What rule blocks this ?!?
-
@marchand.guy you mean you do not log the default deny?
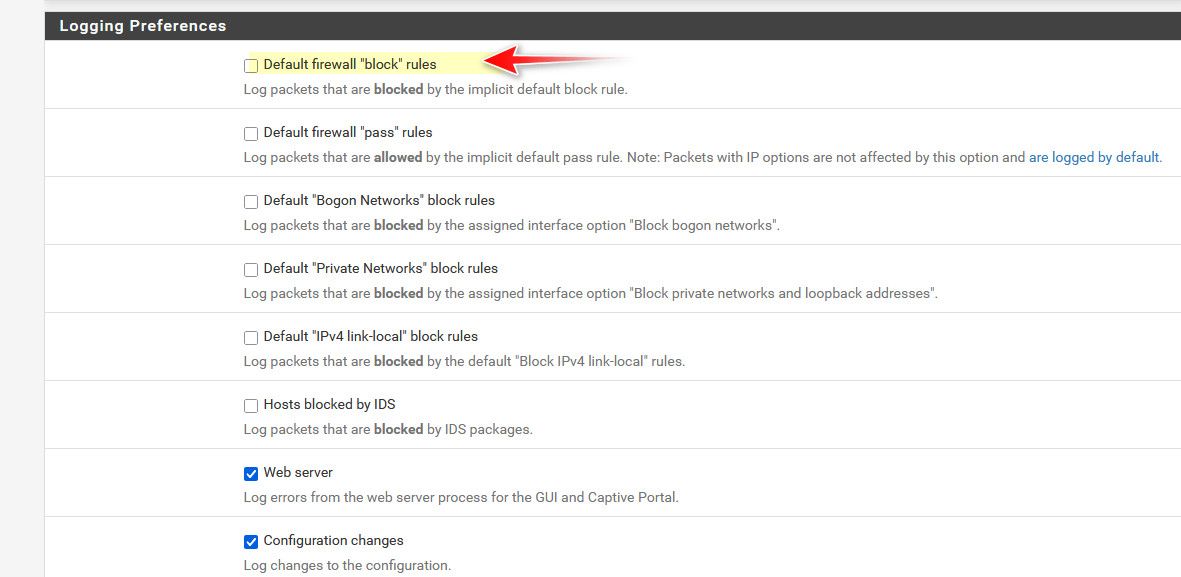
Then yeah that is odd?? That source IP is digital ocean.. Nothing good would ever come from there ;) But 53, dns port is odd that you would log that one? And not anything else.. Do you run IPS? Or Pfblocker with rules?
-
@johnpoz said in What rule blocks this ?!?:
you mean you do not log the default deny?
Exactly.
And yes I do run Pfblocker with rules. But not on the WAN interface. -
@marchand.guy doesn't pfblocker put rules in floating? I don't run any pfblocker rules - I only use it for aliases that I use as I see fit in my rules I create.
Never been a fan of any sort of "auto" generated firewall rules.
-
@johnpoz said in What rule blocks this ?!?:
doesn't pfblocker put rules in floating?
Indeed, if you let it by default. Which I don't. I'm using it to block outgoing traffic only from the LAN interface.
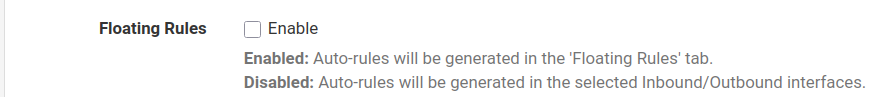
There is no auto rules on the WAN interface. I appreciate your time, but this "glitch" happens so rarely that I doubt we will get to the bottom of this. Don't watse your time anymore bud. And thank you.
-
@marchand.guy said in What rule blocks this ?!?:
block outgoing traffic only from the LAN interface.
Huh.. There are no outgoing rules on an interface.. You mean inbound rules into lan interface, that are dest for somewhere. The only way to put outgoing rules on any interface is via the floating tab. Rules on a specific interface are inbound rules into the interface, from the network the interface is attached to.
-
@johnpoz said in What rule blocks this ?!?:
There are no outgoing rules on an interface
I might not be using the proper words here. What I meant to say is that I control what goes out to the internet from rules on the LAN interface.
-
@marchand.guy I figured - but want to clarify just to make sure all on the same page.
Yes if you do not want something on your lan to go to xyz, then that would be a rule on your lan interface, but it is an inbound rule into the interface. If you want to block outbound traffic from an interface that is done on the floating rule tab. More often than not, these are never required in a typical use case. Only real rule I have as outbound blocking is rfc1918 to the internet.. So say for example I typo something and tried to go to 192.168.22.X vs to a host on my 192.168.2.x network - pfsense would block that traffic from actually going out to the internet via an oubound rule on the wan blocking rfc1918.. Just trying to be a good netizen and keep noise off the internet.
I mean the traffic really wouldn't go anywhere, unless my isp happen to be using 192.168.22 in their internal network.. But why send noise ;)
-
@johnpoz Correct. I am aware.
For future refences, here is the whole picture of both occurences since updating:
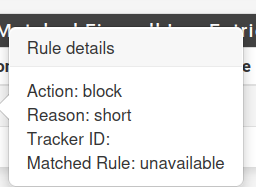
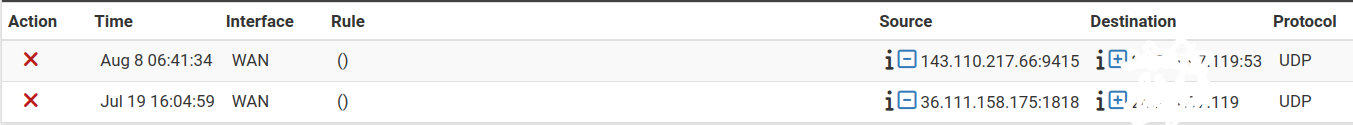
-
@marchand.guy oh that is a short block.. which is why no ID..
-
@johnpoz said in What rule blocks this ?!?:
short block
You mean an invalid short packet?
Edit: Oh the log reason is 'short'. Hmm I don't think I've ever seen that before. Yeah it's doesn't have to match a rule so no id etc.
