 options edns0 trust-ad search .If I follow the commentary and use "resolvectl status" I get this:
Global Protocols: -LLMNR -mDNS -DNSOverTLS DNSSEC=no/unsupported resolv.conf mode: stub Link 2 (wlp4s0) Current Scopes: DNS Protocols: +DefaultRoute -LLMNR -mDNS -DNSOverTLS DNSSEC=no/unsupported Current DNS Server: 192.168.1.1 DNS Servers: 192.168.1.1DNSSEC is enabled in Pfsense but doesnt seem to work in Ubuntu. Maybe DNSOverTLS is the issue? I read about that somewhere in regards to DNSBL.
Your sockstat command does not work on Ubuntu. I only see an active TCP connection from google that contains 53 in the port number
So you are pretty much running the same setup as me. I don't know what I am missing that is not working here.
-
@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
Your sockstat command does not work on Ubu
That's normal. pfSense isn't Ubunutu (Debian, = Linux based).
It's using another ODS : FreeBSD.
So some commands look the same, some don't.This returns somewhat the same results :
netstat -naptul | grep ':53'Is this "Link 2 (wlp4s0)" your Ubuntu interface ?
The option "-DNSOverTLS" mighty in indicate that DNSOverTLS should be used ?
You are the Unbun user, so you tell me.
I know that the pfSense unbound doesn't use the TLS port :
as that port (TCP, port 953) needs to be activated so DNS TLS is supported.
As pSense uses a DNSSEC capable resolver, no need to for Ubuntu to deal with DNSSEC.
Use this https://wander.science/projects/dns/dnssec-resolver-test/ from a LAN 'PC' device and a browser and you'll see ;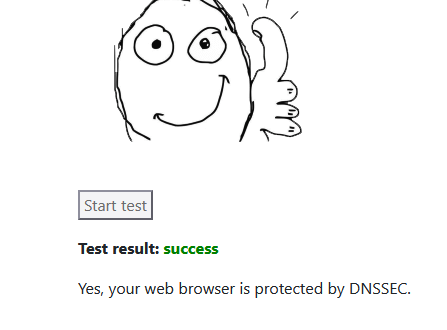
If your PC (or browser settings !!) use another DNS - not pfSense, well, that you might see different results.
-
@Gertjan I am suddenly seeing werid resolves:
192.168.1.31 reply A | A 86400 ipv4only.arpa 192.0.0.170 unkWhat could that be?
I also saw192.168.1.85 reply A | SOA 3140 desktop-AbTuMTYW.local SOA unkNone of these things exist on my network. Why is it resolving these things?
@Gertjan said in pfBlockerNG not logging anything by default?:
As pSense uses a DNSSEC capable resolver, no need to for Ubuntu to deal with DNSSEC.
Use this https://wander.science/projects/dns/dnssec-resolver-test/ from a LAN 'PC' device and a browser and you'll see ;This succeded
@Gertjan said in pfBlockerNG not logging anything by default?:
Is this "Link 2 (wlp4s0)" your Ubuntu interface ?
Yes it is. If I use the netstat command I see:
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN 792/systemd-resolve tcp 0 0 127.0.0.54:53 0.0.0.0:* LISTEN 792/systemd-resolve udp 0 0 127.0.0.54:53 0.0.0.0:* 792/systemd-resolve udp 0 0 127.0.0.53:53 0.0.0.0:* 792/systemd-resolve udp 0 0 0.0.0.0:5353 0.0.0.0:* 1071/avahi-daemon: udp6 0 0 :::5353 :::* 1071/avahi-daemon: -
@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
What could that be?
Locate the device "192168.1.31", it's a device on your LAN. That 's the one who wanted to, knwo the 'A' or IPv4 of the host name "ipv4only.arpa".
Unbound was just answering : it's "192.0.0.170" to 192.168.1.31.@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
None of these things exist on my network. Why is it resolving these things?
192.168.1.85 doesn't exist on your LAN ?
Not in the arp cache ?
Not a DHCP lease (might be a device with a static setup) ?@rasputinthegreatest said in pfBlockerNG not logging anything by default?:
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN 792/systemd-resolve
tcp 0 0 127.0.0.54:53 0.0.0.0:* LISTEN 792/systemd-resolve
udp 0 0 127.0.0.54:53 0.0.0.0:* 792/systemd-resolve
udp 0 0 127.0.0.53:53 0.0.0.0:* 792/systemd-resolveWell well, there you have you Ubuntu DNS !
You saw the name of the system process, : is "systemd-resolve" a resolver ? If so, then your Ubuntu totally bypasses the pfSense resolver (and pfBlockerng) . This means that DNS requests made by your Unbuntu are being handled by Ubuntus own resolver.edit : when your Ubuntu tries to use this 127.0.0.53 ( systemd/resolve ) it errors out .... (the serv fail)
Without details, set your system to, use 192.168.1.1 = pfSense, and you'll be good.
That said, it's your system. Time to check things out ?! -
@Gertjan said in pfBlockerNG not logging anything by default?:
192.168.1.85 doesn't exist on your LAN ?
This IP does exist on my LAN but why it resolves some weird random desktop-sdshdsd.local?
I am overwhelmed by the logs and see so much weird stuff like this. None of these things are on my network. Also no 192.168.51.5 exists on my network either.
DNS-reply,Aug 5 12:42:25,reply,A,NSEC,1835,desktop-A5k217Qu.local,192.168.1.86,NXDOMAIN,unk DNS-reply,Aug 5 10:09:22,reply,A,SOA,2942,hometheater-tQNIYv.local,192.168.1.86,SOA,unk DNS-reply,Aug 5 14:22:28,reply,A,SOA,3146,desktop-ZmWfGXFW.local,192.168.1.86,SOA,unk DNS-reply,Aug 5 10:38:49,local,PTR,PTR,Unk,10.34.1.10.in-addr.arpa,192.168.1.86,NXDOMAIN,unk DNS-reply,Aug 5 10:39:03,local,PTR,PTR,Unk,5.51.168.192.in-addr.arpa,192.168.1.86,NXDOMAIN,unk DNS-reply,Aug 5 10:39:09,local,PTR,PTR,Unk,10.170.0.10.in-addr.arpa,192.168.1.86,NXDOMAIN,unk DNS-reply,Aug 5 11:21:24,reply,A,SOA,2827,hometheater-WADQ2.local,192.168.1.86,SOA,unkI checked the pfblockerng logs and at 11:59:58 I see all these resolve. I assume it is related to time servers? I cant find any good info on what zorac.sf-bay.org is for example?
EDIT: Seems to be related to Perl which is used by pfsense plugins. But just a guess.DNS-reply,Aug 5 11:59:58,resolver,AAAA,AAAA,86400,anyns.pch.net,127.0.0.1,2001:500:14:6004:ad::1,unk DNS-reply,Aug 5 11:59:58,resolver,A,A,86400,anyns.pch.net,127.0.0.1,204.61.216.4,unk DNS-reply,Aug 5 11:59:58,resolver,A,A,57600,f.ntpns.org,127.0.0.1,139.178.72.201,unk DNS-reply,Aug 5 11:59:58,resolver,AAAA,AAAA,57600,f.ntpns.org,127.0.0.1,2a05:dfc1:cb1:123::,unk DNS-reply,Aug 5 11:59:58,resolver,A,A,86400,dns2.udel.edu,127.0.0.1,128.175.13.17,unk DNS-reply,Aug 5 11:59:58,resolver,AAAA,SOA,600,dns1.udel.edu,127.0.0.1,SOA,unk DNS-reply,Aug 5 11:59:58,resolver,AAAA,SOA,600,dns2.udel.edu,127.0.0.1,SOA,unk DNS-reply,Aug 5 11:59:58,resolver,A,A,86400,ns1.eu.bitnames.com,127.0.0.1,165.227.133.206,unk DNS-reply,Aug 5 11:59:58,resolver,AAAA,AAAA,86400,ns1.eu.bitnames.com,127.0.0.1,2a03:b0c0:3:d0::c0:4001,unk DNS-reply,Aug 5 11:59:58,resolver,A,A,3600,osdn.services.net,127.0.0.1,192.55.226.68,unk DNS-reply,Aug 5 11:59:58,resolver,A,A,57600,e.ntpns.org,127.0.0.1,45.33.123.43,unk DNS-reply,Aug 5 11:59:58,resolver,A,A,57600,c.ntpns.org,127.0.0.1,2.59.255.53,unk DNS-reply,Aug 5 11:59:58,resolver,AAAA,SOA,600,dns2.udel.edu,127.0.0.1,SOA,unk DNS-reply,Aug 5 11:59:58,resolver,AAAA,SOA,600,dns1.udel.edu,127.0.0.1,SOA,unk DNS-reply,Aug 5 11:59:58,resolver,AAAA,SOA,300,zorac.sf-bay.org,127.0.0.1,SOA,unk DNS-reply,Aug 5 11:59:58,resolver,A,SOA,300,zorac.sf-bay.org,127.0.0.1,SOA,unk DNS-reply,Aug 5 11:59:58,resolver,A,A,10400,g.ntpns.org,127.0.0.1,212.12.50.229,unk DNS-reply,Aug 5 11:59:58,resolver,A,A,3600,sdn.iecc.com,127.0.0.1,72.249.171.254,unk DNS-reply,Aug 5 11:59:58,resolver,AAAA,AAAA,57600,e.ntpns.org,127.0.0.1,2400:6180:0:d1::695:5001,unk DNS-reply,Aug 5 11:59:58,resolver,AAAA,AAAA,3600,sdn.iecc.com,127.0.0.1,2606:4300:0:4::106e,unk DNS-reply,Aug 5 11:59:58,resolver,A,A,3600,sdn.iecc.com,127.0.0.1,72.249.171.254,unk DNS-reply,Aug 5 11:59:58,resolver,AAAA,AAAA,3600,osdn.services.net,127.0.0.1,2001:470:1f07:1126:4e:6f74:6269:6e64,unk DNS-reply,Aug 5 11:59:58,resolver,AAAA,AAAA,57600,c.ntpns.org,127.0.0.1,2600:3c02::f03c:92ff:fe5f:baf1,unk DNS-reply,Aug 5 11:59:58,resolver,AAAA,AAAA,3600,ns2.everett.org,127.0.0.1,2001:470:1:205::230,unk DNS-reply,Aug 5 11:59:58,resolver,A,A,86400,ns2.us.bitnames.com,127.0.0.1,107.170.182.174,unk DNS-reply,Aug 5 11:59:58,resolver,AAAA,SOA,300,zorac.sf-bay.org,127.0.0.1,SOA,unk DNS-reply,Aug 5 11:59:58,resolver,AAAA,AAAA,3600,sdn.iecc.com,127.0.0.1,2606:4300:0:4::106e,unk DNS-reply,Aug 5 11:59:58,resolver,A,A,86400,ns3.us.bitnames.com,127.0.0.1,68.183.187.150,unk DNS-reply,Aug 5 11:59:58,resolver,A,A,57600,d.ntpns.org,127.0.0.1,86.109.15.15,unk@Gertjan said in pfBlockerNG not logging anything by default?:
Without details, set your system to, use 192.168.1.1 = pfSense, and you'll be good.
I did that but it hasn't changed anything. This was a default Ubuntu install and it has something to do with systemd-resolve but I can't figure it out myself.
@Gertjan said in pfBlockerNG not logging anything by default?:
You saw the name of the system process, : is "systemd-resolve" a resolver ? If so, then your Ubuntu totally bypasses the pfSense resolver (and pfBlockerng) . This means that DNS requests made by your Unbuntu are being handled by Ubuntus own resolver.
But why do I see stuff being resolved in pfblockerNG if it should be bypassed?
-
I am seeing all these strange things resolve in pfblockerNG like
devmachine-FKcElwG.local hometheater-wadq2.localWhy am I seeing this? Does this mean my network is compromised?
-
The situation is getting worse. I now see alot of strange stuff from 127.0.0.1
DNS-reply,Aug 6 09:10:26,resolver,A,A,299,fueled.byhamsters.net,127.0.0.1,69.65.50.223,unkAlienvault says Suspicious Dynamic DNS Update Request
https://otx.alienvault.com/indicator/ip/69.65.50.223Also I see this. Constantly newly named .local adresses despite having blocked port 5353 on the firewall.
devmachine-FKcElwG.local mypc-DogOjT5.local desktop-ZmWfGXFW.local desktop-A5k217Qu.local hometheater-WADQ2.local hometheater-tQNIYv.local hometheater-ejsl1t.local surveillance-GanzOF.local mediacenter-VAY4Bk.localI don't see any of these things in the Status -> DNS Resolver nor in any active states on my firewall.
Its very mysterious and I only see this now with pfblockerNG. My work computer but also my private laptop made some of these DNS requests or just picked up some broadcast? But most of the stuff I see originates from 127.0.0.1. All these names seem so randomly generated but the surveillance part makes me extra worried. Or are the DNSBL lists generating them somehow?Any help is appreciated since it is unnerving me.
EDIT: I found this which seems to be somewhat related https://serverfault.com/questions/1053970/weird-wpad-dns-queries-anyone-seen-this